오늘은 VPN 앱 으로 위장하는 악성코드인 SecureVPN_108.apk에 대해 글을 적어 보겠습니다. VPN이라는 것은 자신의 국가에서 다른 서비스를 이용하고 싶거나 아니면 넷플릭스 같은 곳에서 다른 국가에서 서비스되고 있는 넷플릭스 서비스 등을 이용하고 싶으면 이런 VPN 서비스를 이용합니다. 그런데 이런 VPN 서비스도 인지도가 있는 서비스를 이용해야지 문제가 되지 않지만, 무료 VPN 들은 개인정보를 가져가는 데 이용이 됩니다. 오늘은 이런 VPN 서비스를 제공하는 척하면서 개인정보를 가져가는 악성코드에 대해 글을 적어 보겠습니다.
먼저 해당 악성코드의 해쉬값은 다음과 같습니다.
파일명:SecureVPN_108.apk
사이즈:31.5 MB
CRC32:ed8f5960
MD5:a45ec8749eac7e1e7e194275a25e9ef1
SHA-1:bc48b53101a4cb4d97299f57c461058e8dce0522
SHA-256:f38e9e7214579fbf57dd8ceda1c6ddc4fe5fdcc1a61310613beeb1cd1f3e0358
그리고 해당 악성코드의 안드로이드 권한은 다음과 같습니다.
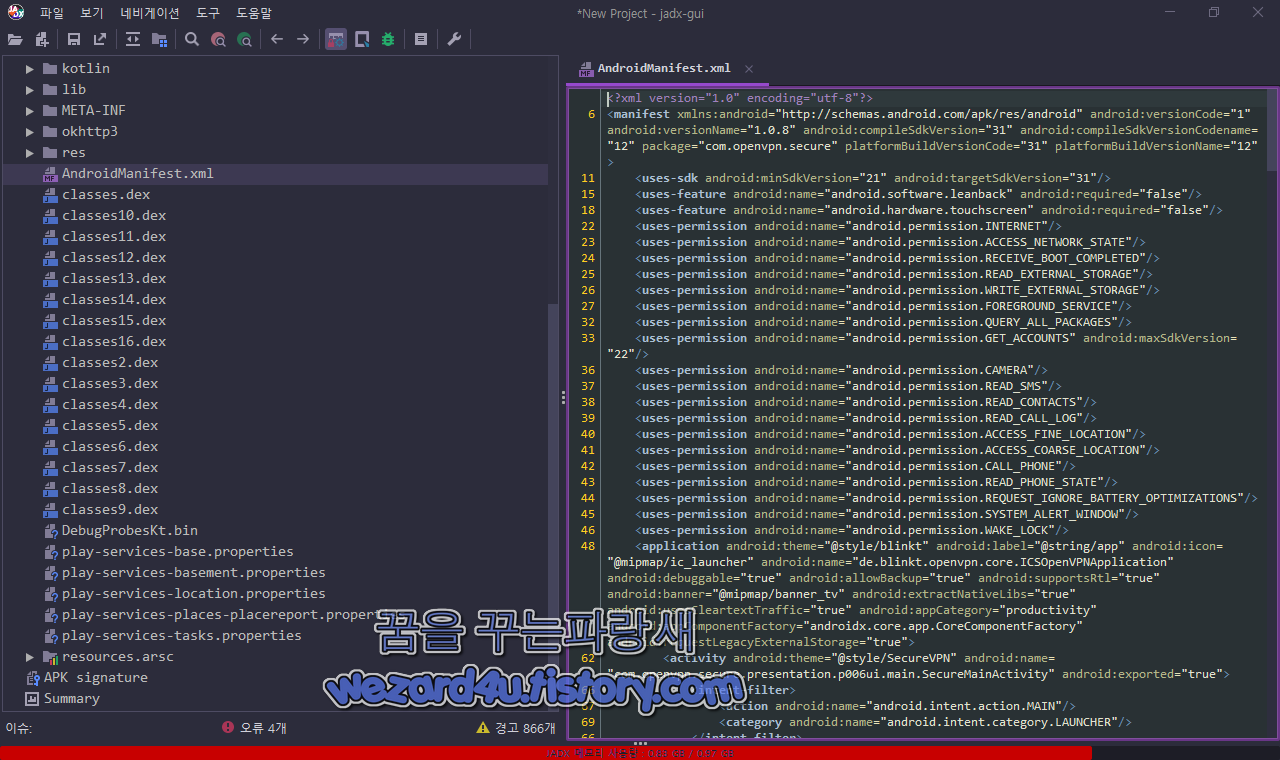
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.FOREGROUND_SERVICE"/>
<uses-permission android:name="android.permission.QUERY_ALL_PACKAGES"/>
<uses-permission android:name="android.permission.GET_ACCOUNTS" android:maxSdkVersion="22"/>
<uses-permission android:name="android.permission.CAMERA"/>
<uses-permission android:name="android.permission.READ_SMS"/>
<uses-permission android:name="android.permission.READ_CONTACTS"/>
<uses-permission android:name="android.permission.READ_CALL_LOG"/>
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"/>
<uses-permission android:name="android.permission.CALL_PHONE"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS"/>
<uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW"/>
<uses-permission android:name="android.permission.WAKE_LOCK"/>보시면 문자 읽기 및 문자 쓰기, 위치 확인, 스마트폰 카메라 접근, 인터넷 연결 등 개인정보에 접근하는 것을 볼 수가 있습니다.
DEX 파일은 총 16개 존재하고 있습니다.
Dex File Name:classes.dex
File Size:10595544 bytes
MD5:5c253eb2bf974ae9f7e6576df5ec15bf
Class Size: 7112
Method Size:65312
String Size:74438
Dex File Name:classes2.dex
File Size:378524 bytes
MD5:5d5a5d26f103cf41159a4450672a4281
Class Size: 235
Method Size:1810
String Size:3036
Dex File Name:classes3.dex
File Size:767964 bytes
MD5:0e39b4375b1556cf410bd9096086bf78
Class Size: 487
Method Size:529
String Size:7192
Dex File Name:classes4.dex
File Size:2136 bytes
MD5:bd067ef19adc9537671b49c5236dc46d
Class Size: 1
Method Size:12
String Size:44
Dex File Name:classes5.dex
File Size:71404 bytes
MD5:6003b2dfd30dfe98011f01a6ad53e5a7
Class Size:45
Method Size:598
String Size:968
Dex File Name:classes6.dex
File Size:128384 bytes
MD5:1d9907049ce55b4f856721b49b210ec4
Class Size:68
Method Size:984
String Size:1755
Dex File Name:classes7.dex
File Size:6528 bytes
MD5:76448c45e817d73ec4915ff6f0b70de4
Class Size:6
Method Size:57
String Size:124
Dex File Name:classes8.dex
File Size:59424 bytes
MD5:1924566640e69a5443a40f8877246ad0
Class Size:18
Method Size:404
String Size:1069
Dex File Name:classes9.dex
File Size:4384 bytes
MD5:0b878cd39dd418202ed29baa7a2aacbc
Class Size:3
Method Size:24
String Size:84
Dex File Name:classes10.dex
File Size:204272 bytes
MD5:d0020d2e071af0d2bbfdca246050dea9
Class Size:133
Method Size:1550
String Size:2578
Dex File Name:classes11.dex
File Size:210064 bytes
MD5:d6cff59260fb2fc9efe06808c7c095a9
Class Size:102
Method Size:1531
String Size:3089
Dex File Name:classes12.dex
File Size:78364 bytes
MD5:ea6a958d644e08e40b7aa6d798756ec2
Class Size:32
Method Size:1042
String Size:1046
Dex File Name:classes13.dex
File Size:22908 bytes
MD5:f03665ad94f9802e37329f6f7f810458
Class Size:17
Method Size:151
String Size:348
Dex File Name:classes14.dex
File Size:51720 bytes
MD5:500f72090c0a4357807ab93de3c5084b
Class Size:50
Method Size:303
String Size:402
Dex File Name:classes15.dex
File Size:6800 bytes
MD5:bc9fa48123ff5c52eac3b78c65dd2fb8
Class Size:4
Method Size:50
String Size:104
Dex File Name:classes16.dex
File Size:2641516 bytes
MD5:19af60fe58b2e0d6870a94a3620b7e12
Class Size:1547
Method Size:11186
String Size:18949
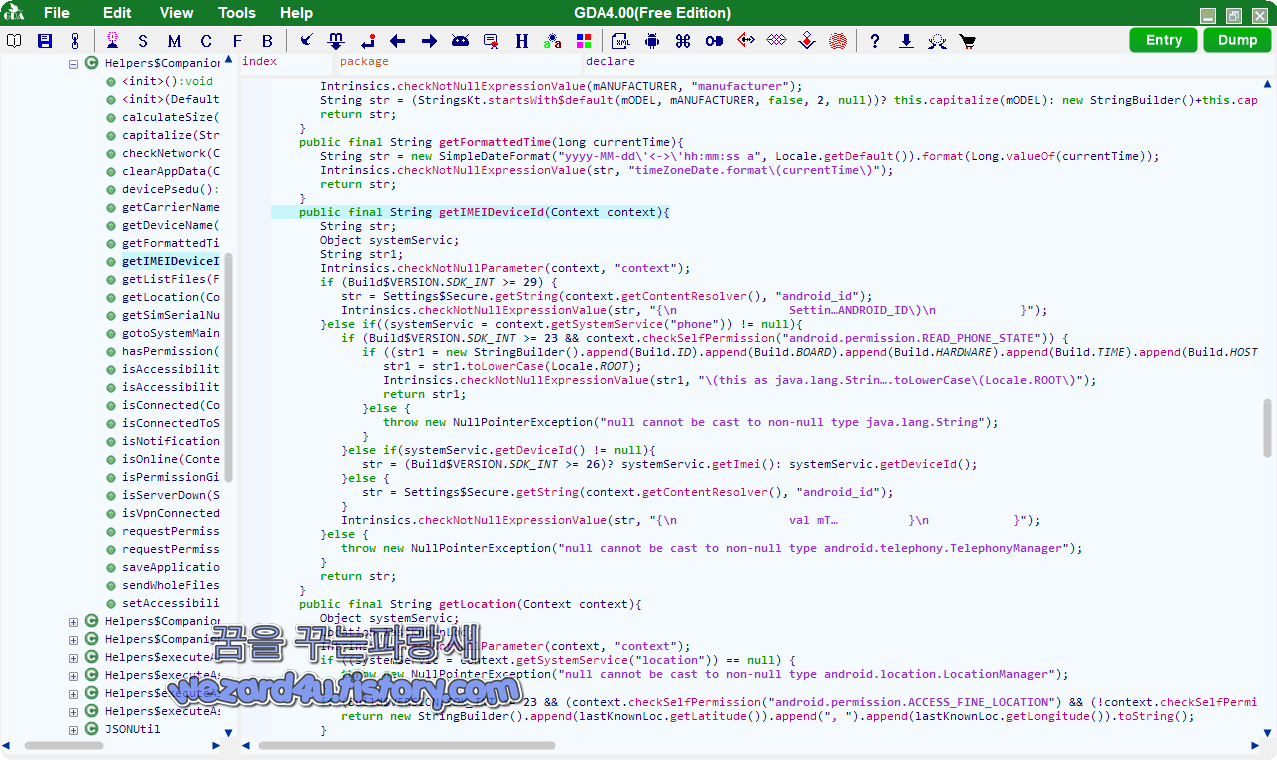
그리고 IMEI 관련 코드는 다음과 같습니다.
public final String getIMEIDeviceId(Context context){
String str;
Object systemServic;
String str1;
Intrinsics.checkNotNullParameter(context, "context");
if (Build$VERSION.SDK_INT >= 29) {
str = Settings$Secure.getString(context.getContentResolver(), "android_id");
Intrinsics.checkNotNullExpressionValue(str, "{\n Settin…ANDROID_ID\)\n }");
}else if((systemServic = context.getSystemService("phone")) != null){
if (Build$VERSION.SDK_INT >= 23 && context.checkSelfPermission("android.permission.READ_PHONE_STATE")) {
if ((str1 = new StringBuilder().append(Build.ID).append(Build.BOARD).append(Build.HARDWARE).append(Build.TIME).append(Build.HOST).toString()) != null) {
str1 = str1.toLowerCase(Locale.ROOT);
Intrinsics.checkNotNullExpressionValue(str1, "\(this as java.lang.Strin….toLowerCase\(Locale.ROOT\)");
return str1;
}else {
throw new NullPointerException("null cannot be cast to non-null type java.lang.String");
}
}else if(systemServic.getDeviceId() != null){
str = (Build$VERSION.SDK_INT >= 26)? systemServic.getImei(): systemServic.getDeviceId();
}else {
str = Settings$Secure.getString(context.getContentResolver(), "android_id");
}
Intrinsics.checkNotNullExpressionValue(str, "{\n val mT… }\n }");
}else {
throw new NullPointerException("null cannot be cast to non-null type android.telephony.TelephonyManager");
}
return str;
}유심 수집 관련은 다음과 같습니다.
public final String getSimSerialNumber(Context context){
SubscriptionManager subscription;
List activeSubscr;
Intrinsics.checkNotNullParameter(context, "context");
if (context.getSystemService("phone") == null) {
throw new NullPointerException("null cannot be cast to non-null type android.telephony.TelephonyManager");
}
if (ActivityCompat.checkSelfPermission(context, "android.permission.READ_PHONE_STATE")) {
return "";
}
if ((subscription = SubscriptionManager.from(context)) != null && (activeSubscr = subscription.getActiveSubscriptionInfoList()) != null) {
SubscriptionInfo subscription1 = activeSubscr.get(0);
String iccId = subscription1.getIccId();
subscription1.getNumber();
if (iccId != null) {
return iccId;
}
}
return "";
}그리고 악성코드 인증서 관련 정보는 다음과 같습니다.
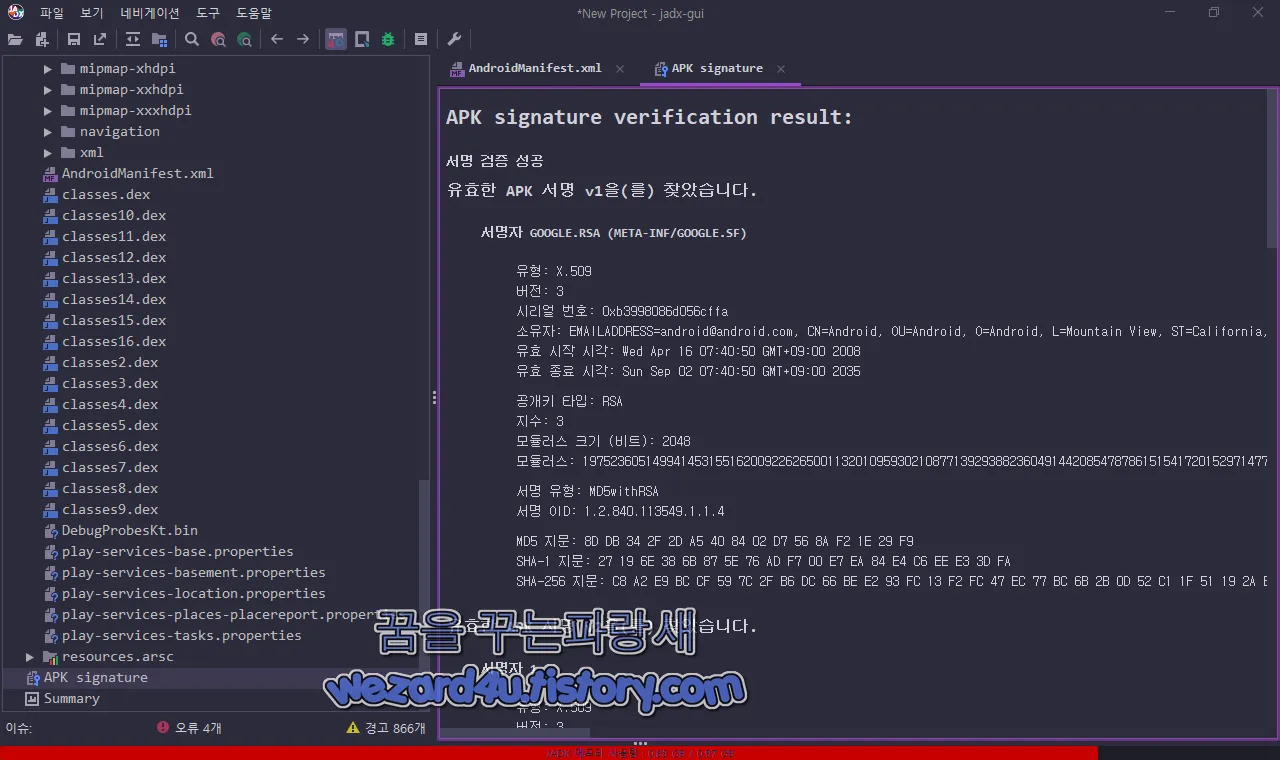
서명자 GOOGLE.RSA (META-INF/GOOGLE.SF)
유형: X.509
버전: 3
시리얼 번호: 0xb3998086d056cffa
소유자: EMAILADDRESS=android@android.com, CN=Android, OU=Android, O=Android, L=Mountain View, ST=California, C=US
유효 시작 시각: Wed Apr 16 07:40:50 GMT+09:00 2008
유효 종료 시각: Sun Sep 02 07:40:50 GMT+09:00 2035
공개키 타입: RSA
지수: 3
모듈러스 크기 (비트): 2048
모듈러스: 19752360514994145315516200922626500113201095930210877139293882360491442085478786151541720152971477143983881863321664523422547611110099273765224120568364777034650912678907821093580890163251737414924719328467952497043183923122387299431695133597891714742890183331347183051675551539479800577268863336014071199303706368639398312068986268364026599287186671128600025042565642878806622080419423130708573166425292783829265431121684947027209494790403079505375733937016316815543438173887549948849561798979965946715421653838315942924851269843940189181281036840618385212605258797972686986149267500613535276192842406091462405965863
서명 유형: MD5withRSA
서명 OID: 1.2.840.113549.1.1.4
MD5 지문: 8D DB 34 2F 2D A5 40 84 02 D7 56 8A F2 1E 29 F9
SHA-1 지문: 27 19 6E 38 6B 87 5E 76 AD F7 00 E7 EA 84 E4 C6 EE E3 3D FA
SHA-256 지문: C8 A2 E9 BC CF 59 7C 2F B6 DC 66 BE E2 93 FC 13 F2 FC 47 EC 77 BC 6B 2B 0D 52 C1 1F 51 19 2A B8
유효한 APK 서명 v2을(를) 찾았습니다.
서명자 1
유형: X.509
버전: 3
시리얼 번호: 0xb3998086d056cffa
소유자: EMAILADDRESS=android@android.com, CN=Android, OU=Android, O=Android, L=Mountain View, ST=California, C=US
유효 시작 시각: Wed Apr 16 07:40:50 GMT+09:00 2008
유효 종료 시각: Sun Sep 02 07:40:50 GMT+09:00 2035
공개키 타입: RSA
지수: 3
모듈러스 크기 (비트): 2048
모듈러스: 19752360514994145315516200922626500113201095930210877139293882360491442085478786151541720152971477143983881863321664523422547611110099273765224120568364777034650912678907821093580890163251737414924719328467952497043183923122387299431695133597891714742890183331347183051675551539479800577268863336014071199303706368639398312068986268364026599287186671128600025042565642878806622080419423130708573166425292783829265431121684947027209494790403079505375733937016316815543438173887549948849561798979965946715421653838315942924851269843940189181281036840618385212605258797972686986149267500613535276192842406091462405965863
서명 유형: MD5withRSA
서명 OID: 1.2.840.113549.1.1.4
MD5 지문: 8D DB 34 2F 2D A5 40 84 02 D7 56 8A F2 1E 29 F9
SHA-1 지문: 27 19 6E 38 6B 87 5E 76 AD F7 00 E7 EA 84 E4 C6 EE E3 3D FA
SHA-256 지문: C8 A2 E9 BC CF 59 7C 2F B6 DC 66 BE E2 93 FC 13 F2 FC 47 EC 77 BC 6B 2B 0D 52 C1 1F 51 19 2A B8
2022-04-19 01:37:06 UTC 바이러스토탈(VirusTotal)에서 탐지하는 백신 프로그램들은 다음과 같습니다.
Alibaba:TrojanSpy:Android/Agent.c758ee5f
Avast-Mobile:APK:RepMalware [Trj]
Avira (no cloud):ANDROID/Spy.Agent.bczlm
BitDefenderFalx:Android.Trojan.SpyAgent.EW
DrWeb:Android.Spy.988.origin
ESET-NOD32:A Variant Of Android/Spy.Agent.BTS
F-Secure:Malware.ANDROID/Spy.Agent.bczlm
Fortinet:Android/Agent.BTS!tr.spy
K7GW:Spyware ( 005882201 )
Kaspersky:HEUR:Trojan-Spy.AndroidOS.Agent.abe
Lionic:Trojan.AndroidOS.Agent.C!c
McAfee:Artemis!5D5A5D26F103
McAfee-GW-Edition:Artemis!Trojan
Microsoft:Trojan:Script/Wacatac.B!ml
Sophos:Andr/Spy-BHC
Symantec:Trojan.Gen.2
Symantec Mobile Insight:AdLibrary:Generisk
Tencent:Android.Trojan-spy.Agent.Lkxi
ZoneAlarm by Check Point:HEUR:Trojan-Spy.AndroidOS.Agent.abe
입니다. 일단 기본적으로 백신앱은 기본적으로 설치하고 특히 구글 플레이스토어 또는 원스토어, 갤럭시 스토어등 기본적으로 공식 스토어가 아닌 곳에서는 앱을 다운로드 및 설치하는 것은 위험한 행동입니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 악성코드 및 랜섬웨어 유포 행위 브라우저 차단 규칙 만드는 방법 (2) | 2022.05.26 |
|---|---|
| 신한은행 보이스피싱앱-sinhan.apk (2) | 2022.05.25 |
| 구글 크롬 브라우저에 저장된 비밀번호 내보내기 (0) | 2022.05.24 |
| 모질라 파이어폭스 긴급 보안 업데이트 (0) | 2022.05.23 |
| 윈도우 11 KB5013943 업데이트 시 블루스크린 등 해결 방법 (0) | 2022.05.13 |
| 윈도우 KB5013942 및 KB5013945 Windows 11 KB5013943 보안 업데이트 (0) | 2022.05.12 |
| 파이어폭스 100(Firefox 100) 보안 업데이트 (6) | 2022.05.06 |
| 파이어폭스 100 새로운 기능 추가 (4) | 2022.05.04 |





