오늘은 스마트폰에 있는 자기장 센서를 이용해서 해당 철 같은 금속이 있을 때 사용을 할 수가 있는 앱들입니다.
기본적으로 해당 악성코드 설명은 다음과 같습니다.
실시간 금속 탐지로 해당 영역의 금속 물체를 식별합니다.
"스마트 금속탐지기는 자기장 값을 측정하여 주변에 금속이 있는지 감지합니다. 이 애플리케이션이 제대로 작동하지 않으면 장치의 사양을 확인하세요. >>
이 앱은 내장된 자기 센서를 사용하여 자기장을 측정합니다. (스터드 파인더와 같은) 벽에서 와이어를 찾을 수 있고 땅에서 철 파이프를 찾을 수 있습니다.
사용법은 간단합니다. 앱을 열고 이동하세요. 자기장 수준은 지속적으로 변동합니다. 그게 다야!
정확도는 전적으로 자기 센서(자력계)에 따라 달라집니다. 전자파로 말미암아 전자기기(TV, PC, 전자레인지)의 영향을 받을 수 있으니 유의하시기 바랍니다."
개발자를 보면 XIE ZHAO MING 말 안 해도 어디인지 알 수가 있을 것입니다. 유포 주소는 다음과 같습니다. 물론 해당 어플은 삭제 조치당했습니다.


https://play.google(.)com/store/apps/details?id=com.smart.metal.sira.detectorJocker(조커) 악성코드입니다.
그리고 악성코드 해쉬값은 다음과 같습니다.
파일명:Smart Metal Detector.apk
사이즈:5.76 MB
CRC32:41e25260
MD5:da4ff31b0fe110ccc15efa0d3ec0e1c9
SHA-1:f48ce6a31dbf6dc13141697bb9f01cd4e232ac88
SHA-256:90d85338b1b62a83118842bfc0fdd5466edec9d14d4a6c00a2993b3428825fa5
일단 해당 악성코드를 실행하면 다음과 같이 권한을 요청하고 실행을 하면 일단 금속 탐지기 앱 담게 동작은 하는 것을 볼 수가 있습니다. 그리고 안드로이드 악성코드는 권한은 다음과 같은 권한을 요구합니다.

<uses-feature android:name="android.hardware.sensor.compass" android:required="true"/>
<uses-feature android:name="android.hardware.touchscreen" android:required="false"/>
<uses-feature android:name="android.hardware.screen.landscape" android:required="false"/>
<uses-permission android:name="android.permission.VIBRATE"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.REQUEST_DELETE_PACKAGES"/>
<uses-permission android:name="android.permission.CHANGE_NETWORK_STATE"/>
<supports-screens android:anyDensity="true" android:smallScreens="true" android:normalScreens="true" android:largeScreens="true" android:resizeable="true" android:xlargeScreens="true"/>
<queries>
<package android:name="com.google.android.youtube"/>
<intent>
<action android:name="android.intent.action.VIEW"/>
<category android:name="android.intent.category.BROWSABLE"/>
<data android:scheme="https"/>
</intent>
<intent>
<action android:name="android.support.customtabs.action.CustomTabsService"/>
</intent>
</queries>
<uses-permission android:name="android.permission.WAKE_LOCK"/>
<uses-permission android:name="com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE"/>
<uses-permission android:name="com.google.android.gms.permission.AD_ID"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.FOREGROUND_SERVICE"/>
<permission android:name="com.smart.metal.sira.detector.DYNAMIC_RECEIVER_NOT_EXPORTED_PERMISSION" android:protectionLevel="signature"/>
<uses-permission android:name="com.smart.metal.sira.detector.DYNAMIC_RECEIVER_NOT_EXPORTED_PERMISSION"/>
<application android:theme="@android:style/Theme.NoTitleBar.Fullscreen" android:label="0x7f11001d" android:icon="0x7f0e0000" android:name="androidx.multidex.MultiDexApplication" android:allowBackup="true" android:usesCleartextTraffic="true" android:appComponentFactory="androidx.core.app.CoreComponentFactory" android:isSplitRequired="true">
<activity android:theme="0x7f1200fd" android:label="0x7f11001d" android:name="com.smart.metal.sira.detector.Intro" android:exported="true" android:screenOrientation="nosensor">그리고 해당 권한에 대한 설명입니다.
android.permission.VIBRATE: 앱이 진동 기능을 사용할 수 있도록 허용
android.permission.INTERNET: 앱이 인터넷에 접근할 수 있도록 허용
android.permission.ACCESS_NETWORK_STATE: 앱이 네트워크 상태에 대한 정보에 접근할 수 있도록 허용
android.permission.REQUEST_DELETE_PACKAGES: 앱이 다른 패키지를 삭제하는 요청을 보낼 수 있도록 허용
android.permission.CHANGE_NETWORK_STATE: 앱이 네트워크 상태를 변경할 수 있도록 허용
android.permission.WAKE_LOCK: 앱이 화면이 꺼진 상태에서도 실행될 수 있도록 허용
com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE: 앱이 Google Play Store에서 설치를 추적하는 서비스에 바인딩할 수 있도록 허용

com.google.android.gms.permission.AD_ID: 앱이 Google 광고 ID를 사용할 수 있도록 허용
android.permission.RECEIVE_BOOT_COMPLETED: 앱이 장치 부팅이 완료되고 실행될 수 있도록 허용
android.permission.FOREGROUND_SERVICE: 앱이 포그라운드 서비스를 사용할 수 있도록 허용
com.smart.metal.sira.detector.DYNAMIC_RECEIVER_NOT_EXPORTED_PERMISSION: 앱 의 동적 리시버가 외부에 노출되지 않고 시그니처 수준의 보호를 받을 수 있도록 허용하는 사용자 정의 권한
그리고 해당 com.google.ads.mediation.AbstractAdViewAdapter 부분에서는 광고 요청을 생성하는 함수인 buildAdRequest 가 포함이 돼 있으며 AdRequest 객체를 생성하고 반환을 진행합니다.

dRequest.Builder 객체를 생성합니다.
mediationAdRequest에서 생일 정보(getBirthday())를 가져와서 비어 있지 않으면 abuilder.zzb(birthday)를 호출하여 AdRequest에 생일 정보를 추가
mediationAdRequest에서 성별 정보(getGender())를 가져와서 기본 값이 아니면 builder.zzc(gender)를 호출하여 AdRequest에 성별 정보를 추가으면 각 키워드를 builder.addKeyword(str)를 호출하여 AdRequest에 추가
mediationAdRequest가 테스트 상태인지 확인하고 테스트 모드이면 zzay.zzb()와 zzcgo.zzy(context)를 사용하여 테스트 장치 정보를 설정
mediationAdRequest에서 Child-Directed Treatment 설정 정보(taggedForChildDirectedTreatment())를 가져와서 설정되어 있으면 builder.zze
mediationAdRequest에서 키워드 정보(getKeywords())를 가져와서 비어 있지 않음(true) 또는 builder.zze(false)를 호출하여 AdRequest에 Child-Directed Treatment 설정을 추가
mediationAdRequest에서 Designed for Families 설정 정보(isDesignedForFamilies())를 가져와서 설정되어 있고 builder.zzd(true)를 호출하여 AdRequest에 Designed for Families 설정을 추가
AdMobAdapter.class와 buildExtrasBundle(bundle, bundle2)를 사용하여 네트워크 추가 번들(Network Extras Bundle)을 생성하고 builder.addNetworkExtrasBundle()를 호출하여 AdRequest에 추가.
마지막으로 builder.build()를 호출하여 최종적인 AdRequest 객체를 생성하고 반환

androidx.browser.browseractions.BrowserActionsIntent 부분에서는 브라우저 액션 인텐트 핸들러가 있습니다. 그냥 쉽게 이야기하면 안드로이드 앱에서 특정 URL을 열 때 어떤 앱이나 기능을 실행할지를 결정하는 역할을 하며 일반적으로 웹사이트의 인터넷 주소를 열 때 기본적으로는 브라우저 앱이 실행되지만, 브라우저 앱 대신 다른 앱을 실행하거나 특정 작업을 수행하도록 설정하기 위해서 존재
관련 코드는 다음과 같습니다.
androidx.browser.browseractions.BrowserActionsIntent
@NonNull
@RestrictTo({RestrictTo.Scope.LIBRARY})
public static List getBrowserActionsIntentHandlers(@NonNull Context context) {
return context.getPackageManager().queryIntentActivities(new Intent(ACTION_BROWSER_ACTIONS_OPEN, Uri.parse(TEST_URL)), 131072);
}과 같은 코드가 있습니다.
해당 함수는 주어진 Context에서 브라우저 액션을 처리할 수 있는 액티비티들의 목록을 반환
브라우저 액션은 사용자가 특정 URL을 열 때 브라우저 앱 대신 다른 앱의 기능을 실행하도록 하는 기능
함수는 라이브러리 범위에서만 사용되므로 다른 앱에서 직접 호출되지 않음
함수는 Context의 PackageManager를 사용하여 액티비티를 검색
검색에 사용되는 Intent는 ACTION_BROWSER_ACTIONS_OPEN 액션과 TEST_URL을 가진 Intent임
검색 옵션으로는 기본 액티비티만 검색하고 필터 정보를 함께 반환하도록 설정
검색 결과로 액티비티 목록을 List로 반환
이를 통해 브라우저 액션을 처리할 수 있는 액티비티를 확인할 수 있음
androidx.appcompat.app.AppCompatDelegateImpl 부분에서 다음과 같은 코드들이 들어가져 있습니다.

private boolean performPanelShortcut(PanelFeatureState panelFeatureState, int i, KeyEvent keyEvent, int i2) {
MenuBuilder menuBuilder;
boolean z = false;
if (keyEvent.isSystem()) {
return false;
}
if ((panelFeatureState.isPrepared || preparePanel(panelFeatureState, keyEvent)) && (menuBuilder = panelFeatureState.menu) != null) {
z = menuBuilder.performShortcut(i, keyEvent, i2);
}
if (z && (i2 & 1) == 0 && this.mDecorContentParent == null) {
closePanel(panelFeatureState, true);
}
return z;
}performPanelShortcut() 메서드는 주어진 패널에 대한 단축키를 처리하고 해당 단축키를 실행
keyEvent.isSystem() 을 확인하여 키 이벤트가 시스템 이벤트인지를 확인
시스템 이벤트일 때 추가 처리를 하지 않고 false를 반환
패널이 이미 준비된 상태인지 또는 준비되어야 하는지를 확인 후 패널이 준비되어야 하는 경우 preparePanel() 메서드를 호출하여 패널을 준비
패널의 메뉴 빌더 객체인 panelFeatureState.menu 를 확인 메뉴 빌더가 존재하는 경우에만 단축키 처리를 진행
메뉴 빌더의 performShortcut() 메서드를 호출하여 주어진 단축키를 처리하고 실행
만약 단축키 처리가 성공하고 단축키 실행 시에 패널 외부를 클릭한 경우에는 패널을 닫음
최종적으로 단축키 처리 결과를 나타내는 z 값을 반환
해당 메서드는 주어진 패널에 대한 단축키를 처리하고 실행하는 역할을 수행을 하며 패널의 준비 상태를 확인하고 메뉴 빌더를 사용하여 단축키를 처리하고 처리 결과에 따라 패널을 닫을 수도 있음
그리고 악성코드에 포함된 인증서 내용은 다음과 같습니다.
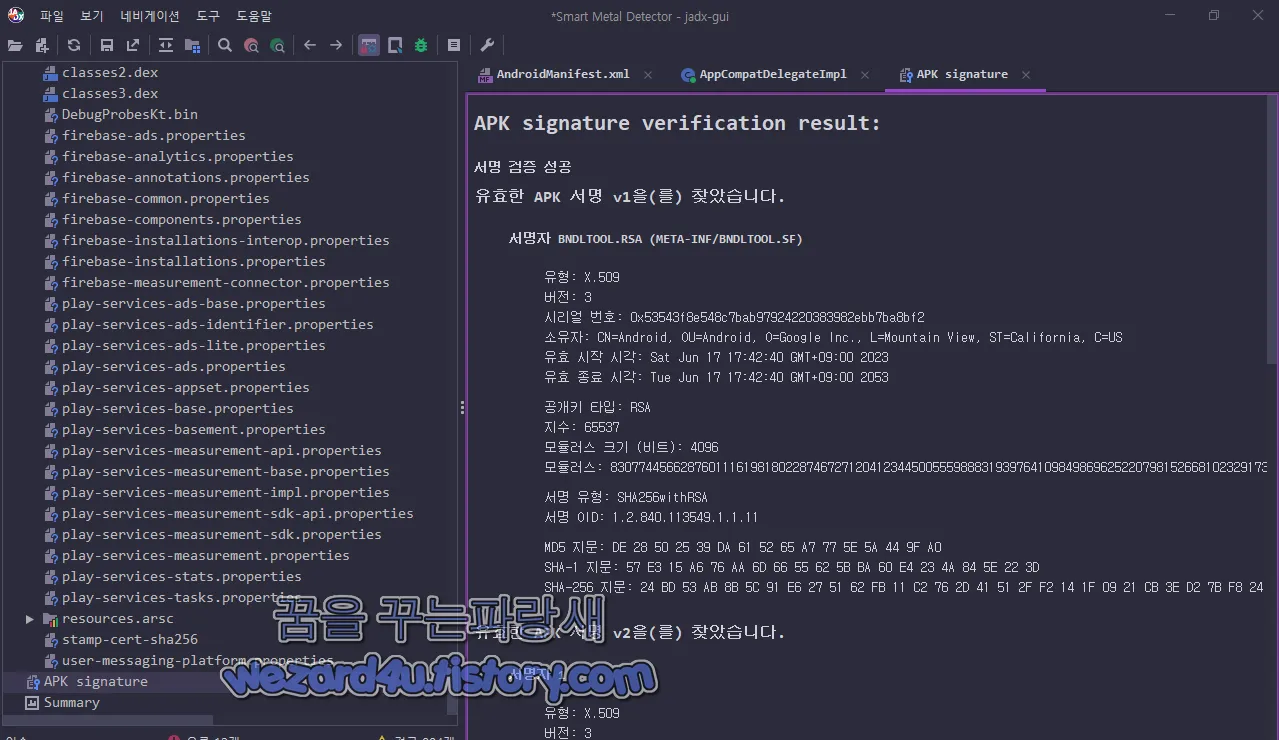
유효한 APK 서명 v1을(를) 찾았습니다.
서명자 BNDLTOOL.RSA (META-INF/BNDLTOOL.SF)
유형: X.509
버전: 3
시리얼 번호: 0x53543f8e548c7bab97924220383982ebb7ba8bf2
소유자: CN=Android, OU=Android, O=Google Inc., L=Mountain View, ST=California, C=US
유효 시작 시각: Sat Jun 17 17:42:40 GMT+09:00 2023
유효 종료 시각: Tue Jun 17 17:42:40 GMT+09:00 2053
공개키 타입: RSA
지수: 65537
모듈러스 크기 (비트): 4096
모듈러스: 830774456628760111619818022874672712041234450055598883193976410984986962522079815266810232917390264550926211751900164283133630195483515410371614404534460996576619253093822454372789046451799291981999082073848866041587890033403671910032265780587753167138907987514115762942859291799142098399611185758769162194533362405072334798939996289777791810175407705463516323348986503511009418017620489824479450249370526372099716379118778692637011574624517733273215293155980755270203974482267872617515363754057164646361578205257029269066334061979207541750998078600751014815919208926012739945852883057105461094310059028781825075586555701322173850959425756861891550683739825199364462184334984699521675884716215069565203065241130563309370606702377099336886991302467476537490700210432869900633257973797247107919039939357582235211370677789066801007324279144989158289213308324894530566958798116301215251686800027957487729411409378470981988325774932004393114625177757667839848075157206559325705485537935166628030134983732147883305262717101147063090444532987056423342047757962049768516482875046011852239429565370971194516238602371633619554696227271172022209497687784933107287551156893274341464256325439157549803617889638372987216702433358269164302916482617
서명 유형: SHA256withRSA
서명 OID: 1.2.840.113549.1.1.11
MD5 지문: DE 28 50 25 39 DA 61 52 65 A7 77 5E 5A 44 9F A0
SHA-1 지문: 57 E3 15 A6 76 AA 6D 66 55 62 5B BA 60 E4 23 4A 84 5E 22 3D
SHA-256 지문: 24 BD 53 AB 8B 5C 91 E6 27 51 62 FB 11 C2 76 2D 41 51 2F F2 14 1F 09 21 CB 3E D2 7B F8 24 99 EA2023-06-29 15:11:51 UTC 기준 바이러스토탈에서 탐지하는 보안 업체들은 다음과 같습니다.
AhnLab-V3:Trojan/Android.Joker.1195502
Alibaba:Trojan:Android/Jocker.bfc5bbcb
Antiy-AVL:Trojan/Generic.ASMalwAD.1C
Avast-Mobile:APK:RepMalware [Trj]
Avira (no cloud):ANDROID/Dldr.Agent.ozuhr
Cynet:Malicious (score: 99)
DrWeb:Android.Joker.2151
ESET-NOD32:Android/TrojanDownloader.Agent.AMI
F-Secure:Malware.ANDROID/Dldr.Agent.ozuhr
Fortinet:Android/Agent.AMI!tr.dldr
Google:Detected
Ikarus:Trojan-Spy.AndroidOS.Joker
K7GW:Trojan-Downloader ( 005a79861 )
Kaspersky:HEUR:Trojan.AndroidOS.Jocker.ys
McAfee:Artemis!DA4FF31B0FE1
McAfee-GW-Edition:Artemis!Trojan
NANO-Antivirus:Trojan.Android.Joker.jwuscm
Symantec Mobile:Insight
AdLibrary:Generisk
Trustlook:Android.PUA.General
언제나 이야기하듯이 구글 플레이 스토어 에서도 악성코든 존재하니 AV-TEST 통과한 백신 앱을 사용을 하는 것이 안전하게 안드로이드 스마트폰을 사용하는 데 도움이 될 것입니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 파일 복구 앱을 위장 하면서 개인정보 전송 하는 악성코드-File Recovery and Data Recovery(2023.07.08) (0) | 2023.07.09 |
|---|---|
| 엑셀 로 구성이 된 악성코드-DETAIL OF DEPENDENTS(2023.02.14) (0) | 2023.07.07 |
| 파이어폭스 115(Firefox 115) 보안 업데이트 새로운 기능 추가 (0) | 2023.07.05 |
| 김수키(Kimsuky)만든 링크 방식 악성코드-scarcurft.lnk(2023-04-19) (0) | 2023.07.04 |
| 김수키(Kimsuky)워드 악성코드-협의 이혼 의사 확인 신청서.doc(2023.06.28) (0) | 2023.06.30 |
| 토르 브라우저 접근성 개선 12.5 업데이트 (0) | 2023.06.29 |
| 김수키(Kimsuky)만든 링크 방식 악성코드-Pipelines Profile(2023,01,31) (0) | 2023.06.26 |
| 이메일로 유포 되는 Remcos RAT 악성코드-RO10098.docx.doc(2023.6.8) (0) | 2023.06.22 |





