오늘은 회사와 서버는 독일에 있는 보안 메일 서비스인 Tuta 메일에 대해 글을 적어보겠습니다.
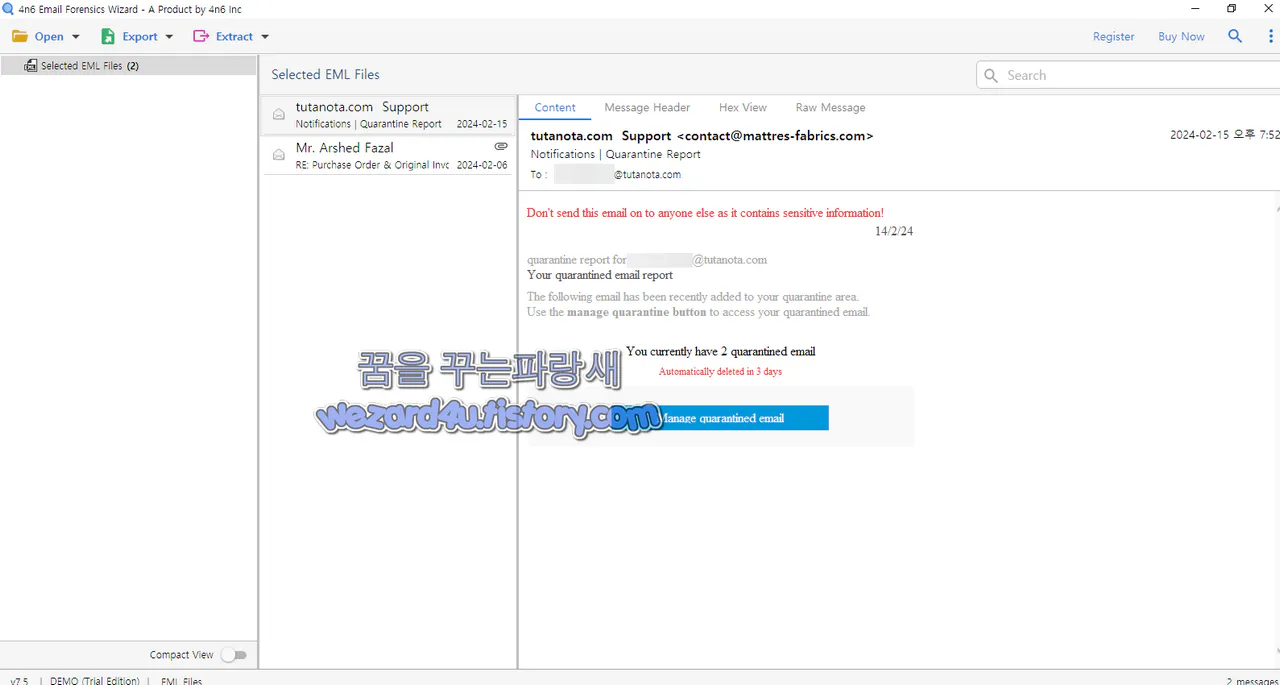
일단 해당 이메일은 간단하게 내용이 돼 있습니다.
Don't send this email on to anyone else as it contains sensitive information!
14/2/24
quarantine report for ???????@tutanota(.)com
Your quarantined email report
The following email has been recently added to your quarantine area.
Use the manage quarantine button to access your quarantined email.
You currently have 2 quarantined email
Automatically deleted in 3 days
Manage quarantined email
피싱 메일 내용
이 이메일에는 민감한 정보가 포함되어 있으므로 다른 사람에게 보내지 마세요!
24/2/14
????????@tutanota(.)com에 대한 격리 보고서
격리된 이메일 보고서
최근 귀하의 격리 구역에 다음 이메일이 추가되었습니다.
격리된 이메일에 액세스하려면 격리 관리 버튼을 사용하세요.
현재 격리된 이메일이 2개 있습니다.
3일 후 자동 삭제됨
격리된 이메일 관리
그리고 이메일 헤더 내용은 다음과 같습니다.
Authentication-Results:w10(.)tutanota(.)de (dis=reject; info=spf);
dmarc=fail (dis=spam p=quarantine; aspf=s; adkim=s; pSrc=dns) header.from=mattres-fabrics(.)com
Received: from w1.tutanota(.)de ([192.168(.)1.162])
by tutadb(.)w10(.)tutanota(.)de
with SMTP (SubEthaSMTP 3.1.7) id LSN3QF9F
for ???@tutanota(.)com;Thu, 15 Feb 2024 11:52:25 +0100 (CET),
from 77(.)65(.)243(.)92.in-addr(.)arpa (unknown [92(.)243(.)65(.)77])
by w1(.)tutanota(.)de (Postfix) with ESMTPS id 0EDC2FBF89F
for <?????@tutanota(.)com>;Thu, 15 Feb 2024 10:52:24 +0000 (UTC)
Received-SPF: Fail (mailfrom) identity=mailfrom; client-ip=92(.)243(.)65(.)77;
helo=77(.)65(.)243(.)92.in-addr.arpa; envelope-from=contact@mattres-fabrics(.)com;
receiver=<UNKNOWN>
From: "tutanota(.)com Support" <contact@mattres-fabrics(.)com>
To:????@tutanota(.)com
Subject: Notifications | Quarantine Report
Date: 15 Feb 2024 02:52:23 -0800
Message-ID: <20240215025222.D2F1CA6D20D0515D@mattres-fabrics(.)com>
MIME-Version: 1.0
Content-Transfer-Encoding: quoted-printable이메일 헤더 설명
1.Authentication-Results:
SPF (Sender Policy Framework):SPF 확인에서 실패한 것으로 나타나 보내는 서버(IP 92(.)243(.)65(.)77)가 mattres-fabrics(.)com 도메인을 대표해 이메일을 보낼 권한이 없다는 것을 의미
DMARC (Domain-based Message Authentication, Reporting, and Conformance):DMARC 확인에서 실패하였으며 quarantine 정책이 적용되어 해당 이메일이 스팸으로 처리되거나 격리될 수 있음을 나타냄
2.Received:
이메일이 서버를 거쳐 가는 과정을 나타냄
IP 92(.)243(.)65(.)77에서 시작되어 w1(.)tutanota(.)de를 거쳐 갔음
3.Received-SPF:
SPF 확인 결과가 실패로 나타나며 IP 92(.)243(.)65(.)77 서버가 mattres-fabrics(.)com을 대표하여 이메일을 보낼 권한이 없다는 것을 의미
4.From:
tutanota(.)com Support 으로 표시되었지만, 실제 이메일 주소는 contact@mattres-fabrics(.)com 입니다.
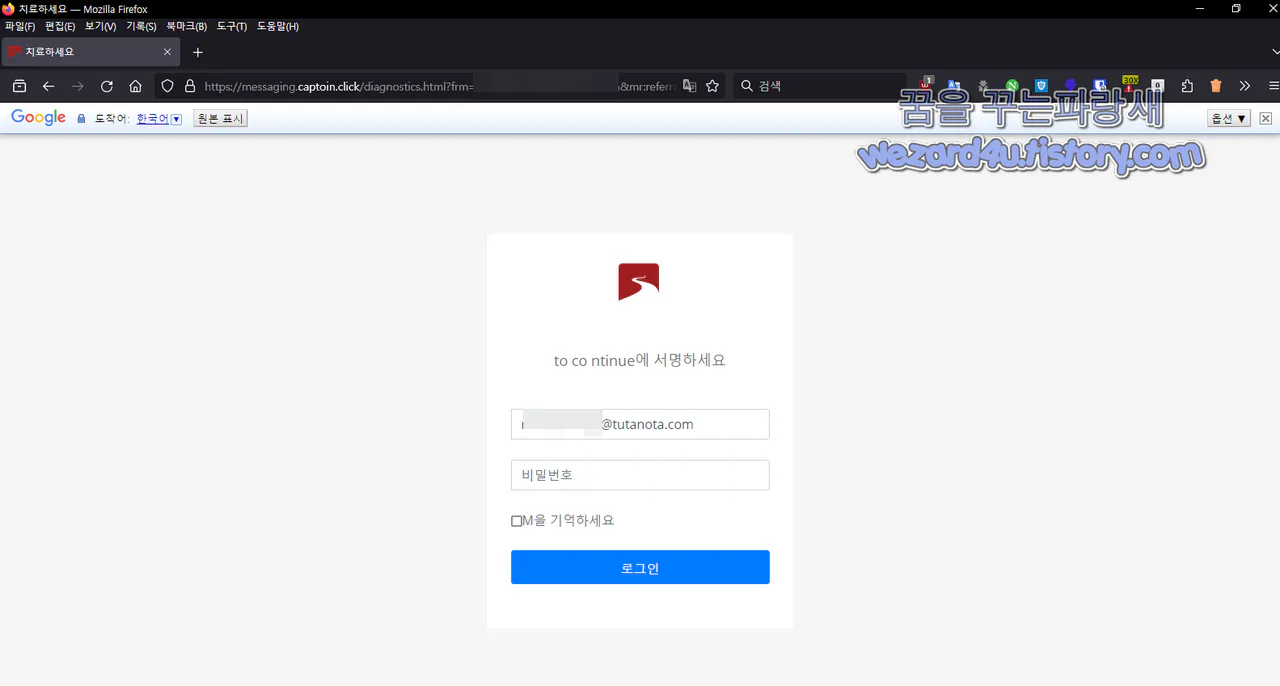
해당 피싱 사이트에 접속을 하면 다음과 같이 돼 있는 것을 확인할 수가 있으며 내용은 다음과 같습니다.
to co ntinue에 서명하세요.
그리고 왼쪽 상단에서는 치료하세요. 라고 돼 있는데 무엇을 치료해야 하는지 궁금해지기는 합니다. 그리고 해당 부분은 새로 고침을 할 때마다 바뀌는 특징이 있습니다. 해당 유포 주소는 다음과 같습니다.
https://messaging(.)captoin(.)click/diagnostics(.)html?frm=???????
@tutanota(.)com&mr:referralID=4dad276d-cf06-11ee-83ba-12a9c0fb0737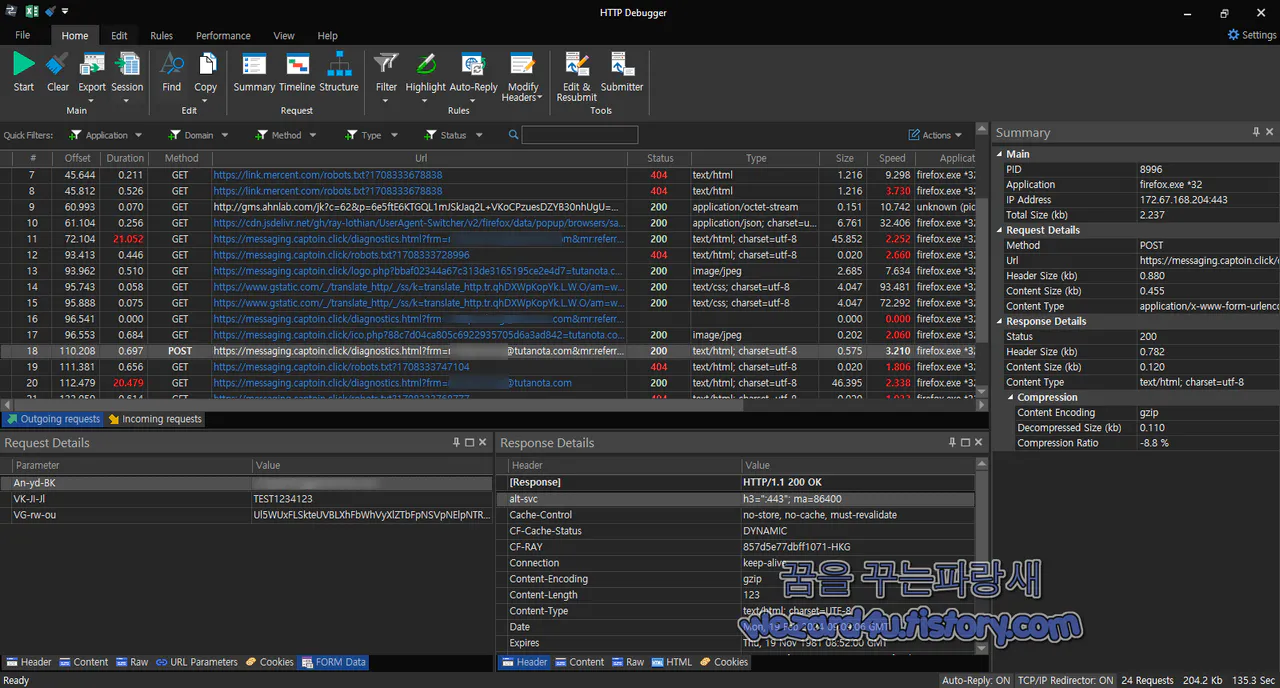
그리고 Raw 값은 다음과 같습니다.
POST /diagnostics(.)html?frm=???????@tutanota(.)com&mr:referralID=4dad276d-cf06-11ee-83ba-12a9c0fb0737 HTTP/1(.)1
Host: messaging(.)captoin(.)click
User-Agent: Mozilla/5.0 (Linux; Android 14; SAMSUNG SM-S921N) AppleWebKit/537.36 (KHTML, like Gecko) SamsungBrowser/22.0.3.1 Chrome/120.0.0.0 Mobile Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: ko-KR,ko;q=0.8,en-US;q=0.5,en;q=0.3
Prefer: safe
Content-Type: application/x-www-form-urlencoded
Origin: hxxps://messaging(.)captoin(.)click
DNT: 1
Sec-GPC: 1
Connection: keep-alive
Cookie: PHPSESSID=i52l0ml0sjfa1iadrf9cgac7d6; googtrans=/auto/ko; googtrans=%2Fauto%2Fko; googtrans=/auto/ko
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Accept-Encoding: gzip, deflate
Content-Length: 466
An-yd-BK=????????%40tutanota(.)com&VK-JI-Jl=TEST1234123&VG-rw-ou=Ul5(W)UxFLSkteUVBLXhFbWhVyXlZTbFpNSVpNElpNTRJvXlhaF0wWBRIf(U)l5WUxFLSkteUVBLXhFbWhM1VFASdG0VSl(F)bWllWUVpbFVRQEnRtE1RQE1pREmpsE1pRFQ4JDw8VBg8PFQ4JDw8VB(w)kPFQ4JDw8VCA8KFQ0LFXFwFQ4VSlFbWllWUVpbNXJQRVZTU14QChEPHxdzVlFKRwQfflFbTVBWWx8OCwQfbH5ybGpx(e)B9s(c)hJsBg0OcRYffk9PU1poWl10VksQCgwIEQwJHxd0d2tycxMfU1ZUWh94WlxUUBYfbF5STEpRWH1NUEhMWk0QDQ0(R)D(x)EMEQ4ffFdNUFJaEA4NDxEPEQ8RDx9yUF1WU1ofbF5ZXk1WEAoMCBEMCTV(t)WllaTVpNDQUf
일단 해당 피싱 사이트는 Eset,구글 세이프 브라우징, 마이크로소프트 스마트스크린,Emsisoft에 신고는 했습니다. 항상 기본적인 보안 수칙을 지키는 것이 안전하게 사용을 하는 방법의 하나입니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 윈도우 11 버전 23H2는 이전 시스템에 자동으로 설치 (0) | 2024.02.26 |
|---|---|
| 애플 제로클릭 바로가기 보안 취약점 해결 및 취약점 정보 공개 (0) | 2024.02.24 |
| 파이어폭스 123.0 보안 업데이트 및 손상된 사이트 보고 도구 추가 (0) | 2024.02.23 |
| LockBit 랜섬웨어 글로벌 경찰 작전으로 인해 중단 (0) | 2024.02.22 |
| 구글 크롬 비밀번호를 기기 내에서 암호화 한후 구글 비밀번호 관리자에 저장 (0) | 2024.02.20 |
| 브라우저에 비밀번호를 저장 하면 안되는 이유 와 안전하게 저장 하는 방법 (2) | 2024.02.19 |
| Microsoft Outlook(마이크로소프트 아웃룩) 새로운 RCE 버그 (0) | 2024.02.17 |
| 견적의뢰서 유포 되고 있는 악성코드-RFQ-견적의뢰서-견적의뢰서.exe(2024.2.8) (0) | 2024.02.16 |





