오늘은 구글 플레이 스토어 에서 유포되었던 Autolycos 악성코드인 Freeglow Camera에 대해서 글을 적어 보겠습니다. 일단 해당 악성코드는 5,000 다운로드 를 기록을 했고 해당 악성코드에 많은 사람이 감염되었다는 것을 확인할 수가 있습니다.
Autolycos는 원격 브라우저에서 URL을 실행한 다음 Webview를 사용하는 대신 HTTP 요청에 결과를 포함하는 등 은밀한 악성 행위를 수행하는 악성 코드이며 즉 동작은 해당 동작을 덜 눈에 띄게 하여 손상된 장치의 사용자가 감지하지 못하도록 하기 위한 목적입니다.
악성코드들은 스마트폰에 설치 시 SMS(문자)를 읽을 수 있는 권한을 요청해서 앱이 피해자의 SMS 문자 메시지에 액세스 할 수 있도록 하고 있으며 새로운 사용자에게 앱을 홍보하기 위해 Autolycos 운영자는 소셜 미디어에서 수많은 광고 캠페인을 만들며 다른 악성코드들에서는 Facebook에서 최소 74개의 광고 캠페인이 포함돼 있습니다. 물론 현재는 해당 악성코드들은 삭제된 상태이며 유포되었던 주소는 다음과 같습니다.
https://play.google(.)com/store/apps/details?id=com.glow.camera.open&ref=apkcombo.com일단 먼저 해당 안드로이드 악성코드의 해쉬값 은 다음과 같습니다.
파일명: Freeglow Camera_1.0.apk
사이즈:33.4 MB
CRC32:e6505261
MD5:d2464e1fb709b82a2e8f2be9f465d4cd
SHA-1:e38d90a28b34c7bc2723397a6b93147a74550b4f
SHA-256:8c64a5f8c482952c2cbc3587c978d73896b79e82452d87e9c6b54108e0908bd4
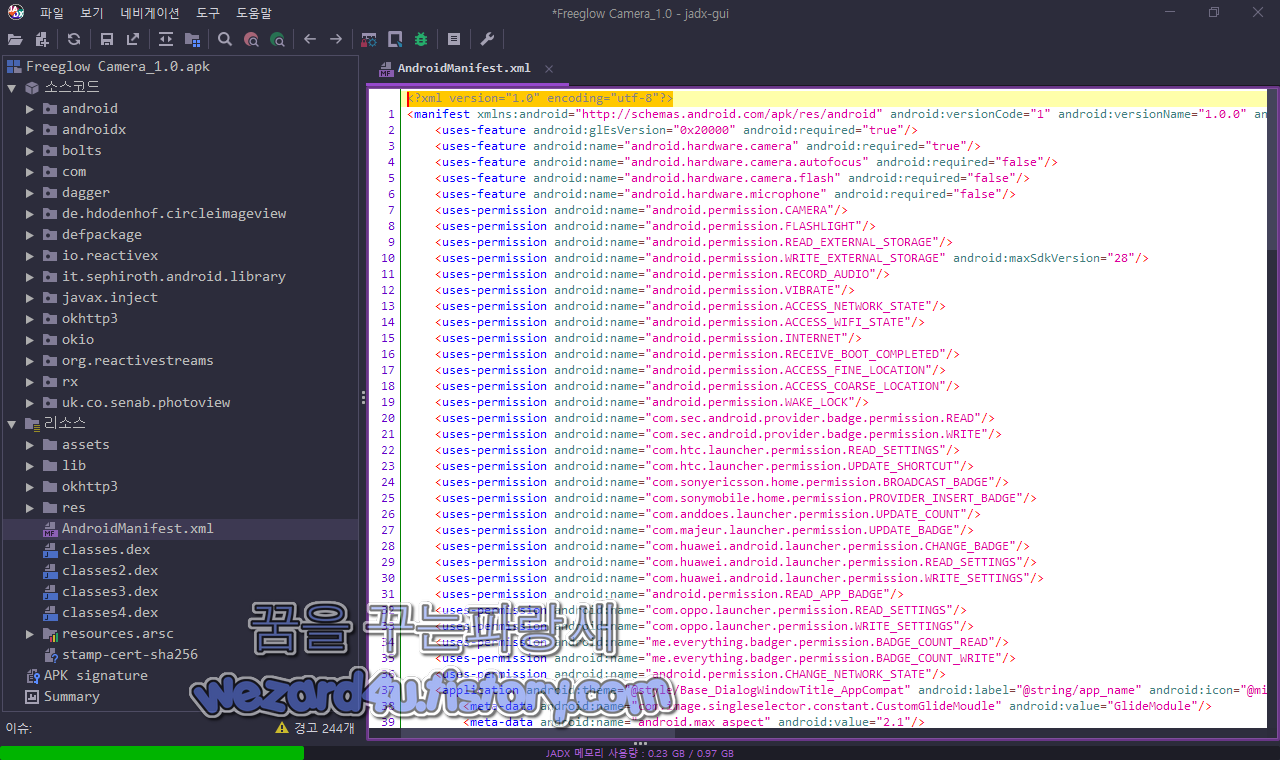
그리고 Freeglow Camera 악성코드 안드로이드 권한은 다음과 같습니다.
<uses-feature android:name="android.hardware.camera" android:required="true"/>
<uses-feature android:name="android.hardware.camera.autofocus" android:required="false"/>
<uses-feature android:name="android.hardware.camera.flash" android:required="false"/>
<uses-feature android:name="android.hardware.microphone" android:required="false"/>
<uses-permission android:name="android.permission.CAMERA"/>
<uses-permission android:name="android.permission.FLASHLIGHT"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" android:maxSdkVersion="28"/>
<uses-permission android:name="android.permission.RECORD_AUDIO"/>
<uses-permission android:name="android.permission.VIBRATE"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"/>
<uses-permission android:name="android.permission.WAKE_LOCK"/>
<uses-permission android:name="com.sec.android.provider.badge.permission.READ"/>
<uses-permission android:name="com.sec.android.provider.badge.permission.WRITE"/>
<uses-permission android:name="com.htc.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.htc.launcher.permission.UPDATE_SHORTCUT"/>
<uses-permission android:name="com.sonyericsson.home.permission.BROADCAST_BADGE"/>
<uses-permission android:name="com.sonymobile.home.permission.PROVIDER_INSERT_BADGE"/>
<uses-permission android:name="com.anddoes.launcher.permission.UPDATE_COUNT"/>
<uses-permission android:name="com.majeur.launcher.permission.UPDATE_BADGE"/>
<uses-permission android:name="com.huawei.android.launcher.permission.CHANGE_BADGE"/>
<uses-permission android:name="com.huawei.android.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.huawei.android.launcher.permission.WRITE_SETTINGS"/>
<uses-permission android:name="android.permission.READ_APP_BADGE"/>
<uses-permission android:name="com.oppo.launcher.permission.READ_SETTINGS"/>
<uses-permission android:name="com.oppo.launcher.permission.WRITE_SETTINGS"/>
<uses-permission android:name="me.everything.badger.permission.BADGE_COUNT_READ"/>
<uses-permission android:name="me.everything.badger.permission.BADGE_COUNT_WRITE"/>
<uses-permission android:name="android.permission.CHANGE_NETWORK_STATE"/>기본적으로 스마트폰 카메라 어플로 돼 있으니 기본적으로 스마트폰 카메라, 스마트폰 손전등, 스마트폰 외장 디스크 읽고 쓰기, 녹음, 진동, 네트워크 연결 확인, 인터넷, 스마트폰 부팅시 인텐트를 수신, 위치 찾기 접근, 삼성 갤럭시, 소니, 화웨이, HTC 런처 들이 보이고 전화번호에 접근하기 위한 권한들이 있는 것을 볼 수가 있습니다.
스마트폰 카메라와 관련된 부분은 다음과 같이 com.glow.camera.main.a.a 에 포함이 돼 있습니다.
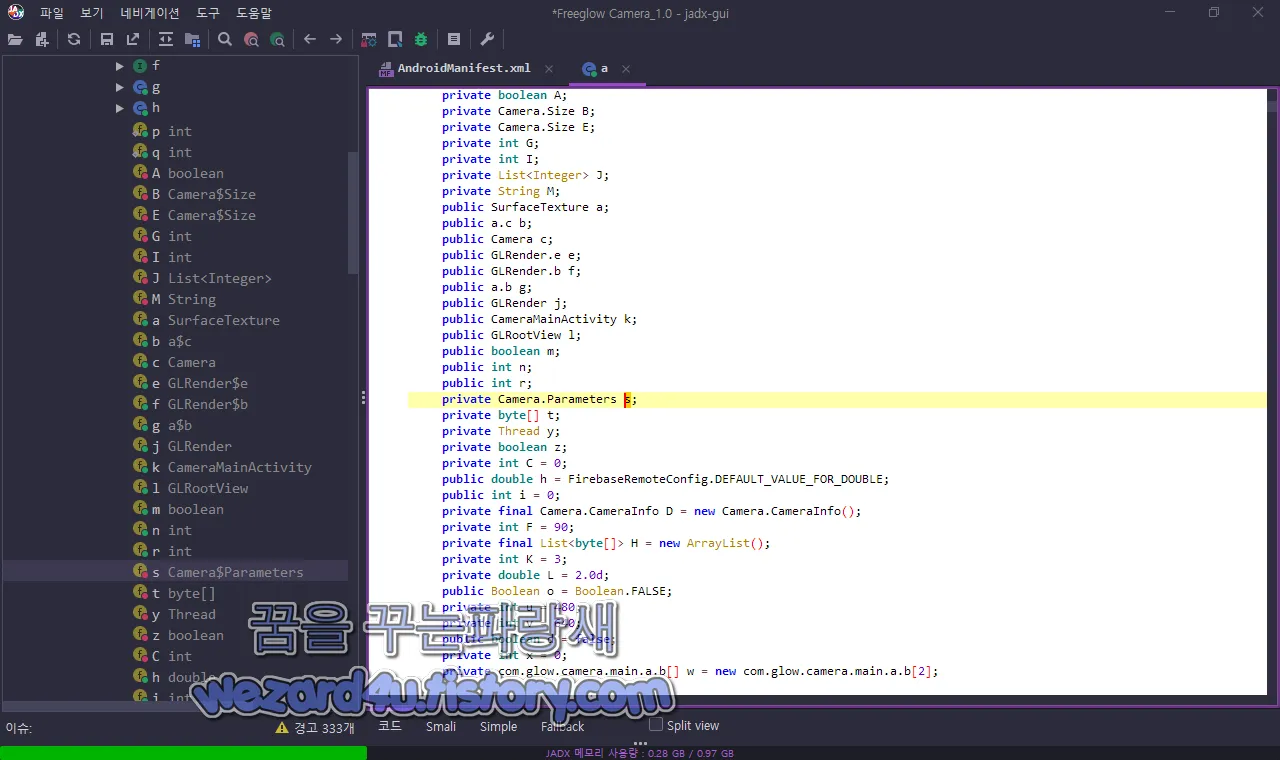
/* loaded from: classes.dex */
public final class a implements SurfaceTexture.OnFrameAvailableListener, Camera.PreviewCallback {
public static int p;
public static int q;
private boolean A;
private Camera.Size B;
private Camera.Size E;
private int G;
private int I;
private List<Integer> J;
private String M;
public SurfaceTexture a;
public a.c b;
public Camera c;
public GLRender.e e;
public GLRender.b f;
public a.b g;
public GLRender j;
public CameraMainActivity k;
public GLRootView l;
public boolean m;
public int n;
public int r;
private Camera.Parameters s;
private byte[] t;
private Thread y;
private boolean z;
private int C = 0;
public double h = FirebaseRemoteConfig.DEFAULT_VALUE_FOR_DOUBLE;
public int i = 0;
private final Camera.CameraInfo D = new Camera.CameraInfo();
private int F = 90;
private final List<byte[]> H = new ArrayList();
private int K = 3;
private double L = 2.0d;
public Boolean o = Boolean.FALSE;
private int u = 480;
private int v = 640;
public boolean d = false;
private int x = 0;
private com.glow.camera.main.a.b[] w = new com.glow.camera.main.a.b[2];사실상 com.glow.camera.main에 카메라 관련 코드 부분이라고 생각을 하시면 됩니다.
스마트폰 IMEI 관련 코드들은 android.support.v7.app.AppCompatDelegateImpl 에 존재하고 있습니다.
코드를 보면 다음과 같습니다.
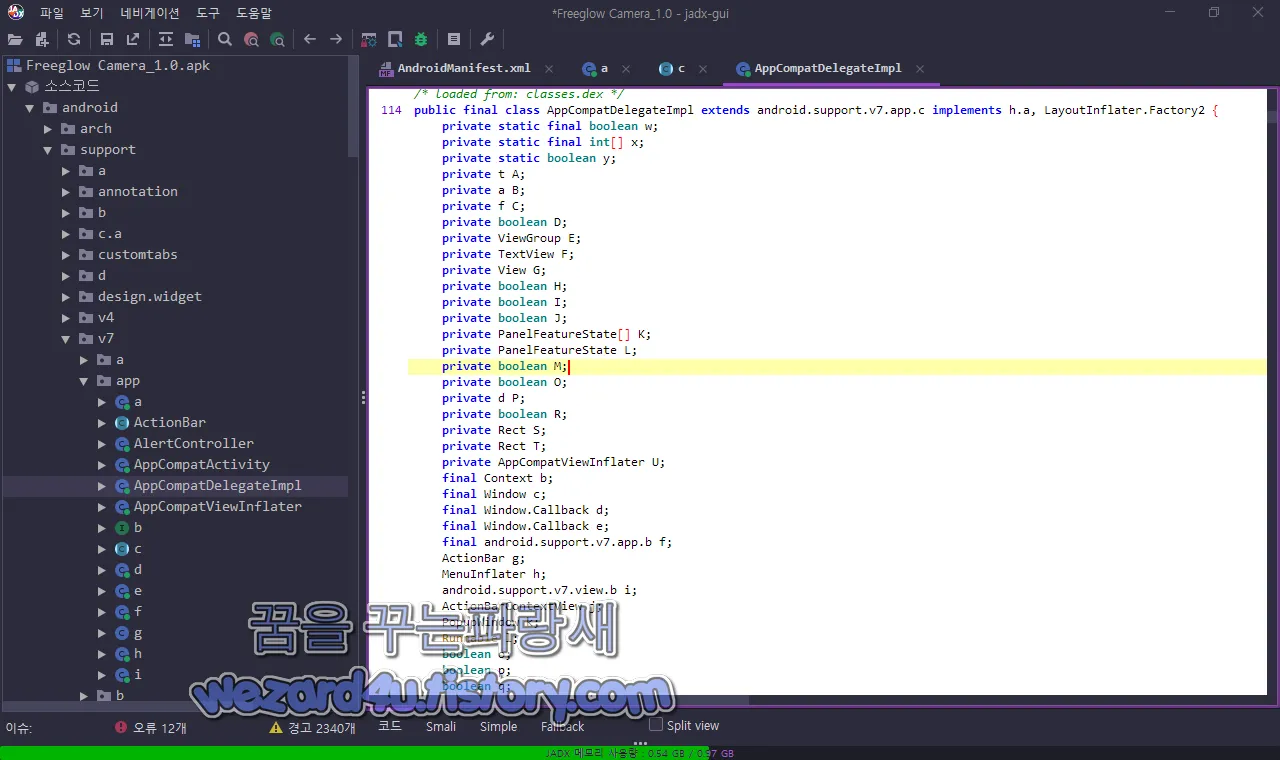
/* loaded from: classes.dex */
public final class AppCompatDelegateImpl extends android.support.v7.app.c implements h.a, LayoutInflater.Factory2 {
private static final boolean w;
private static final int[] x;
private static boolean y;
private t A;
private a B;
private f C;
private boolean D;
private ViewGroup E;
private TextView F;
private View G;
private boolean H;
private boolean I;
private boolean J;
private PanelFeatureState[] K;
private PanelFeatureState L;
private boolean M;
private boolean O;
private d P;
private boolean R;
private Rect S;
private Rect T;
private AppCompatViewInflater U;
final Context b;
final Window c;
final Window.Callback d;
final Window.Callback e;
final android.support.v7.app.b f;
ActionBar g;
MenuInflater h;
android.support.v7.view.b i;
ActionBarContextView j;
PopupWindow k;
Runnable l;
boolean o;
boolean p;
boolean q;
boolean r;
boolean s;
boolean t;
boolean u;
int v;
private CharSequence z;
android.support.v4.view.t m = null;
boolean n = true;
private int N = -100;
private final Runnable Q = new Runnable() { // from class: android.support.v7.app.AppCompatDelegateImpl.2
{
AppCompatDelegateImpl.this = this;
}그리고 해당 악성코드에 포함된 인터넷 주소들은 다음과 같습니다.
http://121.40.46(.)187:8000/web_feedback_wallpaper/feedback/reply.php
http://schemas.android(.)com/apk/res/android
http://www.w3(.)org/ns/ttml#parameter
https://app-measurement(.)com/a
https://firebase.corp.google(.)com/u/0/project/_/overview?purchaseBillingPlan=true
https://google(.)com/search?
https://mlkit.googleapis(.)com/_i/v1/1p/m?n=%s
https://mlkit.googleapis(.)com/v1beta1/projects/%s/models/%s/versions/active?key=%s&app_instance_id=%s&app_instance_token=%s
https://play.google(.)com/store/apps/details?id=
https://plus.google(.)com/
https://vision.googleapis(.)com/
https://www.google(.)com
https://www.googleadservices(.)com/pagead/conversion/app/deeplink?id_type=adid&sdk_version=%s&rdid=%s&bundleid=%s
https://www.googleapis(.)com/auth/appstate
https://www.googleapis(.)com/auth/datastoremobile
https://www.googleapis(.)com/auth/drive
https://www.googleapis(.)com/auth/drive.appdata
https://www.googleapis(.)com/auth/drive.apps
https://www.googleapis(.)com/auth/drive.file
https://www.googleapis(.)com/auth/fitness.activity.read
https://www.googleapis(.)com/auth/fitness.activity.write
https://www.googleapis(.)com/auth/fitness.blood_glucose.read
https://www.googleapis(.)com/auth/fitness.blood_glucose.write
https://www.googleapis(.)com/auth/fitness.blood_pressure.read
https://www.googleapis(.)com/auth/fitness.blood_pressure.write
https://www.googleapis(.)com/auth/fitness.body.read
https://www.googleapis(.)com/auth/fitness.body.write
https://www.googleapis(.)com/auth/fitness.body_temperature.read
https://www.googleapis(.)com/auth/fitness.body_temperature.write
https://www.googleapis(.)com/auth/fitness.location.read
https://www.googleapis(.)com/auth/fitness.location.write
https://www.googleapis(.)com/auth/fitness.nutrition.read
https://www.googleapis(.)com/auth/fitness.nutrition.write
https://www.googleapis(.)com/auth/fitness.oxygen_saturation.read
https://www.googleapis(.)com/auth/fitness.oxygen_saturation.write
https://www.googleapis(.)com/auth/fitness.reproductive_health.read
https://www.googleapis(.)com/auth/fitness.reproductive_health.write
https://www.googleapis(.)com/auth/games
https://www.googleapis(.)com/auth/games.firstparty
https://www.googleapis(.)com/auth/games_lite
https://www.googleapis(.)com/auth/plus.login
https://www.googleapis(.)com/auth/plus.me입니다. 그리고 DEX 는 4개가 존재하고 있고 각각의 해쉬값은 다음과 같습니다.
Dex File Name:classes.dex
File Size:8041172 bytes
MD5:8cb43b13f6fb169f7d72bb52f4235b19
Class Size:7858
Method Size:56141
String Size:42767
Dex File Name:classes2.dex
File Size:3476104 bytes
MD5:eae394ba410284671e1b35e5b1707fa5
Class Size: 3378
Method Size:22360
String Size:21674
Dex File Name:classes3.dex
File Size:720996 bytes
MD5:73a16440bbc35cf7815e975a5fc5c6cd
Class Size:643
Method Size:5211
String Size:8702
Dex File Name:classes4.dex
File Size:1229000 bytes
MD5:0eb63fe2800e9a193a6589118713acc5
Class Size:1171
Method Size:10169
String Size:11934
패키지 이름은 com.glow.camera.open
Main Activity:com.glow.camera.main.privacy.CameraPrivacyActivity
입니다.
그리고 해당 악성코드 인증서 정보는 다음과 같습니다.
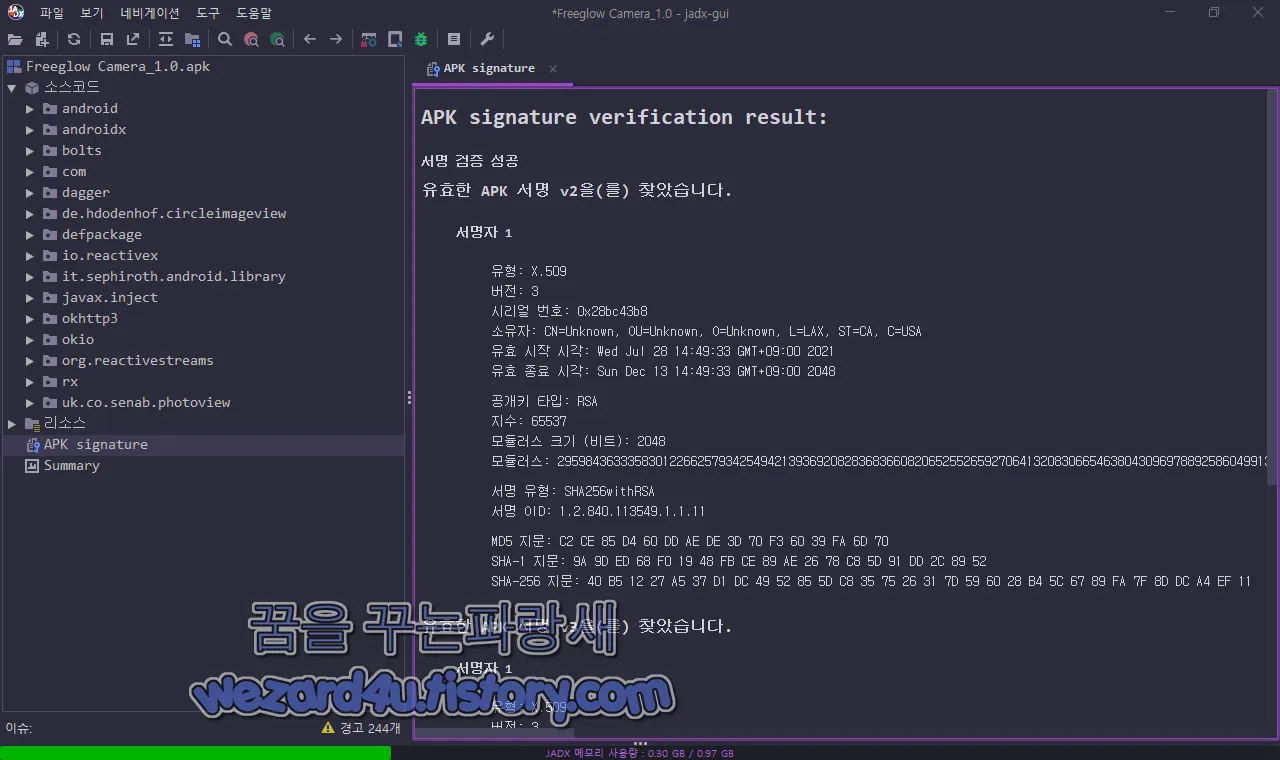
유효한 APK 서명 v2을(를) 찾았습니다.
서명자 1
유형: X.509
버전: 3
시리얼 번호: 0x28bc43b8
소유자: CN=Unknown, OU=Unknown, O=Unknown, L=LAX, ST=CA, C=USA
유효 시작 시각: Wed Jul 28 14:49:33 GMT+09:00 2021
유효 종료 시각: Sun Dec 13 14:49:33 GMT+09:00 2048
공개키 타입: RSA
지수: 65537
모듈러스 크기 (비트): 2048
모듈러스: 29598436333583012266257934254942139369208283683660820652552659270641320830665463804309697889258604991312523657086374052866732485967957161467342555078983952769597534614627273766620642097085058093002125711106584126426237486908515999098614525711552490249624524168053775942935072785655322361706231075764421332611055721906767461547879095026310163353847752095388685644667123515399243435052341588431613618977708416177444589086692211072665163515231790980496096734636371432282819254997108699197907835559518455106343751095099258722699121147345620892842546703659324958020788968569750392457567752876421122914740329752769630485689
서명 유형: SHA256withRSA
서명 OID: 1.2.840.113549.1.1.11
MD5 지문: C2 CE 85 D4 60 DD AE DE 3D 70 F3 60 39 FA 6D 70
SHA-1 지문: 9A 9D ED 68 F0 19 48 FB CE 89 AE 26 78 C8 5D 91 DD 2C 89 52
SHA-256 지문: 40 B5 12 27 A5 37 D1 DC 49 52 85 5D C8 35 75 26 31 7D 59 60 28 B4 5C 67 89 FA 7F 8D DC A4 EF 11입니다.
그리고 VirusTotal(바이러스트 토탈) 에서 2022-07-17 08:49:56 UTC 기준으로 탐지 하고 있는 보안 업체들은 다음과 같습니다.
AhnLab-V3:Trojan/Android.Joker.1024423
Alibaba:Trojan:Android/Agent.e030e854
Avira (no cloud):ANDROID/Agent.kvslp
BitDefenderFalx:Android.Riskware.Joker.XA
ESET-NOD32:Android/Agent.DIY
F-Secure:Malware.ANDROID/Agent.kvslp
Kaspersky:HEUR:Trojan.AndroidOS.Piom.apnu
McAfee:Artemis!8CB43B13F6FB
McAfee-GW-Edition:Artemis!Trojan
Rising:Trojan.Agent/Android!8.358 (CLOUD)
Symantec Mobile Insight:AppRisk:Generisk
Tencent:A.expense.Autolycos
ZoneAlarm by Check Point:HEUR:Trojan.AndroidOS.Piom.apnu
이며 대부분 정상적인 탐지명 과 그리고 사전 방역 기능으로 탐지하고 있습니다. 안드로이드 스마트폰 사용자 분들은 기본적으로 신뢰할 수 있는 백신 앱을 설치를 해서 사용을 하시길 바랍니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 구글 캘린더(구글 달력) 스팸 방지 기능 활성화 방법 (0) | 2022.07.24 |
|---|---|
| 윈도우 11 파일 탐색기 멈추게 하는 버그 수정 KB5015882 업데이트 (0) | 2022.07.23 |
| 구글 안드로이드 DNS-over-HTTP/3 지원을 통한 개인정보 강화 (2) | 2022.07.22 |
| 페이스북 계정 을 훔치는 악성코드-Vanilla Camera(바닐라 카메라) (2) | 2022.07.21 |
| 토르 브라우저(Tor Browser)새로운 기능 연결 지원 추가 (0) | 2022.07.18 |
| 윈도우 8.1 전체 화면 에 기술 지원 종료 알림 경고 표시 (2) | 2022.07.14 |
| 구글 플레이 스토어 에서 유포 되고 있는 악성코드-Advanced SMS(2022.07.12) (0) | 2022.07.14 |
| AMD 및 인텔 새로운 Retbleed 새로운 오버헤드 있을수 있음 (0) | 2022.07.13 |





