오늘은 사진 편집 어플 로 위장하는 안드로이드 악성코드인 Freesia Camera&Photo Filters에 대해 글을 적어 보겠습니다. 해당 악성코드는 스마트폰 사진 편집 및 사진 보정 어플로 위장을 하고 있으며 해당 악성코드는 구글 플레이 스토어 에서 유포하고 있으며 일단 2022.12.21 기준으로 해당 악성코드는 구글 플레이 스토어에서 사라졌습니다.
해당 악성코드는 다음과 같이 설명을 하고 있습니다. Freesia 카메라 또는 사진 필터는 수억 명의 사용자가 가장 좋아하는 앱입니다!
(부분 조정)
· 최대 20가지의 뷰티 기능으로 얼굴을 미세하게 조정하여 얼굴을 더욱 섬세하고 아름답게 가꾸어 주며 동시에 가식이 아닌 자연스럽습니다.
·슬리밍 기능으로 결점을 조정하여 놀라운 결과를 얻을 수 있습니다.
(에이스 스킨 타입 템플릿)
누가 잘생긴 스킨은 같다고 했나요? 다른 에이스 스킨 템플릿 기능은 없습니다. 클래식, 소프트, 크리미, 미스티, 내추럴, 텍스처, 7가지 피부 타입 중에서 선택하세요. 한 번의 클릭으로 높은 수준의 얼굴을 갖고 마음대로 기질을 전환하십시오.
(추천 스티커 스타일)
가장 신선하고 가장 잘생기고 재미있는 스타일 스티커 컬렉션, 기능 메이크업, 스타일 필터 및 개별 셀카 요소. 트렌드를 따라가고, 현재 핫한 스토킹과 함께 플레이하고, 친구들 사이에서 패션 베인이 되세요!
(네이티브 메이크업)
초현실적이고 스마트한 메이크업 효과로 다양한 각도와 표정에 두려움이 없습니다. 언제 어디서나 화장을 하지 않은 채 카메라 앞에 있으면 당신의 모습은 여전히 온라인 상태입니다!
(스케치 아트 룸)
한 번의 클릭으로 스케치, 색연필, 흑백 및 유화 스타일을 마음대로 전환할 수 있으며 아름다운 사진을 사용하여 차원의 장벽을 허물 수 있습니다!
(완벽한 순간을 포착하는 타이머)
평생 간직할 셀카를 찍기에 안성맞춤입니다.
(음소거 옵션)
셀카를 찍거나 조용한 식당에서 사진을 찍을 때 이 옵션을 활성화하십시오.
(사진 공유)
소셜 플랫폼에 쉽게 공유하세요! 아름다운 순간을 보존하려면 클라 우드에 저장하세요!
일단 유포되고 있었던 주소는 다음과 같습니다.
https://play.google(.)com/store/apps/details?id=com.zenobiawright.freesiacamera일단 먼저 해당 악성코드 해쉬값은 다음과 같습니다.
파일명:Freesia Camera & Photo Filters_1.0.2.apk
사이즈:4.41 MB
CRC32:1d988457
MD5:0ca54a12dfeb248b5c0c2400ec288266
SHA-1:9ef4d6cdc12fd7451dee17088de7adc85ffcc7ca
SHA-256:458814653fbde83de9cae6ad092f298265d202f63ac53750ca9987aff6f0dece
SHA-512:8a7644e0abc21e968b4ea57d7faa740f5023ba453ea7a35b7466834a1d378aaad681d25cab98d2c4a53edc115448d981c44a1014d476c8dcec850f7e2ad7ce90

그리고 해당 Freesia Camera & Photo 악성코드 권한은 다음과 같습니다.

<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.WAKE_LOCK"/>
<uses-permission android:name="com.google.android.finsky(.)permission.BIND_GET_INSTALL_REFERRER_SERVICE"/>
<uses-permission android:name="com.google.android(.)gms.permission.AD_ID"/>
<uses-permission android:name="android.permission.CALL_PHONE"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>일단 안드로이드 악성코드 권한을 보면 기본적으로 스마트폰 저장공간 읽기, 인터넷 연결, 네트워크_상태_접근, 전화번호 걸기, 연락처 읽기로 구성이 돼 있습니다. 일단 악성코드를 실행하면 다음과 같이 정상적으로 사진을 보정을 할 수가 있다는 식으로 앱이 실행이 되면 그리고 물론 해당 악성코드는 정상적으로 스마트폰에 저장된 사진이나 이미지 그리고 카메라를 통해서 사진이나 이미지를 필터 효과들을 제공합니다.
그리고 IMEI 관련 코드들은 다음과 같습니다.
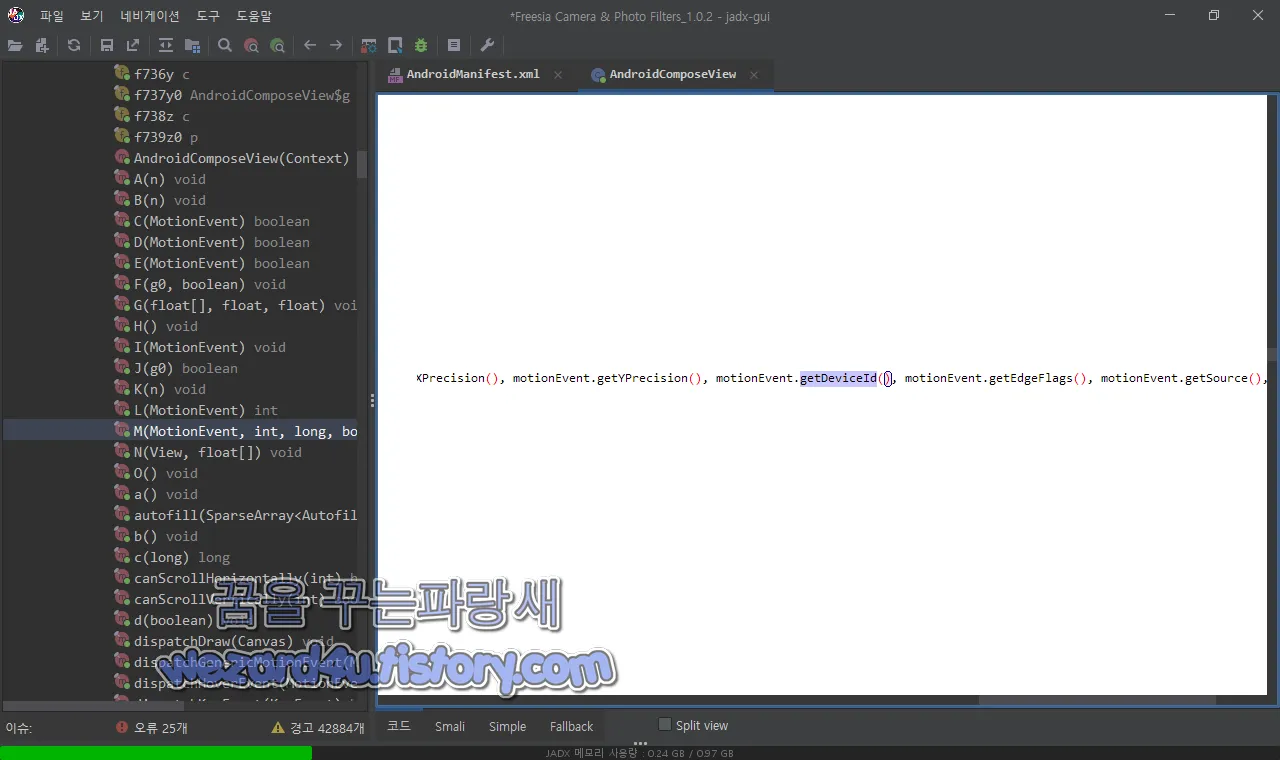
public final void M(MotionEvent motionEvent, int i2, long j10, boolean z10) {
int actionMasked = motionEvent.getActionMasked();
int i10 = -1;
if (actionMasked != 1) {
if (actionMasked == 6) {
i10 = motionEvent.getActionIndex();
}
} else if (i2 != 9 && i2 != 10) {
i10 = 0;
}
int pointerCount = motionEvent.getPointerCount() - (i10 >= 0 ? 1 : 0);
if (pointerCount == 0) {
return;
}
MotionEvent.PointerProperties[] pointerPropertiesArr = new MotionEvent.PointerProperties[pointerCount];
for (int i11 = 0; i11 < pointerCount; i11++) {
pointerPropertiesArr[i11] = new MotionEvent.PointerProperties();
}
MotionEvent.PointerCoords[] pointerCoordsArr = new MotionEvent.PointerCoords[pointerCount];
for (int i12 = 0; i12 < pointerCount; i12++) {
pointerCoordsArr[i12] = new MotionEvent.PointerCoords();
}
int i13 = 0;
while (i13 < pointerCount) {
int i14 = i13 + 1;
int i15 = ((i10 < 0 || i13 < i10) ? 0 : 1) + i13;
motionEvent.getPointerProperties(i15, pointerPropertiesArr[i13]);
MotionEvent.PointerCoords pointerCoords = pointerCoordsArr[i13];
motionEvent.getPointerCoords(i15, pointerCoords);
long c10 = c(b8.r0.d(pointerCoords.x, pointerCoords.y));
pointerCoords.x = u0.c.c(c10);
pointerCoords.y = u0.c.d(c10);
i13 = i14;
}
MotionEvent obtain = MotionEvent.obtain(motionEvent.getDownTime() == motionEvent.getEventTime() ? j10 : motionEvent.getDownTime(), j10, i2, pointerCount, pointerPropertiesArr, pointerCoordsArr, motionEvent.getMetaState(), z10 ? 0 : motionEvent.getButtonState(), motionEvent.getXPrecision(), motionEvent.getYPrecision(), motionEvent.getDeviceId(), motionEvent.getEdgeFlags(), motionEvent.getSource(), motionEvent.getFlags());
f1.h hVar = this.I;
wc.j.c(obtain, "event");
f1.t a10 = hVar.a(obtain, this);
wc.j.b(a10);
this.J.b(a10, this, true);
obtain.recycle();
}해당 악성코드가 사용하는 IP 트래픽은 다음과 같습니다.
104.21.63(.)204:443(TCP)
142.250.179(.)225:443(TCP)
142.250.179(.)234:443(TCP)
142.250.179(.)238:443(TCP)
142.250.180(.)3:443(TCP)
142.250.180(.)3:80(TCP)
142.250.187(.)202:443(TCP)
142.250.187(.)206:443(TCP)
142.250.200(.)14:443 (TCP)
142.251.111(.)94:443(TCP)
142.251.163(.)94:443(TCP)
172.217.16(.)227:443(TCP)
172.217.16(.)238:443(TCP)
172.217.169(.)35:443(TCP)
172.217.169(.)36:443(TCP)
172.217.169(.)42:443(TCP)
172.217.169(.)74:443(TCP)
172.67.150(.)16:443(TCP)
185.199.108(.)153:443(TCP)
185.199.111(.)153:443(TCP)
216.239.32(.)36:443(TCP)
216.58.212(.)238:443(TCP)
216.58.213(.)1:443(TCP)
216.58.213(.)3:443(TCP)그리고 C2 서버는 다음과 같습니다.
app.aidclean(.)com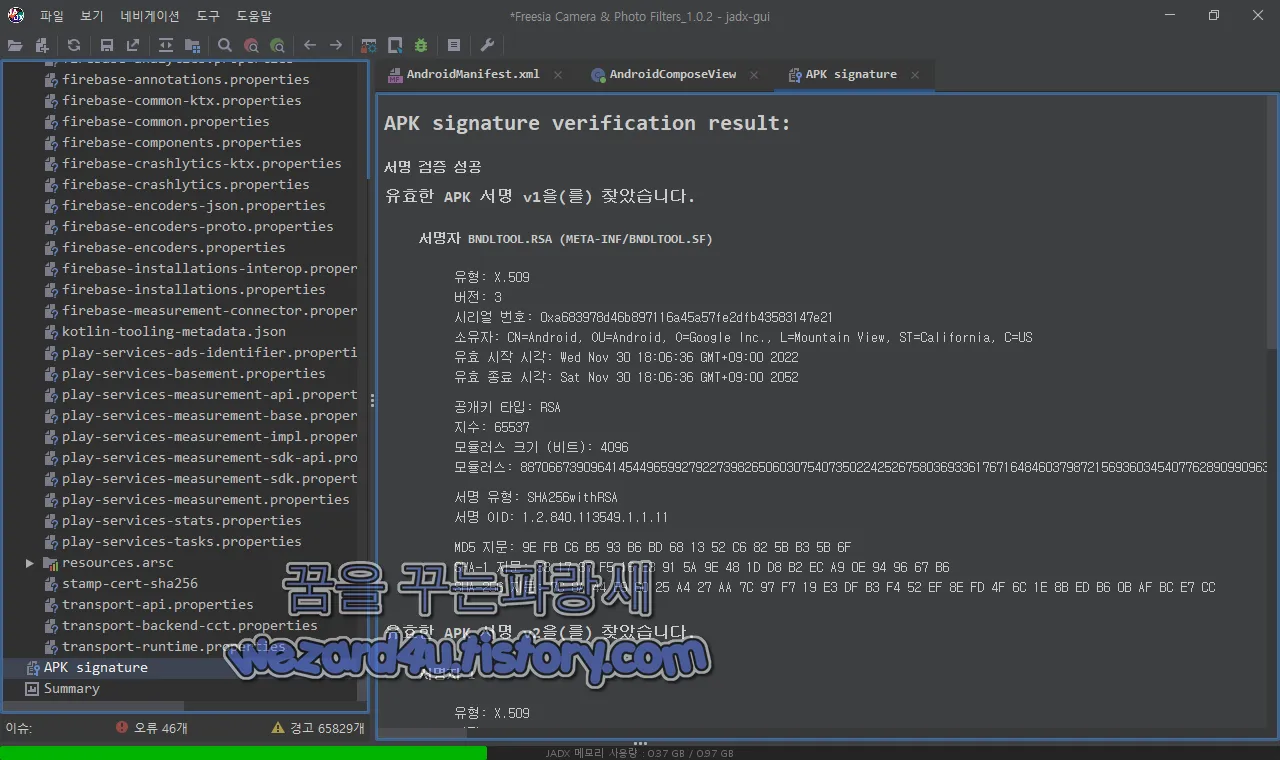
그리고 해당 악성코드 인증서는 다음과 같습니다.
서명자 BNDLTOOL.RSA (META-INF/BNDLTOOL.SF)
유형: X.509
버전: 3
시리얼 번호: 0xa683978d46b897116a45a57fe2dfb43583147e21
소유자: CN=Android, OU=Android, O=Google Inc., L=Mountain View, ST=California, C=US
유효 시작 시각: Wed Nov 30 18:06:36 GMT+09:00 2022
유효 종료 시각: Sat Nov 30 18:06:36 GMT+09:00 2052
공개키 타입: RSA
지수: 65537
모듈러스 크기 (비트): 4096
모듈러스: 887066739096414544965992792273982650603075407350224252675803693361767164846037987215693603454077628909909638967713327667240937896071462710360494369294986001315790626353861622438516534460274790057107636048102851324910276012199054436558324077305600470854267204831112723123397102043369200950971845362584418143813906773333647677641695898182212877627784613449784248511881970187004691396404811131439142638845376874347662997716523142627864734117458835681968615220098760813969236359787677287046488812967260994536148239093817934950784384906337976531315096506006510483372587277563499888605426931824373734845907721432308363153124890126227859798637728258062240962916847280909542642651400502781212608985705901578277336763013653271294291788894587878433954324843935381695598522212108880137013704794086849147177461066622547987281451987809126571939828634805714643770551184354646199943492060260952577004324172533760736998566837409579345246879371268096606621324962034302108187413858340837164039471810424609163734191011730481546494503238358514523984242814320164092494402746888196133421411397006273337970034552092319219302633141026720217233426991481220030800264623943175331851471548011926128191436476546158541762158850686214628062527658481129363007454153
서명 유형:SHA256withRSA
서명 OID:1.2.840.113549.1.1.11
MD5 지문:9E FB C6 B5 93 B6 BD 68 13 52 C6 82 5B B3 5B 6F
SHA-1 지문: 33 17 37 F5 16 E3 91 5A 9E 48 1D D8 B2 EC A9 0E 94 96 67 B6
SHA-256 지문: 7C 8A 44 E9 60 25 A4 27 AA 7C 97 F7 19 E3 DF B3 F4 52 EF 8E FD 4F 6C 1E 8B ED B6 0B AF BC E7 CC2022-12-21 10:57:35 UTC 기준 바이러스토탈에서 탐지하는 보안 업체들은 다음과 같습니다.
Ad-Aware:Trojan.GenericKD.64384459
Alibaba:Trojan:Android/Harly.afad168b
Arcabit:Trojan.Generic.D3D66DCB
Avast-Mobile:APK:RepMalware [Trj]
Avira (no cloud):ANDROID/Agent.hcgml
BitDefender:Trojan.GenericKD.64384459
Cynet:Malicious (score: 99)
DrWeb:Android.Joker.1945
Emsisoft:Trojan.GenericKD.64384459 (B)
eScan:Trojan.GenericKD.64384459
ESET-NOD32:A Variant Of Android/Agent.EFC
F-Secure:Malware.ANDROID/Agent.hcgml
Fortinet:Android/Agent.EFC!tr
GData:Trojan.GenericKD.64384459
Google:Detected
Ikarus:Trojan-Spy.AndroidOS.Harly
K7GW:Trojan ( 0059b57e1 )
Kaspersky:HEUR:Trojan.AndroidOS.Harly.x
Lionic:Trojan.AndroidOS.Harly.C!c
MAX:Malware (ai Score=99)
McAfee:Artemis!0CA54A12DFEB
McAfee-GW-Edition:Artemis!Trojan
NANO-Antivirus:Trojan.Android.Joker.jtyffm
Symantec:Trojan.Gen.MBT
Symantec Mobile Insight:AppRisk:Generisk
Tencent:Dos.Trojan.Harly.Zmhl
Trellix (FireEye):Trojan.GenericKD.64384459
Trustlook:Android.Malware.Trojan
VIPRE:Trojan.GenericKD.64384459
ZoneAlarm by Check Point:HEUR:Trojan.AndroidOS.Harly.x
이며 기본적으로 백신앱은 기본적으로 설치하고 특히 구글 플레이 스토어 또는 원스토어, 갤럭시 스토어등 기본적으로 공식 스토어가 아닌 곳에서는 앱을 다운로드 및 설치하는 것은 위험한 행동이며 구글 플레이 스토어 에서도 악성코드는 올라오고 있으니 항상 인지도가 있는 백신 앱을 사용을 하는 것이 좋으면 그리고 인터넷 사이트 즉 외부에서 따로 다운로드 하는 APK 파일을 설치하는 것은 악성코드에 감염될 확률을 높이는 것이기 때문에 가능한 외부 앱은 설치를 하지 않는 것이 좋습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 번역기 앱 으로 위장 하고 있는 안드로이드 악성코드-Quick Language Translator (0) | 2023.01.03 |
|---|---|
| 문의사항으로 유포 되고 있는 워드 악성코드-_문의사항_.docx(2022.11.02) (2) | 2022.12.31 |
| 가상화폐 거래소 바이낸스(Binance) 피싱 사이트-rbinance (0) | 2022.12.29 |
| 넷플릭스 피싱 사이트-service-office fr(2022.12.26) (2) | 2022.12.27 |
| 구글 웹용 지메일(Gmail)종단 간 암호화 도입 (2) | 2022.12.23 |
| 대북 관계자,북한 민간 전문가등을 노리는 워드 악성코드-동아시아연구원 사례비 지급 서식.docx(2022.12.15) (4) | 2022.12.21 |
| 윈도우 10 KB5021233 설치시 0xc000021a 오류 와 블루스크린 문제 발생 (4) | 2022.12.20 |
| 2023년 2월 Internet Explorer(인터넷 익스플로러) 비활성화 (0) | 2022.12.20 |





