오늘은 네이버 고객센터로 속여서 개인정보 즉 ID, 비밀번호를 훔쳐가는 피싱 사이트 를 탈취를 하려고 제작된 피싱 사이트 에 대해 알아보겠습니다.
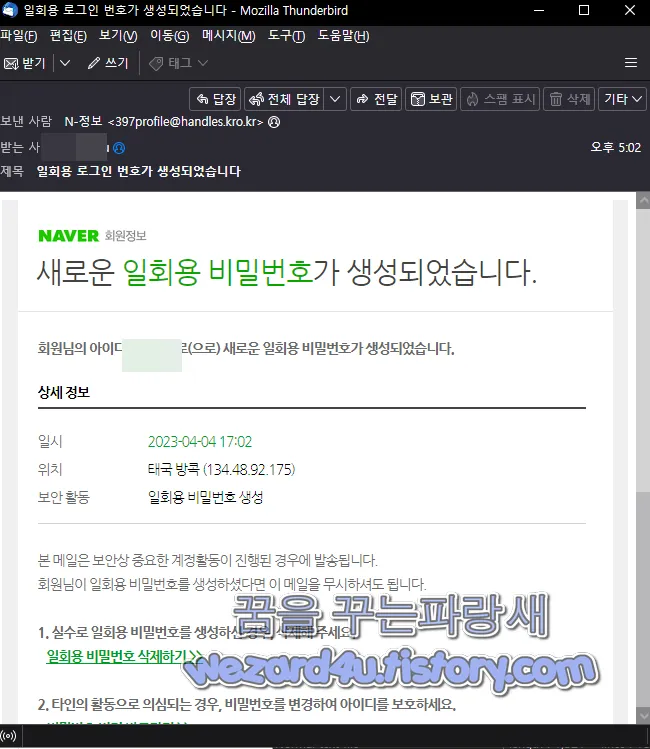
일단 해당 이메일 내용은 다음과 같습니다.
새로운 일회용 비밀번호가 생성되었습니다.
회원님의 아이디 ?????로(으로) 새로운 일회용 비밀번호가 생성되었습니다.
상세 정보
일시: 2023-04-04 17:02
위치: 태국 방콕 (134.48.92(.)175)
보안 활동 일회용 비밀번호 생성
본 메일은 보안상 중요한 계정활동이 진행된 경우에 발송됩니다.
회원님이 일회용 비밀번호를 생성하셨다면 이 메일을 무시하셔도 됩니다.
1. 실수로 일회용 비밀번호를 생성하신 경우, 삭제해 주세요.
일회용 비밀번호 삭제하기 >>
2. 타인의 활동으로 의심되는 경우, 비밀번호를 변경하여 아이디를 보호하세요.
비밀번호 변경 바로 가기 >>
아이디(ID) 도용을 막기 위한 팁(tip) 세가지! 자세히보기
네이버를 이용해 주셔서 감사합니다.
더욱 편리한 서비스를 제공하기 위해 항상 최선을 다하겠습니다.
그리고 해당 이메일 을 보낸 이메일 주소는 다음과 같습니다.
397profile@handles.kro(.)kr해당 이메일 까 보면 다음과 같습니다.
ARC-Sea::i=1; a="rsa-sha256"; d="naver(.)com"; s="arc-20180730"; t="1680595360"; cv="none"; b="WxyvgDPj703smpcJDZgerY+gDGFEEXIKma57HV31SWtUugj1CPh9NZ+1A6Gw
AUxhEwaDMHwkKpSeTworplcNkhcYBe99q0ey2RPWEG3TU9POGix5njNPNSQTy61L7eeXS+
SEagxa8ZNtm4aGF/nKaPZliqAhrCXIDpu1icCzH41B5gXi1W5o8CPEK1oq0T1towDWM/+J
QGVkDOUtI9xVSaWjAtfn2GFdZ/4bwrzSSXjollOz6GuiRbHF0zByX4dezkc+pkRYoDTBgy
y4APwFeDIx+D5yH5fGMGSH3fGLH05Uwt/zTZT+BJ5dZW7MDqujxXflCZ7LQgdBsrjLIlnS
5A=="
ARC-Message-Signature:i=1; a="rsa-sha256"; d="naver(.)com"; s="arc-20180730"; t="1680595360"; c="relaxed/relaxed"; bh="kdhHePNL40rNY8rdrMtCLzLRtaCZPdX+pR/zm9aRPeE="; h="dkim-signature:date:from:message-id:subject:to"; b="azNWTb0MM1YQWf2V6tn
0FMtldjqDKW8dRc6+McimbmARZ8kGbOIy2i260CrzO/AEFzzb1dVuOOWLTUOCGmM9rDIiV
Jfsng1qP0EnNT3tRHymU/62/8VeIdGjQzOftDJ2+QOem70iBCE5Nf//hNmRNTq2A2IoZgx
UjRpU9JziS9upMnuqjf22ufWsyHyEY4snbdGZQ2szMW8TjQvwpXQyKkRSfKKZUW4fqEZRF
ijXV+8wsLsSTQNtjc2UNsj8Y7FAb7Z0qs4WvnLmQm8oZ+8l3A8ac1z6hDznX27AfnM6WeN
968hNOV13JdjY0D4gj5cUcccq7myKJnITruzElSx/ng=="
ARC-Authentication-Results i=1; mx.naver(.)com; spf="none (mx.naver(.)com: domain of bounces+33324563-1685-??????=naver(.)com@em9043.handles.kro(.)kr does not designate permitted sender hosts) smtp.mailfrom=bounces+33324563-1685-??????=naver(.)com@em9043.handles.kro(.)kr"; dkim="fail (no key for signature) header.i=@handles.kro(.)kr"
Return-Path <bounces+33324563-1685-??????=naver(.)com@em9043.handles.kro(.)kr>
Received-SPF:none (mx.naver(.)com: domain of bounces+33324563-1685-???=naver(.)com@em9043.handles.kro(.)kr does not designate permitted sender hosts)
client-ip=149.72.126(.)143; x-iptype="default"
Authentication-Results mx.naver(.)com; spf="none (mx.naver(.)com: domain of bounces+33324563-1685-??????=naver(.)com@em9043.handles.kro(.)kr does not designate permitted sender hosts) smtp.mailfrom=bounces+33324563-1685-???????=naver(.)com@em9043.handles.kro(.)kr"; dkim="fail (no key for signature) header.i=@handles.kro(.)kr"
X-Naver-ESV wQFn+6J4p63TWNmr7BwdW4kYKA2mKotmjJ+Y
X-Session-IP:149.72.126(.)143
Received from s.wrqvtzvf.outbound-mail.sendgrid(.)net (s.wrqvtzvf.outbound-mail.sendgrid.net [149.72.126(.)143])
by crcvmail201.nm.naver(.)com with ESMTP id l4rUX7RSQSmv83bOai64DQ
for <????@naver(.)com>
(version=TLSv1.2 cipher=ECDHE-RSA-AES128-GCM-SHA256);
Tue, 04 Apr 2023 08:02:40 -0000
DKIM-Signature v=1; a="rsa-sha256"; c="relaxed/relaxed"; d="handles.kro(.)kr"; h="content-transfer-encoding:content-type:from:mime-version:subject:to:
cc:content-type:from:subject:to"; s="s1"; bh="kdhHePNL40rNY8rdrMtCLzLRtaCZPdX+pR/zm9aRPeE="; b="LMBc4zUqsbmj53WG01iY4nwuNLzBJYoHjZYytM5EaQastaDNX0vXnZaAX0i3WolF8qpG
Or3z9Rg1yQKdbrWyLMMDh1UnD0zU1yD6xOBi+Yr0N1GBjGp9ssM0hC9CbVzKMnofTZG4W5
izEDsFj+ohZOQiGzTfsIhXhnr3VdTcMIv3TQ7C0wS5XabuXAxGIY4Ro+CaWbExgNKTq4pI
Kjpj9gfQOVwXvzn0OdQBoeUYoOlYtMJwsXhrq/jE4bKlRppzbnTkIkn1O6CeLsR+EzfX5v
xWtB2sK7n89zhNmeFcHwyNEADKbG7j1iH4A+n3ftw25dLeGGrP/xWeGAYTJHEmzw=="
Received by filterdrecv-6c845fd887-wtb99 with SMTP id filterdrecv-6c845fd887-wtb99-1-642BD99D-19
2023-04-04 08:02:37.645050648 +0000 UTC m=+3573069.136478506
Received:from MzMzMjQ1NjM (unknown)
by geopod-ismtpd-canary-0 (SG)
with HTTP
id bR5KP3pjR_a3_9A5ts304Q
Tue, 04 Apr 2023 08:02:37.346 +0000 (UTC)
Content-Transfer-Encoding quoted-printable
Content-Type text/html; charset="utf-8"
Date Tue, 04 Apr 2023 08:02:37 +0000 (UTC)
From N-정보 <397profile@handles.kro(.)kr>
Mime-Version 1.0
Message-ID <bR5KP3pjR_a3_9A5ts304Q@geopod-ismtpd-canary-0>
Subject 일회용 로그인 번호가 생성되었습니다.
X-SG-EID HyIzwTmkQBlkKhQBhrYWEflEDqCXPnaaXl1svX7eAmmd2qLj03EvTPVawCxNP9gurx23DAl3tCGiV3cT+uwSQBcA2RxGGgdHZYkxIwRqnVn0XwZwzv3rRVG3gNHYvLn7YgGBjYwZti2SWj4B8BfGiv9/VrRtQLFCtKsjonIZzBqdijztq8UibD8i2RrZyvKsyV9pESkoB4p4L6uUw4hx4b9RST/mmIOT688IwauavaFjtu57iZiHa4QuTRnCJXup
To ??????@naver.com
X-Entity-ID AIkShCyrN1n3iMhYuRLt3Q==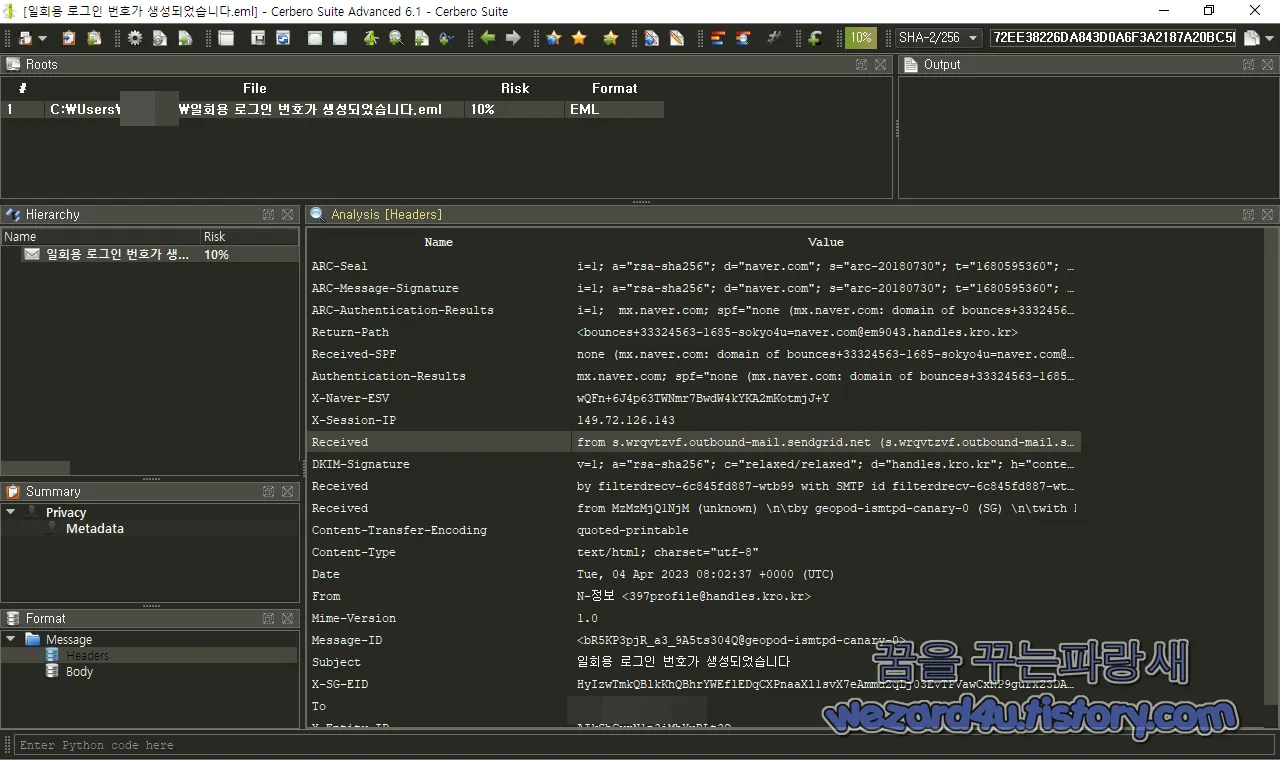
일단 개인정보 탈취를 하려고 사용이 되는 주소는 다음과 같습니다.
https://u33324563.ct.sendgrid(.)net/ls/click?upn=??????????????????QosSwcKyVfywijBPtg4wdJ1oRJJZAVwciUi-2Fvm-2BVgDkWnGnNux0CEWq0npf-2BY9nEOw81RUPt3BpT1Ohhkc-3Dri6n_qJT2AVoUb-2FCCQxRdLh0MIchnNvvDfhB0KCYfTpJGNTow5SLJwHxygJj5cONsKa5-2B89dpd6WJBmrlZ6LVw5xYtr7DTt601zlohN92h9xSS0R2Q71WZA3Y3bat5BBx09tNIlaHTnFCXDT94ytTaefVEmO9-2B8CMOT9s0VDM2zxMGRSrqavd4Iu-2F3OCodcVFu2Jklnay037wSxodCQfVsuaipw-3D-3D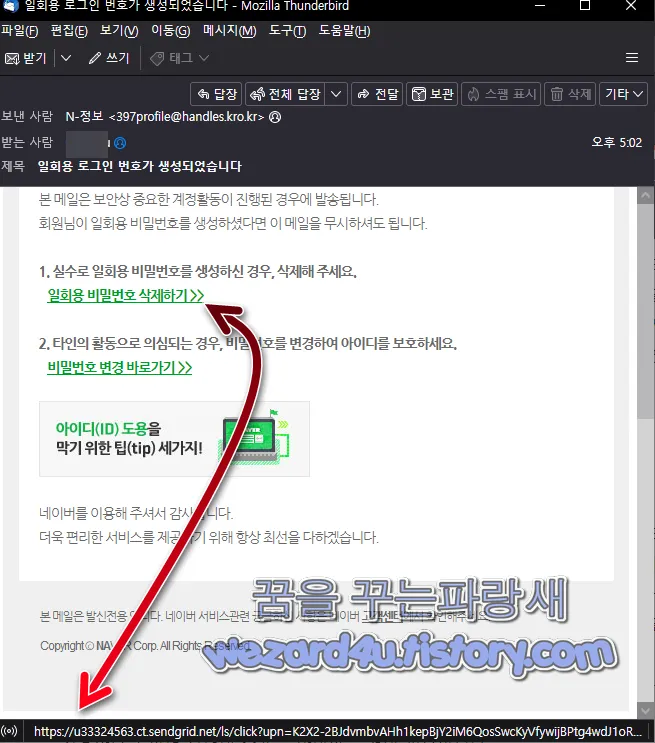
그럼 피싱 메일을 분석을 해 보겠습니다.
Received:from s.wrqvtzvf.outbound-mail(.)sendgrid(.)net
자기 자신이 s.wrqvtzvf.outbound-mail(.)sendgrid(.)net라고 언급한 호스트 발신 호스트에서 수신 호스트에게 “HI 호스트이름” 또는 “HIHI 호스트이름” 형식으로 알려주는 역할이며 해당 부분을 통해서 알 수 있는 것은 로부터 메일을 수신하였다는 의미
실제 IP
(s.wrqvtzvf.outbound-mail.sendgrid(.)net [149.72.126(.)143])
149.72.126(.)143 이라는 IP를 사용하는 것을 확인할 수가 있습니다. 호스트의 이름은 sendgrid(.)net 이 되겠습니다. 만약 Reverse DNS 질의를 했을 때 응답이 없으면 공란으로 나옴
by crcvmail201.nm.naver(.)com with ESMTP id l4rUX7RSQSmv83bOai64DQ
메일을 수신한 호스트는 crcvmail201.nm.naver(.)com 이라는 것을 확인할 수가 있습니다. 그리고 esmtp 프로토콜을 통해 수신하는 호스트에서 해당 메시지를 구별하기 위해 l4rUX7RSQSmv83bOai64DQ 이라는 ID 발급받은 것으로 확인할 수가 있습니다.
for <???????@naver(.)com>
메시지가 전송될 메일주소를 표시합니다.
(version=TLSv1.2 cipher=ECDHE-RSA-AES128-GCM-SHA256);
Tue, 04 Apr 2023 08:02:40 -0000
해당 부분을 통해서 2023년4월4일 08:02:40에 전송이 되었다는 것을 확인할 수가 있습니다.
일단 개인적으로 접속을 시도했으나 해당 피싱 사이트 404 에러 이면서 만약 클릭 시 진짜 네이버 사이트로 연결하도록 조치가 돼 있음
네이버에서 공식 메일 주소는 다음과 같습니다.
account_noreply@navercorp(.)com
입니다.
네이버 공식 메일 비슷하게 naver 이 never처럼 되니 사용자가 속기 쉽습니다.
그리고 네이버 공식 계정에서 발송한 메일에는 발신자 이름 앞에 N 아이콘이 표시되면 네이버 웹 메일 또는 네이버 메일을 사용하지 않으면 해당 부분을 볼 수가 없으니 이메일 주소를 직접 확인해야 합니다.
그리고 기본적으로 저 같은 경우 2023-03-08 오전 8:46에 해당 메일 수신을 했습니다.
여기서 자신이 네이버 계정 비밀번호를 입력했을 때는 기본적으로 할 것은 바로 비밀번호를 변경하고 네이버 2단계 인증을 사용하시는 것을 추천합니다.
즉 기본적으로 네이버 공식 마크를 확인하고 그리고 기본적으로 네이버에서는 기본적으로 아이디는 다 보이게 보내지 않는다. 그리고 인증서 정보, 보낸이 이메일 주소를 확인하는 습관 그리고 다른 이메일 관리 프로그램을 사용한다고 하면 보낸이 주소를 확인하는 것이 필요합니다. 일단 사견(私見)으로는 북한의 김수키(Kimsuky) 일 가능성이 크다고 생각을 합니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 윈도우 10 버전 21H2 2023년 6월에 서비스 종료 (0) | 2023.04.11 |
|---|---|
| 대북 관계자들을 노리는 BlueNorOff(블루노로프)-질문지.doc(2023.04.06) (0) | 2023.04.10 |
| Microsoft Edge 112(마이크로소프트 엣지 112) 보안 업데이트 (0) | 2023.04.07 |
| Microsoft OneNote(마이크로소프트 원노트)120개 위험한 파일 확장자를 차단 (0) | 2023.04.06 |
| 페덱스 로 위장 하고 있는 피싱 메일-[페덱스] 수입면장 안내!.(2023.3.31) (0) | 2023.04.04 |
| 3CX 공격에 악용된 옵트인 레지스터리 수정 방법 (0) | 2023.04.03 |
| Steam(스팀) 윈도우7,윈도우 8 대한 지원 2024년1월1일 까지 (0) | 2023.03.31 |
| 마이크로소프트 계정 훔치기 위한 피싱 엑셀 문서-Statement001.xlsx(2023.03.30) (0) | 2023.03.30 |





