모질라 파이어폭스 70(Firefox 70) 보안 업데이트 및 개인정보 강화 업데이트 모질라에서 제공을 하는 웹 브라우저인 파이어폭스에 대해서 보안 업데이트 및 개인정보기능들이 강화되었습니다.
이번 보안 업데이트 내용은 다음과 같습니다.
CVE-2018-6156: Heap buffer overflow in FEC processing in WebRTC
Description:Incorrect derivation of a packet length in WebRTC caused heap corruption via a crafted video file.
This resulted in a potentially exploitable crash.
CVE-2019-15903: Heap overflow in expat library in XML_GetCurrentLineNumber
Description:In libexpat before 2.2.8, crafted XML input could fool the parser into changing from DTD parsing to document parsing too early.
A subsequent call to XML_GetCurrentLineNumber or XML_GetCurrentColumnNumber
then resulted in a heap-based buffer over-read.
CVE-2019-11757: Use-after-free when creating index updates in IndexedDB
Description:When storing a value in IndexedDB, the value's prototype chain is followed and it was possible to retain a reference to a locale
delete it, and subsequently reference it.
This resulted in a use-after-free and a potentially exploitable crash.
CVE-2019-11759: Stack buffer overflow in HKDF output
Description:An attacker could have caused 4 bytes of
HMAC output to be written past the end of a buffer stored on the stack.
This could be used by an attacker to execute arbitrary code or more likely lead to a crash.
CVE-2019-11760: Stack buffer overflow in WebRTC networking
Description:A fixed-size stack buffer could overflow in nrappkit when doing WebRTC signaling.This resulted in a potentially exploitable crash in some instances.
CVE-2019-11761: Unintended access to a privileged JSONView object

Description:By using a form with a data URI it was possible to gain access to
the privileged JSONView object that had been cloned into content.
Impact from exposing this object appears to be minimal, however it was a bypass of existing defense in depth mechanisms.
CVE-2019-11762: document.domain-based origin isolation has same-origin-property violation
Description:If two same-origin documents set document.domain differently to become cross-origin, it was possible for them to call arbitrary DOM methods/getters/setters on the now-cross-origin window.
CVE-2019-11763: Incorrect HTML parsing results in XSS bypass technique
Description:Failure to correctly handle null bytes when processing HTML entities resulted in Firefox incorrectly parsing these entities.
This could have led to HTML comment text being treated as HTML
which could have led to XSS in a web application under certain conditions.
It could have also led to HTML entities being masked from filters,
enabling the use of entities to mask the actual characters of interest from filters.
CVE-2019-11765: Incorrect permissions could be granted to a website
Description:A compromised content process could send a message to
the parent process that would cause the 'Clickto Play' permission prompt to be shown.
However, due to lack of validation from the parent process,
if the user accepted the permission request an attacker-controlled permission would be granted rather than the 'Click to Play' permission.
CVE-2019-17000: CSP bypass using object tag with data: URI
Description:An object tag with a data URI did not correctly inherit the document's Content Security Policy.
This allowed a CSP bypass in a cross-origin frame if the document's policy explicitly allowed data: URIs.
CVE-2019-17001: CSP bypass using object tag when script-src 'none' is specified
Description:A Content-Security-Policy that blocks in-line scripts could be bypassed using an object tag to execute JavaScript in the protected document (cross-site scripting). This is a separate bypass from CVE-2019-17000
Note: This flaw only affected Firefox 69 and was not present in earlier versions.
CVE-2019-17002: upgrade-insecure-requests was not being honored for
links dragged and dropped
Description:If upgrade-insecure-requests was specified in the Content Security Policy
and a link was dragged and dropped from that page, the link was not upgraded to https.

CVE-2019-11764: Memory safety bugs fixed in Firefox 70 and Firefox ESR 68.2
Description:Mozilla developers and community members Bob Clary, Jason Kratzer, Aaron Klotz, Iain Ireland, Tyson Smith, Christian Holler, Steve Fink, Honza Bambas
Byron Campen, and Cristian Brindusan reported memory safety bugs present in
Firefox 69 and Firefox ESR 68.1. Some of these bugs showed evidence of memory corruption and
we presume that with enough effort some of these could be exploited to run arbitrary code.
Memory safety bugs fixed in Firefox 70 and Firefox ESR 68.2
입니다. 그리고 미국 시각 2019년 10월 22일 2019년7 월에 도입하고 9월에 기본이 설정된 Enhanced Tracking Protection 기능 (향상된 버전의 추적 방지 기능)이 추적 요청을 총 4,500억여 건 추적을 중지할 수가 있습니다.
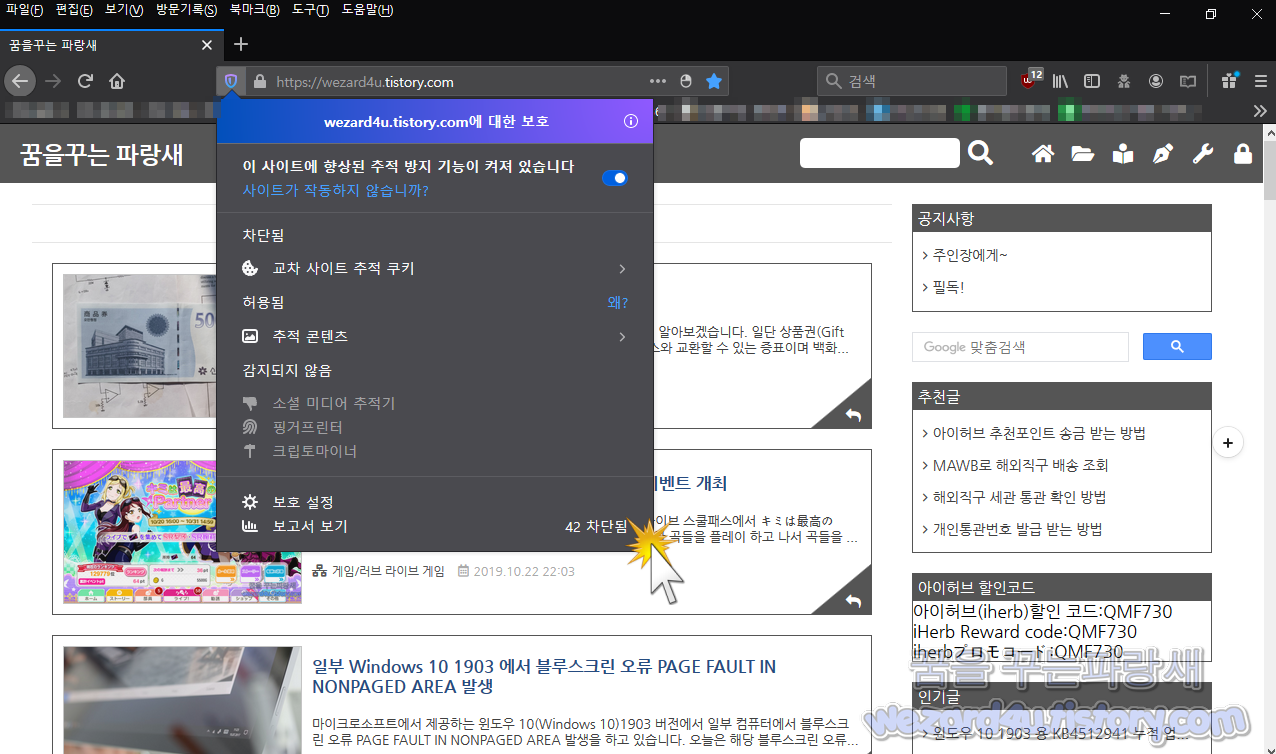
Mozilla는 Firefox 70에서 개인 정보 개인 대시 보드도 기본적으로 제공됩니다. 해당 대시보드를 통해서 Firefox 브라우저에서 타사 Cookie(쿠키), 소셜 미디어 추적기, Fingerprinting 도구(각종 사용자 정보를 수집하는 도구) 가상화폐채굴도구 등이 얼마나 추적 및 차단을 했는지 알 수가 있습니다. 일단 기본적으로 해당 기능은 설정돼 있으며 표준이 아닌 엄격으로 변경하면 일부 웹사이트를 이용하는데 불편을 느낄 수가 있습니다. 개인정보 강화를 하고 싶은 분들은 해당 기능을 엄격으로 변경해서 사용하시면 됩니다.
해당 대시보드 차단 보고서를 보고 싶은 경우 URL 표시(인터넷 주소창)의 방패 아이콘을 클릭해줍니다. 그리고서 보고서 보기를 클릭을 해주면 파이어폭스가 어떤 종류의 추적기능을 차단했는지 그리고 얼마나 차단했습니다. 쉽게 눈으로 확인할 수가 있습니다. 그러면 지금 보는 사이트에 대한 정보와 사용자의 개인 정보 보고서에 대한 링크가 표시될 것입니다. 해당 보고서는 최소한의 항목뿐만 게다가 최근 1주일 뿐이 결과를 표시합니다.
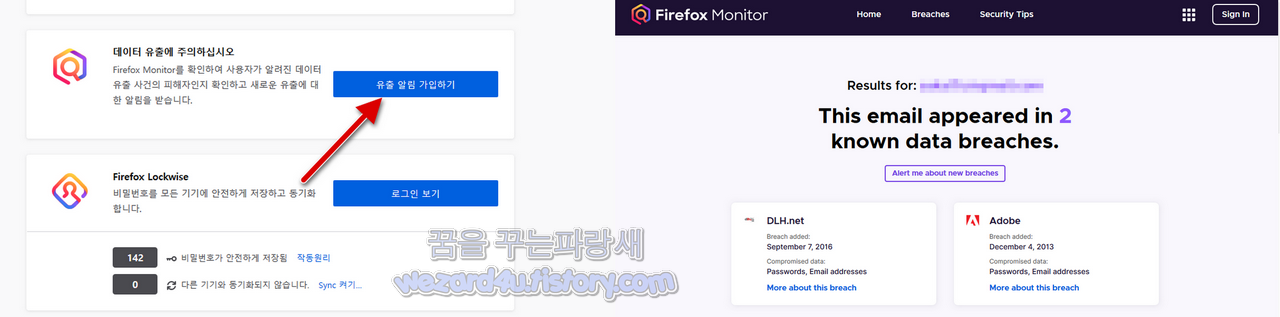
보고서 페이지는 Mozilla의 Firefox Monitor에 대한 링크도 있다. 그것은 이상한 사이트 나 페이지에 사용자의 이메일 계정이 발견되면 경고한다. 또한, 암호 관리 및 동기화 서비스 Lockwise에 대한 링크도 있다. Lockwise 암호 생성 기능과 Firefox Monitor와의 통합 기능도 있다. 간단하게 이메일 주소를 입력을 해주면 어느 사이트에서 어떤 정보가 노출되었는지를 확인을 할 수가 있습니다. 일단 파이어폭스를 사용하고 계시는 분들은 해당 기능을 통해서 개인정보들을 더욱더 쉽게 관리할 수가 있을 것입니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| Windows 10 1903 장치를 재설정하고 다시 시도 오류 해결 방법 (7) | 2019.11.05 |
|---|---|
| VeraCrypt(베라크립트)1.24 Hotfix1 업데이트 (4) | 2019.10.31 |
| 구글 크롬 앗 이런!(Aw, Snap!) 오류 해결 방법 (4) | 2019.10.25 |
| Windows 10 1903 (윈도우 10 1903)용 KB4522355 누적 업데이트 (0) | 2019.10.25 |
| 일부 Windows 10 1903 에서 블루스크린 오류 PAGE FAULT IN NONPAGED AREA 발생 (6) | 2019.10.22 |
| Adobe Acrobat 및 Adobe Reader 2019.008.20071 보안 업데이트 (0) | 2019.10.17 |
| 윈도우 10 1903 Tamper Protection(임의 변경 방지 기능)을 사용을 방법 (8) | 2019.10.17 |
| Windows 10 1703(윈도우 10 1703)버전 서비스 종료 (8) | 2019.10.16 |





